Intended readership
CTOs, CISOs, and threat intelligence teams at banks, payment processors, and financial institutions; fraud, risk management, AML and compliance teams seeking threat intelligence integration.
Available in
Introduction
Detecting and preventing fraud has become a continuous challenge for financial institutions. More than $40 billion in cryptocurrency was laundered in 2024 alone, much of it through wallets and mixing services that leave no trace in standard compliance systems. Meanwhile, fiat-based laundering remains an even larger threat, with global estimates ranging between $2.2 trillion and $5.5 trillion every year. Much of this activity flows through payment infrastructure that even advanced defense systems cannot detect.
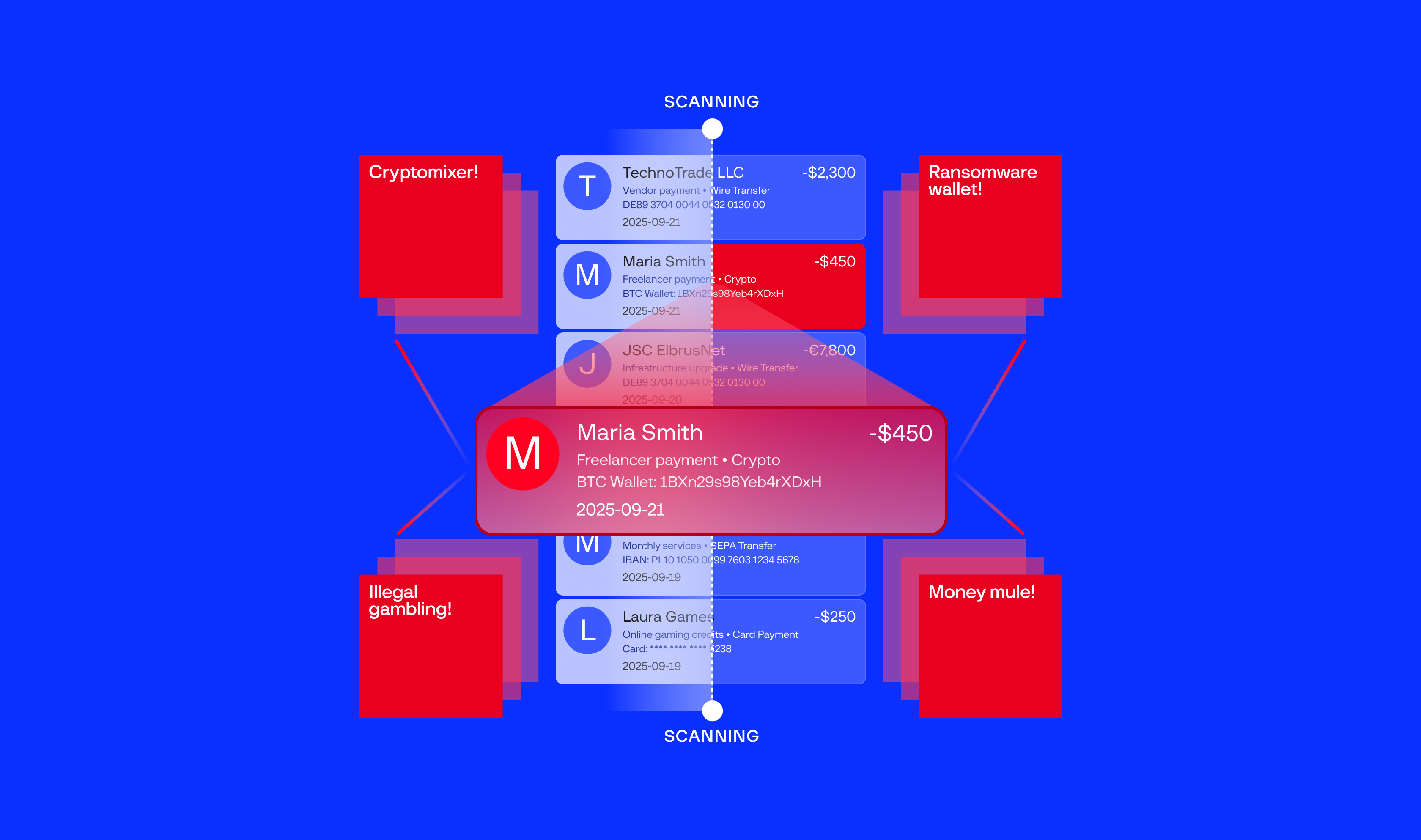
Consider this scenario: Your bank’s fraud system flags a suspicious outbound transaction pattern, but the recipient account passes all standard compliance checks. Three months later, you discover that the transaction was fraudulent and that the same receiving account at a third-party institution has been acting as a mule, processing ransomware payments or illegal gambling proceeds.
This is just one possible scenario. Criminal funds can also flow into legitimate accounts at your bank from external sources, or one of your customer accounts may be operated by criminals as part of a laundering scheme — all without your existing systems noticing. Each of these cases may lead to damaged customer relationships, the need for regulatory scrutiny, and operational costs that end up being much higher than investments in security.
Group-IB’s new Suspicious Payment Details (SPD) module closes this disconnect between detection capabilities and actual criminal payment networks. How? Keep reading to find out.
What threat intelligence teams know, but your fraud team doesn’t
Most threat intelligence providers excel at delivering indicators of compromise and vulnerability assessments that serve SOCs and incident response teams effectively. However, these feeds are not designed to address the payment verification challenges that financial institutions face in real-time transaction processing.
Threat Intelligence teams routinely analyze payment infrastructure as part of threat actor attribution and deanonymization efforts. However, this critical payment data (including details about illegal gambling platforms, ransomware payment processors, and dark web exchanges) remains siloed within security operations and rarely reaches fraud teams.
While your SOC team receives detailed reports about malware families and attack vectors, your fraud team makes split-second payment approval decisions without visibility into whether recipient accounts are controlled by ransomware operators or money mule networks. The disconnect between threat intelligence and payment intelligence is the industry’s most expensive blind spot.
What is the Suspicious Payment Details module?
Suspicious Payment Details (SPD) is the first-of-its-kind module within Group-IB’s Threat Intelligence that delivers payment identifiers associated with active criminal operations: the bank accounts, cryptocurrency wallets, and payment details that fraudsters use to monetize their attacks.
Where other providers tell you about threats, we tell you where the money goes.
Collection methodology and sources
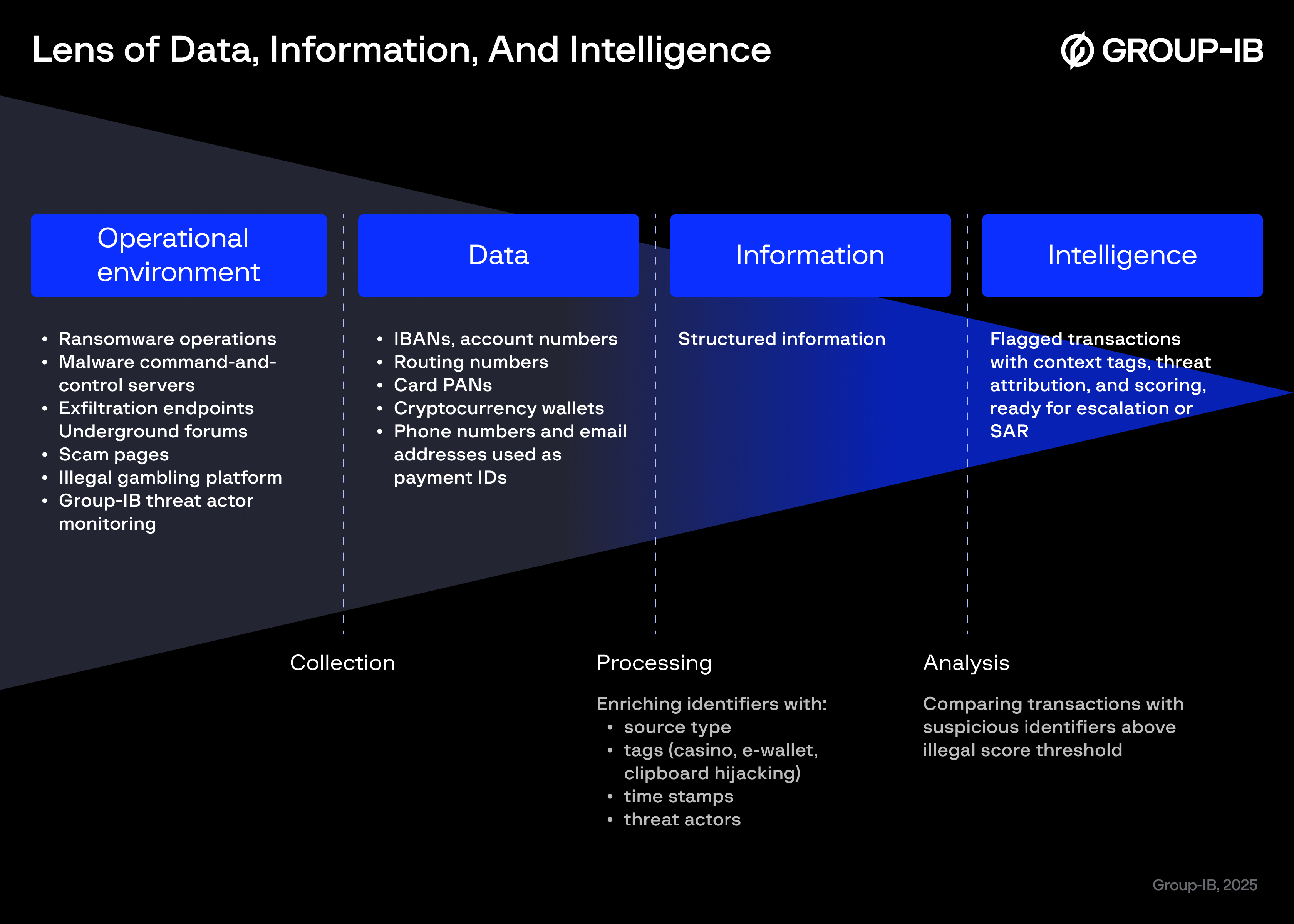
Figure 1. Collection sources, process and outcome
Our collection methodology extends into criminal payment infrastructure that traditional security vendors cannot access. We analyze payment details exposed through ransomware operations, malware command-and-control servers, exfiltration endpoints, underground forums, scam pages, and illegal gambling platforms. In addition, Group-IB experts gather payment details during daily threat actor monitoring activities.
Suspicious Payment Details provide comprehensive intelligence across multiple payment categories:
Banking identifiers: IBANs, account numbers, routing numbers, and card PANs from confirmed money laundering operations and mule networks
Cryptocurrency wallets: BTC, ETH, XMR, and other cryptocurrency addresses tied to ransomware groups, clipper malware, and mixer services
Additional payment identifiers: Phone numbers and email addresses used as payment IDs in various systems, which expands fraud coverage beyond transfers strictly tied to account numbers.
Each record may include contextual tags (casino, e-wallet, clipboard hijacking), service name, source type and detection metadata, threat actor and malware attribution, a numeric Illegal Score via API estimating likelihood of criminal use, and transparent evidence with first-seen and last-seen timestamps.
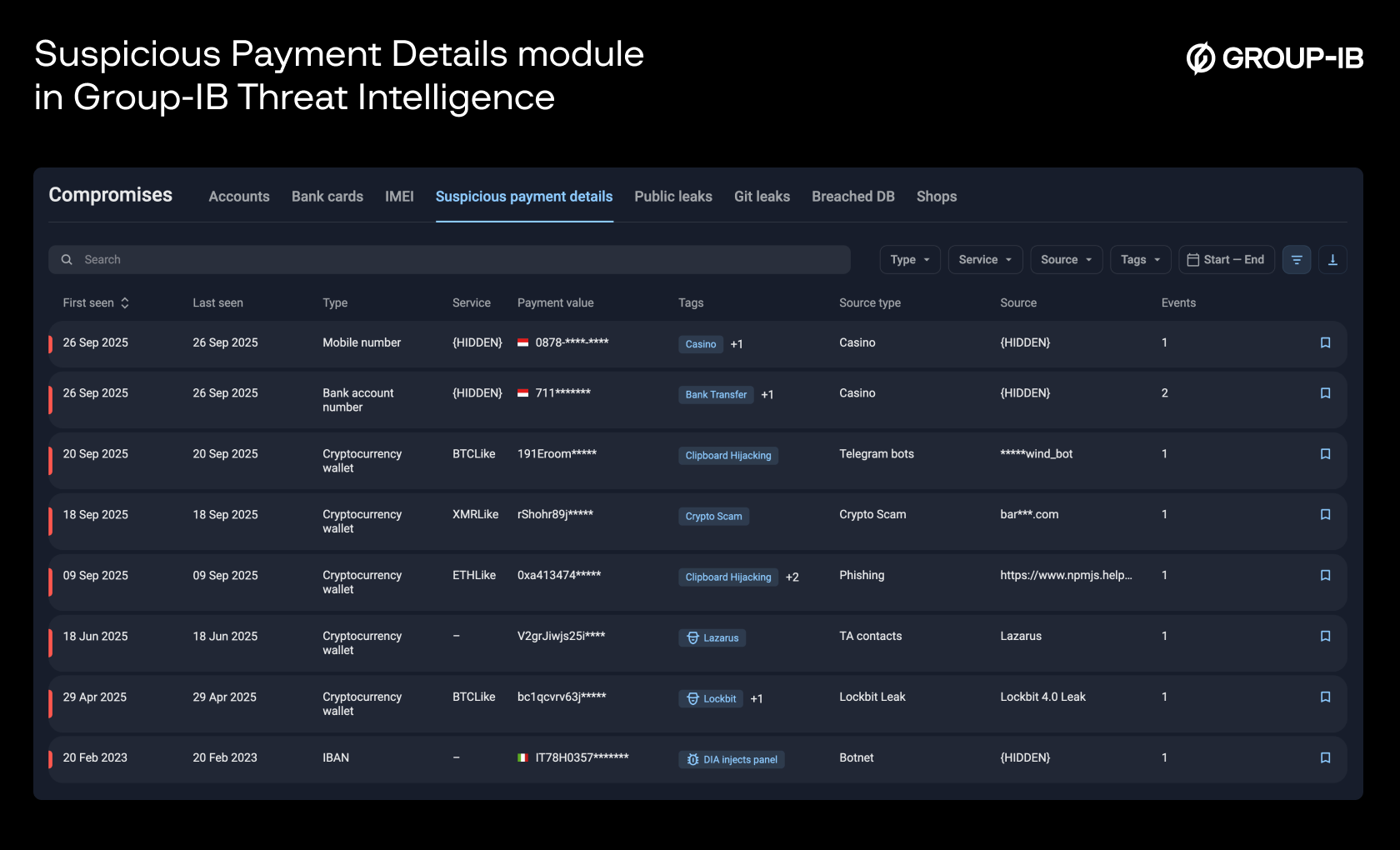
Figure 2. Suspicious Payment Details module in Group-IB Threat Intelligence
How teams use SPD to stop criminal payments
The SPD module delivers actionable intelligence through two operational approaches that address the most pressing challenges in payment security:
For fraud and transaction monitoring teams:
The module supports outbound protection by enabling real-time transaction flagging and escalation. Fraud engines can cross-reference recipient details against criminal payment intelligence before processing wire transfers or other outbound payments. Suspicious Payment Details supply high-volume enrichment data keyed by destination identifiers including IBANs, sort codes, wallet addresses, and phone IDs.
When SPD identifies accounts tied to ransomware operations, illegal casino schemes, or underground exchange networks, transactions can be instantly flagged and escalated for immediate manual review. Compliance teams can then pause the transfer within the legal “report and wait” window and file a Suspicious Activity Report (SAR). This prevents losses, ensures regulatory alignment, and turns compliance into a competitive advantage.
For risk, AML, and compliance teams
The module supports inbound detection and internal risk identification through continuous account auditing and monitoring. Compliance teams can systematically cross-check existing customer accounts against criminal payment intelligence to identify accounts established for money laundering or compromised for illicit activities.
If a flagged external account initiates a transfer to the bank’s legitimate customer, your team can trigger enhanced due diligence, refresh KYC documentation, and investigate why the clean account is receiving flagged funds.
If the module reveals that one of the bank’s own customer accounts is operated by threat actors, your team can freeze the account, initiate an internal review, analyze connected devices or counterparties, and file reports with regulators.
The module provides real-time API access, flexible integration and export functionality, which enables teams to implement predefined response protocols including account freezing, credit rejection, or enhanced due diligence initiation. Early detection through threat intelligence enables swift remediation, reduces regulatory exposure, and prevents reputational damage from unknowingly facilitating criminal operations.
The shift toward cyber-fraud fusion
The way fraud teams use the Suspicious Payment Details module reflects a bigger industry trend known as cyber-fraud fusion. Modern threat actors no longer operate within traditional boundaries. They seamlessly blend cybersecurity attacks with financial fraud monetization. A single criminal operation might deploy malware to steal credentials, use social engineering to bypass authentication, and then leverage money mule networks to cash out stolen funds. This evolution demands an equally integrated defense approach.
What is cyber-fraud fusion? It’s the strategic integration of cybersecurity threat intelligence with fraud detection and AML operations. Instead of treating cyber threats and financial fraud as separate problems handled by different teams, cyber-fraud fusion unites these traditionally siloed functions to create a comprehensive view of criminal operations.
Why does this matter? According to Gartner, by 2028, 20% of large enterprises will move to cyber-fraud fusion teams to combat internal and external adversaries, up from less than 5% today. This highlights the urgency for banks and payment providers to rethink organizational silos and embrace a unified view of threats.
Fraud intelligence as the bridge: Within cyber-fraud fusion, fraud intelligence serves as the critical connector between cyber threat data and financial crime prevention. Group-IB customers already benefit from comprehensive fraud intelligence in Fraud Protection that profiles fraudster behavior using behavioral patterns, geolocation data, device fingerprints, and keystroke patterns. However, traditional fraud intelligence focuses on attack patterns during the fraud attempt itself.
The fusion is also supported by Group-IB’s Fraud Matrix — a visual kill chain of fraud tactics, techniques, and countermeasures, inspired by the MITRE ATT&CK® framework. It helps analysts deconstruct schemes, customize responses, and build rule-based defenses. With its clear visual interface, reporting features, and customization options, the Fraud Matrix is a cornerstone of modern cyber-fraud fusion workflows.
The Suspicious Payment Details module extends fraud intelligence capabilities by providing the intelligence necessary for proactive intervention before fraudulent transactions complete. The module complements other financial intelligence modules already available to Threat Intelligence customers, such as compromised card data and banking credentials.
Strategic value for financial institutions
Group-IB delivers comprehensive threat intelligence that transforms how financial institutions make payment decisions. The Suspicious Payment Details module provides intelligence about criminal payment infrastructure that traditional security vendors cannot access or verify, creating measurable long-term advantages:
Operational clarity: Our integrated intelligence ecosystem connects payment details to broader criminal operations and threat actor campaigns, allowing for informed decisions rather than reactive responses. When you know a cryptocurrency wallet belongs to a specific ransomware group, or that an IBAN is tied to money laundering operations, payment decisions become strategic advantages.
Market differentiation through customer protection: Every prevented payment to a criminal account reinforces customer trust and institutional credibility. Your fraud prevention capabilities become a competitive differentiator when customers recognize that your organization actively protects them from evolving threats that other banks tend to overlook.
Regulatory positioning through proactive compliance: Demonstrating criminal payment intelligence to regulators positions your organization as proactive rather than reactive in financial crime prevention. Such an approach transforms regulatory relationships from compliance obligations into partnership opportunities for industry leadership.
Implementation
For existing Group-IB Threat Intelligence customers, the Suspicious Payment Details module is available immediately and at no additional cost under current contracts. Integration is straightforward: real-time API access allows fraud prevention systems to fetch identifiers and automatically flag suspicious transactions on their end before they’re processed, while batch export options support teams that prefer scheduled checks and audits.
To make adoption even easier, the module is also natively available in leading platforms including Splunk ES/Cloud/SOAR, Google SecOps, ThreatConnect, and IBM QRadar.
What’s next and how to get started
Our development priorities focus on expanding source coverage and analytical capabilities through enhanced scoring models for more nuanced risk assessment beyond binary suspicious determinations, and additional underground sources including illegal money exchangers and emerging payment platforms.
The criminal finance ecosystem evolves rapidly and requires us to keep adapting our collection and analysis methodologies. Organizations can now leverage intelligence about criminal payments for real-time operational decisions, which shows a strategic evolution in threat intelligence that extends security-focused intelligence into financial crime prevention.
We would be happy to show you how the Suspicious Payment Details module can strengthen your existing threat intelligence operations and address challenges relating to payment verification.