Introduction
At every product launch and industry event, smartphone manufacturers promise ever-increasing device security. They emphasize extended support for operating system (OS) updates and claim that even after major OS updates end, security patches will continue for years, providing ongoing protection for users. But how reliable are these assurances?
Recent findings suggest that smartphone manufacturers frequently downplay or conceal security vulnerabilities. This leaves both individuals and businesses exposed to risks such as data breaches, identity theft, and corporate espionage. A recent leak of Cellebrite software—a tool used to extract data from smartphones—illustrates how easily devices can be exploited, raising urgent questions about transparency and user safety.
In this article, we’ll analyze how concealed vulnerabilities affect all users of modern smartphones, review key risks exposed by the Cellebrite leak, and discuss actionable recommendations for manufacturers and users alike.
Key findings in the blog
- Leaked Cellebrite Tools: Sensitive forensic tools have been exposed, showing that virtually all modern smartphones—after their first unlock—are vulnerable to data extraction.
- AFU (After First Unlock) Vulnerability: Most devices are unprotected once unlocked, leaving user data exposed to exploitation.
- Data Port Exploits: Many attacks target vulnerabilities in bootloaders or USB ports during active use.
- Data Manipulation Risks: Cracked forensic software allows unauthorized data modification, undermining the reliability of smartphones as evidence.
- Flawed Anti-Theft Mechanisms: Vulnerabilities such as Apple’s “Find My iPhone” feature could allow stolen devices to be temporarily activated and resold.
Leaked Cellebrite tools and their implications
Who is affected?
Every smartphone user, regardless of whether you use an Apple iOS or Google Android device, has vulnerabilities in smartphone security that put your data, privacy, and safety at risk. While older devices are particularly susceptible, even the latest models are far from immune. Unfortunately, all users of modern smartphones running Apple iOS and Google Android are at risk.
What was exposed?
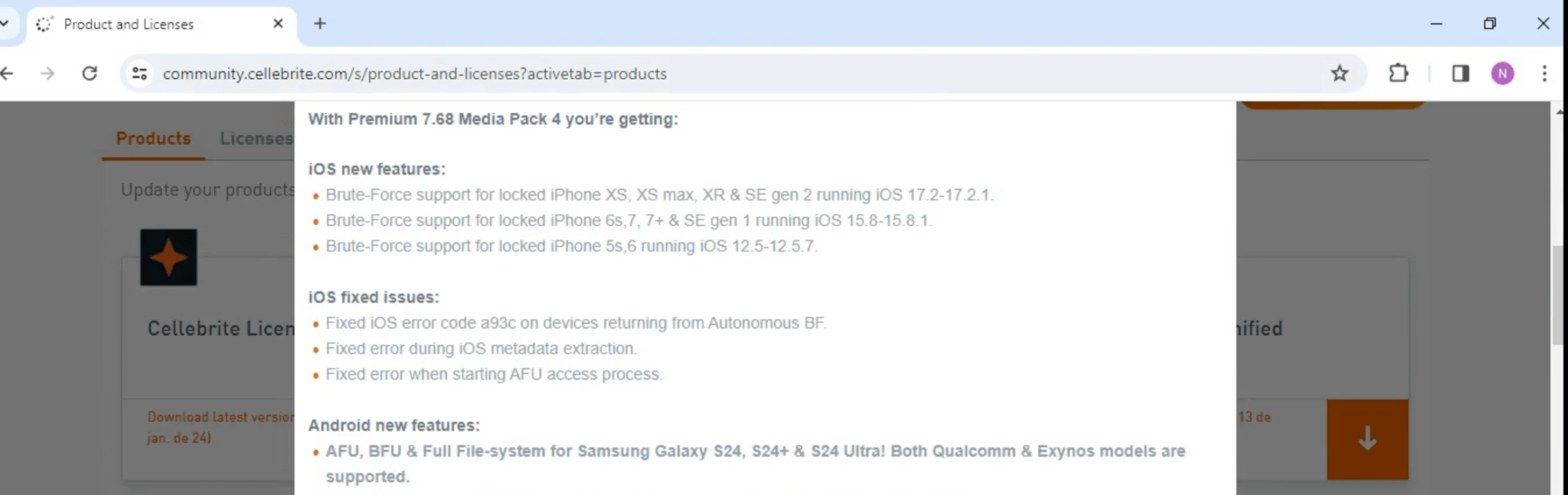
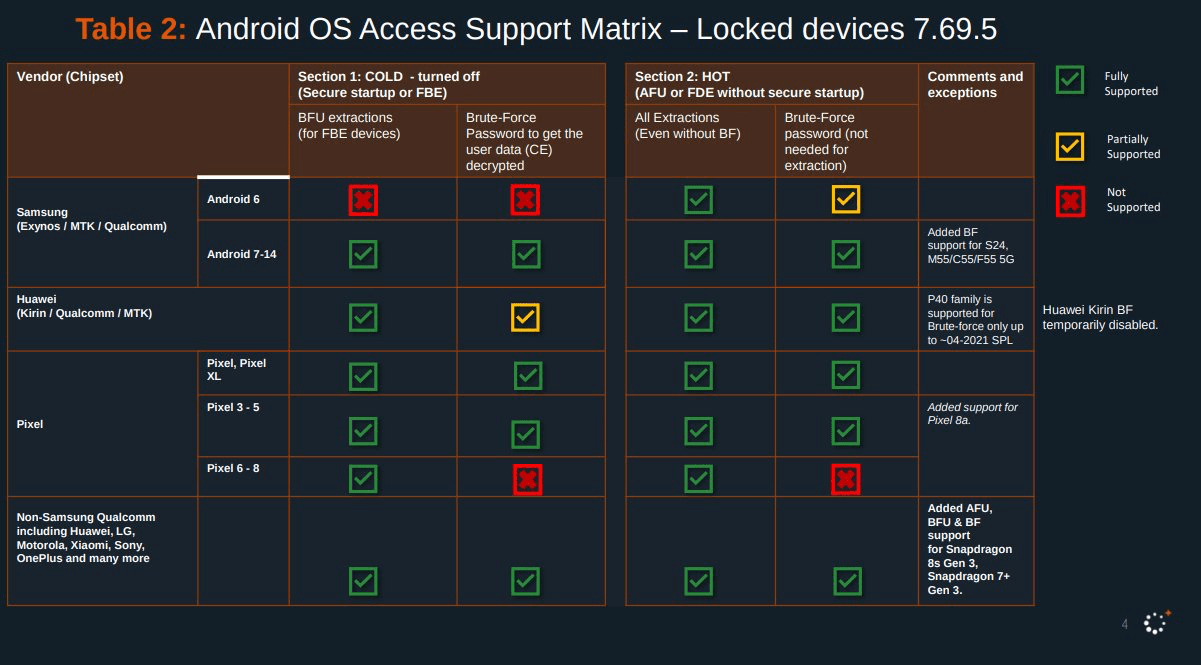
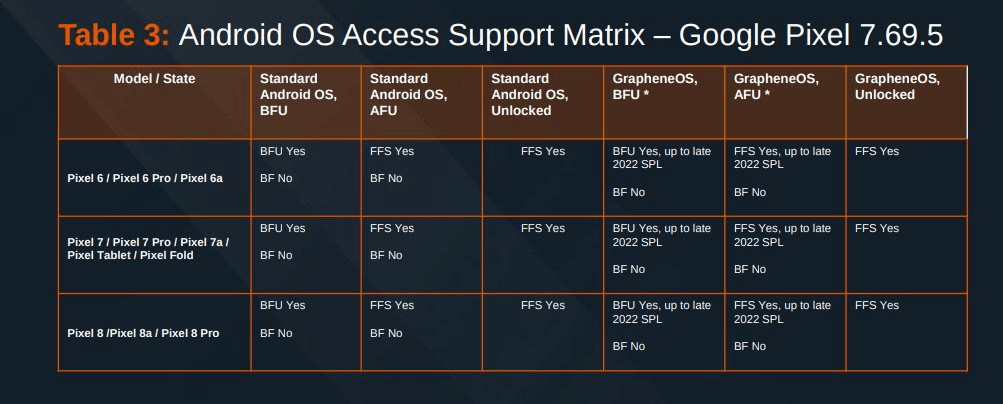
In February 2024, leaks involving Cellebrite Premium—a tool used by law enforcement agencies to extract data from locked smartphones—shone a spotlight on the vulnerabilities of both iOS and Android devices.
The leaks included:
- Changelogs detailing the tool’s capabilities for extracting data from a wide range of devices.
Figure 1. A screenshot of a video file in which an unidentified person flips through the Cellebrite’s software changelog, showing the options for extracting data from various devices.
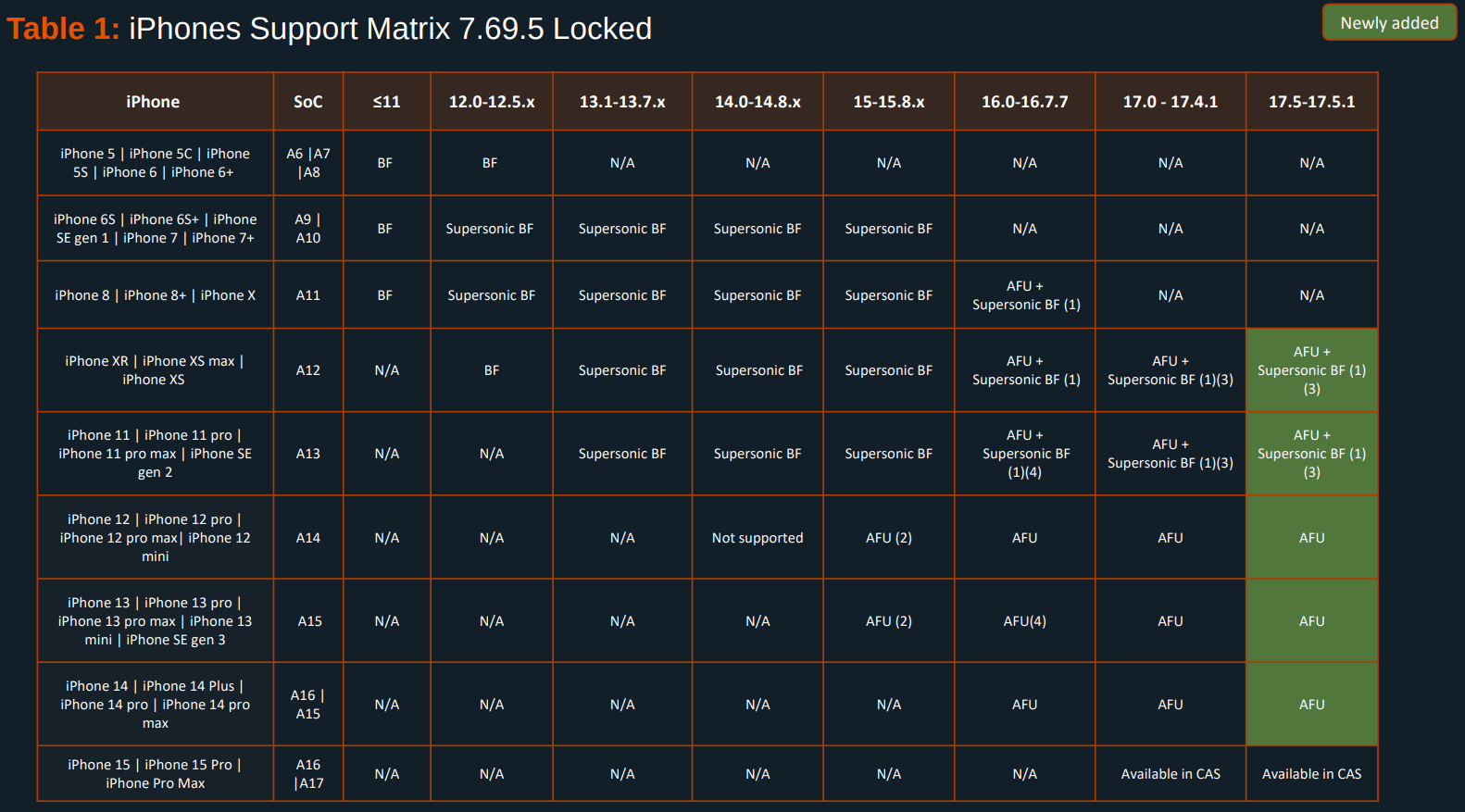
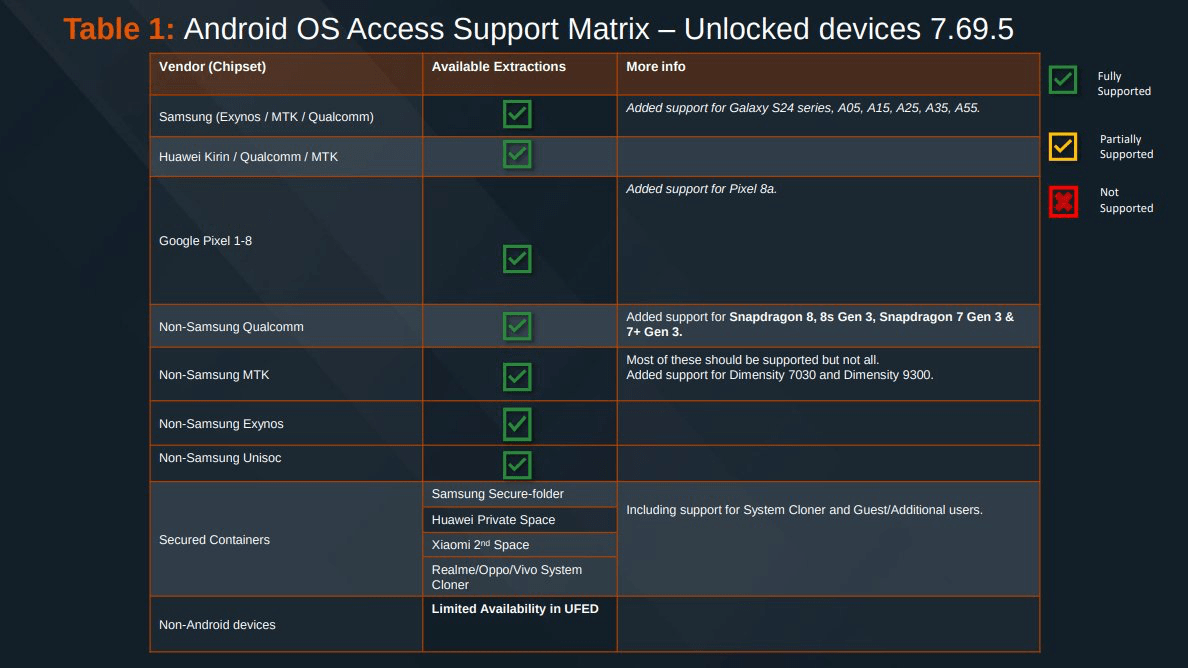
- Device Vulnerability Tables published on platforms like GrapheneOS and websites such as 404 Media, showing which smartphones can be unlocked under specified conditions.
Similarly, in a recent leak, The Graykey, a phone unlocking and forensics tool that is used by law enforcement around the world, light is shed on the potential capabilities of the tool, and exposes its struggles with Apple’s latest iOS updates.
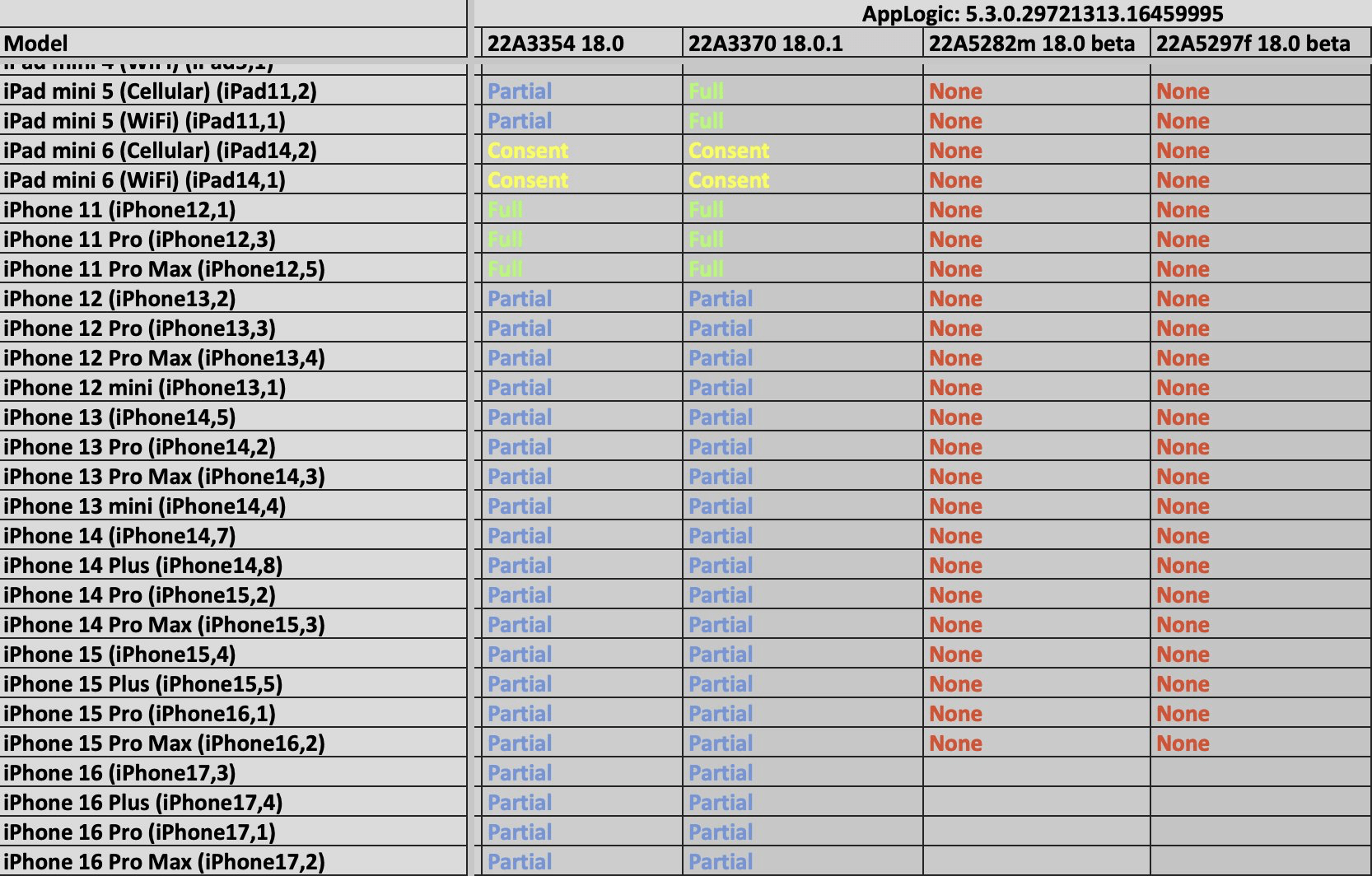
Figure 3. An image of a document detailing Graykey’s functionality with iPhones operating on iOS 18.0 and 18.0.1.
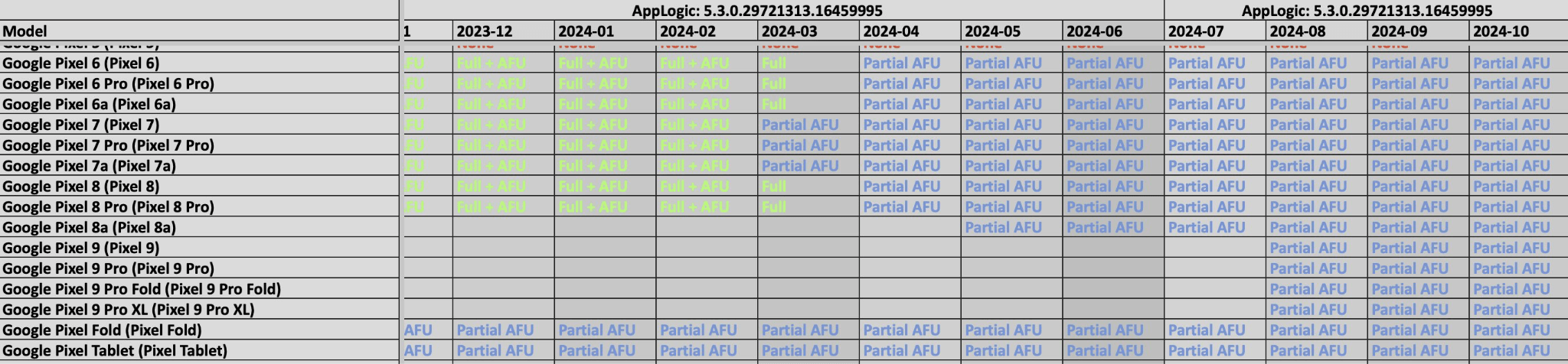
Figure 4. An image of a document detailing Graykey’s functionality with Google Pixel phones.
Key concepts revealed in the leak:
- BF (Brute Force): Cracking a password, often marketed as “supersonic” for speed.
- BFU (Before First Unlock): Exploiting a device before its first password entry, for example when it’s powered down.
- AFU (After First Unlock): most devices are vulnerable after being unlocked once, making them susceptible to data extraction during use.
- FFS (Full File System): Extracting an entire device’s file system, including sensitive user data.
What does this mean for users?
The leak shows that older devices, such as the iPhone X and those preceding it, are wide open and can be easily exploited, with manufacturers declining to patch known vulnerabilities, especially for devices that have been retired from the market, also known as Product End-of-Life (EOL). It also reveals that despite advanced encryption, modern devices are not immune; in fact, current devices remain vulnerable, especially in AFU mode. Finally, it underscores the potential misuse of forensic tools, as highlighted in the case of the cracked versions of Cellebrite software, allowing unauthorized parties to manipulate smartphone data, raising serious concerns about data integrity.
Implementation of “Inactivity Reboot” in iOS18
Mobile device forensics experts have recently identified new security features in iOS 18. Specifically, Apple devices now automatically reboot after 72 hours of inactivity while in a locked state. Following the reboot, the devices switch from the AFU mode to the BFU mode.
Additionally, Magnet Forensics discussed the security implications of iOS 18’s inactivity reboot feature, highlighting that the reboot is triggered after 72 hours of device inactivity, causing a transition from AFU to BFU mode.
It would be beneficial for this feature to be extended across the entire iPhone lineup starting from iPhone XS, and additionally reducing the inactivity period to 12 hours when Lockdown Mode is activated could significantly enhance security.
The exploitation of stolen and locked smartphones
Even the most secure smartphones can be exploited when stolen or lost. Two of the most common methods for leveraging locked iPhones include jailbreaking and file swapping, which enables attackers to access system files and replace them with manipulated data. Another method is bypassing activation locks, which involves unauthorized parties using fake responses seemingly from Apple servers, or swapping backup files to bypass features like “Find My iPhone” and “Activation Lock”.

Figure 5. A screenshot of a price list for unlocking various Apple devices, with prices in Tether (USDT).
These bypasses are often temporary, lasting only until a firmware reset or update. However, they provide enough time for attackers to resell stolen devices as fully functioning smartphones.
Figure 6. A screenshot of an announcement from a popular jailbreaking tool, iRemoval Pro, announcing its compatibility with iOS 17, as well as support for the iPhone XR and models up to the iPhone 15 Pro Max, as well as the iPads with A12 to M4 chipsets.
Implications
There are two key implications: theft and resale, and compromised evidence. First, this shows that even an iPhone 15 Pro Max, can, for instance, be activated and sold despite its security features. Secondly, and perhaps even more sinister, smartphones used as evidence can no longer guarantee data integrity, as information can be planted or altered.
Conclusion
The leaked Cellebrite tools unveil the unsettling reality of smartphone security. Despite manufacturers’ claims, vulnerabilities in modern devices could potentially leave users exposed to risks including data breaches, identity theft, evidence tampering, or even corporate espionage.
Manufacturers must prioritize transparency and take concrete steps to close security gaps, while users should remain vigilant by adopting best practices and using secure devices.
Risks to users:
- Data breaches: sensitive personal information like passwords, photos, and messages can be stolen.
- Identity theft: Exploited vulnerabilities open users to fraudulent activities.
- Planted evidence: Forensic tools in the wrong hands can inject fake data into seized smartphones.
Risks to businesses:
- Corporate espionage: Vulnerabilities can be exploited to steal intellectual property or credential information.
- Regulatory penalties: Organizations failing to secure employee devices may face compliance issues.
- Reputational damage: Data breaches caused by insecure smartphones can erode trust among customers and partners.
Recommendations
Group-IB’s digital forensics investigators have years of experience in ensuring mobile devices are secure. Other steps manufacturers and smartphone users can take include:
For smartphone manufacturers:
- Enhance hardware security: Strengthen hardware security by enabling a complete disconnection of the smartphone port in locked (chariging only) mode, which protects the port hardware and interrupts any data transfer.
- Introduce AFU to BFU transitions: Integrate the ability to switch the smartphone from AFU to BFU mode, for example after a specified period (12/24/72 hours).
- Strengthen bootloaders: Identify and fix vulnerability problems in bootloaders and ensure that these vulnerabilities are reported. Some older smartphones can be compromised by brute-force hacking the password (hence the recommendation for a minimum password length).
- Improve biometric security: Include a setting where it is impossible to unlock a smartphone without a combination of either face + pin code or fingerprint + pin code.
- Fix anti-theft systems: Overhaul the Find My iPhone and Google (FRP) systems, which are currently partially compromised and enable temporary bypasses.
For smartphone users:
Android users:
- Use secure models like the Google Pixel 8 and newer smartphones with activated MTE (Memory Tagging Extension).
- Experienced users could consider a custom OS that converts AFU to BFU, and remember to lock the bootloader.
- Use Huawei smartphones with HarmonyOS for the Chinese market.
iOS users:
- Activate Lockdown Mode to limit exploitability.
- Upgrade smartphone hardware as often as it is available.
Digital Forensics Services for Your Needs
Win legal battles with indisputable evidence