Intended readership:
SOC teams, incident response managers, XDR users, MSSPs, and CISOs seeking faster detection with less manual triage.
Available in Group-IB Managed XDR
Introduction
What if every alert told the whole story — no stitching, no guesswork, no duplicates? For most SOC teams, that’s a goal for the future. But with our new industry-first technology, that goal can be achieved now.
Security stacks in mid-sized and large companies are built on three key pillars: endpoint protection, network protection, and email protection. Each of them generates alerts, often hundreds or even thousands a day. Some alerts indicate a genuine attack, others turn out to be false positives, and many simply echo threats that have long passed. All of them land in the SOC, where Tier 1 analysts begin the triage process.
At that point, things often unravel. A genuine attack might trigger multiple alerts across different tools. One analyst might launch an investigation and another could pick up the same case a few hours later. They repeat the same work, unaware of each other’s progress. The duplication wastes time, fragments context, and delays resolution.
To manage the overload, some teams group alerts into incidents. Others configure custom rules in SIEM platforms. But such solutions come with their own trade-offs: they require constant fine-tuning and technical effort, and still things get overlooked. Inevitably, analysts fall back into manual workflows, one alert at a time.
It’s no surprise, then, that the 2024 SANS SOC Survey named “lack of automation and orchestration” as the top operational barrier for security teams. And the impact is not negligible — alert fatigue, missed detections, and burned-out teams who never truly catch up with the workload.
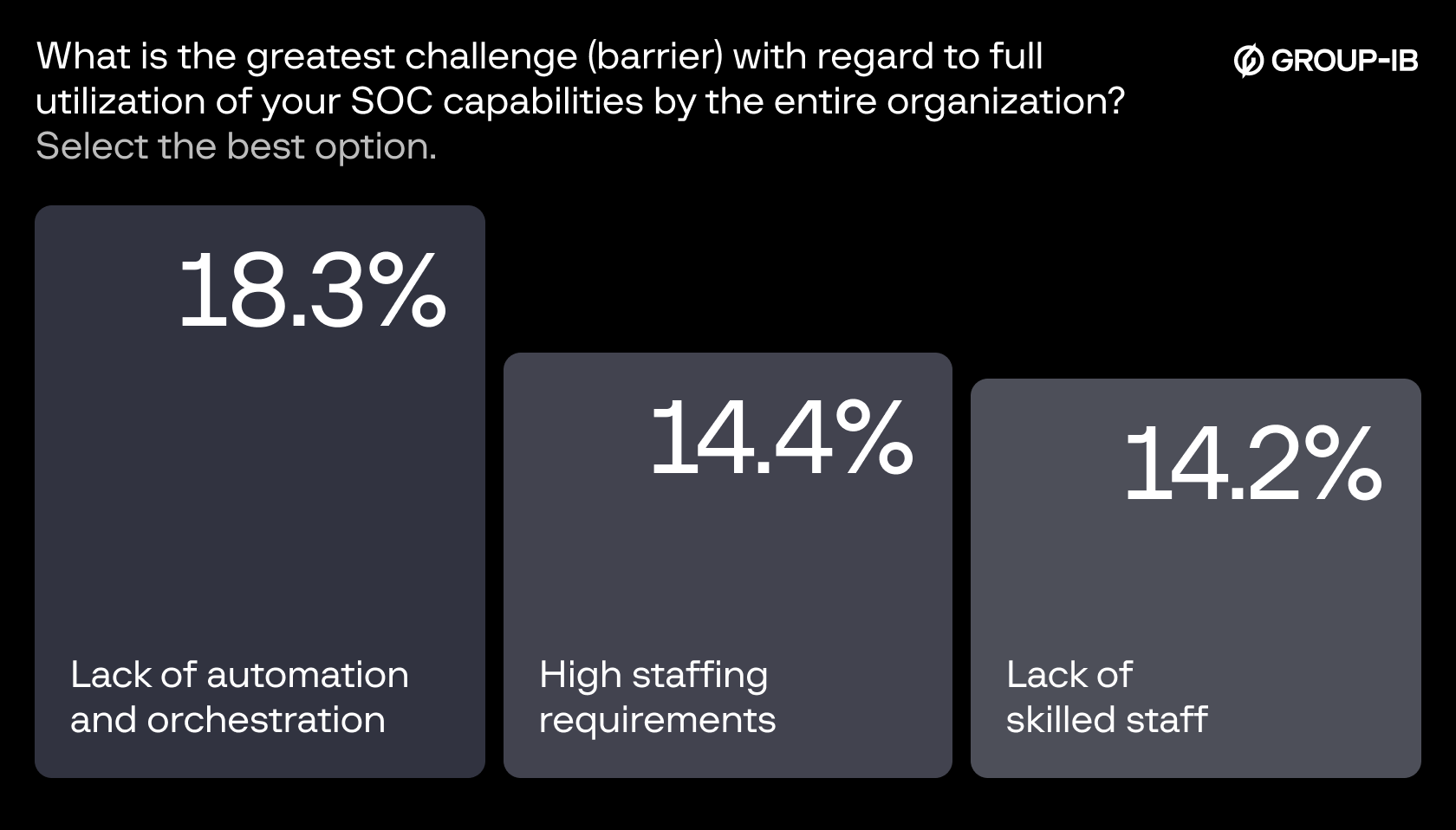
Figure 1. The SANS 2024 SOC Survey identified “lack of automation and orchestration” as the top barrier for SOCs
All three key pain points highlighted in the SANS survey can be addressed with a single feature… Keep reading to find out what it is.
From thousands of alerts to one
Group-IB’s previous alert triage strategy mirrored many in the industry — incident grouping based on correlation rules. But too often critical alerts slipped through ungrouped. Analysts still had to sort through the noise. That’s why we took a new direction.
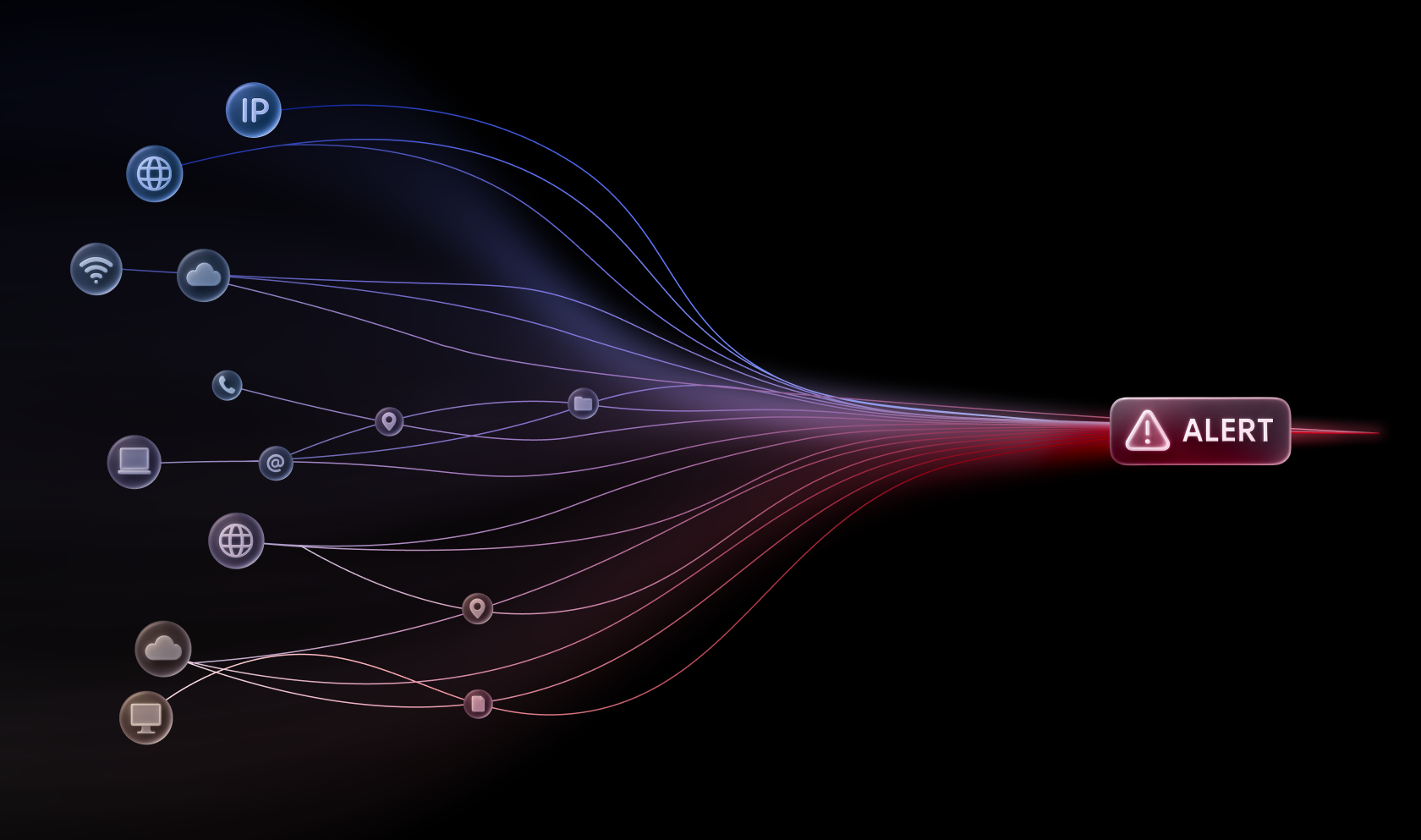
With Smart Alert in Group-IB Managed XDR, all events related to a threat are automatically consolidated into a single alert.
In an internal demo, Group-IB SOC analysts simulated a phishing campaign in a test environment and let it play out without any response over a few weeks. The attack chain was complex. It started with a single phishing email and expanded to include malware deployment, lateral movement, and multiple C2 channels. In a conventional setup, that would have triggered thousands of separate alerts, each one requiring triage.
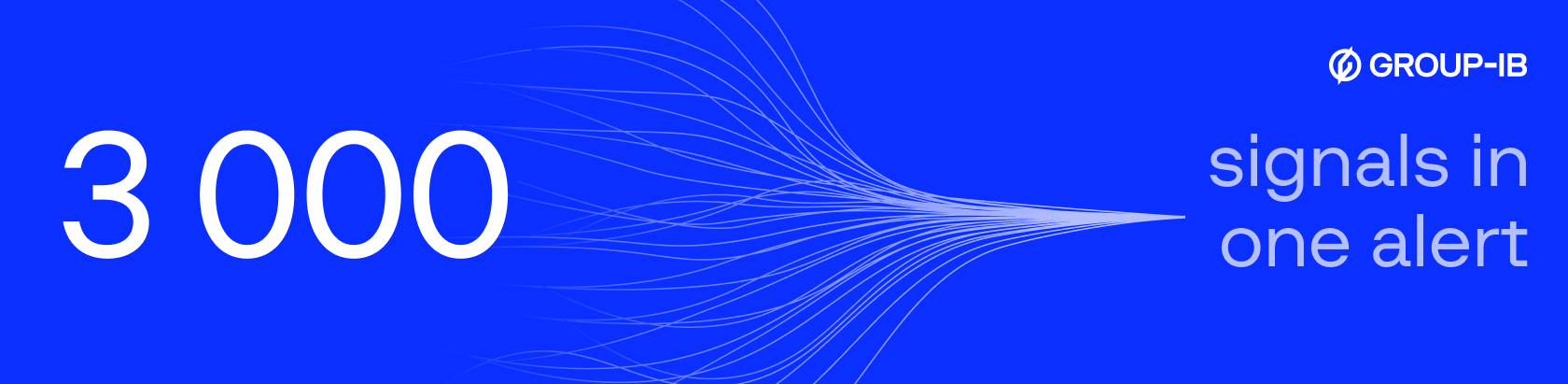
Instead, Smart Alert combined more than 3,000 signals into a single alert. From the initial email to the final malicious process, analysts could trace every step from one place. They saw how the email was delivered, when the user opened the attachment, which host executed the payload, which processes spawned, which suspicious connections were made, and how the malware moved laterally. All the details — the affected hosts, malicious processes, traffic logs, triggered signatures, attack graph, remediation advice, attribution data, and analyst comments — were consolidated into one evolving alert.
Cyber kill chain of a demo campaign (hundreds of notifications in a single alert)
What this means for your SOC
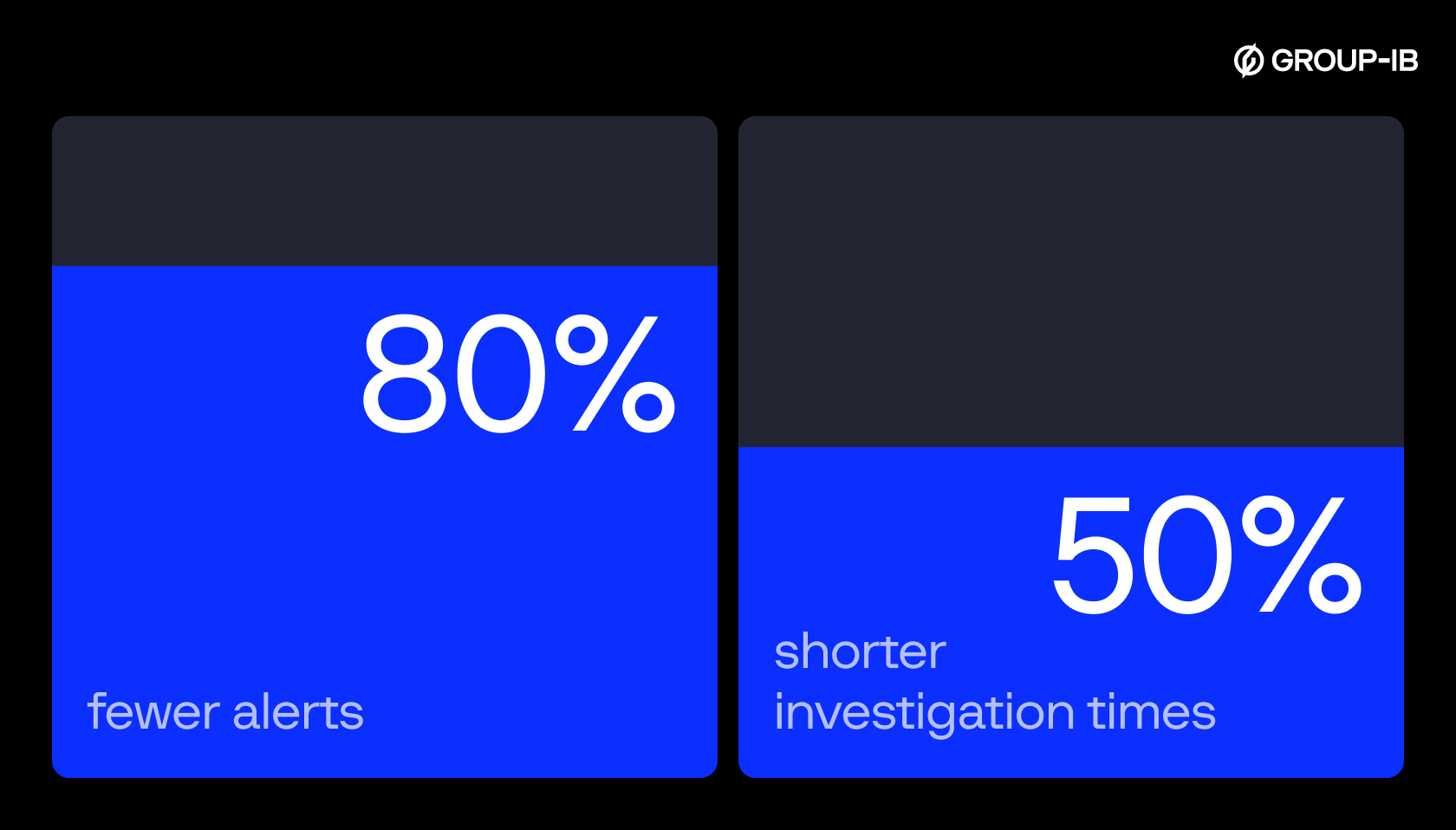
Smart Alert dramatically reduces investigation time and makes detection scalable without scaling headcount. Instead of spending hours connecting dots across dashboards, analysts start with a complete picture — one that updates itself as the attack unfolds. The new feature cuts the number of alerts by up to 80%, based on early deployments. With fewer alerts and a clearer context, teams see investigation times cut in half, fewer missed links between signals, and higher productivity without the need for more people or tools.
Crucially, Smart Alert ensures that security posture scales alongside business growth. In traditional setups, more endpoints mean more alerts. But with Smart Alert, the alert count no longer rises linearly with infrastructure size or attack frequency. One alert can tell the story of one incident, regardless of how many endpoints are involved or how long the activity spans.
Our solution also addresses the human challenges of working in a SOC: burnout, cognitive overload, and inconsistency. By consolidating alerts and preserving context across shifts, Smart Alert supports training, reduces the number of errors that can occur, and keeps teams focused on genuine threats instead of alert hygiene.
From static noise to evolving signals
Traditionally, alerts are static — frozen snapshots triggered by detection systems. After they’ve been created, they don’t evolve, even when more context becomes available. Analysts are left stitching together partial clues, juggling logs, dashboards, and internal messages, trying to reconstruct what really happened.
Smart Alert in Group-IB Managed XDR upends that model. It enables all alerts to evolve over time. When new signals come in — whether from network traffic, endpoint telemetry, email activity, or Threat Intelligence — they don’t generate alert noise. Instead, they enrich the original alert in real time, pulling in context, evidence, and historical analyst notes. Even if an alert is already closed, Smart Alert reopens it automatically when it comes across signs of the same threat. This means that no critical context is lost and that no analyst has to start from scratch.
Smart Alert also gives SOCs a more meaningful lens to alert resolution. Instead of prioritizing speed alone, it emphasizes threat elimination. Smart Alert ensures that resolution truly reflects a neutralized threat. If fresh detection data indicates continued malicious activity, the system automatically reopens the case and prompts further investigation. Only when the threat remains inactive for 48 hours is the alert considered fully resolved.
What makes Smart Alert smart
At the heart of Smart Alert is an AI-driven engine that analyzes each new detection in real time and searches for matches among existing alerts. It connects logs, artifacts, indicators, context, and timelines to build a unified incident view — not across dashboards but in a single, living alert. And while the option to group manually will remain in Managed XDR, most teams won’t need it.
Smart Alert isn’t just driven by AI, it’s also tested by our analysts. Group-IB’s SOC team uses the feature daily as part of its managed detection and response services. Feedback from live operations is continuously looped back into the product. Every detection model and correlation pattern is tested against live threats and refined by both machine learning and expert oversight.
A step toward SOC automation
Smart Alert is only the beginning as we continue to move toward making more and more cybersecurity processes smart and AI-powered. As part of Group-IB Managed XDR, Smart Alert works seamlessly across endpoint, network, and email layers. It scales with your business and sharpens with every detection. And unlike systems that require constant fine-tuning, Smart Alert adapts to you automatically.
As your infrastructure grows, so too will the number of hosts and alerts. Without automation, that growth quickly leads to rising costs, expanding workloads, increased risk, and the pressure to scale your team. Every SOC eventually reaches a point where manual processes can’t keep up. Smart Alert is a critical capability that addresses all these challenges at once.
Instead of waiting for complexity to overwhelm your operations, take a proactive step toward automation. Give your team the visibility, control, and confidence they need — all in one place.
Smart Alert
It is now available for all Group-IB Managed XDR customers. If you're ready to see how one alert can tell the whole story, we’d love to show you what’s possible.