Setting the crypto world ablaze
In the eyes of most regular Internet users, the world of cryptocurrency has always been shrouded in a vale of mystery. That said, the allure of potential financial gain has been sufficient to appeal to millions of people worldwide. The cryptocurrency world also attracts criminals trying to capitalize on people’s lack of experience and awareness.
There are now thousands of cryptocurrencies in circulation, which creates countless opportunities not only for legitimate users but also for cybercriminals. One of the most common techniques nowadays is a crypto-related phishing scam involving a type of malware known as a drainer. How is this malware leveraged and why is its use on the rise?
Group-IB’s High-Tech Crime Investigation department has uncovered details about drainer-related schemes and infrastructure that will help users and organizations to identify malicious websites and secure their assets.
This blog post describes the case of Inferno Drainer, a notable phishing operation that functioned under the scam-as-a-service model. In November 2023, the team behind the drainer announced in their Telegram channel that the malware was shutting down for good, after a widespread campaign targeting cryptocurrency wallet providers that left a massive amount of financial damage in its wake.
In line with the company’s zero-tolerance policy to cybercrime, Group-IB’s Computer Emergency Response Team issued proactive notifications to cryptocurrency brands whose name and likeness was used to feature on the sophisticated phishing pages that were created as part of the Inferno Drainer scam-as-a-service scheme.
What is Inferno Drainer?
Inferno drainer is a sophisticated multichain crypto wallet-draining malware that has made headlines by exploiting the vulnerabilities of crypto users through an elaborate scam-as-a-service model. Active from November 2022 to November 2023, Inferno Drainer operated by luring victims to phishing websites that mimicked trusted cryptocurrency platforms, tricking users into connecting their wallets to a malicious infrastructure.
At its core, Inferno Drainer used advanced malicious scripts to spoof popular Web3 protocols, including Seaport, WalletConnect, and Coinbase. These scripts were cleverly embedded into phishing pages designed to look like genuine crypto token projects. When users connected their wallets and authorized what they believed were legitimate transactions—often in the guise of collecting free airdrops—the malware covertly initiated fraudulent transactions. This enabled cybercriminals to drain the victim’s assets without raising immediate suspicion.
Although the developers announced the shutdown of Inferno Drainer in November 2023, Group-IB later discovered that its user panel for cybercriminals remained active well into January 2024. This lingering presence underscores the persistent threat posed by Inferno Drainer and the need for constant vigilance and robust security practices in the crypto ecosystem.

Figure 1. Screenshot of post in the Inferno Multichain Drainer Telegram channel from November 26, 2023.
As if from Dante’s imagination
Inferno Drainer started being used in the wild in November 2022 and within a year became one of the biggest drainers worldwide.
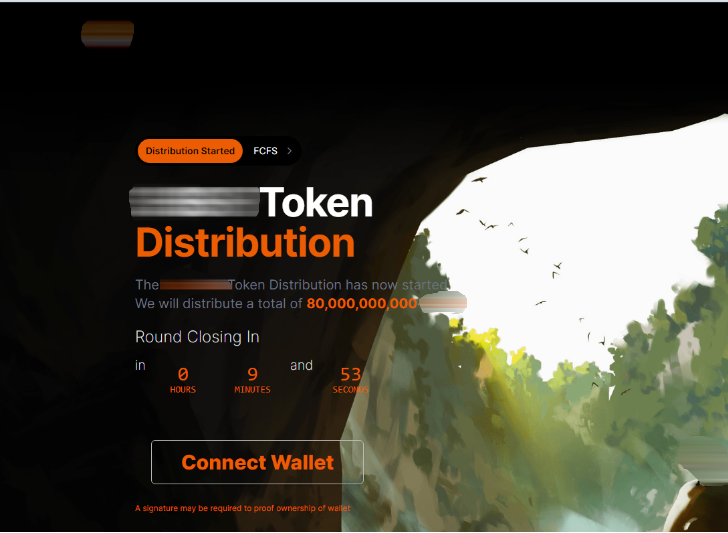
Group-IB’s sector-leading Threat Intelligence platform detected in excess of 16,000 unique domains that were linked to Inferno Drainer’s phishing operations, with more than 100 individual cryptocurrency brands having their name, brand logo, and other intellectual property imitated. As reported by Scam Sniffer, at least USD $80 million in assets was stolen as a result of Inferno Drainer’s activity, making it the most prominent crypto drainer of the past year.
Inferno Drainer operated under the scam-as-a-service model. After luring potential victims in with phishing sites that impersonated crypto brands, the cybercriminals also spoofed popular Web3 protocols such as Seaport, WalletConnect, and Coinbase to initiate fraudulent transactions.
Seaport, as described on its website, is a Web3 marketplace protocol by OpenSea, created for safe and efficient NFT trading. WalletConnect and Coinbase are protocols that allow self-custody crypto wallets to connect to decentralized applications (DApp) in Web3. Once a user approves a connection request from a DApp (via WalletConnect), the DApp can send transaction requests to their wallet, which must also be approved manually in the wallet.
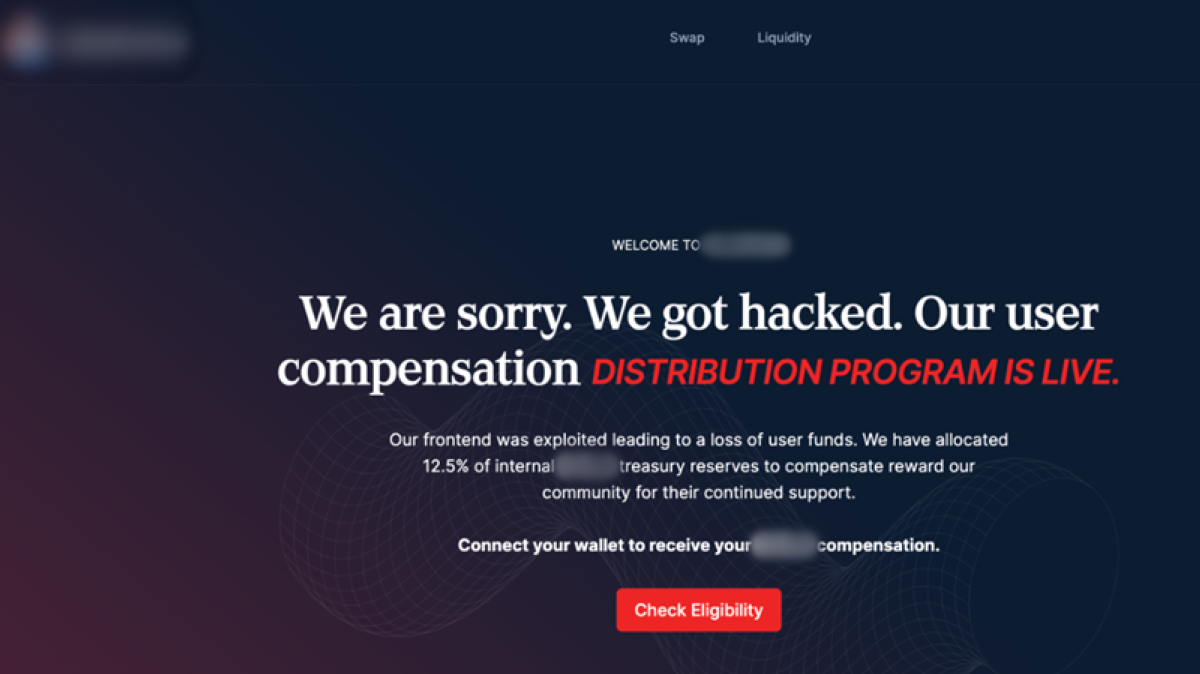
Once the connection with the wallet is secured, Inferno Drainer spoofed these protocols under the guise of various DApps for the purpose of initializing malicious transactions. Users are requested to link their accounts and accept a transaction in order to claim a prize or other financial reward, but in doing so, they open themselves up to receiving fraudulent transaction requests from the drainer’s operators.
The allure of potential riches, which forms a key part of the content presented to victims on phishing websites, makes users connect their wallets to the attacker’s infrastructure. The malware was placed on sites that are disguised as official crypto token projects and spread on X (formerly Twitter) and Discord.
The most popular tricks used on phishing websites by cybercriminals to fool potential victims into connecting their cryptocurrency wallet include:
- Sites offering to give away free tokens (airdrops), with text that included claims of:
- Exclusive airdrop
- First ever company airdrop
- Last company airdrop
- The biggest airdrop
- Encouraging the potential victim to mint NFTs and claim the rewards.
- Claim a reward for issues or disruptions faced by the company, such as:
- A company was hacked
- The company’s assets were frozen and are now available again
Apart from that, the Inferno Drainer team regularly provided a free service for creating and hosting phishing websites. This wasn’t the case all the time, however, as Group-IB investigators saw cases when the scam service’s administrators demanded 30% of assets stolen as a result of phishing attacks carried out on websites created and hosted by the developers.
As is the case with other “X as a service” schemes, these phishing websites were designed for customers who were able to attract victims to phishing websites but either lacked the technical proficiency to create and host a website or they simply did not want to do this task themselves.
The blazing eye of the Inferno

Figure 3. Detailed overview of Inferno Drainer’s workflow.
So how did this scam as a service work, from the stage of inception to funds being transferred to the cybercriminals? Here’s a step-by-step description of the crypto-scam scheme involving Inferno Drainer:
- Inferno Drainer’s developers gave their customers access to a user panel and Telegram channel. They also provided the software and phishing websites (on request).
- Customers placed drainer on the website and spread these websites through X (formerly Twitter), Discord, and other social media.
- Victims connect their wallets by scanning a QR code contained on these phishing websites.
- Drainer checked the victim’s most valuable and easiest to transfer assets.
- The software initializes a malicious transaction.
- Victims confirmed the transaction.
- Assets were transferred to criminals. Of the stolen assets, 20% is transferred to Inferno Drainer developers and 80% to customers.
It is important to note that the victim’s consent was required for every chain change and transaction initiated by the drainer. In some cases, the drainer’s operators could wait for an extended period of time before initiating the first fraudulent transaction and check minimum wallet values. If it found that the assets were below $100, then a transaction was not initiated.
This functionality is likely explained by the fact that many crypto users first connect a wallet containing a small amount of assets to check if the website is legitimate. After verifying, they may connect a wallet with larger funds. This method lets the drainer catch a more valuable account.
Telegram channel
The scammers promoted their services through a Telegram channel called Inferno Multichain Drainer.

Figure 4. Screenshot showing the description of the Telegram channel Inferno Multichain Drainer
The only account specified in the channel description is @Mr_inferno_Drainer (Telegram ID: 5600090206). Presumably, @Mr_inferno_Drainer is a developer and one-person tech support team.
The first public mention of Inferno Drainer dates back to November 5, 2022, when the Telegram channel was created.

Figure 5. Screenshot of post from Inferno Multichain Drainer Telegram channel dated November 5, 2022
In the beginning, the Inferno Drainer developer also used the Telegram account @Inferno_Drainer_AdBot (id5655532486) for advertising (until mid-February 2023).
Inferno Drainer’s Panel
The scammers behind Inferno Drainer also used the website inferno-drainer[.]com, which contained a user panel.
The domain name inferno-drainer[.]com expired on 10 December 2023. But a new domain name that hosted the panel was found – dfgdfgqg[.]com.
Inferno Drainer ceased activity in late November 2023, although the panel is still live. Group-IB experts believe that this may have been done to give customers the opportunity to close their accounts and transfer any assets.
The Group-IB Threat Intelligence platform detected a Telegram message posted in August 2023 in which the Inferno Drainer mastermind sent instructions to customers and mentioned inferno-drainer[.]com.
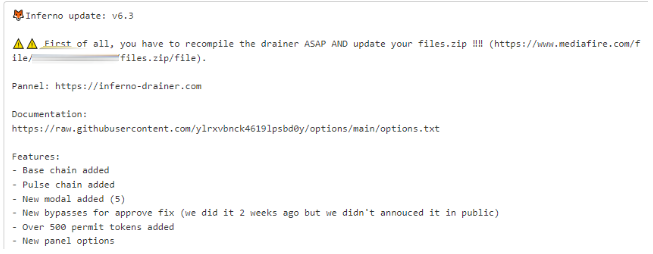
Figure 6. Text body of August 2023 Telegram post
Members of the Group-IB High-Tech Crime Investigation unit conducted a thorough analysis of Inferno Drainer’s panel, in an attempt to uncover more clues about how this prominent scam-as-a-service scheme operated.

Figure 7. Screenshot of Inferno Drainer’s panel dated from the first week of December
The main page shows customers their statistics: number of connections (the victim has connected their wallet on a phishing website), successful hits (if the victim has confirmed the transaction) and the price of the stolen assets.
Every customer of the scam service could customize the drainer’s features in the “storage config” section:

Figure 8. Screenshot detailing how users could customize Inferno Drainer.
After that, the panel would compile a unique JavaScript (JS) for the customer.
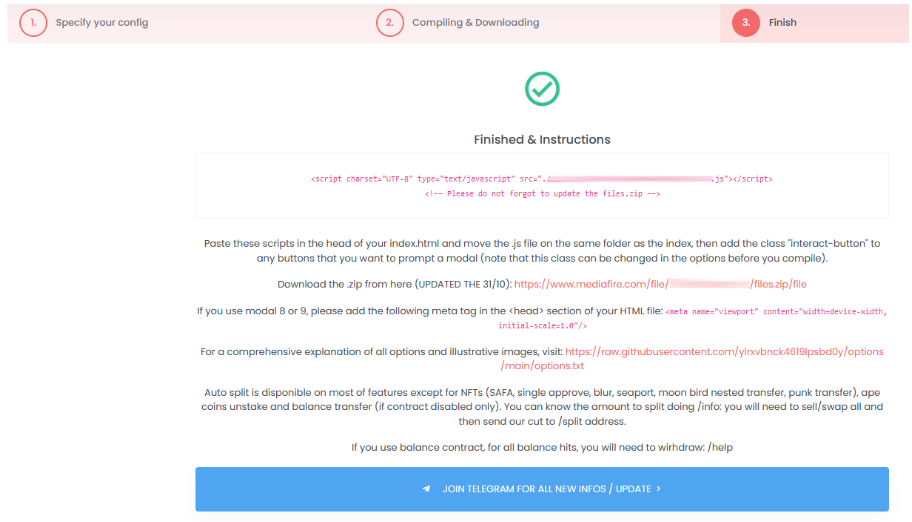
Figure 9. Screenshot from Inferno Drainer’s panel demonstrating JavaScript generator
The JS name contained a Universally Unique Identifier (UUID), which means that a unique JS was created for each customer. As a result, researchers are able to identify and distinguish between different Inferno Drainer customers.
After the JS was compiled, the customer could view the following instructions and links:
- A ZIP file named “files.zip” with scripts (more information about the file will be provided below)
- Description of where these scripts should be located (i.e., in the website’s head section)
- Link to the documentation about drainer customization.
The documentation was located in the GitHub repository belonging to the user with the nickname ylrxvbnck4619lpsbd0y. Given that there was only one upload to this account, Group-IB experts believe that the account was created solely for the purpose of sharing these files.
How did Inferno Drainer work?
This section covers the websites and main techniques used by the threat actor behind Inferno Drainer and their customers. A list of phishing websites connected to Inferno Drainer was mentioned by ScamSniffer in their report into the malware.
Let’s start by analyzing one of these websites: shardeum-whitelist[.]com.
The website had the same domain registrar as inferno-drainer[.]com: Tucows Inc.
The IP addresses were 89.117.27.137 and 2a02:4780:11:1084:0:212d:6d2c:10 (both are hosted by Hostinger).
Using Group-IB’s patented Graph Network Analysis tool, the company’s High-Tech Crime Investigation department identified other similar phishing websites by the abovementioned IP addresses: lensprotocol-register[.]com, lensprotocol-whitelist[.]com, base-whitelist[.]com, scroll-wl[.]com, sei-whitelist[.]com, zk-sync-register[.]com, zk-sync-whitelists[.]com, and layer-zero-register[.]com.

Figure 10. Connections to 89.117.27.137 and 2a02:4780:11:1084:0:212d:6d2c:10. Source: Group-IB Graph Network Analysis tool
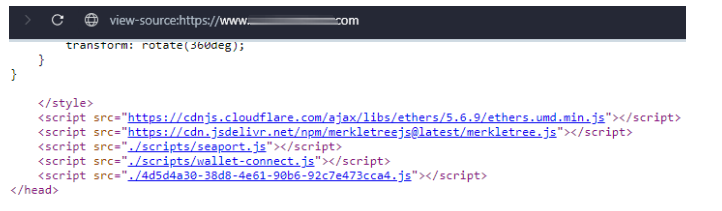
What is worth noting is that every abovementioned website contained the script kuzdaz.github.io/seaport/seaport.js in the “head” section. This script is a part of Inferno Drainer that must be placed on each phishing website.
The script was initially located at kuzdaz.github.io/script/seaport.js. Later, seaport.js was located on websites directly, without using GitHub repositories.
At the time of writing, the GitHub user “kuzdaz” does not exist.
As per data available via urlscan.io, kuzdaz.github.io was used to load the malicious seaport.js script on more than 500 unique websites.
The earliest created website containing a link to kuzdaz.github.io, was zkcync[.]xyz. This website contained another JS: coinbase-wallet-sdk.js (SHA-256 883afe469b8706938f681b78750974b5daa373befe51f91eba6e9cb0a18d8238), which led to kasrlorcian.github.io.
The user with the nickname kasrlorcian has only this script in their repository. Group-IB experts believe that the account was created solely for the purpose of sharing these files.

Figure 11. Screenshot of Github user kasrlorcian
Group-IB’s Threat Intelligence platform detected more than 350 websites containing the malicious coinbase-wallet-sdk.js script.
At some point, the Inferno Drainer developer added another script (wallet-connect.js) and started spreading all three scripts (seaport.js, coinbase.js and wallet-connect.js) in a separate ZIP file on a file sharing site. It allowed the developer to stop using GitHub repositories.
These scripts masquerade as popular Web3 protocols (Seaport, WalletConnect and Coinbase). The original protocols serve as bridges between various parts of the crypto chain, helping users to trade tokens (including NFT) or connect wallets to DApps (such as Uniswap and PancakeSwap). Inferno Drainer spoofs these protocols, then initiates a malicious transaction, and after getting users’ confirmation,where assets are redirected to the threat actors.
Some of the phishing websites leveraged by Inferno Drainer could contain multiple malicious scripts (as evidenced in Figure 14 below). In total, Group-IB Threat Intelligence discovered more than 14,000 websites containing malicious scripts that impersonated the Seaport protocol, in excess of 5,500 websites containing scripts that spoofed WalletConnect’s protocol, and more than 550 websites that featured scripts designed to impersonate Coinbase protocol.

Figure 12. Screenshot from one phishing site used by the threat actors
Let’s go back to the instructions for customers detected in the Telegram message. The instructions contained a link to a file on a file sharing site.

Figure 13. Screenshot of a .zip file with malicious scripts on a file-sharing site
This is a ZIP file “flies.zip”, dated August 2023, (SHA-256 d72c65832b78eac498973efbc617486ea981cb6a2efe477e2887ac4142a50c1e) containing four JavaScripts.
- coinbase.js (SHA-256 8c1ea67e021fe82120a99d3bc33c92dec4845f5af94f192e17104e14ca04ecee)
- seaport.js (SHA-256 7e9952bf40a202b4d047ea5157e5c67930667d29749dcecfd20df0fc1a40f276)
- old-wallet-connect.js (SHA-256 c45901852230a3d2c67eae5fdf7204ba6afb7432377ec25157d838b1663d5b96)
- wallet-connect.js (SHA-256 88930dc583b10fe369e8f3ec632c819d54c6cc6a812087eba17b9b7db6a86cba)
These scripts are the key components of phishing websites related to Inferno Drainer.
There is another file called files.zip with updated scripts, which was detected on the panel inferno-drainer[.]com in December 2023 (SHA-256 c000fe851a6c81056e617d3132bcdc741b8a9a715f59b3d0f304816ffc8f397c).
- coinbase.js (SHA-256 8c1ea67e021fe82120a99d3bc33c92dec4845f5af94f192e17104e14ca04ecee)
- seaport.js (SHA-256 f7052689181410efcf4c857c8a0eeb8bf911ff9958a88884063edf5d43578437)
- wallet-connect-v2.js (SHA-256 56ee391037568f8f72a191635288afe7274cb7cb2439d1cdadc407be07b3925c)
- wallet-connect-v3.js (SHA-256 3c141574427ff088849cebd2fde1bde711158020be7edb496bcf41b8c10d5231)
The Group-IB Threat Intelligence platform detected more than 16,000 unique domains using these scripts, and at least 100 crypto brands had their brand name and likeness appropriated on phishing websites that contained Inferno Drainer.
The earliest website discovered to contain one of these scripts was dated May 15, 2023.
Let’s take a deep dive into one of the phishing sites that contained Inferno Drainer.
This website contains seaport.js and wallet-connect.js in the head section. It also contains a unique script with the following settings: 4d5d4a30-38d8-4e61-90b6-92c7e473cca4.js
Another typical feature of phishing websites belonging to Inferno Drainer was that users cannot open website source code by using hotkeys or right-clicking on the mouse. This means that the criminals attempted to hide their scripts and illegal activity from their victims.
Users who wish to bypass this source code limitation, need to change the name of the website to view-source:websitename.
How cybercriminals use Inferno Drainer for phishing attacks
Phishing remains one of the most common attack vectors in the cyber world, and Inferno Drainer has elevated the art of deception to a new level. It is difficult to understand all about Inferno Drainer. However, cybercriminals utilize expertly crafted phishing sites that closely resemble legitimate crypto portals. These sites use high-quality graphics, accurate logos, and persuasive language to convince victims that they are accessing official platforms.
The process typically unfolds as follows:
- Deceptive Landing Pages: Websites offering “free tokens” or “exclusive airdrops” entice users to connect their wallets.
- Spoofed Web3 Protocols: Scripts such as seaport.js, wallet-connect.js, and coinbase.js mimic well-known protocols to create a facade of legitimacy.
- Consent Manipulation: Users are tricked into approving transactions that they believe are for rewards, while in reality, their assets are being siphoned off.
Key features of Inferno Drainer malware
The ingenuity of the Inferno Drainer lies in its combination of technical sophistication and user-centric deception. Here are some of its defining features:
- Scam-as-a-Service Model: This approach lowers the barrier to entry for cybercriminals by offering ready-made phishing kits and customizable scripts.
- Phishing Website Proliferation: Over 16,000 unique domains have been linked to Inferno Drainer, with more than 100 crypto brands impersonated.
- Sophisticated Scripting: The malware uses spoofed versions of popular Web3 protocols to initiate unauthorized transactions.
- Delayed Attack Mechanism: In some cases, the malware waits for a more lucrative wallet to be connected before initiating the drain.
- Revenue Sharing: A unique feature where a percentage of the stolen assets is allocated to the malware developers, ensuring continuous innovation and support.
- User Interface Panel: A dedicated control panel that allows cybercriminals to monitor and manage their phishing operations efficiently.
Conclusions and recommendations
Before its closure, Inferno Drainer was one of the biggest drainers in the criminal cryptocurrency market. The software placed a heavy toll on the crypto industry and was used to steal more assets than the next three most popular drainers combined.
Inferno Drainer has now been shut down by the developer, but its prominence over the past year has opened up a wide range of possibilities for criminals to get rich. Its customers are still around, and there is nothing to suggest that their appetite for stealing tokens and NFTs has waned. As a result, they will most likely look for other draining scam-as-a-service schemes to participate in. Ultimately, the amount of phishing websites in the crypto world is essentially countless.
The dangers will only get worse. In-depth investigations and bringing criminals to justice are the only way to prevent future attacks. It is crucial that victims file cases about the attacks they experienced with the relevant law enforcement agencies.
Best security practices to protect crypto wallets from drainers
While analyzing all about Inferno Drainer, Group-IB realized it is important for users to be careful when connecting your wallets, and don’t chase free tokens and NFT giveaways called airdrops because, most likely, these fake giveaways will be posted on phishing websites. Trust only official websites for tokens. You can find them at https://coinmarketcap.com.
If you fall victim to a cryptocurrency crime, you should do the following:
- Transfer any remaining assets to another wallet.
- Save the phishing URL address and take a screenshot of it.
- Make a record of how you got to the phishing website and take a screenshot of it.
- Save your browsing history.
- Save any data relating to malicious cryptocurrency transactions.
- Contact your local law enforcement agency.
- Get in touch with Group-IB Cyber Investigations for case assessment and investigation. The preliminary assessment is free of charge. It allows our specialists to evaluate the chances for a successful completion of the investigation. Based on the results of the assessment, we announce the expected results and the scope of work.
Before connecting your wallet to a website, take the following steps:
- On whois.com, check when the website was registered. If the website was created less than six months ago, it is most likely fraudulent.

Figure 15. Screenshot of phishing website leveraged by Inferno Drainer customer, highlighting its creation date.
- Check the official website and social media for the token mentioned on the website. You can ask its official representatives whether the resource is legitimate.
- Never share your private keys or seed phrases.
- Be cautious about granting wallet permissions, especially if they seem overly broad or unnecessary.
- Check the source code of the website. If the right mouse button and hotkeys don’t work, use view-source:websitename. If you find seaport.js, wallet-connect (-v2 or -v3 and etc).js or coinbase.js, leave the website immediately.
- Be careful if you see scripts with similar names, as it could be other crypto drainers, with their own scripts.

Figure 16. Screenshot showing code fragment linking to seaport.js and wallet-conect.js
Identify and neutralize cybercriminals attacking your organization
Eliminate threats to your revenue, property and reputation with Group-IB High-Tech Crime Investigations