Intended readership
CISOs, Incident Response teams, SOC managers, IT leaders, MSSPs
Introduction
Once upon a time, email threats were easy to spot. The messages were full of spelling mistakes, poor formatting, and obvious malicious links. Security tools flagged them immediately, and basic awareness was enough to avoid falling into the trap.
That is no longer the case.
In 2025, attackers get in through legitimate conversations, known email addresses, and perfectly clean headers. While your security team celebrates dashboards full of blocked phishing attempts, sophisticated attackers have moved on to a strategy that renders traditional email security solutions almost useless.
The biggest threat to your organization’s inbox in 2025 isn’t phishing with a login form. It’s a familiar-looking message seemingly sent by a partner that delivers an infostealer. Most email security tools won’t intercept it, and by the time it’s detected, it may already be too late.

Infographic: Email threat statistics
Why business email compromise evades conventional security tools
Group-IB experts often witness this pattern in pilot projects: organizations rely on security solutions that excel at spotting obvious phishing links, but these represent only a fraction of the actual threats. When phishing leads to fake login pages, it’s relatively easy to spot and mitigate the attack through password policies, MFA, and user awareness. Such incidents generate alerts and dashboard metrics that create an impression of effective defenses.
Sophisticated attacks, however, exploit fundamental limitations, as detailed below.
AI has weaponized deception beyond recognition: The most critical factor that makes BEC attacks nearly invisible is artificial intelligence. Nowadays, threat actors use generative AI to mimic tone, style, and structure based on real email threads, with supernatural precision. By exporting mailbox content and feeding it to tools like ChatGPT, attackers produce flawless, personalized messages that come in mid-conversation, with zero grammar mistakes or unusual phrasing. Traditional systems that analyze email content for suspicious patterns and grammatical errors become meaningless when AI can perfectly replicate communication patterns.
Reputation-based trust models fail: In today’s email attacks, the message often comes from a legitimate business partner’s actual email account, with proper SPF, DKIM, and DMARC authentication. The compromised partner has been communicating with your organization for years, creating perfect reputation scores and trust ratings. Standard systems trust established senders by design and do not scrutinize them. When such accounts are compromised, messages are delivered without scrutiny because they are whitelisted, creating massive blind spots that attackers can exploit.
Antivirus file inspection overlooks sophisticated threats: Email antivirus engines use simplified versions of endpoint protection, with outdated signatures and minimal heuristic analysis. If endpoint protection can’t catch an infostealer, email antivirus won’t either.
URL analysis only catches obvious threats: URL sandboxes detect phishing pages but they are not designed to flag payloads hosted on legitimate infrastructure. Group-IB analysis shows that malicious links often lead to trusted domains like Google Drive, Dropbox, Facebook, Discord, or compromised partner sites hosting malware loaders. As the links direct to trusted domains, sandboxes fail to raise alerts.
Why infostealers represent a fundamental shift
Infostealer attacks don’t make any noise. They get into systems stealthily, without any visible signs of attack such as ransom notes, signs of disruption, or locked screens. Such attacks exploit the trust inherent in business relationships rather than relying on user mistakes. Unlike traditional phishing that results in limited account compromise, infostealers harvest VPN and RDP configurations that offer direct paths into corporate networks.
When credentials are collected and sold on underground forums, eventually they are used by ransomware groups to infiltrate networks, sometimes weeks or even months after the initial breach. Even mandatory password changes often prove ineffective as users usually make superficial modifications like capitalizing letters or swapping digits around.
Use case of a perfect email attack
The following example is based on one of Group-IB’s real-world incident response cases. A company receives a message seemingly from a long-time partner continuing an earlier conversation about quarterly delivery schedules. A familiar supplier document is attached, accompanied by a polite request: “Could you clarify the quantities in line item 7?”
The email passes every security check made by well-known email security vendors:
- Sender authentication: ✓ Verified legitimate account with perfect headers
- Domain reputation: ✓ Excellent trust score based on years of communication
- Content analysis: ✓ Perfect grammar, knowledge of context, no suspicious patterns; tone and style aligned with the partner’s usual communication, thanks to AI
- File scanning: ✓ No known malware signatures detected
- URL analysis: ✓ All links direct to trusted domains
The recipient opens the attachment — after all, they’ve reviewed the supplier’s delivery schedules dozens of times before. Everything looks normal so they provide the requested clarification.
Four months later: Ransomware cripples the entire network. Business operations come to a halt, production lines stop, and recovery costs reach millions. The “familiar” supplier document had been weaponized with infostealer malware that silently harvested VPN credentials, which were later sold to a ransomware group.
The attack succeeded because no traditional security system could distinguish between the legitimate original document and its weaponized twin.
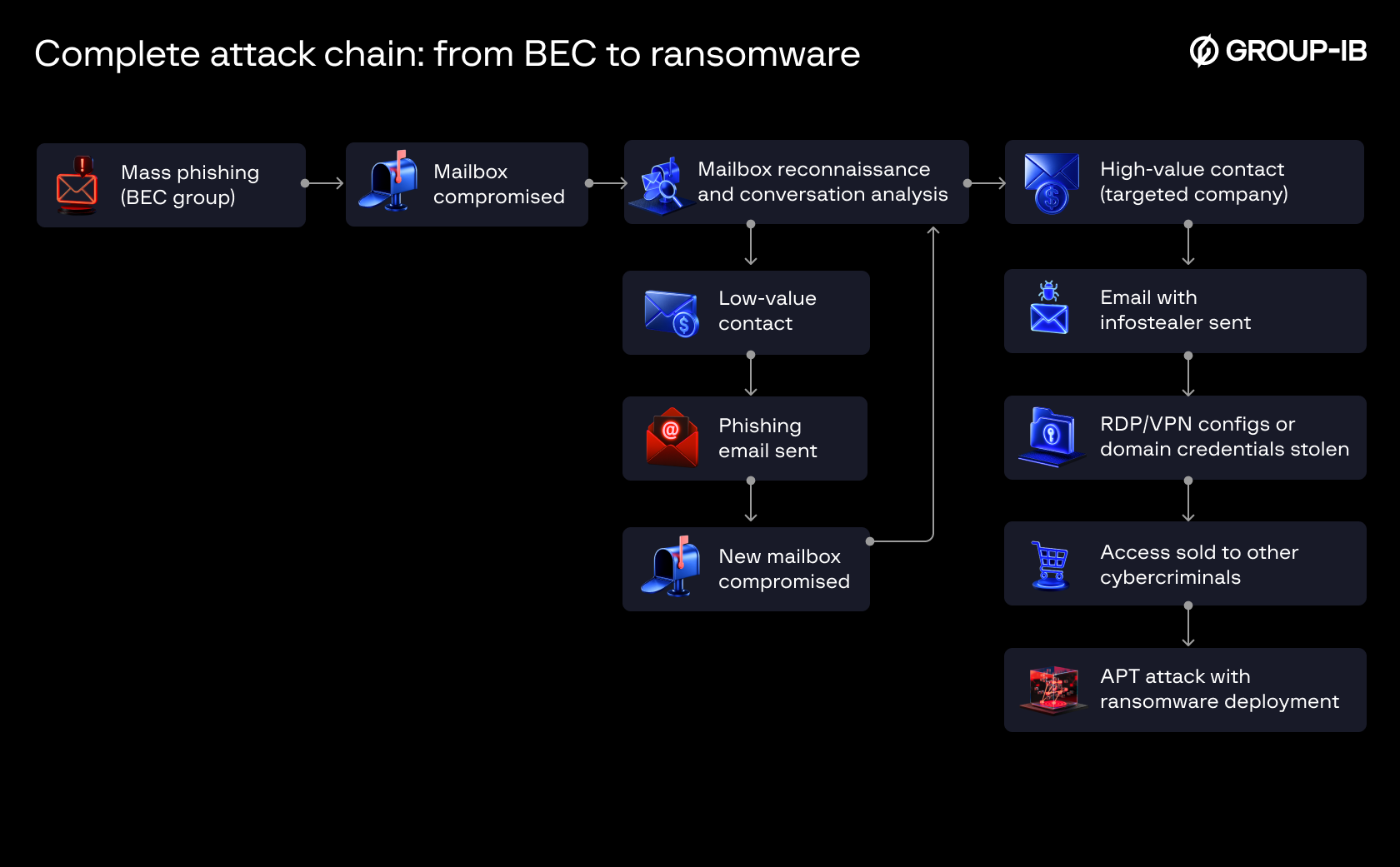
Complete attack chain: from BEC to ransomware
How to ensure real protection against BEC, AI-driven attacks, and infostealers
Group-IB’s Business Email Protection doesn’t rely on deciding whether an email looks suspicious. It assumes the opposite: that attackers will do everything they can to appear legitimate. Whether the threat is written by AI, sent as part of a business email compromise, or delivering infostealer malware, Business Email Protection focuses on the behavior behind the message rather than its appearance.
1. Sandbox-first behavior analysis
Each attachment and embedded link is extracted from the email and detonated in a secure sandbox environment that replicates a real operating system. The sandbox observes what the file or URL does after being launched. If it tries to launch PowerShell, decrypt payloads, establish persistence, or connect to command-and-control infrastructure, the threat is identified and blocked. The approach is crucial for catching infostealers, which often remain dormant until activated on the victim’s system.
2. Protection against AI-generated content
Whether a message is fluent or flawed is irrelevant. Business Email Protection doesn’t analyze grammar or semantics — it examines the impact of interaction. Clicks, downloads, and embedded payloads are all tested for malicious behavior. AI-generated email cannot evade behavioral detection because the analysis occurs during payload execution and not content review.
3. Zero trust for “trusted” contacts
Business Email Compromise attacks exploit compromised but trusted accounts. Most security solutions whitelist such contacts based on reputation and history. Business Email Protection treats every single message as potentially hostile, subjecting even longtime partners to the same rigorous behavioral analysis. If a malicious macro is embedded or remote access tools are triggered during sandbox detonation, the email is blocked regardless of the sender’s reputation.
4. Encrypted file analysis
Attackers often use password-protected archives to evade inspection. Business Email Protection automatically detects passwords within email content or metadata, extracts archives, and detonates payloads in controlled environments. This allows it to stop threats that legacy solutions often miss due to encryption or obfuscation.
5. Post-delivery remediation
If a malicious file is initially overlooked or a threat becomes apparent only after external infrastructure is flagged as dangerous, Business Email Protection’s post-delivery engine can retroactively remove the message from all inboxes. This step is essential for stopping slow-acting attacks or staged compromises that unfold over several days.
6. Correlation with Managed XDR
Every alert and sandbox verdict is correlated with Group-IB’s Managed XDR telemetry. If a user clicks on a file and later shows signs of compromise on the endpoint or unusual lateral movement in the network, analysts can see the entire chain of events. The cross-surface correlation is critical when responding to infostealer infections that lead to account takeovers or ransomware.
Rethinking email security: trust but verify
The way that email threats have evolved in recent years represents a fundamental shift requiring organizations to rethink trust and verification in digital communications. The era of reputation-based security is over. When AI can perfectly mimic legitimate business communications and cybercriminals are able to hijack trusted relationships, traditional email security becomes not just inadequate but dangerously misleading.
Organizations that continue to rely on standard email security approaches will find themselves increasingly vulnerable to sophisticated threats that exploit the very relationships that make business possible. The solution is to verify business communications continuously through behavioral analysis that examines what emails actually do rather than how they look.
Level up your business email security now
Request a live demo to see how behavioral email protection addresses the limitations of traditional security approaches in your organization.