Introduction
In September 2023, Group-IB uncovered a previously unknown Spanish-speaking criminal group, GXC Team, operating a sophisticated AI-powered phishing-as-a-service platform. Targeting users of Spanish banks, GXC Team utilized unconventional tactics that posed a significant regional threat. Initially emerging in January 2023 on Telegram and Exploit.in, GXC Team specialized in developing and selling phishing kits, Android malware, and AI-powered scam tools. Their services included the sale of stolen banking credentials and custom coding for hire, operating under a malware-as-a-service model where customers could purchase phishing resources tailored to mimic bank domains. Notably, their Android malware was designed to intercept OTP (One-Time Password) codes, particularly affecting users of over 36 Spanish banks, governmental bodies and 30 institutions worldwide. Group-IB analysts have detected at least 250 phishing domains attributed to the threat actor and discovered 9 variants of the Android malware.
Despite their tools not being highly sophisticated, GXC Team’s innovative features made them a severe menace to banking security in Spain. This blog post delves into their operational methods, the distinct characteristics of their malicious tools, their attack strategies, and effective defense strategies against such threats.
We prepared the Spanish version of this investigation!
GXC Team criminal business
GXC Team appeared on Group-IB’s radar in January 2023, when they started to offer their criminal services through their private Telegram channel and the underground forum Exploit.in. Their price for the phishing kit ranged from $150 to $900, while the bundle including the phishing kit and Android malware cost approximately $500 per month. GXC Team was particularly focused on developing and distributing phishing kits and Android malware targeting users of Spanish financial institutions, as well as other entities including tax and governmental services, e-commerce, banks, and cryptocurrency exchanges in the United States, United Kingdom, Slovakia, and Brazil.
The GXC Team criminal business comprises of:
- Developing and selling phishing kits
- Developing and selling Android malware
- Developing and selling AI-powered scam tools
- Selling stolen banking accounts of spanish banks
- Coding for hire services
At the core of the GXC Team’s business is a classic malware-as-a-service model where other threat actors paid a monthly fee for either the phishing kit only, or as a bundle with the malicious Android app. The GXC Team then takes care of the rest, setting up and configuring infrastructure and registering domain names to deliver stolen credentials.
After purchasing the services from the GXC Team, other threat actors are usually provided with a fully setup phishing resource, complete with a domain name —typically typosquatting or impersonating a bank’s domain—as well as hosting and a configured phishing kit. They will also be added to a specially created Telegram chat, where a Telegram bot acts as command-and-control (C2) server, sending stolen credentials from the phishing panel to the chat.
What was special about GXC tools?
The main tool of the trade of the GXC Team included custom phishing kits and Android malware. Phishing kits offered by the GXC Team were available for 36 banks operating in Spain and 30 other institutions from other countries. In addition to that, the GXC Team offered Android malware disguised as a banking application designed to intercept OTP codes sent from legitimate banks. Based on Group-IB’s research, this malware was identified to be in use and targeting customers of at least 10 banks currently operating in Spain.
What distinguishes the GXC Team’s tools is not their technical sophistication but several remarkable features implemented that made their tools a significant threat to banking customers in Spain.
Phishing kit and Android malware bundled together
The first notable implementation is the bundling of a phishing kit with a malicious Android application. Unlike typical phishing developers, the GXC Team combined phishing kits together with an SMS OTP stealer malware pivoting a typical phishing attack scenario in a slightly new direction. Instead of just grabbing credentials and other data straight off a phishing page, the malware would prompt its victims to download and install a banking application under the guise of preventing a “phishing attempt”. Once installed by its victims the application will request permissions to manipulate SMS, allowing the attackers to covertly forward SMS from the victim’s device to a Telegram bot controlled by the GXC Team, facilitating the freedom to drain their victim’s bank accounts much easily.

A screenshot of an announcement made by the GXC Team about their SMS OTP stealer targeting Spanish banks on their Telegram chat.
AI-powered voice caller feature in the phishing kit
The developers also integrated an up-to-date AI feature that enables other threat actors to generate voice calls to its victims based on their prompts, straight from the phishing kit. In essence, the victims will receive calls purportedly from their bank, instructing them to provide their two-factor authentication (2FA) codes, instruct them to install apps disguised as malware, or perform any other actions desired by the other threat actors. Employing this simple yet effective mechanism enhances the scam scenario even more convincing to their victims, and demonstrates how rapidly and easily AI tools are adopted and implemented by criminals in their schemes, transforming traditional fraud scenarios into new, more sophisticated tactics.
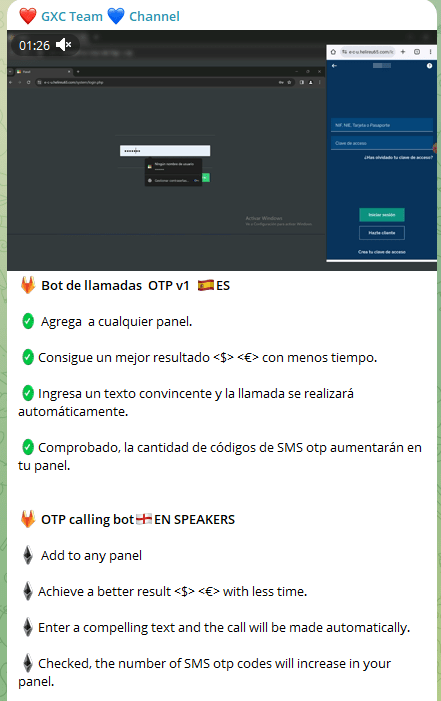
A screenshot of an announcement from the GXC team about the AI-powered voice caller feature on their Telegram channel.
Attack scenario
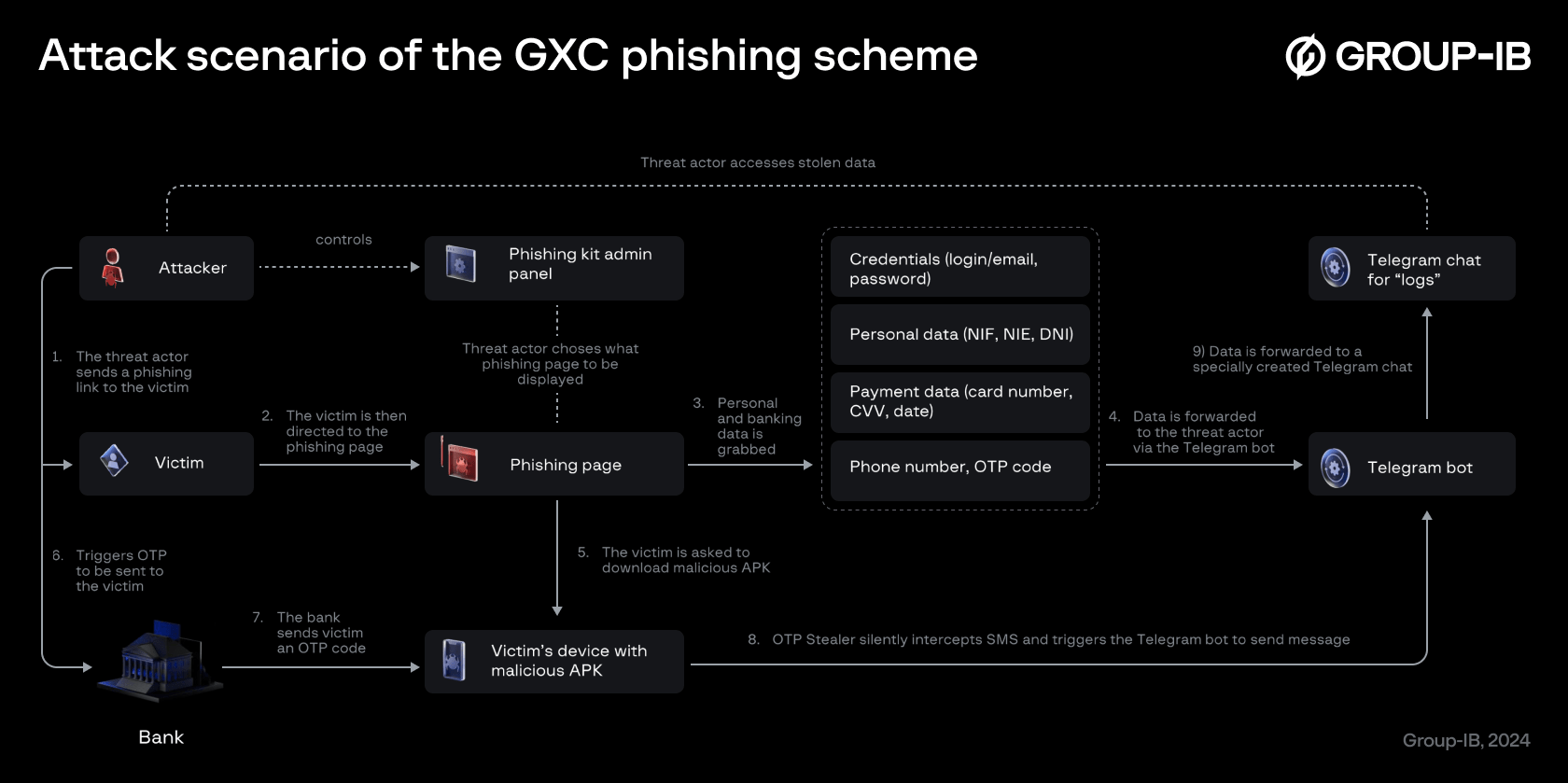
Generalized attack scenario of the GXC Team phishing kit and OTP stealer malware
From their victim’s perspective, the fraud starts from them receiving a phishing lure via a smishing SMS, and continues with following steps:
Phishing path
- The victim is directed to a phishing website via smishing or other way of link distribution.
- Once a victim arrives on the phishing website, they are asked to provide their initial credentials including Spanish Tax Identification Number (NIF, or Número de Identificación Fiscal) login details, or other data along with a password. Simultaneously, the threat actor receives a notification in the admin panel or Telegram chat about the victim’s visit to the phishing website.
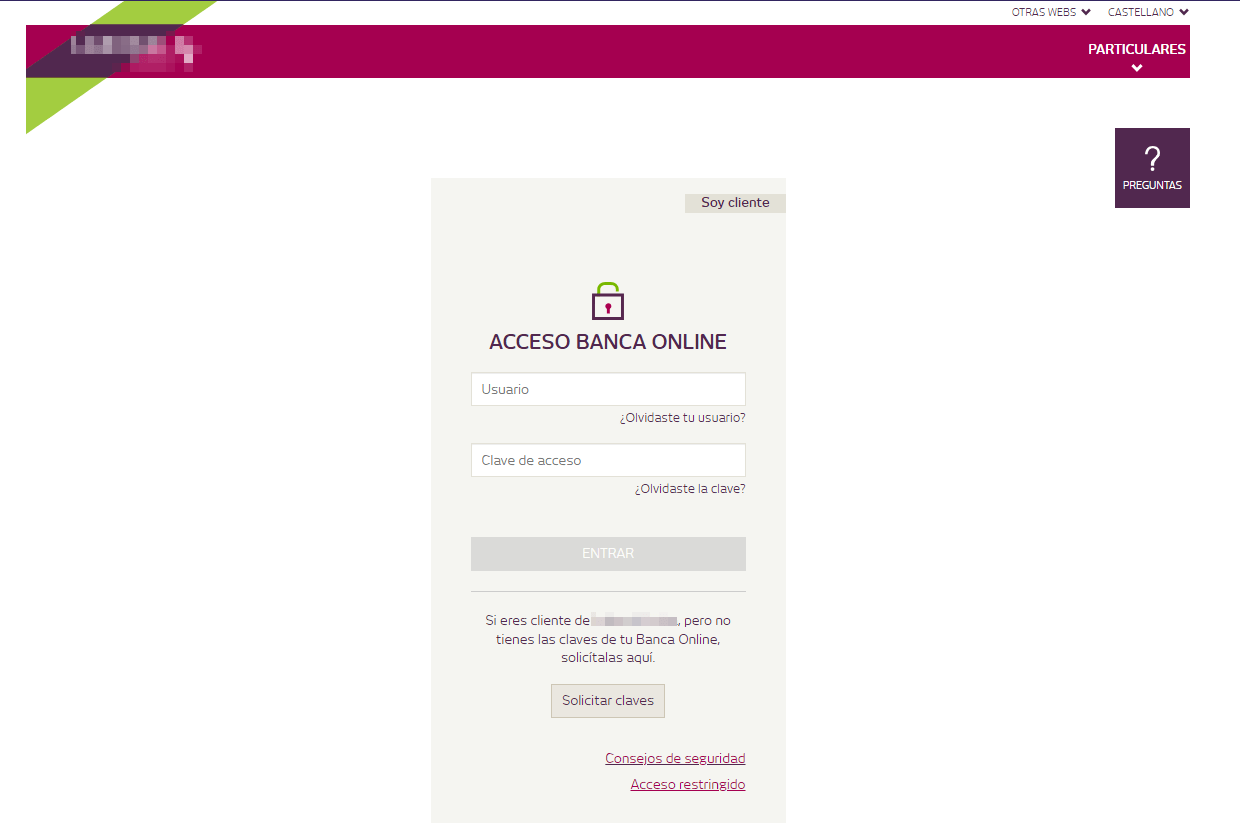
Example of the initial phishing website.
Once these are established, the threat actor will exert full control in real time via a so-called “live panel”—a type of a phishing kit—specifically, administration panel—in which the attacker can manually choose what type of data to request from the victims and subsequently which page to display to them. Based on their victim’s choices, the threat actor is able to request for further personal information, based on this dynamic manipulation strategy.
A screenshot of the live admin panel of the phishing kit.
3. Depending on the impersonated financial institution and threat actor’s choice, its victims may be asked for a photo of identity document (DNI), their physical address, email address, phone number, SMS OTP code, and others. The data then appears in the phishing kit admin panel or is sent to the Telegram chat controlled by the threat actor using the Telegram bot.

A screenshot of a phishing page requesting for DNI (Identity document), using a sample document.
At this point the criminals can also trigger an AI-powered voice caller feature straight in the phishing kit, so their victim will receive an automated call persuading them to provide yet more of their precious data.
Android malware path
For customers of several financial institutions, the con isn’t over yet. The phishing page deceives them into downloading and installing a purported Android banking application under the guise of “preventing “fraud attempts”. Tragically, the victims would instead be downloading malware designed to steal SMS OTPs.
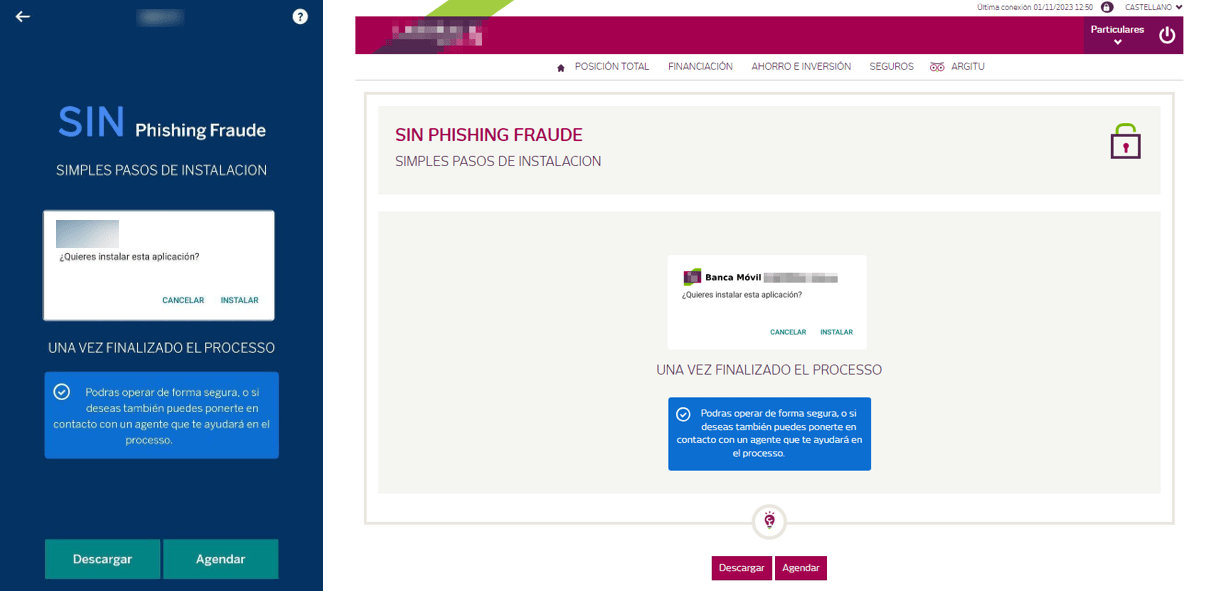
Example of a phishing page asking to its victims to install a “banking app” under the guise of preventing fraud attempts.
4. The malicious APK (Android Package Kit) pretends to be a legitimate bank app using the genuine logo and styles. Upon installing and opening the app the victim is presented with a page (WebView with a hard-coded URL) asking for granting permissions to the app.
An example of a fake app asking for permissions.
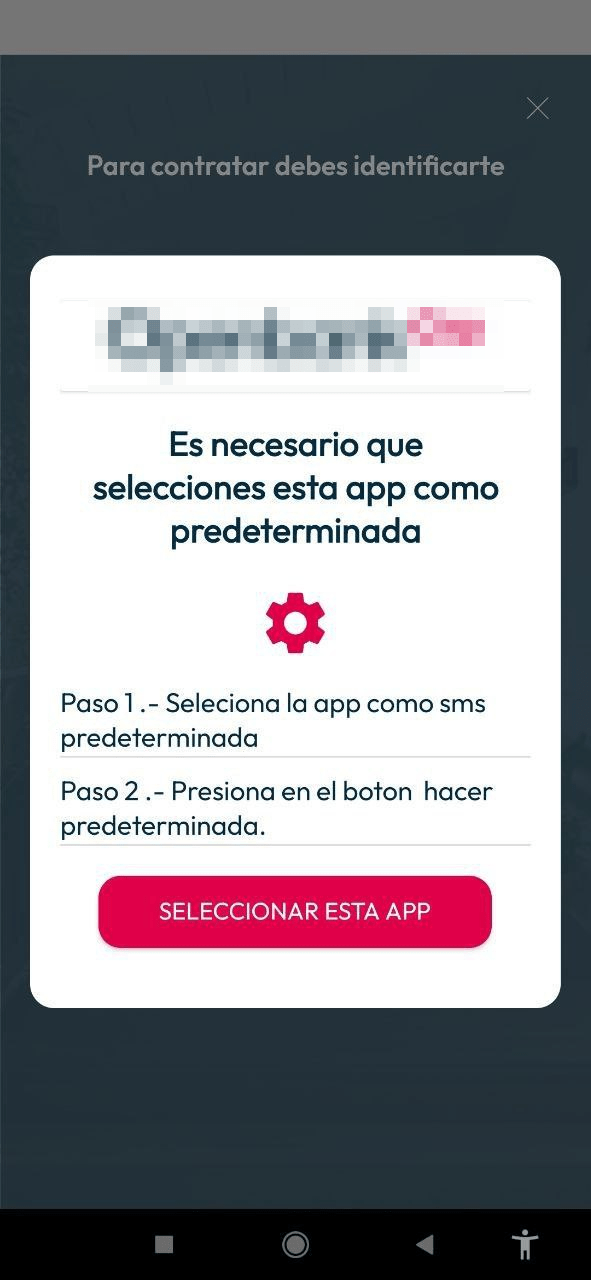
5. Upon clicking anywhere within the app window a dialog box is opened requesting the victim to configure the app as the default SMS app. This dialog box can not be closed and will reopen as long as the app is not configured as the default SMS app.
6. Once the app is set as the default SMS app it will give it a number of permissions including READ_SMS and RECEIVE_SMS allowing criminals to to covertly read, forward, and delete SMS messages.
7. In the final stage the app opens a genuine bank’s website in WebView allowing users to interact with it normally.
8. After that, whenever the attacker triggers the OTP prompt, the Android malware silently receives and forwards SMS messages with OTP codes to the Telegram chat controlled by the threat actor, allowing attackers to confirm any kind of operations including money transfer, account changes, increasing credit limits, and other financial transactions.
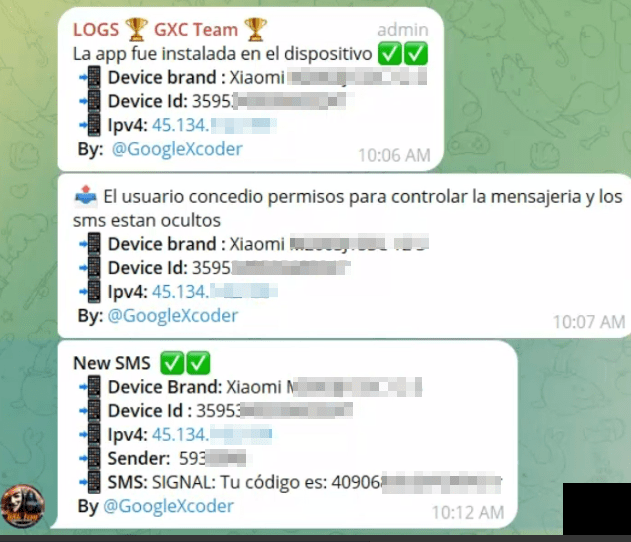
Screenshot of Telegram notifications sent to the threat actor’s controlled bot containing their victim’s data and forwarded SMS from the infected device.
If the attack were successful at the end of the scheme, the threat actor would have a wealth of credentials and personal data to perform various banking transactions with the victim’s bank account, thanks to the phishing kit, and ability to confirm those operations, thanks to the OTP stealer malware installed.
GXC Android malware analysis
The malware that the GXC Team uses is a SMS stealer type Android malware. The core functionality of the app is to receive SMS messages containing OTP login codes for bank logins and send them to a threat actor controlled Telegram chat.
Features
- Request to become the default SMS app.
- Explicitly request specific permissions.
- READ_SMS
- RECEIVE_SMS
- ACCESS_WIFI_STATE
- FOREGROUND_SERVICE
- Receive and read SMS messages.
- Send SMS messages to a Telegram chat using a Telegram bot.
- Display HTML pages in the app.
- Collect and send victim device information, such as device hardware identifiers, IP, etc.
Execution analysis
Following is a step by step description of how the malware operates from the perspective of a victim.
- Upon opening the app, the victim is presented with a WebView. This WebView is configured to visit a hard-coded URL and display the webpage, which is a genuine bank website
- Upon clicking anywhere within the app window a dialog box is opened requesting the victim to configure the app as the default SMS app. This dialog box can not be closed and will re-open as long as the app is not configured as the default SMS app.
- Setting the malicious app as the default SMS app will give it a number of permissions, most importantly READ_SMS and RECEIVE_SMS, which will allow the app to read and receive SMS messages sent to the victim device respectively.
- Upon returning to the app, and after having set the app as the default SMS app, the website via the hard-coded URL can be interacted with as normal. The dialog box will not re-open.
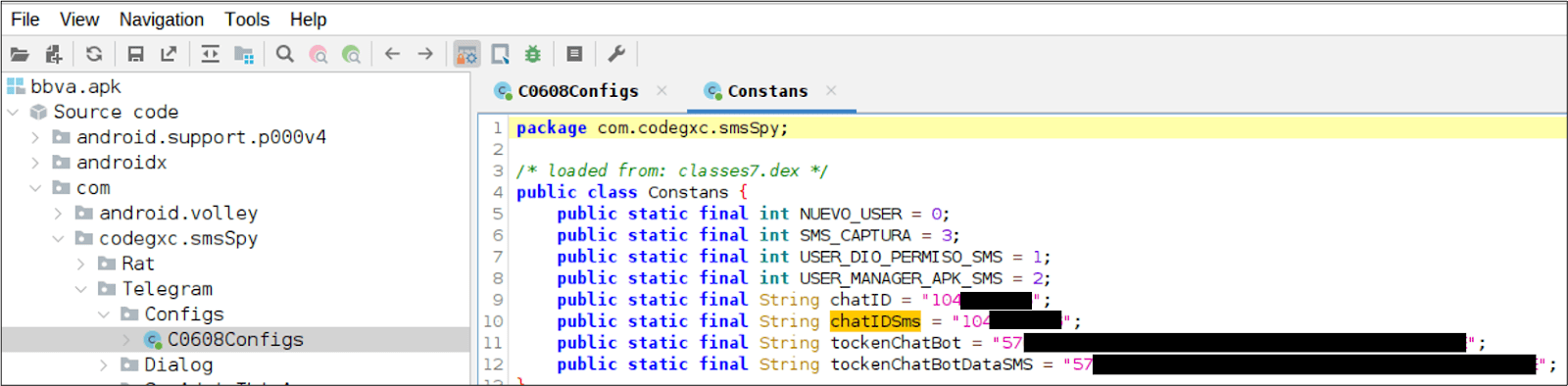
In the background, the app is sending any SMS messages received by the victim to a threat actor controlled Telegram chat using a Telegram bot. The chat and bot IDs are hard-coded into the malicious APK.
Along with the contents of the SMS messages, additional information is also sent to the threat actor, including device manufacturer and model, the device’s Android firmware version, current IP address, phone number of the sender of the SMS, and the contents of the SMS message.
The idea is that the victim will install the application giving the necessary permissions and then each hSMS message containing an OTP code to complete the login or confirm transaction would be received by the app instead, and sent to the threat actor controlled Telegram chat.
Conclusion
The discovery of the GXC team reveals an emerging cyber threat aimed specifically on Spanish banking customers and having a pretty well-established criminal business and effective phishing tools, making them a significant threat to the region. Specific attention is brought to an unusual combination of phishing kit and Android OTP stealer malware, making it much more versatile for criminals and far more dangerous to unsuspecting users.
Starting from generic phishing pages and implementing new features and ways to improve lures and attack scenariosGXC team demonstrates that criminals that are using simple yet creative techniques rapidly become successful and therefore pose a significant risk to not only users themselves but financial institutions as well.
Group-IB will continue to monitor and track the activity of this threat actor and has already launched a more comprehensive investigation into the threat actor.
Recommendations
For prevention and mitigation, financial institutions can adopt a multipronged approach to tackle this or similar threats:
- Monitoring the local threat landscape and track threat actor’s activity through threat intelligence solutions
- Proactive detection and taking down phishing resources to prevent fraud in early stages
- Implementing session-based anti-fraud or fraud protection solutions to detect and protect account compromises
- Spreading awareness about the new fraud schemes and educating users.
- Stepping up efforts into combating this type of threat by enabling cybercrime investigations.
As a banking customer, here is how you can recognize such threats, and protect yourself from fraudulent or phishing attempts:
- Always verify the authenticity of the request with your bank.
- Double-check before providing any personal or bankning-related information online.
- Do not download or sideload any banking or related applications from suspicious or untrusted websites and links.
- Use only officially verified communication channels with your bank and its employees.
If you’ve fallen victim to such an attack, don’t stay silent. Criminals thrive on our silence. When you realize you’ve become a victim of a compromise, make sure to report it to the police. Provide as many details as you can so that investigations can get underway, and perpetrators can be brought to justice.
IoCs
- hu-alert[.]online
- caixabank-particular[.]com
- mi-bancsabadell[.]com
- be-ceca[.]com
- lng-direct[.]es-miparticulares[.]com
- es-miparticulares[.]com
- grupos-inicio[.]com
- au-myposts[.]com
- es-bsnacional[.]com
- mi-deustsche-bank[.]com
- mi-deutschebank[.]com
- es-miempresas[.]com
- cuenta-app[.]com
- santander[.]esp-aviso[.]com
- esp-aviso[.]com
- ing[.]direct-usuario[.]com
- direct-usuario[.]com
- grupo-inicios[.]com
- santander-empresas[.]grupo-inicios[.]com
- www[.]direct-cuentas[.]com
- direct-cuentas[.]com
- amazon-cuentas[.]com
- es-registros[.]com
- bancosantander-empresa[.]net
- bancosantander-empresas[.]net
- supportfbappeal[.]com
- banca[.]grupocajarural-esp[.]com
- esp-avisos[.]com
- grupocajarural-esp[.]com
- cancelar-recibos[.]net
- mi-satander[.]com
- aviso-laboralkutxa[.]com
- movil-abanca[.]online
- mi-evobanco[.]com
- dispositivo-triodos[.]com
- micorreo-aviso[.]com
- mi-kutxabank[.]com
- cornerbanks-ch[.]com
- www-banca-sabadell[.]com
- laboraikutxa-web[.]com
- mi-caixabanca[.]com
- www-laboraikutxa[.]com
- mi-sabadell[.]com
- usuario-e[.]com
- banca-laboraikutxa[.]com
- f-fb-watch[.]com
- mibanca-bankinter[.]com
- banca-arquia[.]com
- banca-deutsche[.]com
- mi-bankinter[.]com
- mi-laboraikutxa[.]com
- mi-laboralkutxa[.]com
- opensbank[.]com
- aviso-bbva[.]com
- seguridad-eurocaja[.]com
- seguridad-mi-abanca[.]com
- laboraikuxta-usuarios[.]com
- micorreo-notificacion[.]com
- seguridad-mibbva[.]com
- abanca-usuario[.]com
- eligecamino[.]com
- laboraikutxa-usuario[.]com
- laborakutxa-usuario[.]com
- www-bancasabadell[.]com
- bancasantander-es-empresa[.]com
- bancasantander-empresa-es[.]com
- mi-abanca[.]com
- bancaminos[.]com
- bancasantander-empresa[.]com
- micorreos-notificacion[.]com
- bankinter-banca[.]com
- antifraudes-es[.]com
- bancasantander-app[.]com
- bancasantander-empresas[.]com
- tuscaminos[.]com
- targobank-verificacion[.]com
- bankinter-ingreso[.]com
- bancaminos[.]tuscaminos[.]com
- cajamar-verificacion[.]com
- bbva-seguridad-es[.]com
- bbva-atencion-cliente[.]com
- targobank-verificaciones[.]com
- caixaeginyers[.]com
- tuscamino[.]com
- cancelacion-transferencias[.]net
- es-entra[.]online
- mioficina-es[.]com
- laboralkutxa[.]es-users[.]com
- es-users[.]com
- laboralkutxa[.]es-usuarios[.]online
- es-usuarios[.]online
- hanseaticsbank-da[.]com
- es-html[.]com
- es-iniciar[.]online
- es-particular-es[.]com
- incidencia-404[.]com
- www[.]incidencia-404[.]com
- bancaminos-es[.]online
- bbvaempresa-es[.]com
- es-enter[.]com
- www[.]es-enter[.]com
- bancsabadell-esp[.]com
- ing[.]home-html[.]com
- home-html[.]com
- hanseaticbank[.]su
- uk-lives[.]su
- es-saldo[.]su
- es-funciones[.]su
- es-lives[.]su
- es-live[.]su
- es-funcion[.]su
- au-lives[.]su
- bancamarch[.]es-acceso[.]su
- es-acceso[.]su
- bancobbva[.]es-online[.]su
- es-online[.]su
- arquiabanca[.]es-accesos[.]su
- es-accesos[.]su
- es-actualizacion[.]su
- bbvacuentaonline[.]su
- caixaenginyers[.]es-cuentas[.]su
- es-cuentas[.]su
- es-cuenta[.]su
- deutschbank[.]es-infos[.]su
- bancosantander[.]es-web[.]su
- es-web[.]su
- es-infos[.]su
- es-clientes[.]su
- openbank[.]es-clientes[.]su
- unicajabanco[.]es-info[.]su
- es-info[.]su
- liberbanconet[.]club
- renta4banconet[.]club
- liberbanksnet[.]club
- renta4banconets[.]club
- r4banconet[.]club
- liberbankis[.]club
- libersbanknets[.]club
- etherscamorg[.]club
- liberbanknets[.]club
- liberbankes[.]club
- liberbankiorg[.]club
- liberbankorg[.]club
- andbank[.]club
- z-sms[.]online
- binacenow[.]com
- binacefull[.]net
- binaceeasy[.]com
- binacecoin[.]net
- binacefull[.]biz
- dg[.]esmas[.]online
SHA-256
402544C3C74924C7A9F355108F474FD3B0D643A38ABA45C933D880B1C2A206DE
E65C24D6E5F883CA02F79EDC0BD4FDBD28DC130F11FDBCA75B7FD26B2587BFA4
B1B0EB10002669BE6B32792A196227F1D595E26B0039E719EF9357E2B8F5361B
944F0568CE0394B4DB3FD618D6F1A0C53F94712F91FA162A4F28B1F93AD9F18F
2826A1C5ED1456BA00421FFDD4E331C691B39FC0334F4590EB860C38452D606B
9C718529F37A6C3EA0B128A8C15A1D1950BB350A9B5039C770651B8B73393007
E047F13914278AD4E5CC63D30CFDAC56CF20F86D3A4CF26414001E9AED5F9875
05A5CF0D0EB2A224D0326F2AC95A2D60CA9935D015070ED17439C2DD7A79D50C
AE2976F99876605DF0E043AC62081AF43426286EC5759DC3ECA080E26CB16B97
APK signing certificate serial number
45ff9a3
APK signing certificate SHA256
492682F877607EE99DF2DDD2BD5953FD727BDF6E19D397DE9DBBAFD582BCAD75