Introduction
In March 2023, as part of regular cyber intelligence gathering, Group-IB’s Threat Intelligence team attempted to infiltrate a private Ransomware-as-a-Service (RaaS) program that uses the Nokoyawa ransomware strain. To do so, our researchers had to pass a “job interview” with a threat actor who, as it later turned out, operated their own botnet and had gained access to several corporate networks. We previously conducted a similar exercise with the Qilin RaaS program.
In most cases, we would simply describe the inner workings of the RaaS program based on information received from the “recruiter”, but this case was different. The threat actor who conducted the “interview” for a new ransomware affiliate program not only shared a trove of valuable information about their RaaS project but also provided insights into their background and their role within various RaaS programs. All of this deserves a separate blog post. For those eager to learn about Nokoyawa and other RaaS, stay with us. But before we delve into that, we would like to talk about farnetwork, a threat actor known as farnetworkl, jingo, jsworm, razvrat, piparkuka, and farnetworkit.
Throughout the threat actor’s cybercriminal career, which began in 2019, farnetwork has been involved in several connected ransomware projects, including JSWORM, Nefilim, Karma, and Nemty, as part of which they helped develop ransomware and manage the RaaS programs before launching their own RaaS program based on Nokoyawa ransomware (also used by ShadowSyndicate). On June 19, 2023, farnetwork announced that they would stop recruiting for their team and declared their intentions to retire from the business. Nokoyawa DLS ceased its operations in October 2023.
Nonetheless, Group-IB researchers believe that it is only a matter of time before farnetwork returns to their illicit activities under a different name and with a new RaaS program, as they have done many times in their varied career.
In this report, Group-IB’s Threat Intelligence team reveals previously unknown details about farnetwork’s activities and the timeline of their operations. We also describe ransomware affiliate programs that farnetwork was involved in at different points in time. Group-IB’s researchers carefully studied the online presence of this prolific threat actor on underground forums and their activity, under various nicknames, between 2019 and 2023. This blog will be useful for threat intelligence experts, threat hunters, corporate cybersecurity teams, and cybersecurity enthusiasts.
Key findings
- farnetwork operates on several underground forums under many different usernames, including farnetworkl, jingo, jsworm, razvrat, piparkuka, farnetworkit
- The threat actor has been active since at least 2019
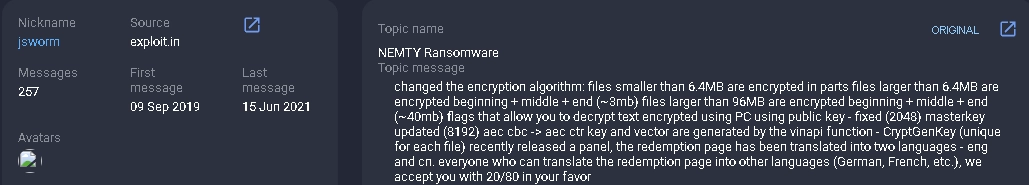
- Between 2019 and 2021, farnetwork was associated with JSWORM, Karma, Nemty, and Nefilim ransomware, as part of which the threat actor presumably helped develop ransomware and manage the RaaS programs
- Nefilim was a worldwide ransomware operation. The number of known victims exceeded 40
- In 2022, farnetwork shifted their focus to Nokoyawa ransomware, operating their own private RaaS affiliate program and running a botnet used to provide affiliates with access to compromised corporate networks
- In February 2023, farnetwork started actively recruiting candidates to their Nokoyawa RaaS program and, as part of a test task, asked them to execute privilege escalation and use the ransomware to encrypt a victim’s files, then demand payment for the decryption key
- In farnetwork’s RaaS program, affiliates do not need to compromise networks themselves. Instead, they acquire access to compromised networks from farnetwork
- Revenue distribution for successful attacks in farnetwork’s most recent RaaS is as follows: the affiliate receives 65% of the ransom, the botnet owner receives 20%, and the ransomware owner receives 15%
- As of October 2023, the Nokoyawa dedicated leak site (DLS) contained information about 35 victims before ceasing its operations
- Group-IB shared all the findings about the threat actor with relevant law enforcement authorities
What we learned from farnetwork
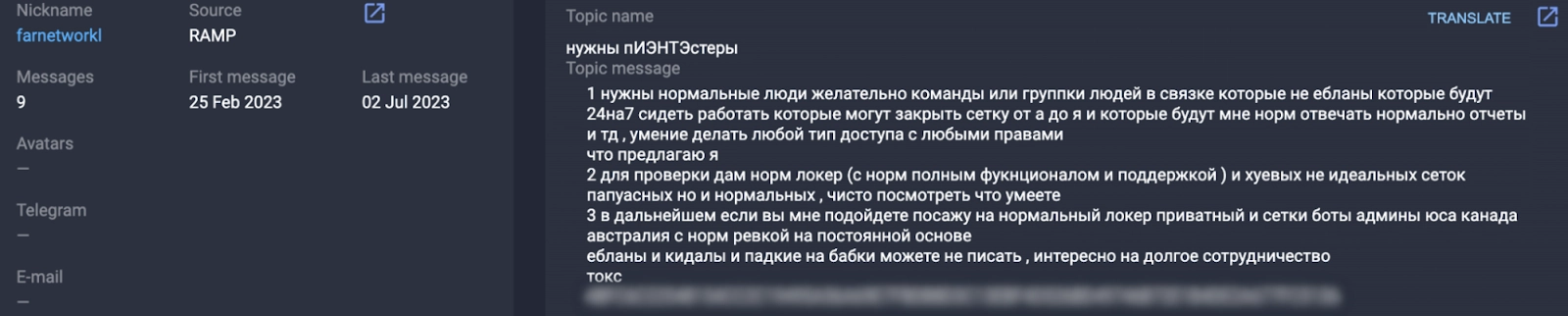
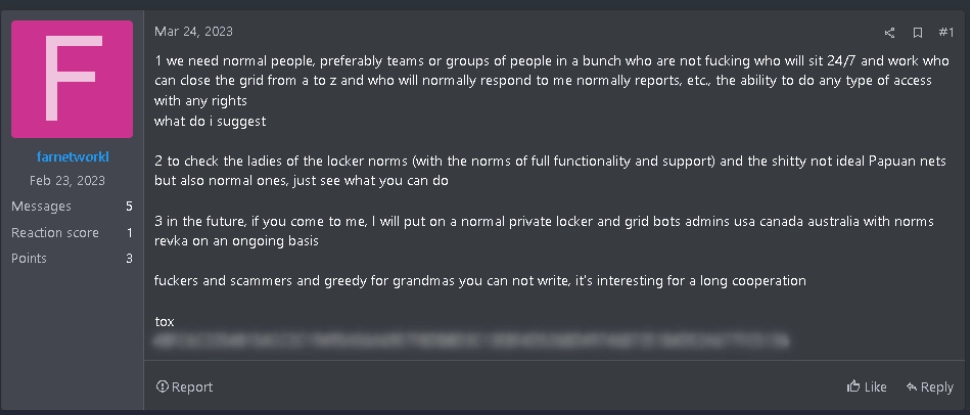
On February 23, 2023, the user farnetworkl registered on RAMP, a ransomware-themed underground forum. RAMP is an exclusive, predominantly Russian-speaking forum that requires a $500 deposit or an invitation from a moderator in order to gain access.
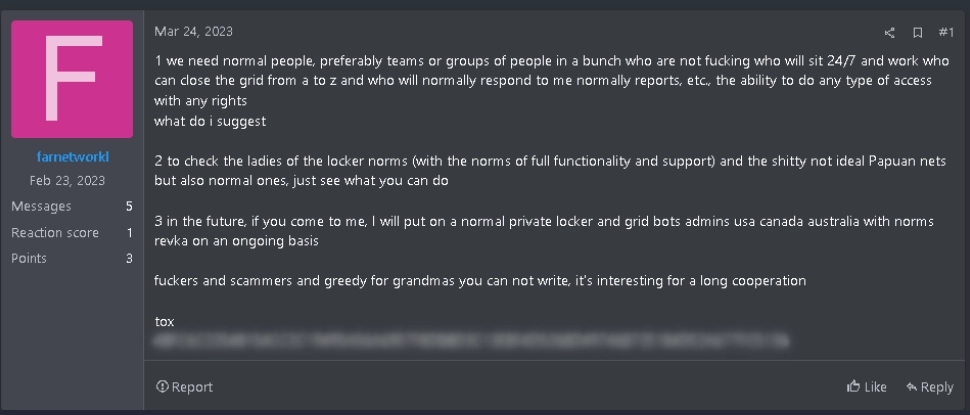
On March 24, 2023, Group-IB’s Threat Intelligence system detected an ad on RAMP posted by farnetworkl, who wanted to recruit affiliates for their Ransomware-as-a-Service program. In the post, the threat actor said that they were looking for people able to work with access to compromised networks and they promised to provide fully functional ransomware samples and support for testing purposes.
During a private chat with Group-IB researchers, farnetwork shared several insights into their current operations and past activity.
The threat actor stated that they were currently managing a RaaS affiliate program based on Nokoyawa ransomware. They described the working conditions in the Nokoyawa RaaS program as follows: a ransomware affiliate who carries out a successful attack receives 65% of the ransom amount, the botnet owner receives 20%, and the ransomware developer receives 15%. On average, in other groups, affiliates receive up to 85%. However, in this case, farnetwork is granting affiliates access to corporate networks of targeted companies. As a result, affiliates only need to escalate privileges, extract sensitive data, and encrypt targeted networks, which explains why the distribution of profits is different from the industry average.
In the Nokoyawa RaaS program, affiliates do not need to compromise networks themselves. Instead, they acquire access to compromised networks from the RaaS owner. In the chat with Group-IB researchers, farnetwork said that they had their own botnet with unauthorized access to several corporate networks.
The “candidates” wanting to join farnetwork’s RaaS program based on Nokoyawa must complete a test assignment. For the purposes of the test, farnetwork provides several compromised corporate account credentials (login + password) to facilitate privilege escalation within targeted networks. Successful candidates must execute privileges and use the ransomware to encrypt the victim’s files, then demand payment for decryption.
It is worth noting that Group-IB’s Threat Intelligence unit discovered that some of the credentials provided by farnetwork first appeared in Underground Clouds of Logs, a service that gives access to compromised confidential information obtained, for the most part, by info-stealing malware. The credentials provided by the threat actor had been compromised using the infamous RedLine information stealer (Figure 2), which suggests that they were not obtained from an exclusive source like the botnet.
As we predicted in the Hi-Tech Crime Trends Report 2022/2023, stealer logs and underground markets are becoming the main way to gain access to companies’ networks particularly among ransomware threat actors.

Figure 2. Example of credentials provided by farnetwork and found earlier in Underground Clouds of Logs.
Source: Group-IB Threat Intelligence
The threat actor mentioned specifically that they were not a Nokoyawa developer, and that affiliates were not allowed to attack medical and healthcare organizations.
During the chat, farnetwork also shared that they were currently targeting a victim from “China or Taiwan, compromised via its Columbian branch” and were about to start negotiations. According to the threat actor, their RaaS affiliate program had a DLS.
Group-IB researchers identified two DLSs connected with Nokoyawa ransomware. One (6yofnrq7evqrtz3tzi3dkbrdovtywd35lx3iqbc5dyh367nrdh4jgfyd[.]onion) was operational in January 2023 and contained information about only one victim. At the time of writing, the website is not accessible. The other Nokoyawa DLS, located at nokoleakb76znymx443veg4n6fytx6spck6pc7nkr4dvfuygpub6jsid[.]onion, appeared in May 2023 and has been updated regularly since. As of October 2023, prior to its shutdown, the Nokoyawa DLS contained information about 35 victims.
A shady past
In addition, farnetwork shared information about their past operations. The threat actor said that they had been involved with Nefilim and Karma ransomware, as part of which they managed a RaaS program as well.
According to farnetwork, the RaaS they managed in 2019 received ransom payments of $1 million in the beginning and about $600,000 later on (per victim on average). The project had the reputation of being “serious”, which is why victims were inclined to pay the ransom. The threat actor did not mention the project name, but Group-IB specialists believe it was Nemty. During the chat, farnetwork wondered why Hive had not taken all payments, which could indicate that farnetwork has interacted with Hive in some way.

Figure 3. Ransomware strains that farnetwork was involved in at different points in time
Based on the timeline of their operations, it is fair to assume that farnetwork has been one of the most active players in the RaaS market.
Further investigation by Group-IB’s Threat Intelligence unit revealed farnetwork’s aliases on other underground forums: jingo, jsworm, razvrat, piparkuka, and farnetworkit.
With help from the Group-IB Threat Intelligence system, Group-IB researchers traced the threat actor’s underground activity from 2019, which confirmed some of the information that farnetwork had shared in private.
Please refer to the table below for a detailed timeline of farnetwork’s operations between 2019 and 2003.
January 2019
The JSWORM ransomware appears in the wild.
April 20, 2019
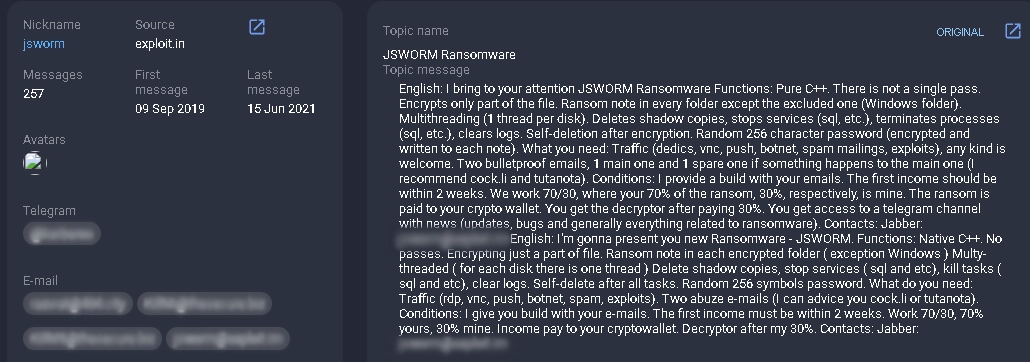
jsworm registers on the underground forum exploit[.]in.
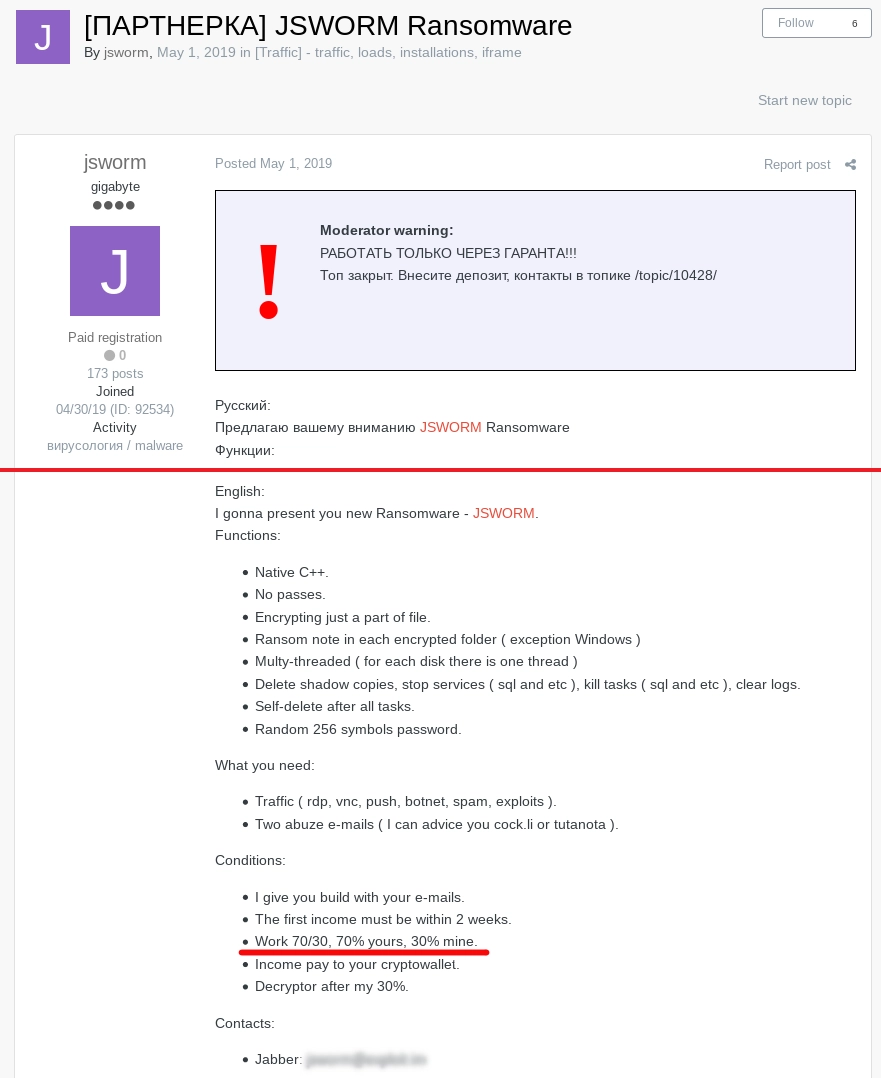
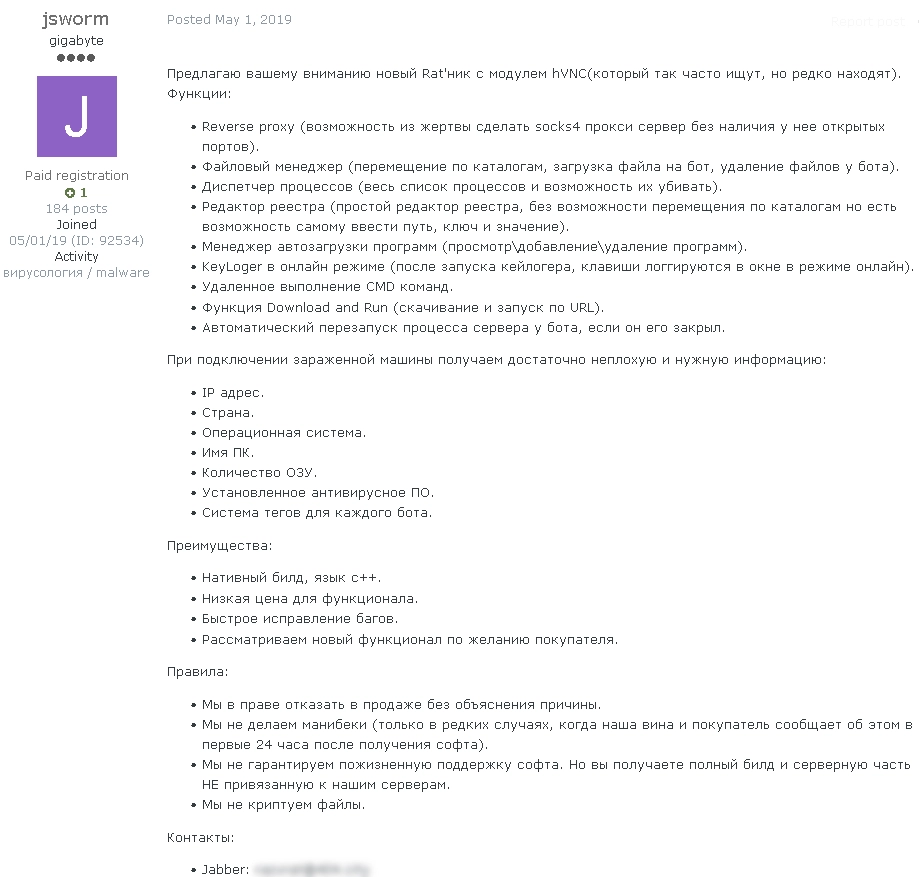
May 1, 2019
The JSWORM RaaS program is announced on exploit[.]in.
Original post in Russian and a machine translation into English.
Source: Group-IB Threat Intelligence
May 1, 2019
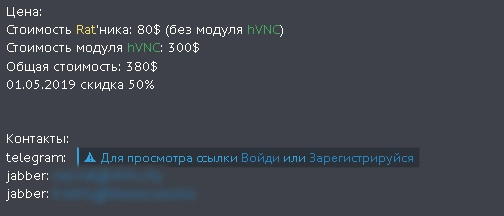
jsworm starts selling RazvRAT malware with an hVNC module on exploit[.]in. The malware has been offered on other forums by the same user but under a different nickname (razvrat and piparkuka).
Machine translation of the post in Group-IB’s Threat Intelligence system:
May 1, 2019
jsworm starts selling RazvRAT malware with an hVNC module on exploit[.]in. The malware has been offered on other forums by the same user but under a different nickname (razvrat and piparkuka).
Machine translation of the post in Group-IB’s Threat Intelligence system:
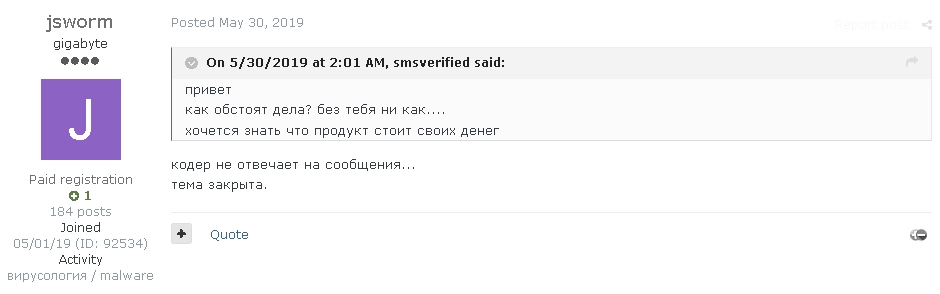
May 30, 2019
The JSWORM RaaS program is shut down (after the developer leaves the team).
May 30, 2019
jsworm stops selling RazvRAT malware.
Aug 20, 2019
Nemty ransomware emerges; jsworm creates a new thread on exploit[.]in to recruit affiliates for Nemty.
Machine translation of the post into English in Group-IB’s Threat Intelligence system:
September 1, 2019
The user jingo registers on XSS.
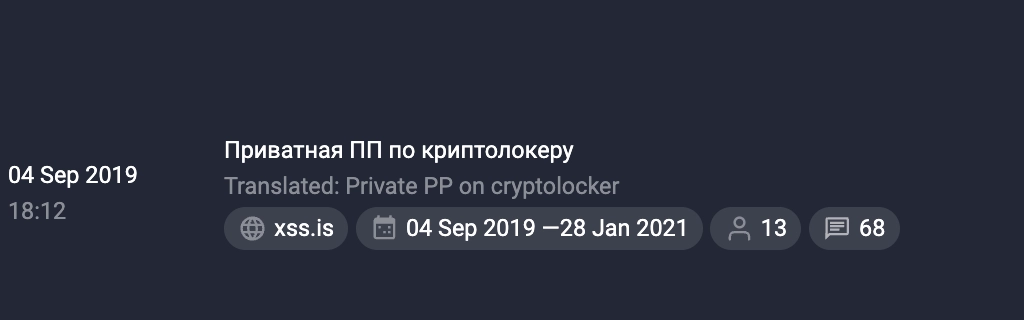
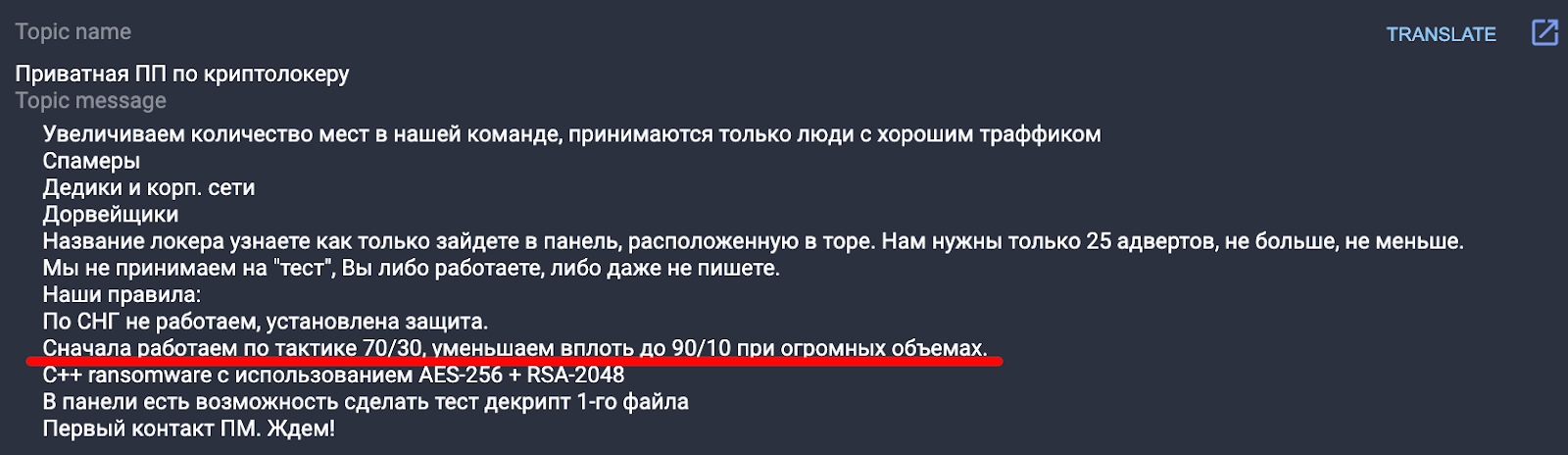
September 4, 2019
jingo creates a thread on XSS titled “Private affiliate program.”
The ransomware name is not specified.
Machine translation of the post into English in Group-IB’s Threat Intelligence system:
The description is similar to that of the Nemty Ransomware affiliate program published by jsworm on exploit[.]in.
Machine translation of the post into English in Group-IB’s Threat Intelligence system:
It is worth noting that a message by another user in this thread mentioned Nemty.
Machine translation of the post into English in Group-IB’s Threat Intelligence system:
October 2019
jsworm looks for a web developer.
December 12, 2019
jingo posts information about Nemty RaaS on XSS in the thread “Private affiliate program”
This suggests that jingo’s “private affiliate program” is jwsorm’s Nemty, and that jingo and jsworm are two nicknames used by the same person on different forums.
Machine translation of the post into English in Group-IB’s Threat Intelligence system:
1-2 March 2020
Nemty DLS emerges.
March 2020
Nefilim/Nephilim ransomware emerges. Its code shares similarities with Nemty. In addition, the Nefilim DLS called Corporate Leaks appears.
April 14, 2020
jsworm announces the end of the Nemty RaaS program and changes the model; the ransomware is to be operated privately.
Machine translation of the post into English in Group-IB’s Threat Intelligence system:
September 20, 2020
The user farnetwork registers on exploit[.]in.
November 16, 2020
jingo mentions the jabber account on XSS, which indicates a connection between jingo and farnetwork.
March 18, 2021
The user farnetwork registers on XSS.
May 2021
The website Karma Leaks (WordPress-based) emerges.
June 2021
Karma Ransomware emerges and seems to be a rebranding of Nefilim ransomware.
June 2, 2021
Farnetwork searches for a zero-day vulnerability in Citrix VPN. They state that their “budget is unlimited”.
Machine translation of the post into English in Group-IB’s Threat Intelligence system:
July 2021
Information about the last victim is published on the Nefilim DLS.
July 28, 2021
Farnetwork creates a thread searching for an account with a balance on the website pentest-tools.com. They likely intended to use the website to acquire tools for conducting offensive security testing, particularly for web applications and network penetration testing. Pentest-Tools.com is a comprehensive toolset designed for such purposes.
Screenshot of the post (original version):
Machine translation of the post into English in Group-IB’s Threat Intelligence system:
April 14, 2022
Farnetwork creates a thread in search of a person who will crypt .exe files. They offer two payment options: fixed payments per file or a monthly salary.
Machine translation of the post into English in Group-IB’s Threat Intelligence system:
Feb 21, 2023
Farnetwork creates a thread looking for a “caller” to assist in attacks on corporate networks.
Machine translation of the post into English in Group-IB’s Threat Intelligence system:
Feb 23, 2023
The user farnetworkl registers on the forum RAMP.
March 24, 2023
Farnetworkl searches for teams or individuals on RAMP for their RaaS (Nokoyawa).
Machine translation of the post into English in Group-IB’s Threat Intelligence system:
Late March 2023
Farnetwork claims to be working with Nokoyawa ransomware.
April 2023
The recruitment announcement on RAMP is still valid.
May 3, 2023
Farnetwork looks for a darkweb traffer who could provide access to corporate networks of companies in the United States and Canada.
Machine translation of the post into English in Group-IB’s Threat Intelligence system:
April 14, 2022 – June 19, 2023
Farnetwork creates threads about purchasing access to corporate networks of companies mainly in the US, Canada, and Australia. They are also interested in accessing companies in Europe with revenues exceeding $50 million and companies from other regions with revenues over $200 million.
Machine translation of the post into English in Group-IB’s Threat Intelligence system:
In addition, farnetwork creates threads seeking to buy logs that contain the following strings:
/owa/auth/logon.aspx
/RASHTML5Gateway/
https://parallels.
bots,vnc
/vpn/index.html
/vpn/tmindex.html
/auth/login.aspx
/LogonPoint/tmindex.html
XenApp1/auth/login.aspx
auth/silentDetection.aspx
/citrix/
RDWeb
/+cscoe+/
remote/login
/global-protect/
Machine translation of the post into English in Group-IB’s Threat Intelligence system:
Machine translation of the post into English in Group-IB’s Threat Intelligence system:
Machine translation of the post into English in Group-IB’s Threat Intelligence system:
On June 19, 2023, farnetwork announced that they would stop recruiting for their team in a month, stating that they plan to retire from the business once they finish with their current victims.
Screenshot of the post (original version):
English translation of the post in Group-IB’s Threat Intelligence system:
June 30, 2023
A threat actor with the username “tsyko” creates a thread on XSS about selling access to an online bank through VPN. Farnetwork shows an interest and asks tsyko to get in touch.
Screenshot of the post (original):
Machine translation of the post into English in Group-IB’s Threat Intelligence system:
October 8, 2023
The Nokoyawa dedicated leak site (DLS) had documented information on 35 victims before ceasing its operations in October.
October 2023
No new activity relating to the threat actor on underground forums.
How revenue is distributed in various RaaS affiliate programs
While investigating farnetwork, Group-IB’s Threat Intelligence unit obtained insights into the revenue distribution models in various RaaS programs.
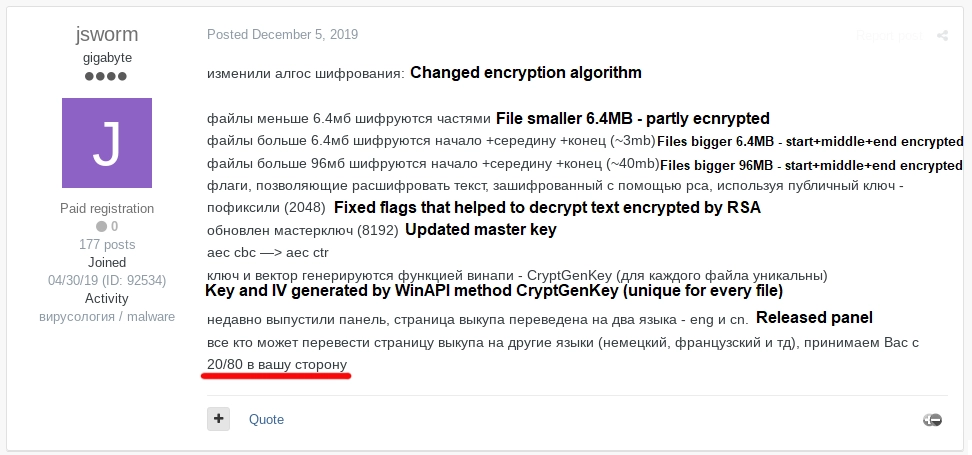
In May 2019, the threat actor created a thread on the underground forum exploit[.]in to recruit partners, offering them a 70% share of the ransom in their affiliate program.
By September 2019, the threat actor had discussed the possibility of increasing the share given to affiliates to 90% of the ransom for larger-scale attacks.
In December 2019, farnetwork was offering partners 80% of the ransom.
In March 2023, the threat actor proposed that affiliates receive 65% of the ransom, the botnet owner 20%, and the ransomware owner 15%. Over time, the percentage allocated to affiliates increased, along with the increase in the average ransom demand. In a private conversation with Group-IB researchers, the threat actor mentioned that the share of the ransomware owner could eventually decrease to 10%.
Farnetwork’s ransomware career
This part examines the various ransomware strains that farnetwork was involved in at different points in time. In our analysis, we focus on the threat actor’s most recent ransomware projects.
Nokoyawa
Nokoyawa samples were discovered in February 2022. SentinelOne researchers found that the code shared similarities with Karma ransomware (rebrand of Nefilim), which itself is an evolution of Nemty.
The initial version of Nokoyawa was developed in C and used asymmetric Elliptic Curve Cryptography (ECC) with Curve SECT233R1 (also known as NIST B-233), using the Tiny-ECDH open-source library. Each file was secured using a Salsa20 symmetric key. Nokoyawa 2.0 appeared in late September 2022 and relies on Salsa20 for symmetric encryption, like Nokoyawa 1.0. The elliptic curve was replaced with Curve25519, however, and the code is written in Rust.
In early 2022, analysts at Trend Micro discovered links between Nokoyawa and the Hive ransomware group due to similarities in the attack chain. Interestingly, during their chat with Group-IB researchers, farnetwork mentioned that they had interacted with Hive and knew some internal information.
Nokoyawa had a DLS called Nokoyawa Leaks (nokoleakb76znymx443veg4n6fytx6spck6pc7nkr4dvfuygpub6jsid[.]onion). During our investigation, it worked intermittently before shutting down in October 2023. As of September 2023, it was still functional, although this would change the following month. The details of many victims (ten) appeared on the DLS in May 2023. The total number of victims whose details were published on the DLS at the time of analysis (October 2023) was 35.

Figure 9. Screenshot of the DLS for Nokoyawa ransomware
In late May 2023, Group-IB specialists discovered that the Nokoyawa ransomware group had defaced a website and placed a ransom note on it. At the time of analysis (September 2023), we had not detected any similar cases of defacement.
The page contains a link to a chat in Tor: nokopayzp3s3jxyagxjlbxisvda74tsthc6f4v455we2gnobmehunfad[.]onion
Screenshot of the defaced web page from Google:
Below is a screenshot of the defaced web page with the ransom note:

Figure 10. Screenshot of the defaced page by Nokoyawa ransomware
Nokoyawa
You are probably wondering why you are receiving a message from me. Yesterday, got breached.
You are probably not aware, but over the past few days, we have been exfiltrating all of your data that we could get our hands on. We took over 248 GB in data ( userdata / clients info / netshares / photos id ).
To reach an agreement you have 48 hours to visit our Onion Website. If contact is not made within 48 hours: we will start showing the data to our potential buyers, and leak a partial.
All of your clients (customers / employers) will be informed and given proof that their data has been compromised and publish everything in a public way in multiple places and outlets to get more customers interested in buying the data and also reporting the availability of this data to the appropriate news platforms.
How to open Onion links:
– Download TOR Browser from official website.
– Open and enter this link:
http://nokopayzp3s3jxyagxjlbxisvda74tsthc6f4v455we2gnobmehunfad.onion/pay/
– On the page, you will see a chat with the support.
– Send your first message.
Don’t waste your time.
Otherwise all your valuable and sensitive data will be leaked.
Our website are full of companies that doubted the fact of the data breach or it’s extent.
– http://nokoleakb76znymx443veg4n6fytx6spck6pc7nkr4dvfuygpub6jsid.onion/
As of October 2023, the Nokoyawa DLS contained information about 35 victims before ceasing its operation. At the time of writing, the DLS is not accessible.

Figure 11. Victims of Nokoyawa ransomware posted on DLS: distribution by country and industry
The first post with information about a victim appeared on the Nokoyawa DLS in October 2022.
According to Trend Micro, Nokoyawa had already been used in attacks prior to that. Trend Micro researchers said that most of Nokoyawa’s targets detected in early 2022 were located in South America, mainly Argentina. However, the victims from Argentina were not posted on the Nokoyawa DLS.
According to public reports, the threat actors requested a ransom of $200,000 in Bitcoin The same report also revealed that Nokoyawa operators used IcedID malware and tools such as PsExec, AdFind, and Cobalt Strike.
Karma
In June 2021, Karma ransomware was discovered. Karma shares similarities with Nefilim, and we believe it to be the next version of Nefilim.
The Nefilim DLS, Corporate Leaks, operated on Onion version 2, which was deprecated in July 2021. The most recent leak observed on this page was on July 20, 2021. On the other hand, Karma’s DLS was established on May 22, and the first leak occurred on September 1.
The Karma DLS was called Karma Leaks:

Figure 12. Screenshot of DLS for Karma ransomware
Based on available data, Karma ransomware and its associated onion pages seem to have been yet another rebranding of Nemty and Nefilim’s Corporate Leaks. The main difference lies in the encryption algorithm, which makes sense given that this is an area where many ransomware authors experiment and make modifications.
Karma DLS contained information about 4 victims, with three from the USA and one from Switzerland. The victims were software companies (2), hardware (1), and manufacturing sector companies (1).
Nefilim
Nefilim ransomware was discovered in March 2020. This malware is used to encrypt data belonging to business users and companies using AES-128 + RSA-2048. Nefilim requires the victim to send an email to the ransomware operators to find out how to pay the ransom in BTC and get their files back. The ransomware mostly targets English-speaking users and has been found worldwide.
Nefilim, which was active from March 2020 to July 2021, had a DLS called Corporate Leaks (see screenshot below).

Figure 13. Screenshot of DLS for Nefilim ransomware
Nefilim was a worldwide ransomware operation, with more than 40 known victims.

Figure 14. Victims of Nefilim ransomware posted on DLS: distribution by country and industry
Nemty
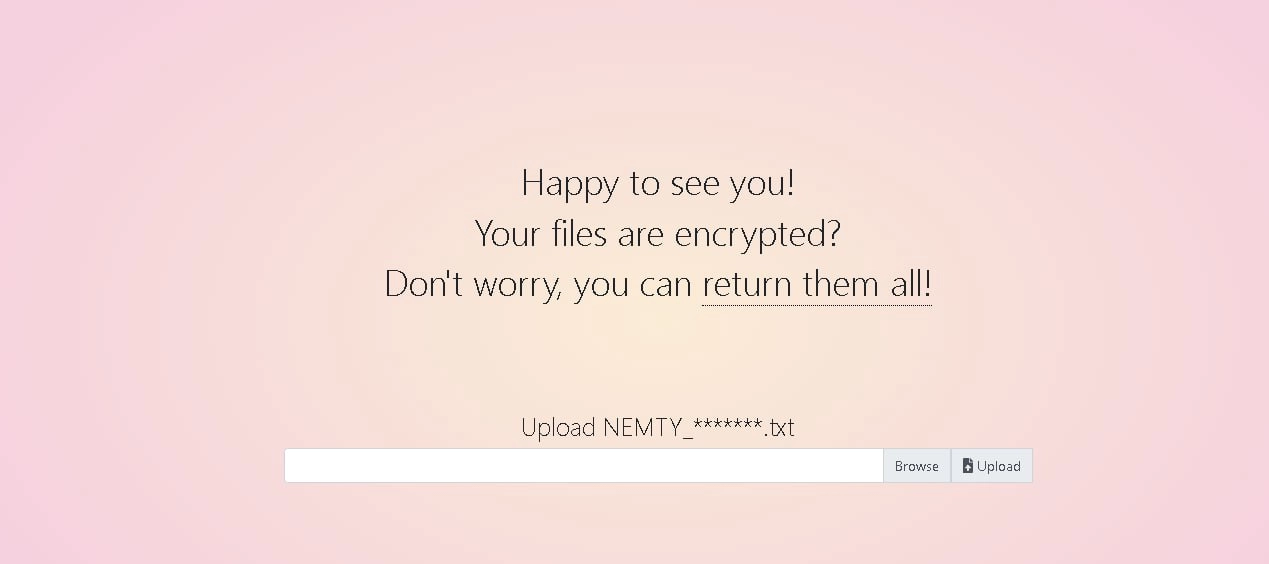
Nemty succeeded JSWORM ransomware. JSWORM was farnetwork’s first known ransomware project, detected in the wild in January 2019.
Nemty was detected for the first time in August 2019. After encryption, this ransomware appends the .nemty extension to all files and creates the NEMTY-DECRYPT.txt note. On August 20, 2019, a thread advertising the Nemty ransomware affiliate program was created on the underground forum exploit[.]in.
While the RaaS program was in operation, several Nemty versions were released, namely 1.4, 1.5, 1.6, 2.2, and 2.3.
On April 14, 2020, the user jsworm left a message on the forum saying that they had abandoned the public Nemty Ransomware-as-a-Service model and changed it to be operated in private only.
Nemty has been detected in various regions: North America, South America, Europe, Africa, Asia, and the Commonwealth of Independent States (CIS). Nemty ransomware was distributed in different ways, including phishing emails, RDP, RIG and Radio exploit kits, a PayPal phishing site, and the Trik botnet (aka Wortrik, Phorpiex).
Two versions of the Nemty DLS design were detected, but neither contained information about victims. In addition, threat actors behind the Nemty project are known to have communicated with their victims using a chat in Tor:

Figure 15. Screenshot of negotiation page for Nemty ransomware
Screenshot of the ransom note:

Figure 16. Screenshot of the ransom note for Nemty ransomware
The Nemty negotiation page is known to have had several designs:
Affiliates
During our investigation into underground forums, Group-IB specialists discovered potential affiliates and participants in farnetwork’s RaaS programs. This information is available to Group-IB Threat Intelligence customers.
RazvRAT malware
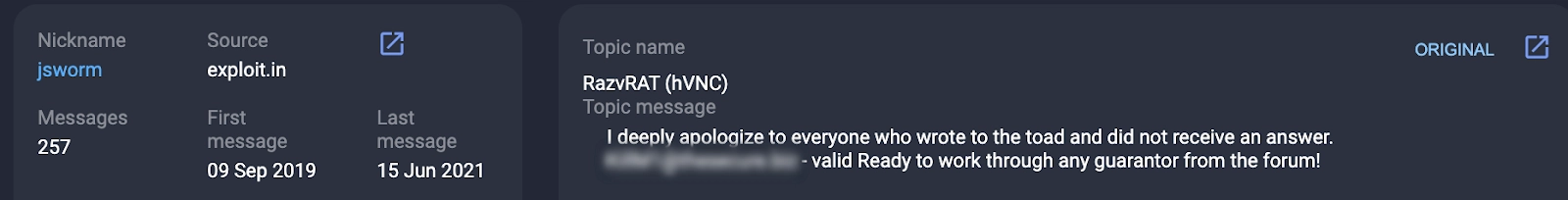
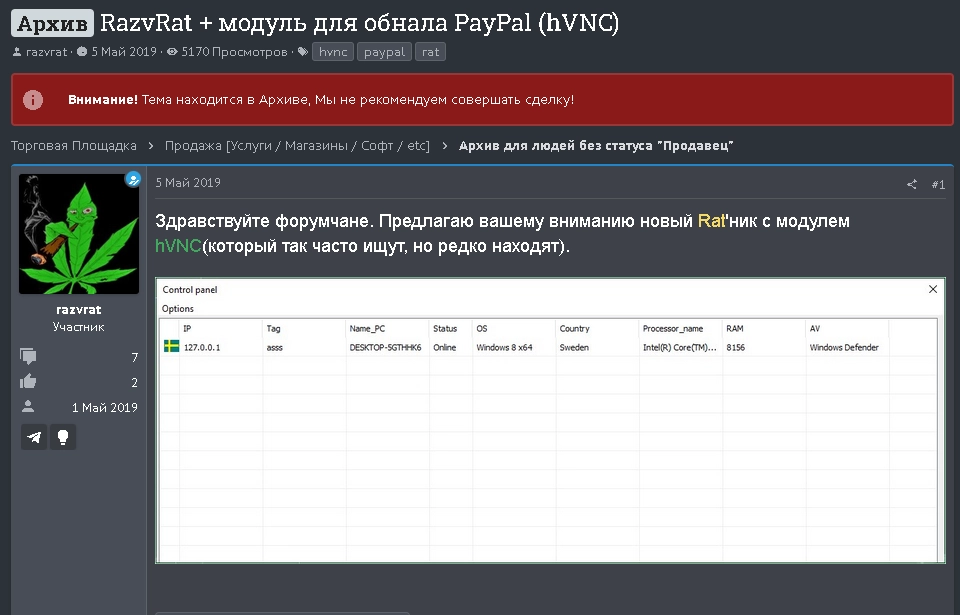
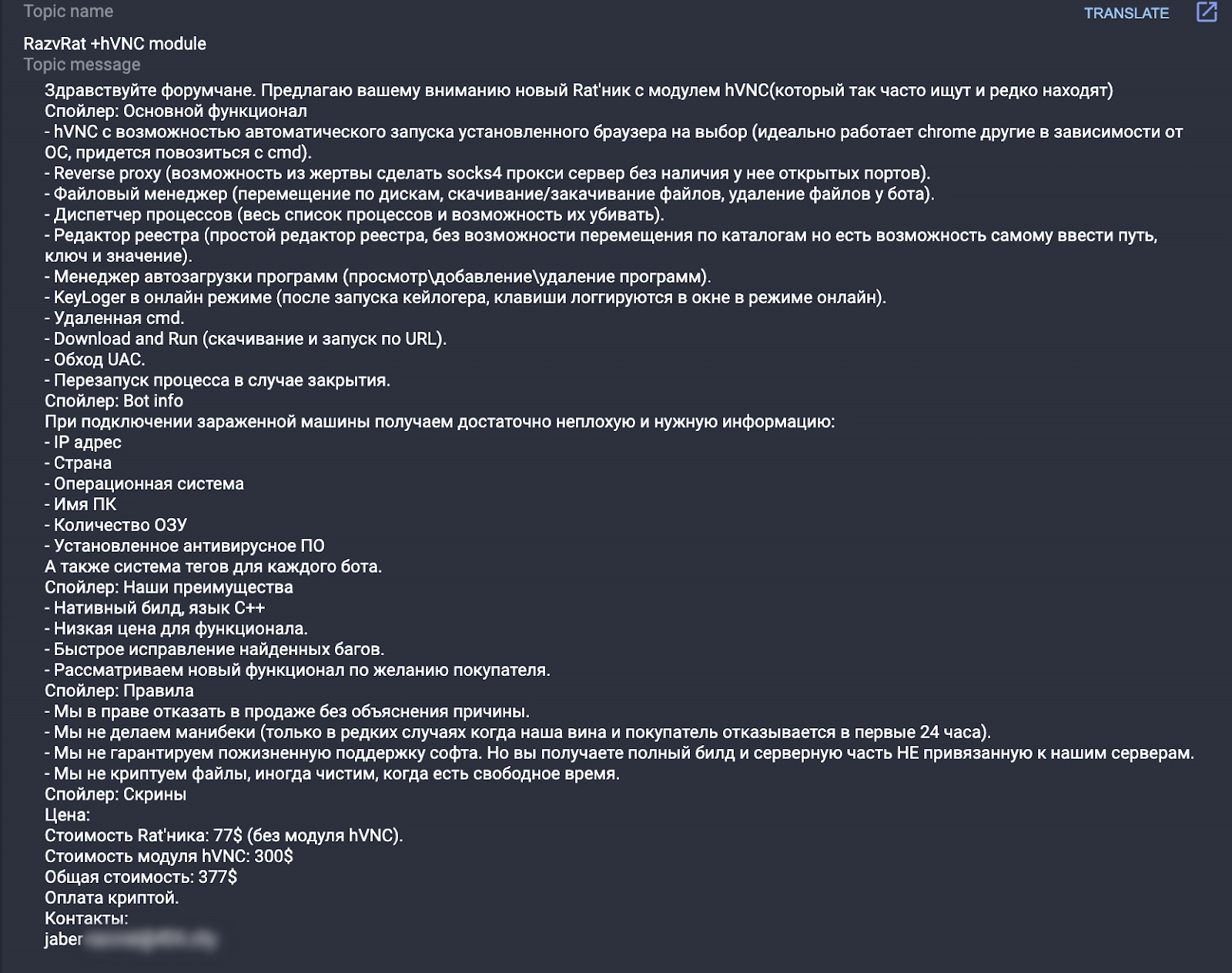
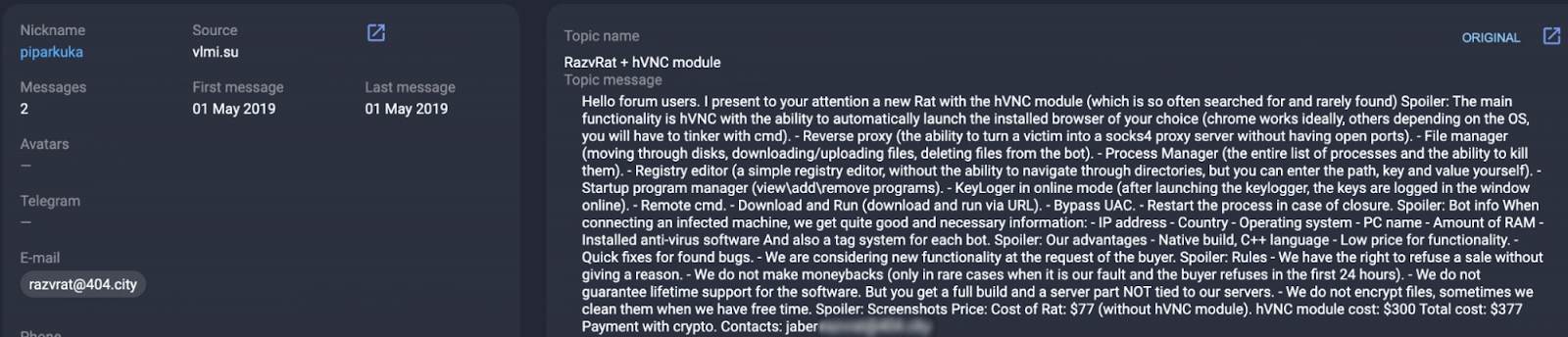
On May 1, 2019, a user with the nickname jsworm created a thread on the underground forum exploit[.]in offering a malicious program called RazvRAT for sale together with an HVNC module.
The threat actor had not developed the malware but was trying to sell it as a vendor, and left contact information:
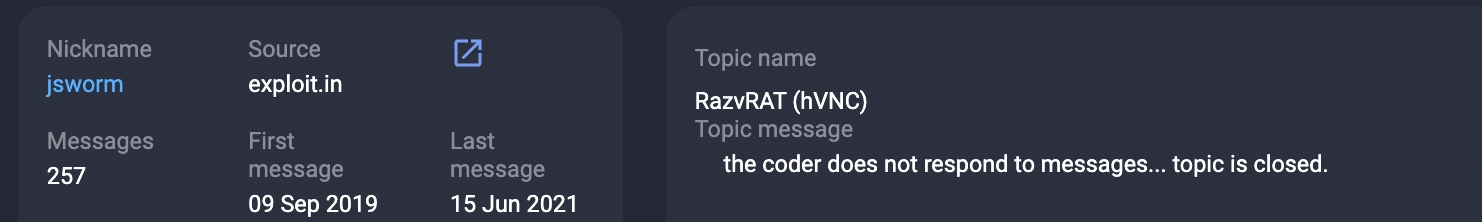
On May 30, 2019, the threat actor closed the thread because the malware developer did not respond, which suggests that a sale could not be agreed.
Furthermore, the individual created a similar thread for selling the malicious program (RazvRAT + hVNC module) on other forums using different usernames.
On May 5, 2019, the threat actor used the username razvrat to create a sales thread on the Gerki forum.
They gave the same contact information:
On May 1, 2019, using the nickname piparkuka, the individual gave the same contact information on the forum Vlmi. The thread has since been removed, but a screenshot is available in Group-IB’s Threat Intelligence system.
The price of $377 is rather low for the RAT + hVNC bundle. We’ve seen several other threat actors selling a similar bundle for as much as $2,000 a month.
Conclusion
Our findings show that farnetwork is an experienced and highly skilled threat actor. Their previous projects resulted in a large number of victims and considerable monetary losses for organizations.
Farnetwork has become one of the most active players of the RaaS market. The threat actor has been involved in five ransomware-as-a-service programs in less than five years. Group-IB researchers discovered evidence suggesting that the threat actor has not only been managing RaaS programs but also developed ransomware themselves.
Despite farnetwork’s retirement announcement and the closure of Nokoyawa DLS, which is the actor’s latest known project, the Group-IB Threat Intelligence team doesn’t believe that the threat actor will call it quits. As it happened several times in the past, we are highly likely to witness new ransomware affiliate programs and large-scale criminal operations orchestrated by farnetwork. We will keep monitoring the threat actor’s activity and will provide updates as they become available.
At Group-IB, our ongoing commitment to fighting cybercrime drives us to continue detecting and exposing the methods, tools, and tactics used by ransomware groups. We are committed to maintaining a proactive stance, which helps us to anticipate threats and keep organizations worldwide informed and protected.
We invite cybersecurity experts from any background or specialization to investigate adversaries together with the Group-IB team as part of the Cybercrime Fighters Club. If you have a fresh take on an interesting cybersecurity topic, whether it be a new perspective on an ongoing attack, changes to the TTPs of known groups, new vulnerabilities, the latest adversary infrastructure, or anything that you think might be of interest, send us your original and complete materials via the form below, and we will explore how we can activate our resources to help advance your investigation. We also welcome applications to join the Group-IB team. Check out our vacancies here.
Recommendations
Although ransomware groups have gained notoriety for targeting companies in critical sectors especially, they are a threat to organizations across all industries. In addition to having new members in its network, farnetwork’s ransomware affiliate program equips members with upgraded tools and techniques and even provides ransomware delivery. That being said, it is essential that businesses take specific steps immediately to keep their mission-critical operations and data secure. We recommend the following:
- Add more layers of security: Multi-factor authentication (MFA) and credential-based access solutions help businesses secure their critical assets and high-risk users, making it harder for attackers to be successful.
- Stop ransomware with early detection: Leverage the behavioral detection capabilities of the Endpoint Detection and Response (EDR) solution to help identify ransomware indicators across your managed endpoints, promptly alerting your teams to any suspicious activity for further scrutiny. This proactive approach enables agile detection, investigation and remediation of both known and unknown threats on your endpoints.
- Have a “backup” strategy: Data backup processes should be conducted regularly as they reduce damage and help organizations avoid data loss following ransomware attacks.
- Leverage an advanced malware detonation solution: Organizations should leverage AI-infused, advanced analytics-based solutions to detect intrusions in real time. Learn how Group-IB’s Managed XDR coupled with Threat Intelligence helps businesses to:
- gain insights into the unique TTPs used by APTs and other threat groups and pivot their security strategies accordingly, and
- enable multi-layered cybersecurity (endpoint, email, web, and network) through automated threat detection and response.
- Patch it up: The longer a vulnerability remains unpatched, the greater the risk that it will be exploited by cybercriminals. Security patches should therefore be prioritized. Organizations should also set up a process to regularly review and apply patches as they become available.
- Train employees: Educate employees about the risks relating to the organization’s network, assets, devices, and infrastructure. The human factor remains one of the greatest vulnerabilities in cybersecurity. Organizations should conduct training programs and security drills to help employees identify and report the tell-tale signs of cybercrime (e.g. phishing emails).
- Control vulnerabilities: Do not turn a blind eye to emerging vulnerabilities. Checking your infrastructure annually with a technical audit or security assessment is not only a good habit — it also adds a much-needed layer of protection. Infrastructural integrity and digital hygiene processes should be monitored continually.
- Never pay the ransom: In 97% of ransomware attacks, it is impossible to regain access to data without decryption software. Group-IB’s Incident Response experts do not recommend rushing to pay ransoms.
Financially-motivated threat actors are driven to make you pay more. Even if one attacker returns your data, another will find out about your willingness to pay, which will lead to an increase in the number of attempted attacks on your company. The best you can do is to contact incident response experts as quickly as possible.