Introduction
Over the past 2 years, mule operators targeting top retail banks across the Middle East, Turkey & Africa (META) have evolved from using basic IP-masking to deploying complex, multi-layer supply-chain fraud schemes. Drawing from Group-IB Fraud Protection telemetry (>200 million mobile sessions) and thousands of confirmed mule investigations, this report traces their step-by-step adaptations – and the countermeasures that helped banks stay ahead.
The research outlines key evolutionary phases: basic IP obfuscation, roaming SIM abuse, GPS spoofing, SIM-removal evasion, and eventually physical device “muling” using hired individuals and postal shipments. It also proposes a layered detection strategy that blends network intelligence, device telemetry, and behavioral analytics.
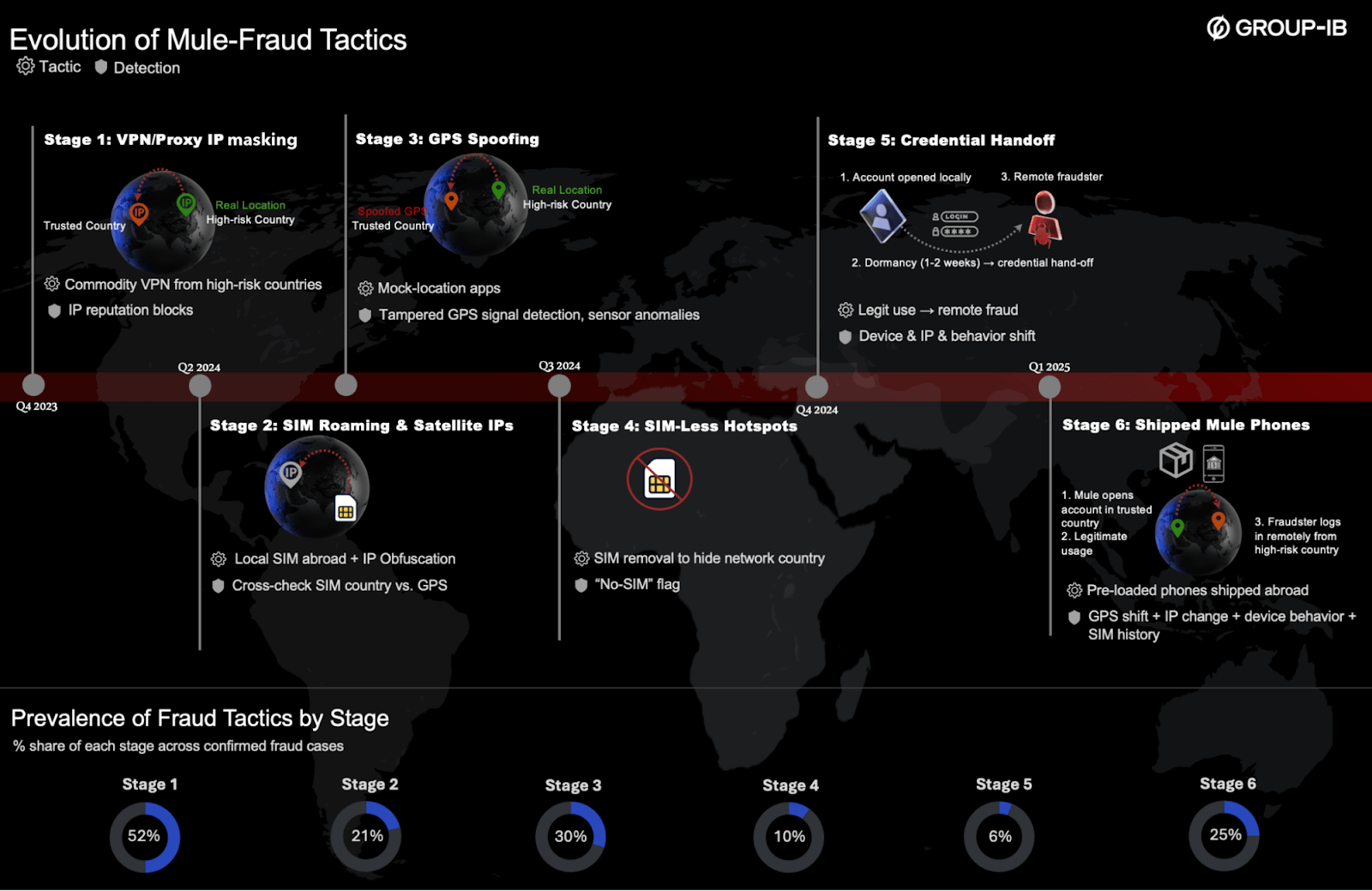
Figure 1: Timeline of evolving mule fraud tactics and detection points
Financial institutions in the Gulf region, where regulations are especially tight, enforce strict restrictions on VPN, hosting, and proxy traffic. Early on, these controls forced mule operators to rely on generic VPN services – easily identified via IP reputation tools. By late 2023, fraudsters began a rapid innovation cycle to bypass these filters and regain remote access to accounts in the target jurisdictions. This article tracks that cycle and draws lessons for banks across META facing similar threats.
Stage One: Basic IP Masking via VPNs and Proxies
Timeline: Q4 2023 – Q1 2024
Tactic Summary: Fraud actors attempted to open and operate mule accounts remotely from high-risk countries in the Middle East by masking their IP addresses using commonly available VPNs and proxy servers.
Constraints: Regional regulatory policy blocks access to banking applications from IPs tied to VPNs, cloud hosting providers, and proxy networks.
Detection:
- Group-IB’s IP Fraud Protection system flagged VPN infrastructure and suspicious autonomous system numbers (ASNs) in real time.
- Thousands of fraudulent sessions (accounting for 50% of attempted fraudulent account openings) were blocked through automated IP filtering protection.
Conclusion: VPN-based IP obfuscation was rapidly rendered ineffective due to straightforward policy filters and Group-IB IP intelligence alerts.
Stage Two: SIM-Based Roaming and Starlink Obfuscation
Timeline: Q2 2024 – Present
Evasion Tactics:
- Fraud groups began adapting VPN detection and started to purchase SIM cards and eSIMs registered in trusted targeted countries, either through physical purchases or intermediaries.
- They also deployed Starlink terminals (often sourced via European online marketplaces) to mask true IP origins. Starlink devices receive dynamically assigned public IP addresses corresponding to the country where the terminal is officially registered or licensed to operate – often registered to non-META countries – and were used to obfuscate the fraudster’s real IP location.
While these sessions appeared to come from legitimate trusted locations, GPS data often revealed a mismatch – showing activity outside the IP’s expected region.
Detection Response:
- Fraud sessions were cross-checked against GPS coordinates and MCC/MNC-based SIM NetworkCountry (as reported by mobile SIM operator).
- Rule logic triggered on mismatches between device-level location (GPS in Country A) and underlying network location (Country B).
Outcome: This dual-validation method blocked multiple campaigns originating from high-risk fraudster locations using roaming and satellite network infrastructures.
Stage Three: GPS Spoofing on Android and iOS Devices
Timeline: Q2 2024 – Present
Challenge:
Banking applications in the META region enforce mandatory GPS permissions at login, blocking suspicious access from devices physically located outside the country or in high-risk geographies. Early on, this acted as an effective barrier against remote fraud attempts related to previous stages – even fraudsters using advanced IP obfuscation were flagged and blocked through Group-IB’s geo-profiling alerts and detection of blacklisted geohashes.
Adaptation:
Fraud groups developed methods to falsify GPS signals on both Android and iOS platforms, allowing mule devices located abroad to simulate presence within trusted countries. These spoofed locations were strategically selected to avoid triggering location-based velocity or blacklist-based rules.
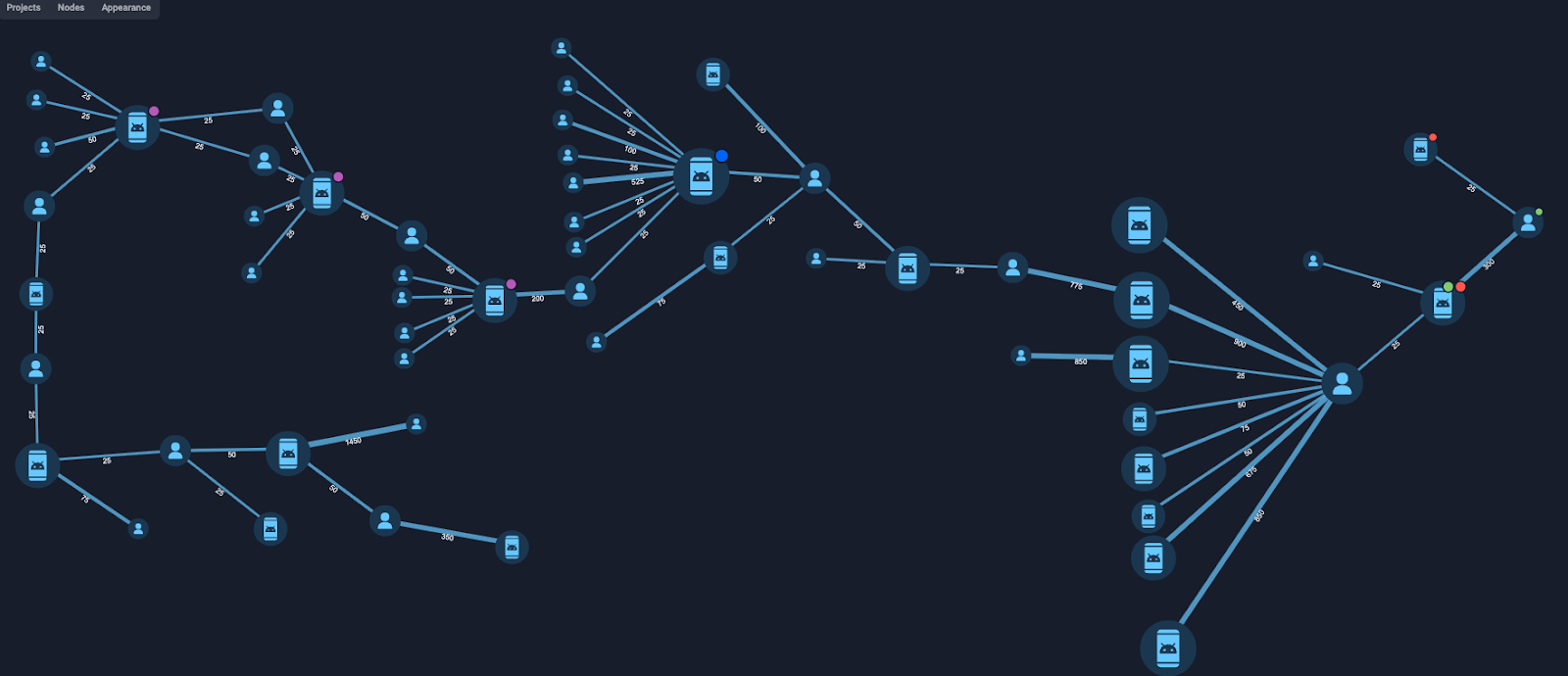
One of the largest mule networks in the META region – the Syrian/Turkish Mule Group – demonstrates how GPS spoofing and roaming eSIMs are used to bypass banking controls. By combining stolen identities with advanced location obfuscation, the group remotely opened hundreds of accounts to launder funds across targeted countries, with flows traced to restricted locations and suspected extremist financing links. Figure 2 illustrates the threat profile of this group and its tactics.

Figure 2: Mules from Syria and Turkey Threat Actor profile
Group-IB customers can access our Threat Intelligence Portal for more information about the Syrian/Turkish mule group.
Detection Response:
Group-IB’s mobile fraud protection SDK includes advanced mechanisms to detect abnormal or tampered GPS signals on both Android and iOS devices—regardless of the spoofing method. Sessions were flagged and investigated when declared GPS data showed inconsistency with device or network-level signals.
Result:
- New mule identities within their first login session were detected through this logic.
- Geospatial risk intelligence was updated in real time to deny access with GPS spoofing anomalies.
- These capabilities remain effective across both major mobile operating systems.
Devices initially active in high-risk blacklisted geolocations began appearing in internal regions of trusted targeted countries with spoofed GPS.
Indicators:
- Same device Universally Unique Identifiers (UUIDs) being reused in different countries (based on GPS data).
- Duplicate coordinates, abrupt GPS changes (user teleportation), and inconsistent patterns.
- Sudden activity from devices in trusted country districts.
- Spike in fraudulent session attempts inside trusted countries (see Figure 3).
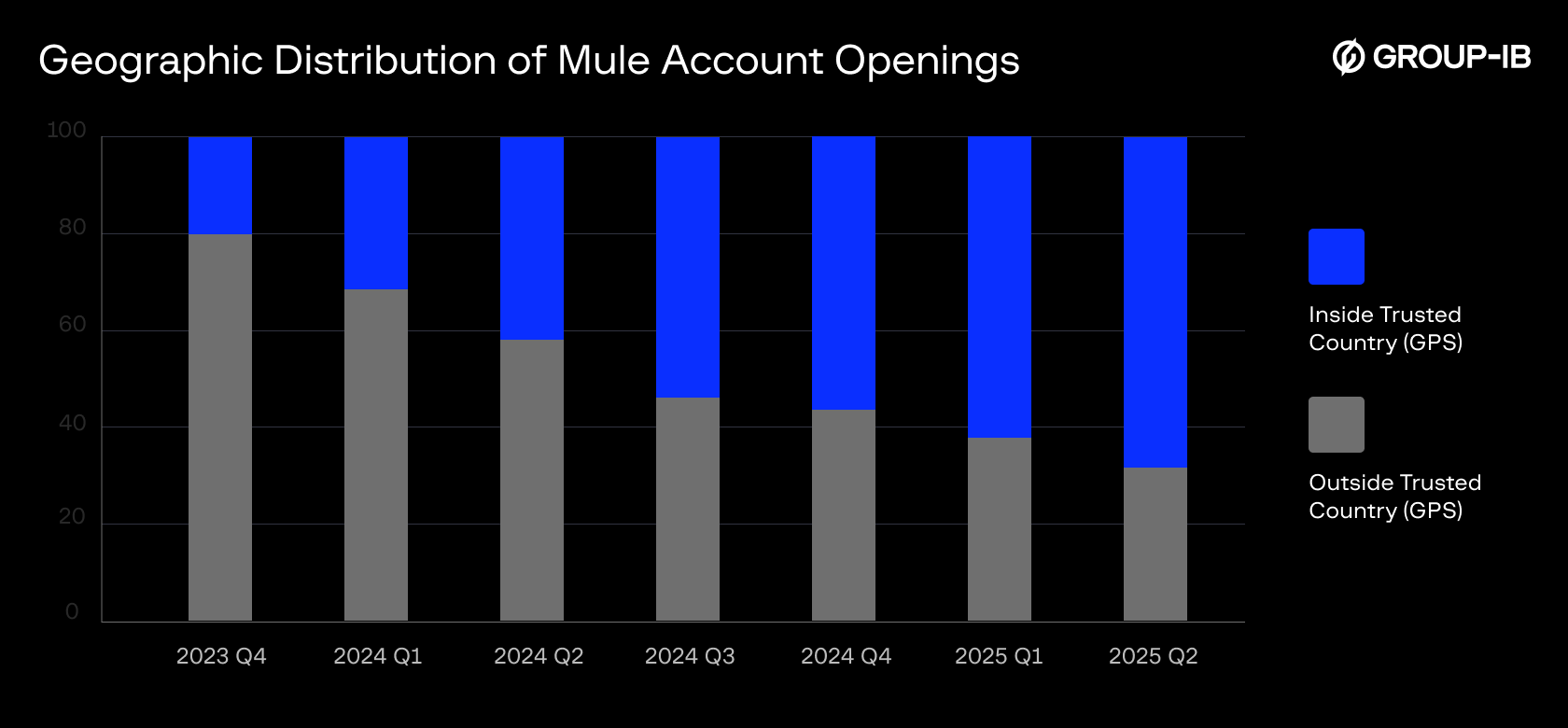
Figure 3: Surge in fraudulent account activity linked to GPS spoofing within trusted regions
The picture above illustrates the fraudsters adaptation strategy to GPS restrictions methods implemented. Such change of trend can indicate a presence of fraudulent users enabled GPS spoofing methods on smartphones to bypass geo restrictions of the banking apps.
Countermeasure:
Detection models were enhanced with updated GPS spoofing anomaly detection, real-time geohash blacklists and temporal-spactial profiling models to flag suspicious devices entering trusted zones without a KYC activity trail.
Stage Four: SIM Removal to Evade Telecom-Based Detection
Timeline: Q2 2024 – Present
Technique Observed:
As banks enhanced detection based on mismatches between GPS data and SIM network codes (MCC/MNC), fraudsters began removing SIM cards entirely from Android devices to evade telecom fingerprinting. These SIM-less devices connected to the internet via Wi-Fi hotspots, typically from nearby roaming-enabled phones, masking their network origins while maintaining internet access.
Result:
- Surge in “No SIM” flagged sessions, often originating from IP blocks previously associated with legitimate behavior.
- Clear shift toward burner device operations supported by hotspots-tethered phones.
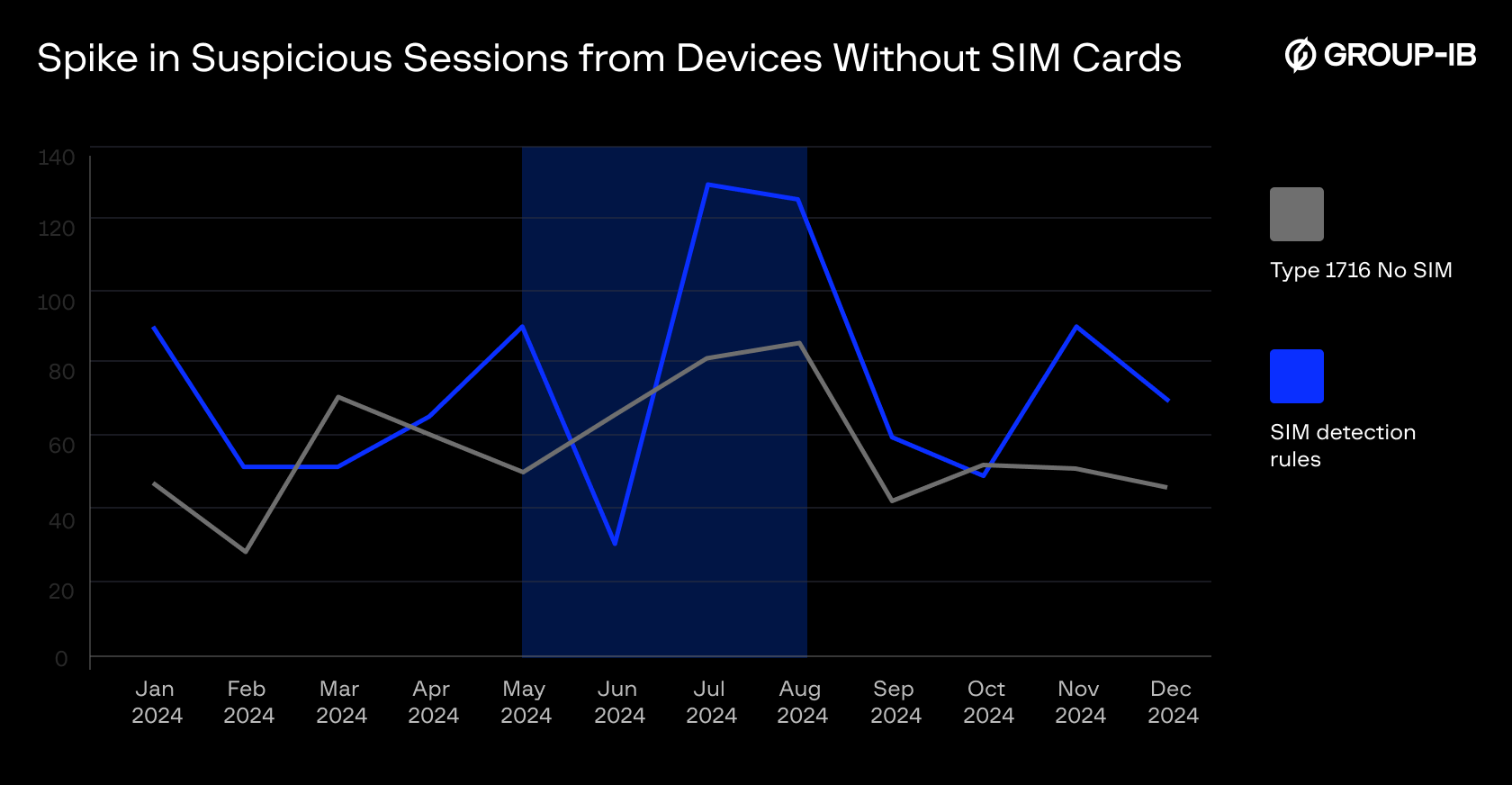
Figure 4: Increased number of “No-SIM” suspicious sessions
Stage Five: Layered Mule Account Access – Credentials Handoff After Legitimate Use
Timeline: Q4 2024 – Present
Tactic Overview:
Fraud networks have evolved beyond one-off account sales into highly structured fraudulent operations designed to mimic legitimate business activity. In this phase, fraud groups began recruiting individuals – often temporary workers or residents physically located in trusted jurisdictions – to open bank accounts in-person after successfully passing KYC procedures.
These recruits,known as first-layer mules, initially maintained clean behavioral profiles: logging in to the accounts from their own devices, avoiding any high-risk actions, and allowing systems to register them as low-risk users. This trust-building phase typically lasts for one to two weeks, serving to build credibility.
Once this trust was established, account credentials were silently handed over to second-layer operators located abroad, who then remotely executed fraudulent operations – such as unauthorized fund movements, laundering sequences, or synthetic merchant flows.
The Modern Twist: Commercial Camouflage
Recent intelligence reveals a shift from clear-cut fraud (e.g., direct offers to sell accounts) to schemes camouflaged as international business ventures. Fraudsters now pose as professional entities offering “partnerships” and “commission-based collaborations,” complete with documentation and backstories involving foreign investment, corporate expansion, or legal stock transactions.
Common tactics include:
- Region-based commission structures
- Reimbursement of travel expenses for formal meetings
- Documentation that mimics regulatory compliance and due diligence
- Corporate-style explanations masking illicit intent
This business camouflage makes detection significantly more difficult, as the laundering behavior is framed within what appears to be standard business operations.
To illustrate how these schemes unfold in real-world environments, Group-IB researchers collected evidence from social media and encrypted messaging platforms where such activities are actively coordinated. The screenshots below (see Figure 5) captured from underground banking sales groups – reveal how account trading and laundering recruitment are being openly discussed.
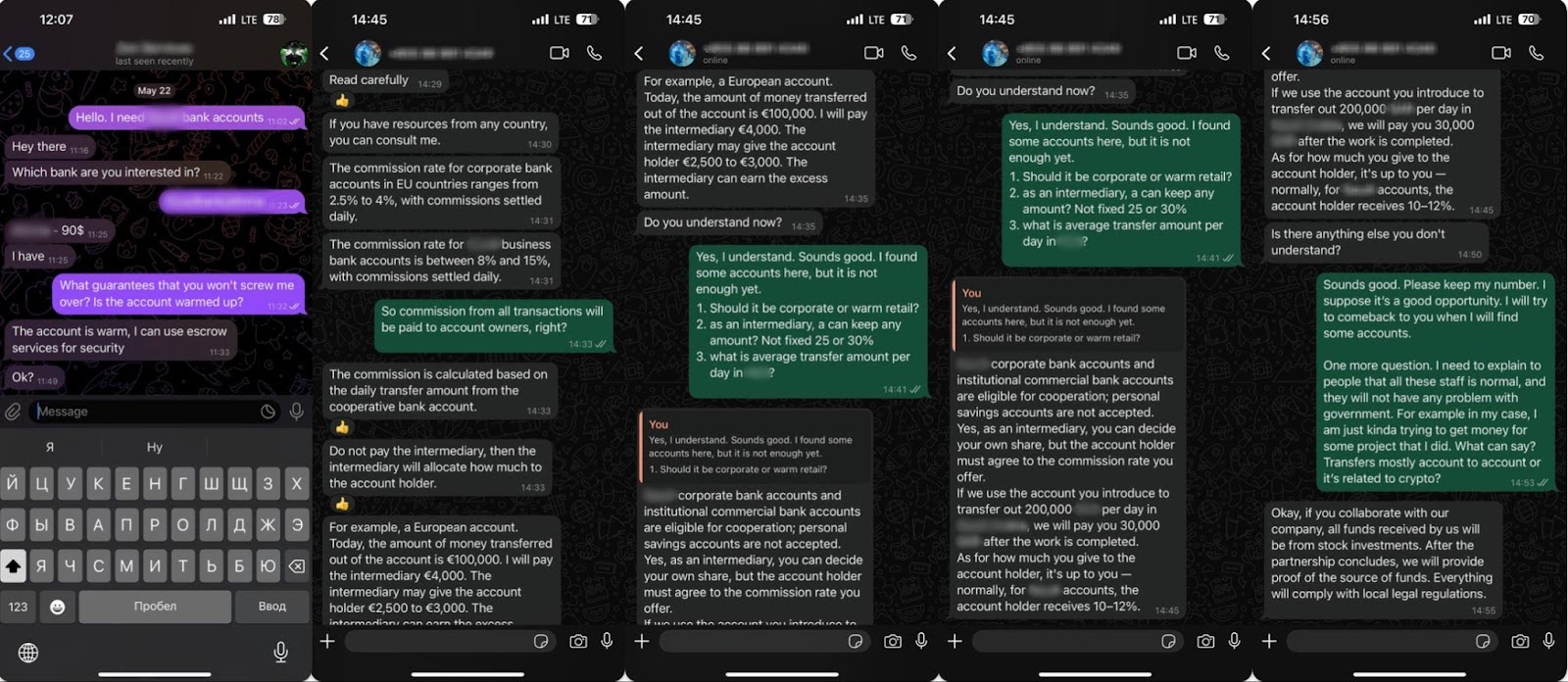
Figure 5: Underground account trade in messaging app
Detection Indicators:
Group-IB systems identified several red flags triggered during second-layer access:
- Sudden login from a new, previously unseen device
- Access from a new device with multiaccounting patterns
- First access attempt from a new device coming from an untrusted or high-risk geo-IP
- Rapid onset of suspicious transaction behavior (velocity, value, recipient risk)
- Sharp deviation from the initial access pattern of the original KYC user
Risk Implication:
This layered approach transforms the fraud lifecycle from “suspicious behavior → laundering” into “legitimate behavior → laundering → again legitimate-like patterns.” If detection occurs only after fraud execution, first-layer participants may present themselves as victims of compromise, complicating attribution. Distinguishing between unwitting users and complicit actors becomes a significant analytical challenge.
Despite this sophistication that creates an appearance of legitimacy in early sessions, behavioral analysis and device fingerprinting still provide critical signals helping to detect – especially when access shifts abruptly cross-border or to high-risk regions.
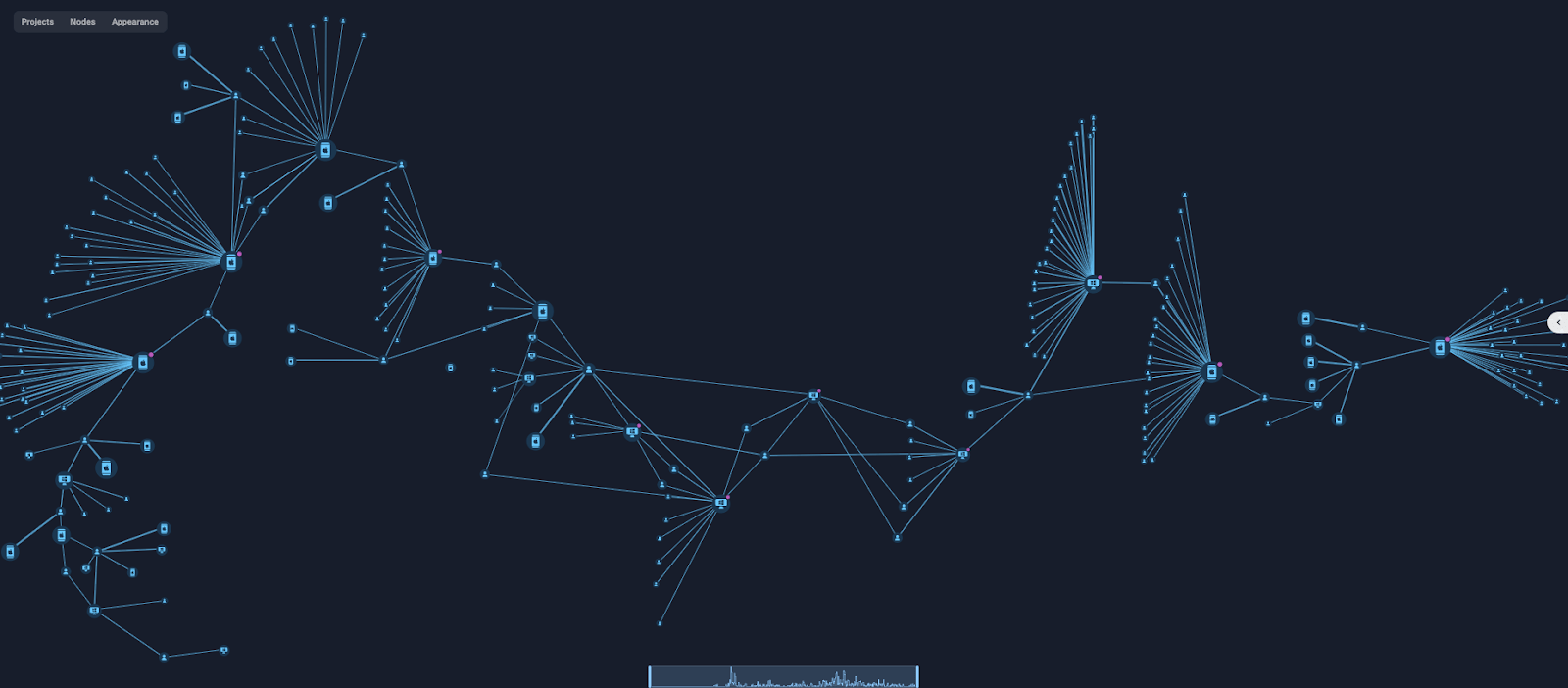
Network-Level Mule Linkage:
Following the credential hand-off pattern outlined in stage five, Group-IB investigators mapped device-to-identity links and found that mule operators act as tightly knit webs. A single phone may support dozens of accounts, and each account can later surface on additional phones, forming a broad, layered network – not merely simple multi-account use.
Figure 6 shows several of these webs: thicker lines mark relationships with the highest usage frequency, highlighting how activity cascades through related identities and foreshadowing the handset movements discussed in stage six.
Stage Six: Physical Device Muling – Shipping Preconfigured Phones Across Borders
Timeline: Q1 2025 – Present
Tactic Overview:
In this advanced stage, fraudsters eliminated the need for credential handover by physically shipping pre-configured phones. First-layer mules based in trusted countries would open accounts and build trust through initial legitimate usage. Instead of sharing login credentials, they ship pre-configured phones to second-layer fraudsters operating abroad.
Figure 7 shows the full operational flow and device-level signature of this cross-border mule network.
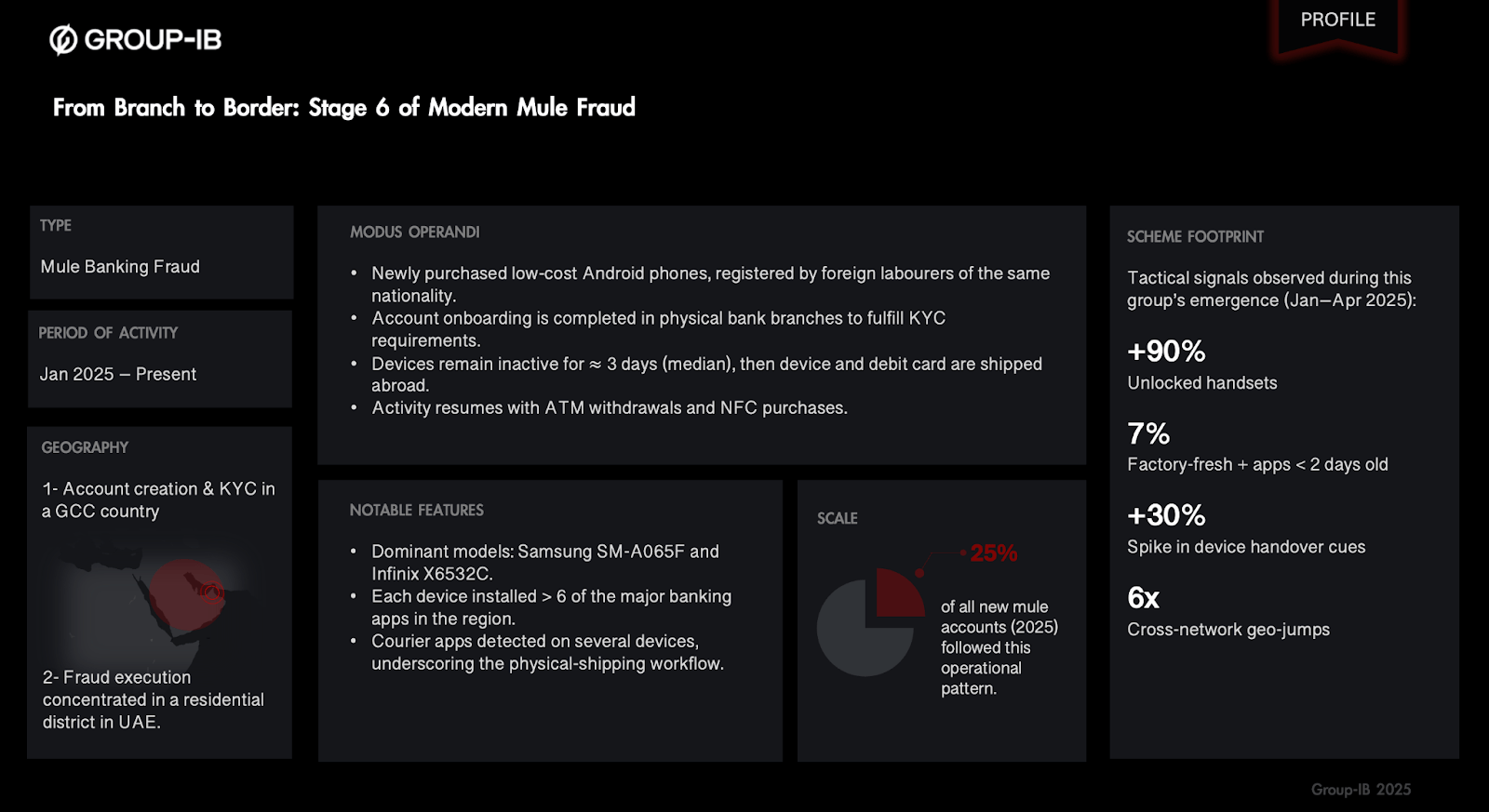
Figure 7: Threat Actor Profile of a Coordinated Mule Network (Stage 6)
Detection Indicators:
- Same device ID shows GPS activity appearing in a new country with high-risk geohash or mismatched location after initial account opening and legitimate usage.
- Suspicious ATM activity detected outside the originating country.
- Sudden shifts in IP geolocation, roaming proxies or IT carrier change.
- Behavioral anomalies: different swipe speed, tap patterns, typing cadence, transaction time and device orientation suggest a different user.
- SIM card country change, SIM card activity mismatches and suddenly switches into roaming mode.
Risk Implication:
This tactic is more advanced due to the absence of a new device fingerprint, making it harder to detect via traditional “new device” rules. However, multi-layer telemetry – especially across IP, SIM, GPS, and ATM channel data – remains effective in exposing these operations combined with changed behavior patterns and unknown previously GPS location change outside trusted countries. For instance, Figure 8, shows how Group-IB Fraud Protection flagged a case where a trusted device – previously registered and used in a trusted country – suddenly initiated transactions from a high-risk geolocation abroad. There was no associated KYC update, travel pattern, or behavioral consistency to justify the shift. Combined with changes in session behavior and environmental signals, the system identified this as a likely device “handover” and responded in real time to prevent fraud.
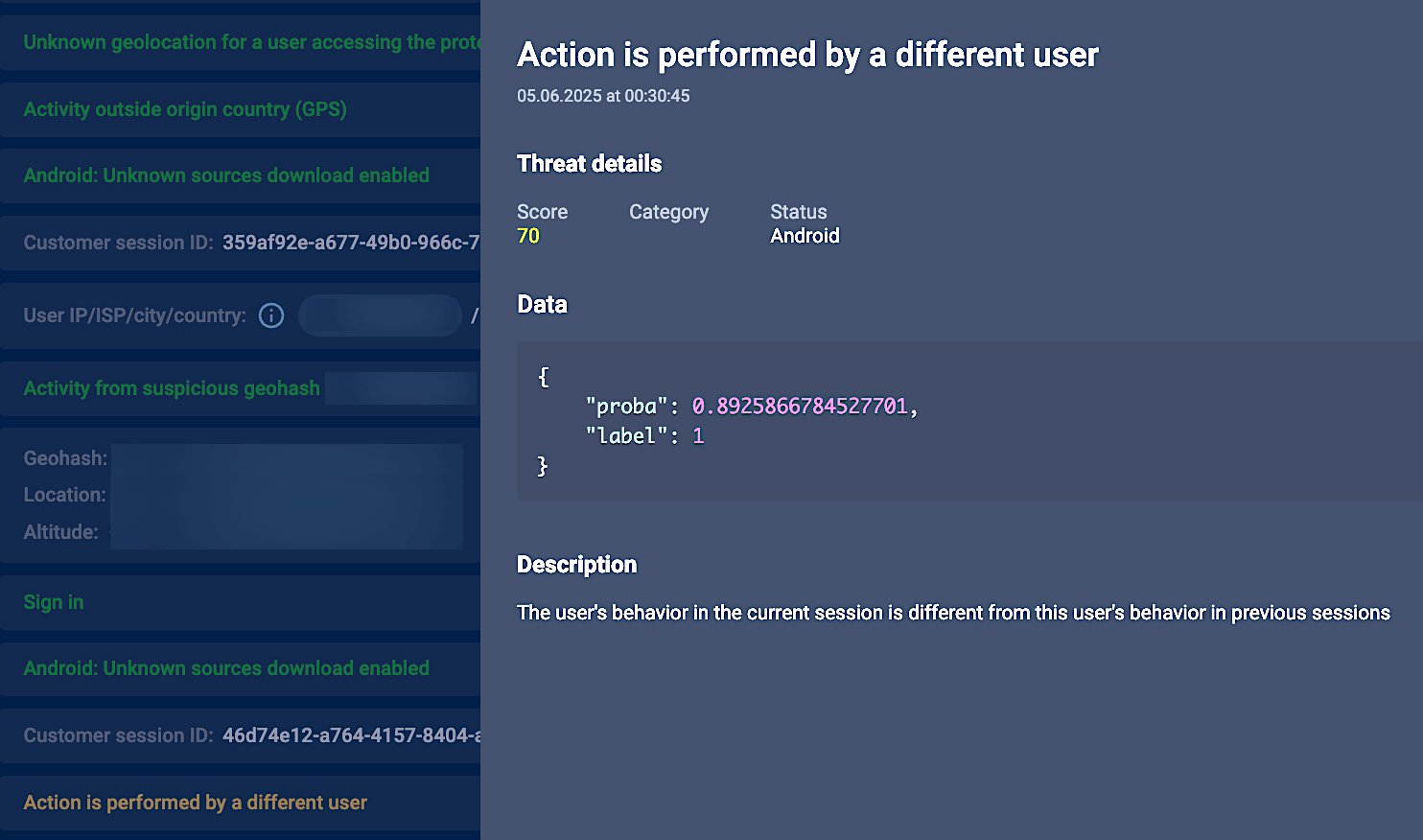
Figure 8: Detection of unknown geolocation outside the country of origin and behavior pattern change for the user’s account on the same device
Behavioral biometrics analysis
Machine learning–based behavioral biometrics are critical in detecting “multi-layered” mule schemes, where a first-tier mule builds account trust before handing the device to a second-tier operator for laundering. By tracking swipe patterns, tap timing, and session behavior, these models can spot shifts revealing when control has been passed to a new user—even if the device remains trusted. Combined with GPS anomaly detection – such as sudden long-distance “jumps”- these models constitute a powerful tool for early fraud detection.
Figure 8 below shows a comparison of heat maps, illustrating the behavioral shift between “first-” and “second-layer” users on the same smartphone device before and after a geolocation change – evidence of account handover.
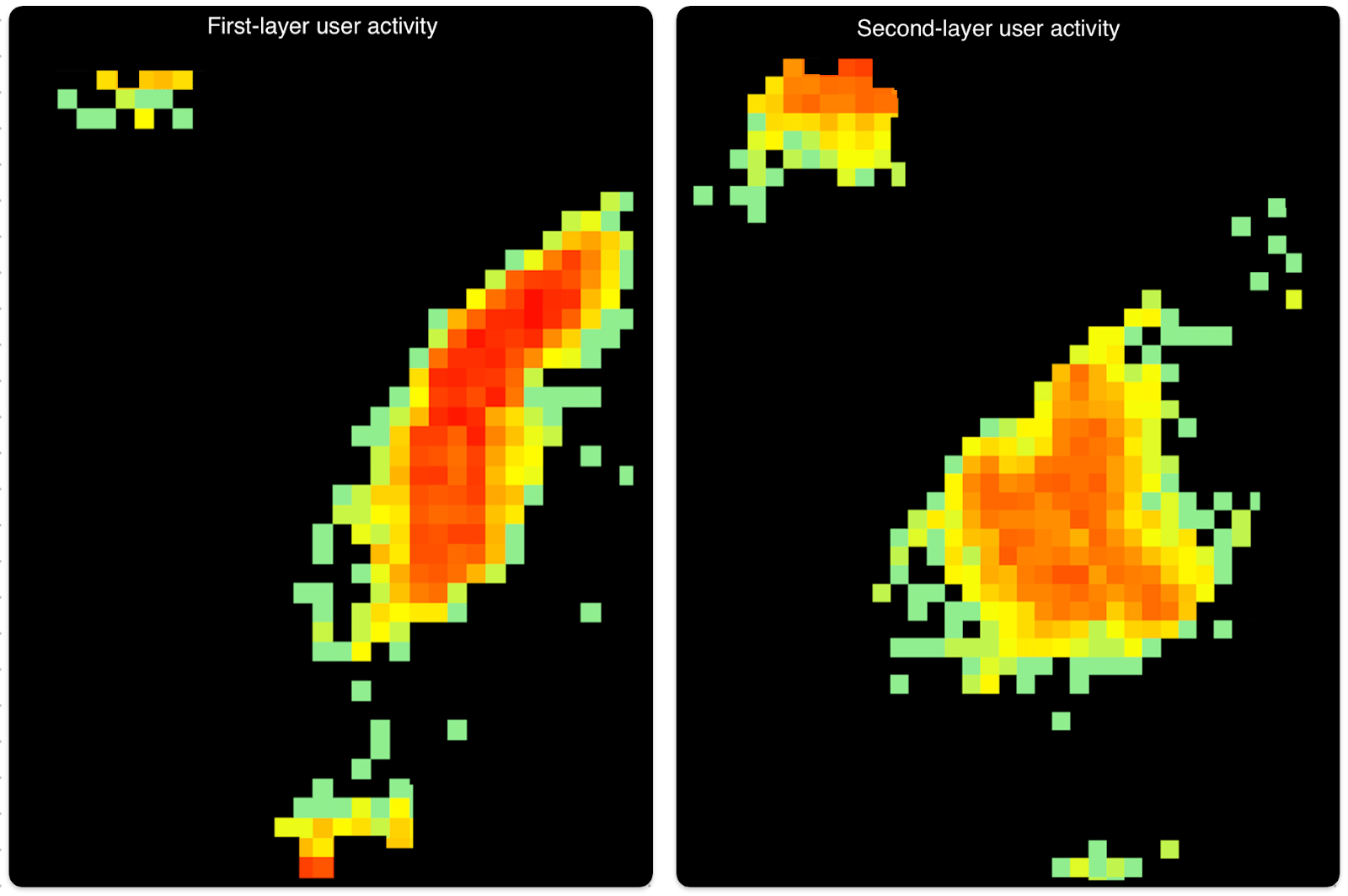
Figure 9. Heatmaps show the behavioral shift between the first- and second-layer users on the same device, following a geolocation change
Emerging Twist:Victim-to-Victim Mule Handoff
One of the most deceptive evolutions in mule operations involves the exploitation of multiple victims in sequence, effectively turning an unsuspecting user into an unknowing mule. This technique makes detection and attribution more complex. How it works:
- Victim A is manipulated – often through phishing, impersonation, or social engineering – into sending money to Victim B.
- Once the transfer is complete, the fraudster quickly engages Victim B, posing as a bank representative or corporate official. The fraudster convinces Victim B that funds were transferred by “mistake “ and “guides” them to forward the funds or share credentials.
- In doing so, Victim B thus becomes an involuntary mule, giving the attacker a fresh, unflagged conduit and a second set of customer details.
While this method attempts to bypass traditional mule detection by delaying the point of compromise, signals such as irregular fund routing paths, behavioral inconsistencies, and device–account mismatches remain strong indicators for detection.
Conclusion
The evolution of mule fraudulent techniques in the META region signals a stark reality: financial fraud is no longer confined to purely digital exploits – it is now fully integrated with real-world logistics, human recruitment, social engineering, AI technologies and physical infrastructure. From commodity VPNs and GPS spoofing apps to physical shipments of preloaded mule devices, fraud networks have matured into agile, distributed ecosystems capable of bypassing static defenses.
As shown in this research, fraud leaves patterns. With the right telemetry, cross-channel intelligence, and real-time anomaly detection remain highly effective. Group-IB’s Fraud Protection Service brings together IP intelligence, geolocation analytics, device integrity checks, and behavioral modeling into a unified detection framework, even sophisticated multi-stage fraud can be exposed and disrupted at scale.
Looking ahead, a new wave of threats is emerging with the misuse of Generative AI and Deepfake technologies. These tools are rapidly lowering the barrier for non-technical actors to launch high-impact fraud campaigns. AI-generated fake identities, synthetic documents, automated Card Testing attacks using automated tools and AI agents, or even Deepfake KYC video verification can accelerate account farming and enable fraud rings to scale operations without requiring deep technical expertise. The result is an increasingly asymmetric threat landscape—where the speed of fraudster adaptation is no longer constrained by skill level, but by access to scalable automation tools.
To stay ahead of this curve, financial institutions must adopt a mindset of continuous intelligence fusion—real-time collaboration between mobile banking security SDKs, device reputation engines, transaction monitoring platforms, and external threat intelligence. Proactive sharing of fraud indicators, advanced signal correlation, and automated response pipelines should form the foundation of a resilient defense strategy.
The following recommendations translate these principles into practical steps that banks and payment providers in the META region can apply to strengthen their anti-fraud posture against rapidly evolving mule tactics.
Recommendations
Deploy Multi-Layered Detection Framework:
- Combine IP intelligence, device fingerprinting, geolocation checks, and behavioral biometrics into a unified, real-time fraud detection system.
- Integrate telemetry data across mobile, web, and transaction channels to ensure comprehensive visibility and detection coverage.
Advance GPS and SIM Detection Techniques:
- Utilize SDK-based detection to identify and flag IP obfuscation and GPS spoofing, SIM removal, or mismatches between GPS coordinates and mobile network country.
- Regularly update geohash blacklists and refine temporal-spatial anomaly detection models to adapt to emerging spoofing methods.
Implement Machine Learning–Based Behavioral Biometrics and User Profiling:
- Deploy machine-learning-based behavioral biometric models that track touch and swipe patterns, typing speed, device orientation, session timing, and other user-specific interaction characteristics.
- Continuously profile users to detect subtle shifts indicative of device handover or fraudulent activity.
Fuse Intelligence Across allChannels in Real-Time:
- Establish real-time collaboration between mobile security SDKs, transaction monitoring platforms, and external threat intelligence feeds.
- Implement automated workflows to correlate anomalies across different telemetry channels (IP changes, GPS anomalies, new device IDs, behavioral shifts).
Strengthen KYC and Identity Verification:
- Enhance KYC processes to detect synthetic identities and utilize robust video verification technologies to identify Deepfake manipulations.
- Monitor accounts closely during initial trust-building phases, especially when new accounts exhibit minimal or benign activity.
Map Network and Device Linkage:
- Conduct regular linkage analysis to detect shared devices, multi-account behaviors, and credential hand-offs.
- Use graph-based analytics to visualize and disrupt tightly-knit mule networks and prevent cascading fraudulent activities.
Continuous Fraud Threat Intelligence Sharing:
- Participate in collaborative fraud intelligence-sharing networks with other financial institutions and cybersecurity firms.
- Regularly update internal fraud analytics systems based on external fraud indicators, threat alerts, and industry intelligence.
Adopt Proactive AI-Driven Fraud Response:
- Leverage AI-driven anomaly detection and automated fraud response systems that quickly adapt to new threat patterns and automatically trigger protective measures.
- Continuously refine detection models through supervised and unsupervised machine learning methods to anticipate and adapt to fraudster innovation.
Educate and Spread Awareness:
- Provide regular training and updates for fraud analysts and cybersecurity teams to understand evolving fraud trends, such as device muling, SIM removal, GPS spoofing, and AI-driven threats.
- Educate customers on secure account practices, recognizing fraudulent requests, and maintaining vigilance against evolving threats.
- Emphasize the importance of developing a “fraudster mindset,” predicting potential attacker strategies, and systematically assessing cybersecurity solutions for vulnerabilities and potential bypass methods.