Introduction
While the vulnerability CVE-2023-27532 was made public in March 2023 and subsequently patched by Veeam for versions 12/11a and later for Veeam Backup & Replication software, Group-IB’s Digital Forensics and Incident Response (DFIR) team recently observed a notable incident related to this vulnerability. This blog post delves into the intricacies of a recent ransomware incident involving the emerging threat actor known as EstateRansomware.
Crafted for cybersecurity professionals and anyone that is keen on understanding modern cyber threats, this detailed analysis highlights how quickly the threat actors practiced the exploitation of the recently disclosed CVE-2023-27532 vulnerability (March 2023) to target unpatched Veeam Backup & Replication Software. The blog provides an overview of the attacker’s tactics, techniques, and procedures (TTPs), from initial access via FortiGate SSL VPN to the impact of the ransomware. By reading this blog, readers will be better equipped to recognize and prevent similar threats in their own methods
Key Discoveries in this Blog
- Initial access via FortiGate Firewall SSL VPN using a dormant account
- Deployed persistent backdoor (“svchost.exe”) on the failover server, and conducted lateral movement via RDP.
- Exploitation attempts of CVE-2023-27532 was followed by activation of xp_cmdshell and rogue user account creation.
- Threat actors made use of NetScan, AdFind, and various tools provided by NirSoft to conduct network discovery, enumeration, and credential harvesting.
- Windows Defender was permanently disabled using DC.exe, followed by ransomware deployment and execution with PsExec.exe.
Who may find this article interesting:
- Cybersecurity analysts and corporate security teams
- Threat Intelligence specialists
- Cyber investigators
- Computer Emergency Response Teams
- Cyber Police Forces
Initial Access
T1078 Valid Accounts
T1133 External Remote Services
The initial indication of intrusion occurred in April 2024 when the threat actor pivoted laterally from the FortiGate Firewall through the SSL VPN service to access the Failover server. Before the ransomware attack, there were VPN brute-force attempts noted in April 2024 using a dormant account identified as ‘Acc1.’ Several days later, a successful VPN login using ‘Acc1’ was traced back to the remote IP address 149.28.106[.]252
A Backdoor Hidden in Plain Sight
T1053.005 – Scheduled Task/Job: Scheduled Task
T1571 – Non-Standard Port
In April 2024, multiple VPN connections using ‘Acc1’ originated from United States IP addresses (149.28.106[.]252, 149.28.99[.]61, and 45.76.232[.]205). Shortly thereafter, RDP connections were established from the Firewall to the failover server.
An examination of the Firewall configuration file revealed an existing RDP bookmark that granted access to the failover server. This bookmark, associated with the ‘Acc1’ VPN account, enabled the threat actor to access the failover server via RDP without requiring additional credentials.

Figure 3 RDP bookmark of Compromised VPN user
During the remote session, the threat actor deployed a persistent backdoor named “svchost.exe” and set up a scheduled task to ensure its daily execution. After installing the backdoor, the threat actor disconnected from the VPN tunnel, and no further logins were observed. To regain access to the network, the threat actor utilized the unnoticed backdoor to re-establish a foothold.
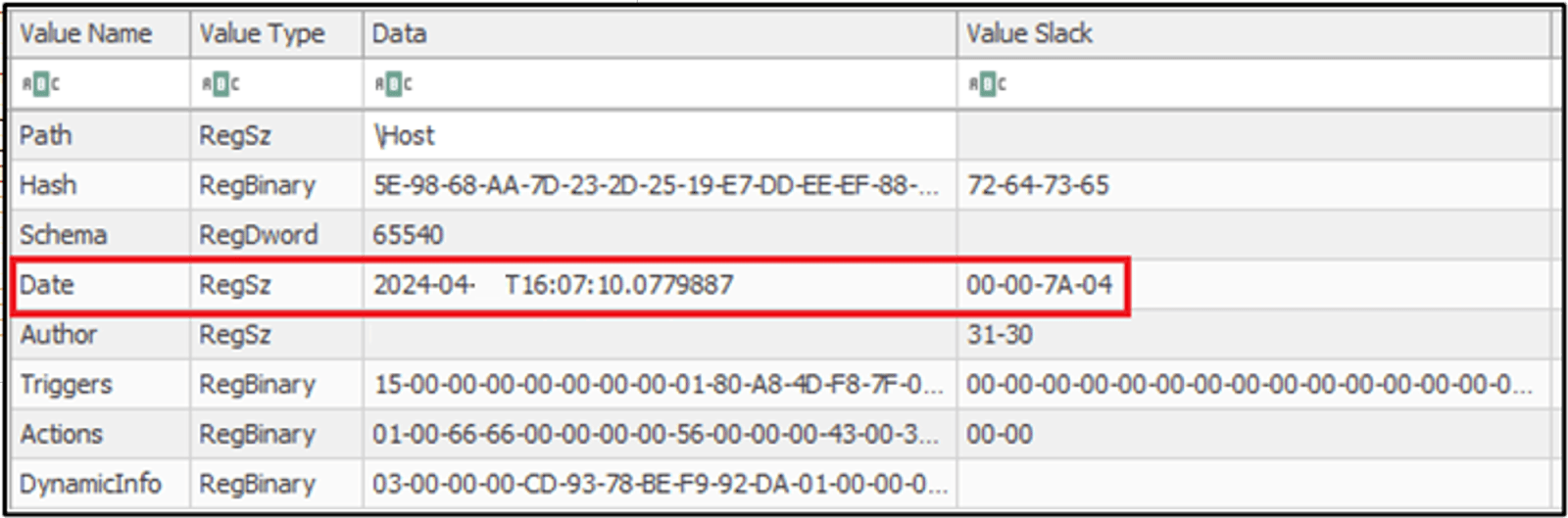
Figure 4 SOFTWARE registry Scheduled Task
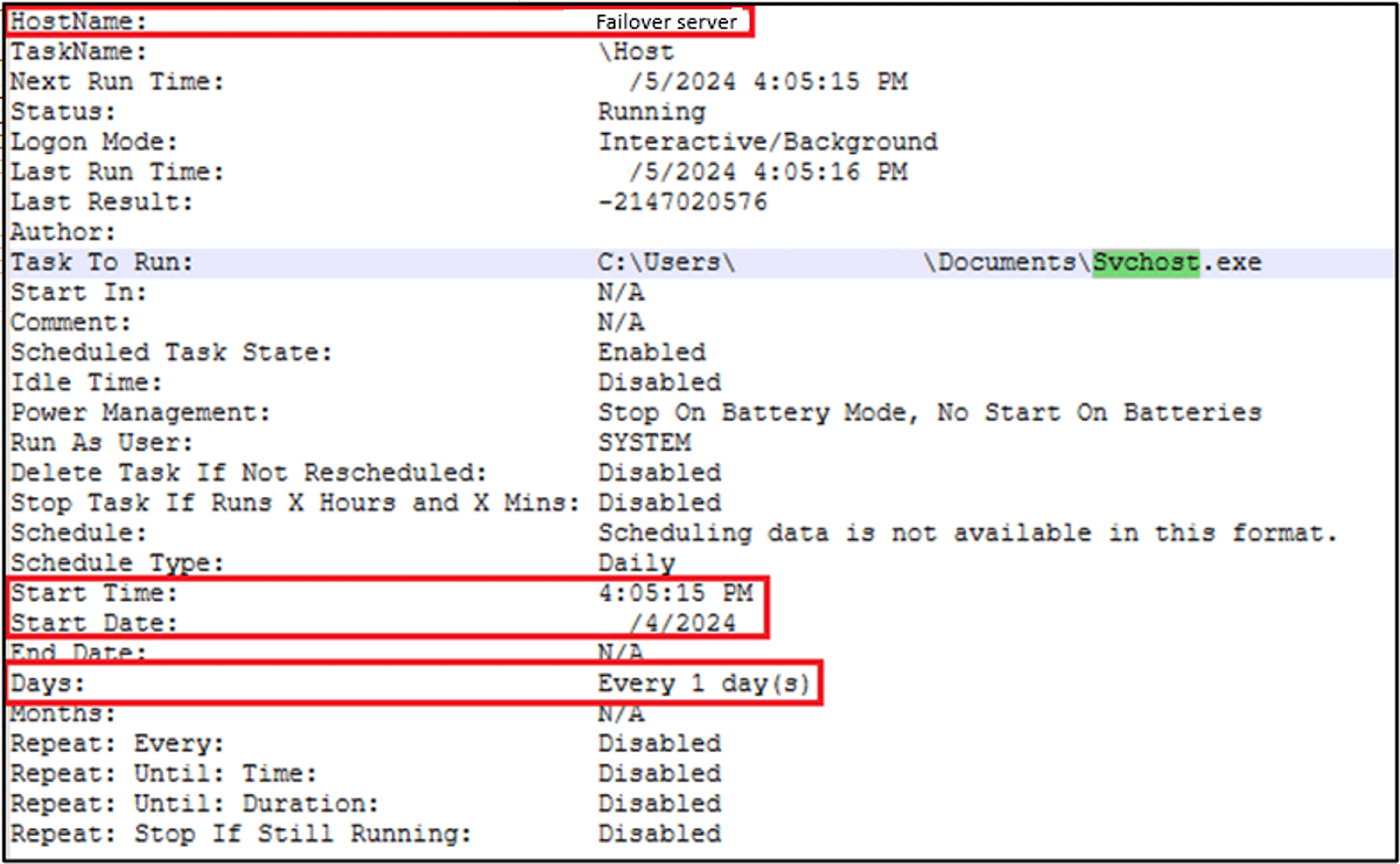
Figure 5 Details of svchost.exe Scheduled Task
An in-depth examination of active network connections on the failover server by our DFIR team uncovered connections to IP address 77.238.245[.]11 through an uncommon port, 30001. Further analysis of ‘svchost.exe’ confirmed that 77.238.245[.]11:30001 functions as a command and control (C2) address. This backdoor establishes a reverse tunnel using the HTTP protocol to connect back to the C2 server, enabling the threat actor to remotely execute commands on the failover server.
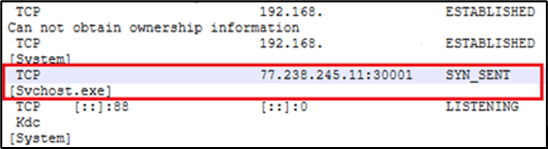
Figure 6 Connection to C2 Address from Failover Server
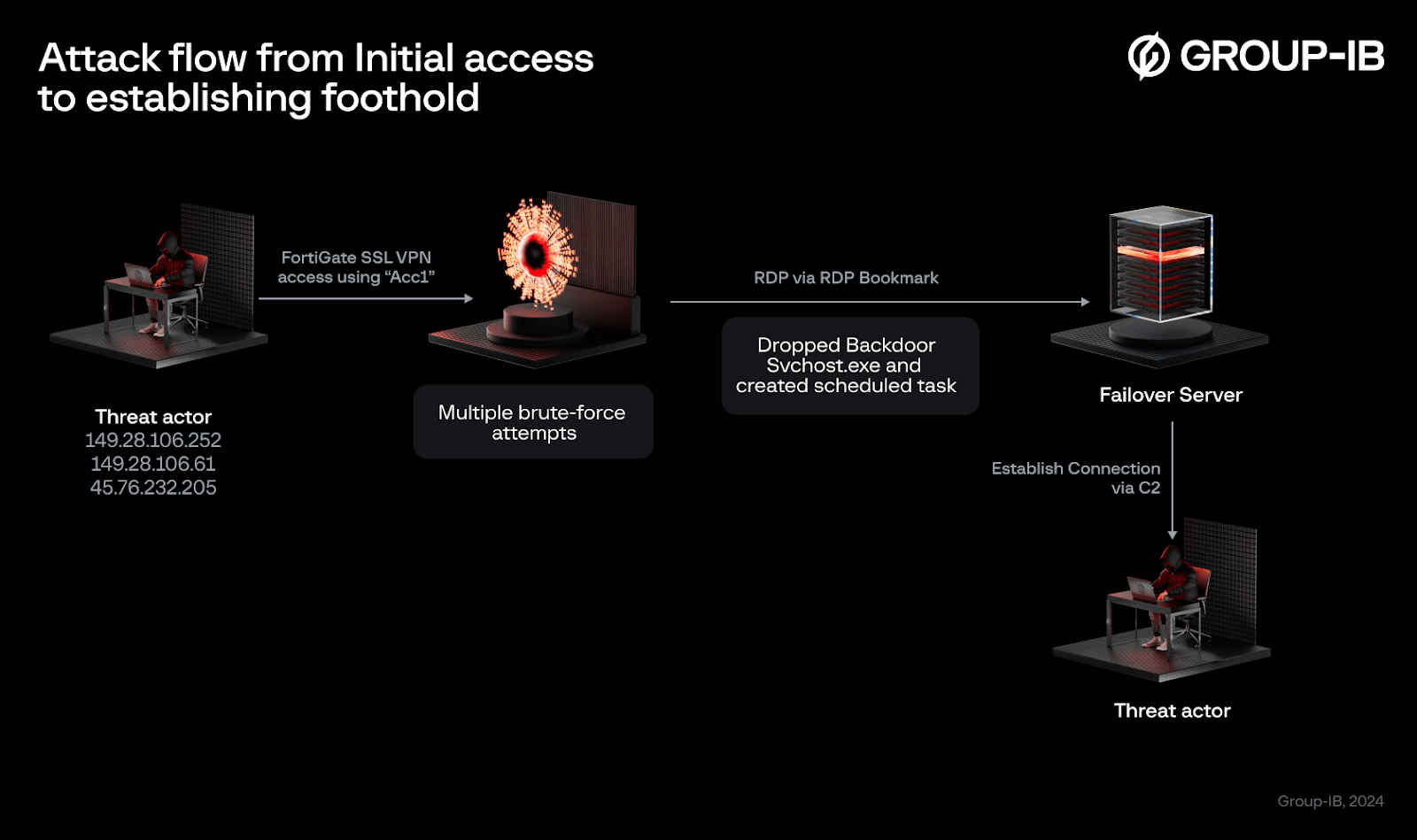
Attack flow from Initial access to establishing foothold
Preparing for the Big Attack
T1505.001 – Server Software Component: SQL Stored Procedures
The following day, the threat actor pivoted from failover server to file server via RDP and began engaging in multiple malicious activities. Based on the files accessed by the threat actor, their primary focus seemed to be on harvesting credentials and exploiting vulnerabilities in Veeam Backup & Replication software. Some of the artifacts related to these activities are:
- C:\Users\[redacted]\Downloads\veeam-creds-main folder
- C:\Users\[redacted]\Downloads\Debug\Debug\net6.0\CVE-2023-27532.exe
- C:\Users\[redacted]\Downloads\Debug\Debug\Veeamhax folder
Threat actor’s intent to execute ‘Veeam-creds-main’ was logged in the Windows PowerShell event log. According to the project maintained by sadshade on GitHub, successful execution would allow the threat actor to obtain passwords from the Veeam Backup and Replication credential manager.
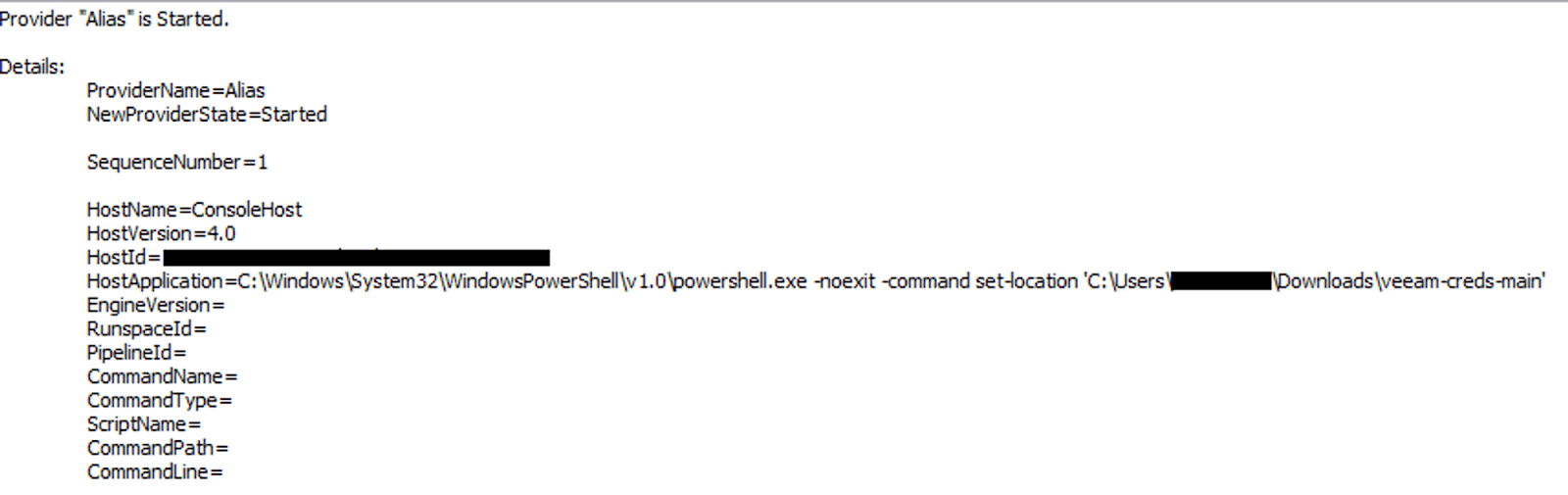
Figure 7 Windows PowerShell Event Log Event ID 600
There is a strong likelihood that CVE-2023-27532.exe and VeeamHax are linked to the Proof of Concept published by Horizion3 and sfewer-r7 on GitHub. Both the file server and backup server were identified to be running vulnerable versions of Veeam Backup & Replication: v9.5.2855 and v9.5.0.1922, respectively.
Analysis of the Windows Application event log revealed an attempt to execute CVE-2023-27532.exe, which resulted in a software crash.
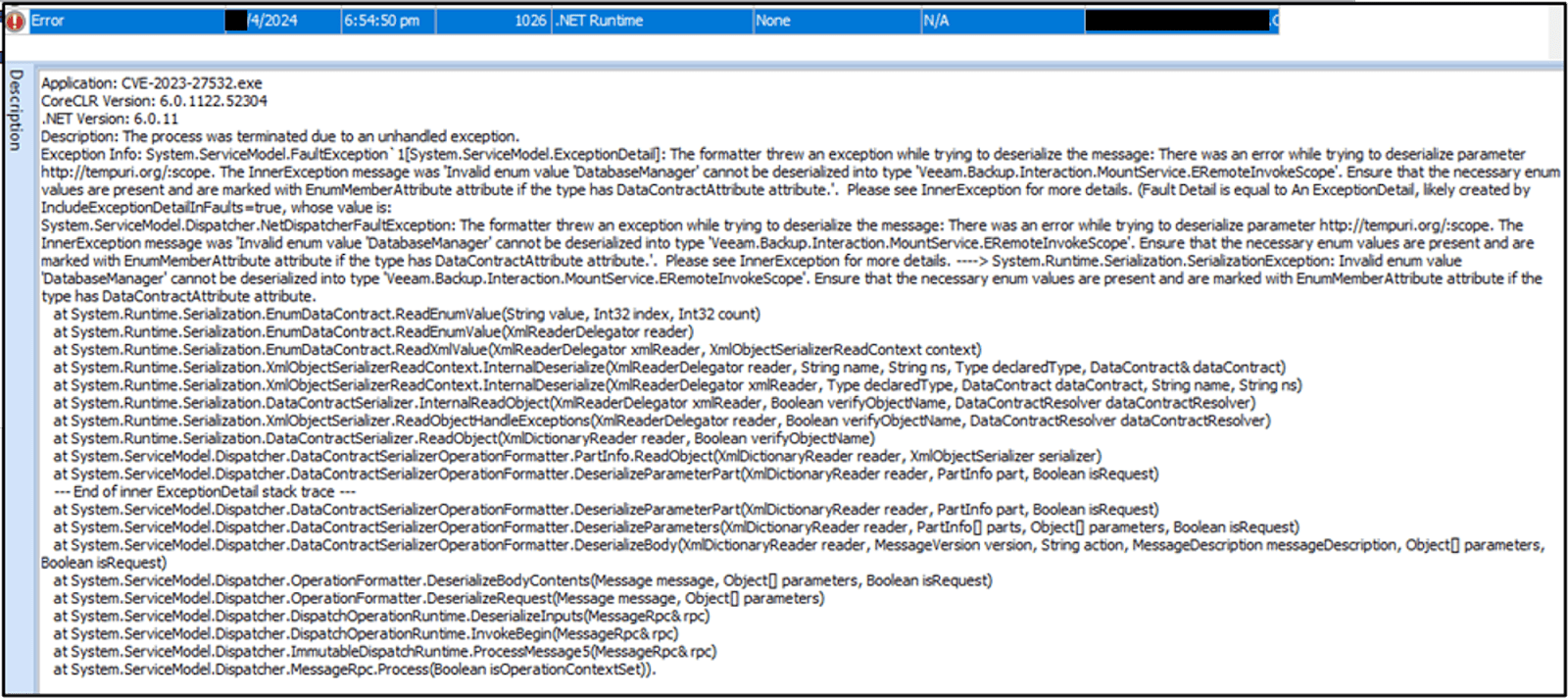
Figure 8 Software Crashed
Immediately following this crash, the threat actor accessed the VeeamHax folder. With reference to the IOCs for CVE-2023-27532 mentioned in Veeam Community and Attackerkb’s PoC, examination of MSSQL ERRORLOG revealed that 20 seconds after VeeamHax folder was accessed, xp_cmdshell—a stored procedure in SQL Server that allows execution of Windows shell commands from the SQL Server environment—was enabled on the backup server, and an account named “VeeamBkp” was created right after.
| Host | Timestamp | Description |
| Backup server | 04-2024 18:54:50 | CVE-2023-27532.exe crashed |
| File server | 04-2024 18:55:31 | VeeamHax folder accessed |
| Backup server | 04-2024 18:55:51 | Configuration option ‘xp_cmdshell’ changed from 0 to 1. Run the RECONFIGURE statement to install. |
| Backup server | 04-2024 18:55:51 | VeeamBkp account created |

Figure 9 xp_cmdshell enabled
Our analysis of the Svc.VeeamBackup.log did not uncover the essential Indicators of Compromise (IOCs) to determine the successful execution of the attack, primarily because default logging configuration was used. Due to the lack of visibility (i.e., commands/API usage) from the available logs, it was impossible to ascertain whether veeam-creds was successfully executed, or if CVE-2023-27532 had been exploited.
However, given the rapid sequence of events, the flow of execution, and reference made to Attackerkb’s PoC, we assess with high confidence that the threat actor likely successfully exploited the vulnerability in Veeam Backup & Replication. Our hypothesis suggests that this exploitation potentially involved an attack originating from the VeeamHax folder on the file server against the vulnerable version of Veeam Backup & Replication software installed on the backup server (the target of the exploit). This activity facilitated the activation of the xp_cmdshell stored procedure and subsequent creation of the ‘VeeamBkp’ account.
T1555 – Credentials from Password Stores
T1018 – Remote System Discovery
T1087.002 – Account Discovery: Domain Account
From the file server, the threat actor deployed SoftPerfect Netscan along with various password recovery tools from Nirsoft. These tools were used to scan the network, gathering information such as alive hosts, open ports, file shares, and harvest credentials. Additional credential harvesting was conducted on the backup server through the newly created ‘VeeamBkp’ account. With the collected information, the threat actor proceeded to pivot laterally to the Active Directory (AD) server via RDP for further network scanning.
From the AD server, AdFind, a command-line query tool that can be used for gathering information from Active Directory, was downloaded from “hxxp://www[.]joeware[.]net/freetools/tools/adfind/” and used by the threat actor to enumerate domain users.

Figure 10 AdFind Downloaded using Google Chrome
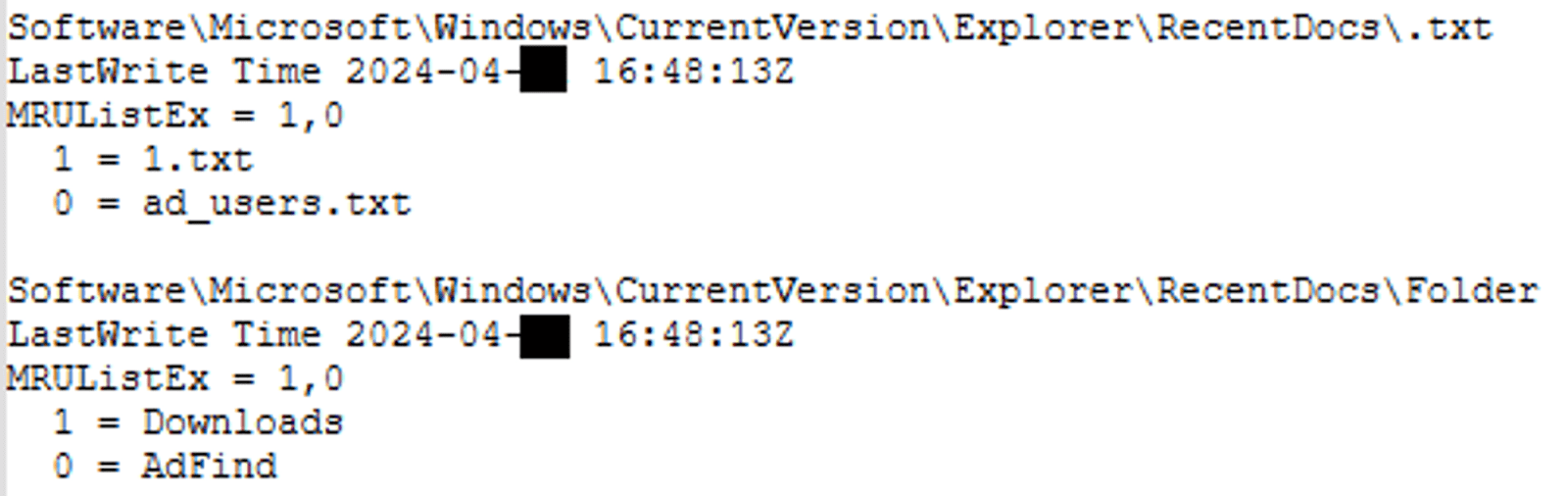
Figure 11 AdFind folder ad_users.txt were recently opened
The Grand Finale
T1562.001 – Impair Defenses: Disable or Modify Tools
T1204.002 – User Execution: Malicious File
T1569.002 – System Services: Service Execution
T1486 – Data Encrypted for Impact
Once the threat actor had gathered sufficient information and established a foothold in the AD server, the threat actor proceeded to move laterally from the AD server to all other servers and workstations using compromised domain accounts.
Execution of binaries necessary for the deployment of ransomware was observed through the analysis of user account registry files (NTUSER), MFT, security event logs and prefetch files. These binaries include:
- DC.exe
- LB3.exe
- PsExec.exe
Upon accessing each host, the threat actor disabled Windows Defender and used Defender Control (DC.exe) to ensure its permanent deactivation.
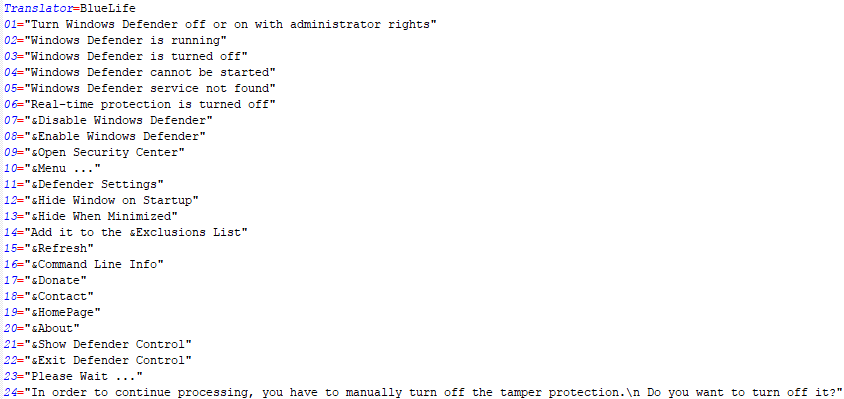
Figure 12 Defender Control configuration file
Shortly thereafter, LB3.exe (EstateRansomware) and PsExec utility was dropped into the “C:\PerfLogs” folder. Within moments of staging these tools, the threat actor logged into the host via PsExec, as PSEXESVC service installation was seen on the host. This login was swiftly followed by the execution of the ransomware file and the creation of the first ransomware note. To avoid detection and hinder forensics investigation efforts, the ransomware cleared essential Windows event logs on all affected servers and workstations.
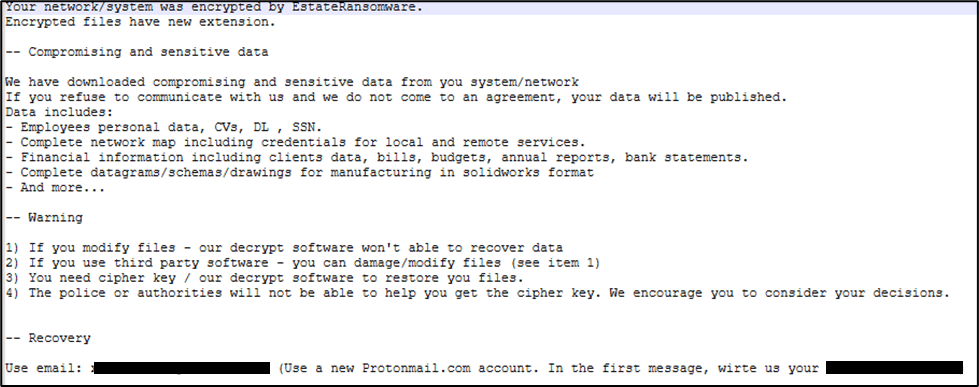
Figure 13 Ransom note

Attack flow overview after initial access to Impact of ransomware
Network Indicator of compromise
- 149.28.106[.]252
- 149.28.99[.]61
- 45.76.232[.]205
C2 connection from Svchost.exe during the incident:
- 77.238.245[.]11:30001
- DC.exe
CB704D2E8DF80FD3500A5B817966DC262D80DDB8
- DC.ini
2C56E9BEEA9F0801E0110A7DC5549B4FA0661362
- Svchost.exe
5E460A517F0579B831B09EC99EF158AC0DD3D4FA
- LB3.exe
107EC3A7ED7AD908774AD18E3E03D4B999D4690C
- netscan.exe
- veeam-creds-main
- CVE-2023-27532.exe
- VeeamHax
- BulletsPassView64.exe
- netpass64.exe
- PasswordFox64.exe
- ChromePass.exe
- WirelessKeyView64.exe
- mspass.exe
- VNCPassView.exe
- WebBrowserPassView.exe
- mailpv.exe
- RouterPassView.exe
- PstPassword.exe
- OperaPassView.exe
- Dialupass.exe
- BulletsPassView64.exe
- ExtPassword.exe
- pspv.exe
- iepv.exe
- SniffPass64.exe
- rdpv.exe
Recommendations
- Monitor and audit accounts regularly. Delete or disable any dormant account to prevent unauthorized access. Implement multi-factor authentication (MFA) for VPN and other remote access services.
- Implement patch management policy to ensure firmwares and softwares used are updated with the latest security patches to protect against known vulnerabilities.
- Segment critical systems and enforce strict firewall rules to limit lateral movement within the network. Disable unnecessary RDP access and restrict it to specific, trusted IP addresses.
- Implement application control on hosts to prevent execution of unauthorized programs. Ensure that only approved security applications are used and running on enterprise systems.
- Implement Endpoint Detection and Response (EDR) solution to detect and respond to suspicious activities such as deployment of backdoors and the use of tools like PsExec.
- Engage in MTH (Managed Threat Hunting) service, to proactively detect unknown threats and sophisticated attacks.
- Subscribe to an incident response retainer service to ensure access to a team of cybersecurity professionals who can effectively respond to any incidents that may occur within the infrastructure.
| Tools | Techniques | |
| Initial Access | T1078 Valid Accounts
T1133 External Remote Services |
|
| Execution | Veeam-creds-main
CVE-2023-27532.exe PsExec.exe |
T1204.002 – User Execution: Malicious File
T1569.002 – System Services: Service Execution |
| Persistence | Xp_cmdshell | T1053.005 – Scheduled Task/Job: Scheduled Task
T1136.001 – Create Account: Local Account T1505.001 – Server Software Component: SQL Stored Procedures |
| Defense Evasion | DC.exe | T1070.001 – Indicator Removal: Clear Windows Event Logs
T1070.004 – Indicator Removal: File Deletion T1562.001 – Impair Defenses: Disable or Modify Tools |
| Credential Access | BulletsPassView64.exe
netpass64.exe PasswordFox64.exe ChromePass.exe WirelessKeyView64.exe mspass.exe VNCPassView.exe WebBrowserPassView.exe mailpv.exe RouterPassView.exe PstPassword.exe OperaPassView.exe Dialupass.exe BulletsPassView64.exe ExtPassword.exe pspv.exe iepv.exe SniffPass64.exe rdpv.exe |
T1555 – Credentials from Password Stores |
| Discovery | Netscan | T1018 – Remote System Discovery
T1087.002 – Account Discovery: Domain Account |
| Lateral Movement | T1021.001 – Remote Services: Remote Desktop Protocol | |
| Command & Control | Svchost.exe | T1571 – Non-Standard Port
T1071.001 – Application Layer Protocol: Web Protocols |
| Impact | EstateRansomware – LB3.exe | T1486 – Data Encrypted for Impact |
































![Successful Login from Remote IP 149.28.1069[.]252](https://www.group-ib.com/wp-content/uploads/1-min-55.png)



