What is Eldorado Ransomware?

Eldorado Ransomware Profile
Eldorado Ransomware is a sophisticated cyber threat that encrypts critical data and locks organizations out until a ransom is paid. Utilizing advanced encryption and multi-vector attack techniques, it targets both Windows and Linux systems. It exploits vulnerabilities via phishing, unpatched software, and remote access tools.
With its constantly evolving, polymorphic code that evades traditional security measures, Eldorado Ransomware demands strong cybersecurity practices, continuous monitoring, and swift incident response to mitigate its potentially devastating impact.
Key Findings
Group-IB investigated all about Eldorado Ransomware to unveil what is it, how it works and the key solution to safeguard the system.
In March 2024, an ad for a new affiliate program was posted on the ransomware forum “RAMP.” The post advertised the availability of a locker and loader, while seeking pentesters to join the team. Group-IB analysts infiltrated the Eldorado group and discovered that the group’s representative was a Russian speaker. The ransomware builder asked for the domain administrator’s password or NTLM ( Windows New Technology LAN Manager) hash and other parameters to generate ransomware samples.
The Eldorado has two versions of the malware in its arsenal – for Windows and Linux. However, this development is unique and does not rely on previously published builder sources. For example, on September 21, 2022, the builder for LockBit 3.0 ransomware was leaked, allowing various threat actors to create their own versions and conduct numerous high-profile attacks using its robust encryption and evasion techniques. Similarly, the Babuk ransomware source code was leaked on September 1, 2021, leading to the creation of multiple ransomware strains by different groups to exploit and exfiltrate data from targeted networks. Notable examples include the LIMPOPO (aka SOCOTRA, FORMOSA, SEXi) ransomware group, BabLock ransomware, and Estate ransomware.
The Eldorado ransomware uses Golang for cross-platform capabilities, employing Chacha20 for file encryption and Rivest Shamir Adleman-Optimal Asymmetric Encryption Padding (RSA-OAEP) for key encryption. It can encrypt files on shared networks using the Server Message Block (SMB) protocol. Key parameters for customization during the build include target networks or company names, ransom note details, and admin credentials.
How did Eldorado Ransomware start?
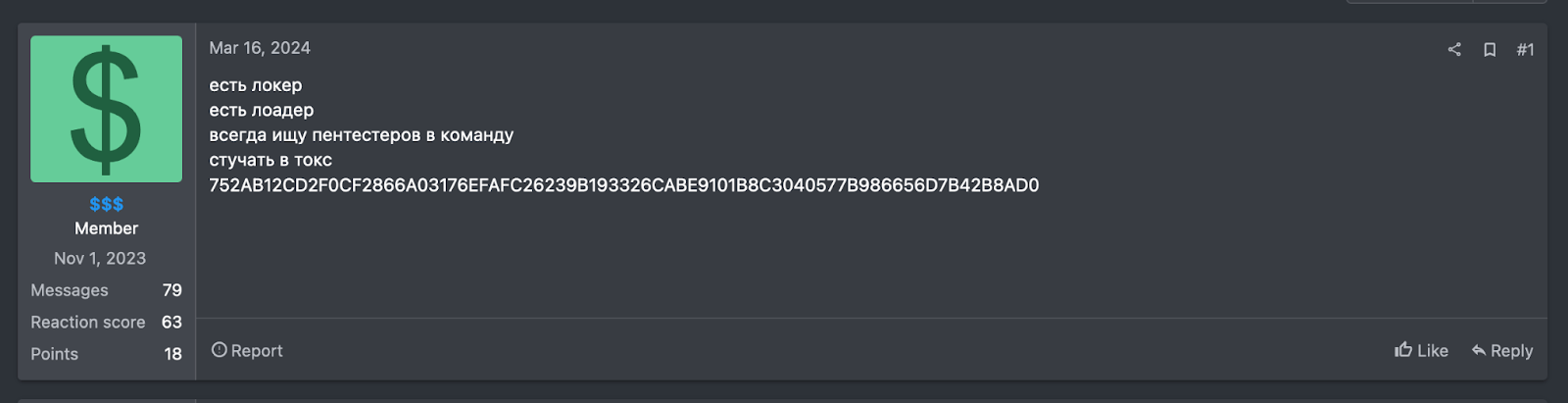
Group-IB conducted a ransomware analysis to find out how it all started. On 16th March 2024, a user going by “$$$” started an affiliate program for the Eldorado ransomware. He published a topic on the underground forum “RAMP”.
Some information about this affiliate program:
The Intruder left his contact in topic:
TOX: 752AB12CD2F0CF2866A03176EFAFC26239B193326CABE9101B8C3040577B986656D7B42B8AD0
Screenshots of the topic:
Original:
есть локер
есть лоадер
всегда ищу пентестеров в команду
стучать в токс
752AB12CD2F0CF2866A03176EFAFC26239B193326CABE9101B8C3040577B986656D7B42B8AD0
Translated text:
There’s a locker.
There’s a loader.
I’m always looking for pentesters for the team.
Hit me up on Tox.
752AB12CD2F0CF2866A03176EFAFC26239B193326CABE9101B8C3040577B986656D7B42B8AD0
Based on our findings, there are posts on the underground forum in Russian, some of which contain expressions that can only be used by native Russian speakers.
Screenshots of the posts suggest that the intruder is a Russian-speaking user
Onion domain for the chat platform used by the Eldorado ransomware group to communicate with their victims:
http://support7iybxvye6f6f5pcl6e6v4axi3u34ghrxljnjpytrw2p7p2iyd.onion
Screenshot of the panel of Eldorado ransomware group:
The attacker grants access only to a chat with victims, which generates ransomware samples as per an affiliate’s instruction. The affiliate must specify the following parameters for generating a ransomware sample: the name of the targeted network or company, the file name for the ransom note and its text, and either the domain admin’s password or its hash.
The Group-IB analysts managed to obtain an encryptor from the developer, which was provided along with the user manual. The encryptor is available in four formats: for esxi, esxi_64, win, and win_64.
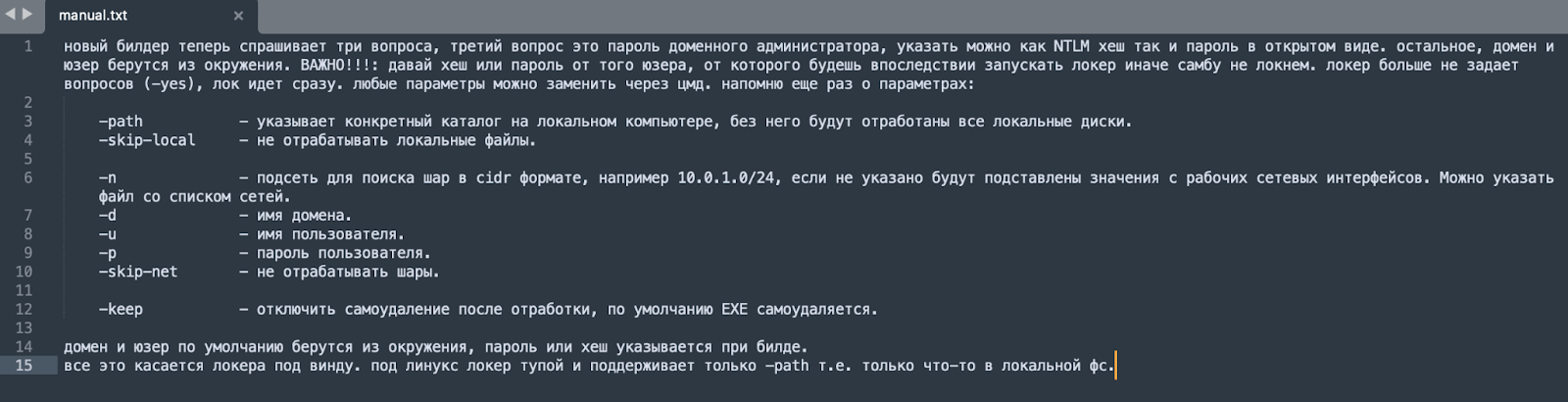
Screenshot of the manual (Original):
The new builder then asks three questions, with the third question being the domain administrator’s password, which can be provided as either an NTLM hash or in plain text. The rest, the domain and user, are taken from the environment.
“IMPORTANT: Provide the hash or password of the user you will later use to run the locker, or we won’t be able to lock the SMB. The locker no longer asks questions (-yes), locking happens immediately. Any parameters can be replaced via CMD. Here are the parameters once again:
– -path specifies a specific directory on the local computer; without it, all local disks will be processed.
– -skip-local to skip processing local files.
– -n subnet for searching for shares in CIDR format, e.g., 10.0.1.0/24. If not specified, values from active network interfaces will be used. A file with a list of networks can also be specified.
– -d domain name.
– -u username.
– -p user password.
– -skip-net to skip processing shares.
– -keep to disable self-deletion after execution; by default, the EXE self-deletes.
The domain and user are taken from the environment by default, and the password or hash is specified during the build. This applies to the locker for Windows. For Linux, the locker is simpler and supports only -path, i.e., it affects only something in the local file system.”
Onion domain of DLS of Eldorado ransomware:
http://dataleakypypu7uwblm5kttv726l3iripago6p336xjnbstkjwrlnlid.onion
Screenshot of DLS of Eldorado ransomware:
Technical Analysis
During the analysis of the encryptor, Group-IB analysts found that the ransomware was written in Golang. There are Eldorado versions for Windows (32bit and 64bit) and Linux (32bit and 64bit). The choice of using the Go programming language could be due to its cross-platform capabilities. Go programs’ ability to cross-compile code into native, self-contained binaries could be a reason why malware authors favored developing in Golang.
All encrypted files will have the extension “.00000001”. During the locking process, the following logs are printed to the console. Here is an example of the output logs when we tried encrypting a single directory.
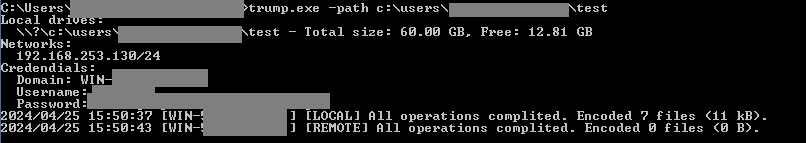
Console logs during encryption
A ransom note titled “HOW_RETURN_YOUR_DATA.TXT” will be written in the Documents and Desktop folder, containing instructions for contacting the TA. The filename and text for the ransom note can be customized during the building process.
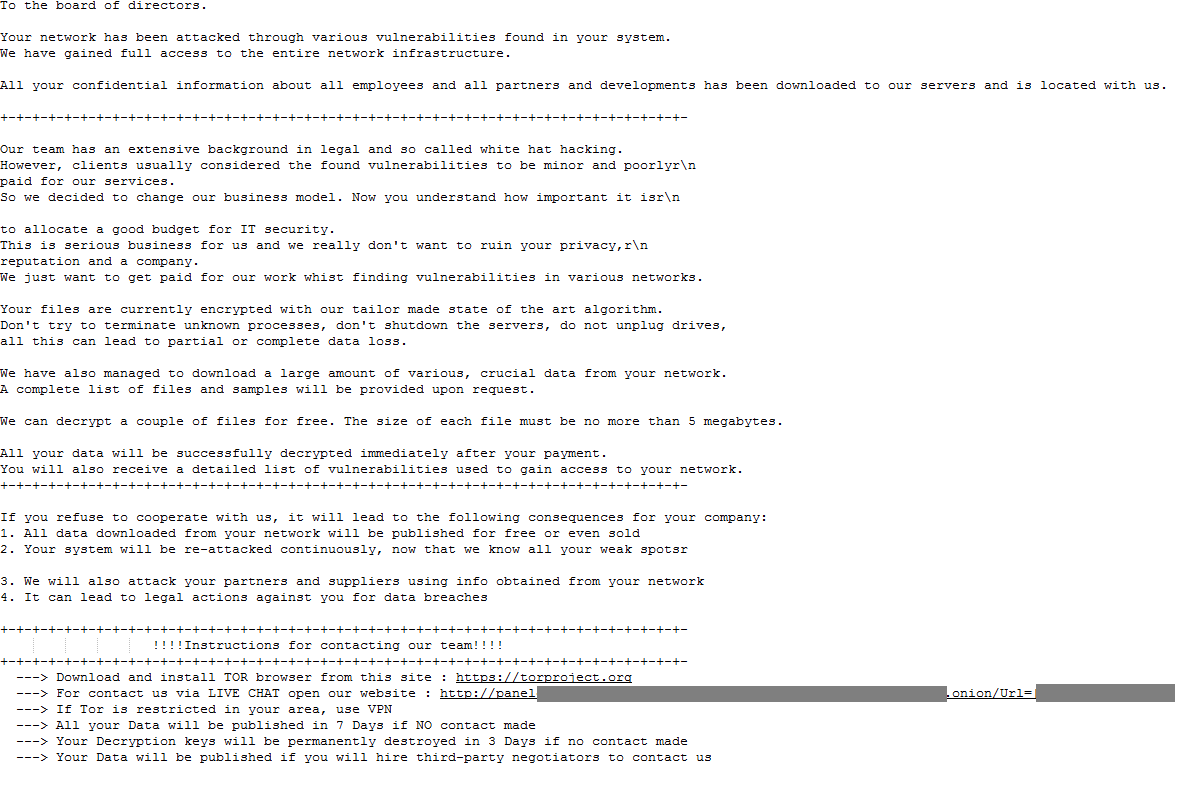
Ransom note with a URL to conduct a live chat with the attackers
Windows
The Windows version of Eldorado ransomware accepts various command line parameters. The table below lists the available options, along with their corresponding descriptions:
| Arguments | Description |
| -path | encrypts all files in the provided directory (and its subdirectories); without it, local disks will be processed instead |
| -skip-local | skip processing local files |
| -n <subnet> | shares in CIDR format, e.g., 10.0.1.0/24. If not specified, values from active network interfaces will be used. A file with a list of networks can also be specified. |
| -d <domain> | Specifies a domain |
| -u <username> | Specifies username for SMB |
| -p <password> | Specifies password for SMB |
| -skip-net | skip processing shares |
| -keep | disable self-deletion after execution; by default, the executable self-deletes. |
Within the binary contains a gzip-compressed configuration blob. The configuration contain the following fields.
type main.EC struct {
K []uint8 // public key
NN string // note name
NT []uint8 // note text
DA string // domain admin pw or hash
}
In the sample which we analyzed, we found that some logs are sent to 173.44.141[.]152 via websockets with Origin header set to “http://logger”.
When supplied with the appropriate user credentials, it can encrypt files on shared networks. It utilizes the SMB protocol and relies on the SMB2/3 client library for this functionality.
Encryption Algorithm
The Eldorado ransomware uses Chacha20 for encrypting files and RSA-OAEP for encrypting the generated key.
For each file, it will generate a 32-byte key and 12-byte nonce, and encrypt the file using Chacha20. The key and nonce will be encrypted with RSA-OAEP with the embedded public key from the configuration, and appended to the end of each file.
Clean up
To remove any traces, the Eldorado ransomware then runs a powershell command to overwrite the encryptor with random bytes before deleting the file. This action will not be performed if “-keep” is specified in the command arguments.
$f=; while(Test-Path -Path $f) { $o=new-object byte[] 10485760; (new-object Random).NextBytes($o); [IO.File]::WriteAllBytes($f,$o); Remove-Item -Path $f; Sleep 1; }
It then removes shadow volume copies at the end of execution. Shadow volume copies are a backup mechanism used in Windows that can be used to recover files if they get lost or damaged, and it is executed via the following command.
vssadmin delete shadows /all /quiet
Windows, programdata, program files, program files (x86), $recycle.bin, all users, winnt, appdata, application data, local settings, boot
ntldr, ntdetect.com, autoexec.bat, ntuser.dat, ntuser.dat.log, iconcache.db, bootsect.bak, bootfont.bin, bootmgr, thumbs.db
.00000001, .exe, .dll, .sys, .msi, .ini, .inf, .lnk
Linux
For Linux, the encryptor is simple and supports only the -path argument. It will only recursively walk through files in the specified directory. The encryption algorithm remains the same as the Windows version.
Conclusion
Despite the widespread awareness and ongoing discussions about the threat of ransomware, cybercriminals continue to find new and effective ways to attack various organizations. The persistent evolution of ransomware tactics and strategies ensures that these malicious actors remain a formidable threat in the cybersecurity landscape.
The Eldorado ransomware group serves as a prime example of this enduring menace. Although relatively new and not a rebrand of well-known ransomware groups, Eldorado has quickly demonstrated its capability within a short period of time to inflict significant damage to its victims’ data, reputation, and business continuity.
Group-IB’s analysis of the Eldorado ransomware reveals that the Eldorado group has managed to develop and deploy a highly effective ransomware builder, which has been used to target both Windows and Linux systems. The ransomware group’s use of Golang for cross-platform capabilities and their detailed encryption methodologies underscore their technical prowess.
Despite law enforcement efforts and increased security measures, ransomware groups continue to adapt and thrive. The ongoing development of new ransomware strains and the emergence of sophisticated affiliate programs demonstrate that the threat is far from being contained. Organizations must remain vigilant and proactive in their cybersecurity efforts to mitigate the risks posed by these ever-evolving threats.
In conclusion, while the names and faces of ransomware groups may change, the underlying threat remains constant. The rise of new players like Eldorado, coupled with the continued success of established groups, highlights the persistent and dynamic nature of the ransomware threat. As these cybercriminals refine their techniques and expand their reach, it is imperative for organizations to stay ahead of the curve with robust security strategies and comprehensive threat intelligence. The battle against ransomware is ongoing, and only through continuous vigilance and adaptation can we hope to counteract this pervasive danger.
Key targets and victim profile of Eldorado Ransomware
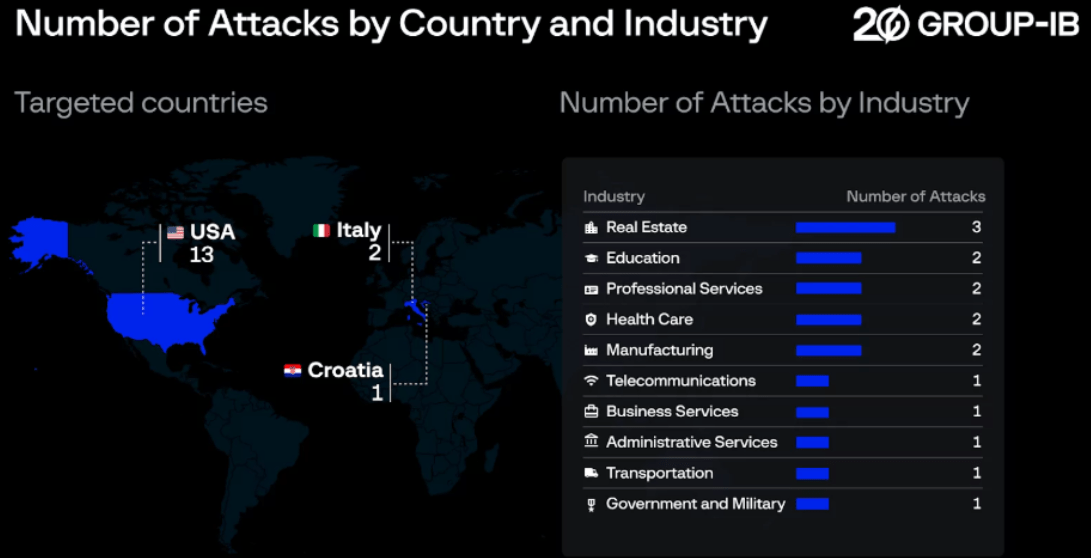
As of June, 2024, 16 companies across various countries and industries have suffered the Eldorado ransomware attacks, with companies in the United States attacked 13 times, contributing up to 81.25% of the total number of incidents. There was also evidence of 2 attacks in Italy (12.5%), and a single attack in Croatia (6.25%).
The most targeted industry is Real Estate with 3 attacks, representing 18.75% of the total. Other affected industries include Education, Professional Services, Health Care, and Manufacturing, each with 2 attacks (12.5% each). Additionally, Messaging and Telecommunications, Business Services, Administrative Services, Transportation, and Government and Military each experienced 1 attack (6.25% each).
This diverse victim profile of the Eldorado Ransomware highlights the pervasive threat it poses, urging organizations across all sectors to reinforce their cybersecurity defenses and adopt proactive risk management strategies.
How organizations can strengthen their cyber defenses
Although ransomware groups have gained notoriety for targeting companies in critical sectors, they are a threat to organizations across all industries. In addition to having new members in its network, ransomware affiliate programs equip members with upgraded tools and techniques. That being said, it is essential that businesses take specific steps immediately to keep their mission-critical operations and data secure. We recommend the following:
- Add more layers of security:
Multi-factor authentication (MFA) and credential-based access solutions help businesses secure their critical assets and high-risk users, making it harder for attackers to be successful. - Install behavioral detection capabilities
Leverage the behavioral detection capabilities of the Endpoint Detection and Response (EDR) solution to help identify ransomware indicators across your managed endpoints, promptly alerting your teams to any suspicious activity for further scrutiny. This proactive approach enables agile detection, investigation, and remediation of both known and unknown threats on your endpoints. - Stop ransomware with early detection
Leverage the behavioral detection capabilities of the Endpoint Detection and Response (EDR) solution to help identify ransomware indicators across your managed endpoints, promptly alerting your teams to any suspicious activity for further scrutiny. This proactive approach enables agile detection, investigation and remediation of both known and unknown threats on your endpoints. - Have a backup strategy
Data backup processes should be conducted regularly as they reduce damage and help organizations avoid data loss following ransomware attacks. - Leverage an advanced malware detonation solution
Organizations should leverage AI-infused, advanced analytics-based solutions to detect intrusions in real-time. Learn how Group-IB’s Managed XDR coupled with Threat Intelligence helps businesses to: gain insights into the unique Tactics, Techniques, and Procedures (TTPs) used by Advanced Persistent Threats (APTs) and other cybercriminal groups and pivot their security strategies accordingly; and enable multi-layered cybersecurity (endpoint, email, web, and network) through automated threat detection and response. - Patch it up
The longer a vulnerability remains unpatched, the greater the risk that it will be exploited by cybercriminals. Security patches should therefore be prioritized, and organizations should also set up a process to regularly review and apply patches as they become available. - Employee Training
The human factor remains one of the greatest vulnerabilities in cybersecurity. Educate employees about the risks relating to the organization’s network, assets, devices, and infrastructure. Organizations should conduct training programs and security drills to help employees identify and report the tell-tale signs of cybercrime (e.g. phishing emails). - Control vulnerabilities:
Do not turn a blind eye to emerging vulnerabilities. Checking your infrastructure annually with a technical audit or security assessment is not only a good habit, it also adds a much-needed layer of protection. Infrastructural integrity and digital hygiene processes should be monitored continually. - Never pay the ransom
In 97% of ransomware attacks, it is impossible to regain access to data without decryption software. Group-IB’s Incident Response experts do not recommend rushing to pay ransoms.Financially-motivated threat actors are driven to make you pay more. Even if one attacker returns your data, another will find out about your willingness to pay, which will lead to an increase in the number of attempted attacks on your company. The best you can do is to contact incident response experts as quickly as possible.
Think you’re equipped to combat ransomware?
Assess weak points in your cybersecurity strategy with the ransomware readiness framework developed by Group-IB Incident Response experts and put their recommendations into action to effectively eliminate those weak points.
File IOCs
| SHA256 | Classification |
| 1375e5d7f672bfd43ff7c3e4a145a96b75b66d8040a5c5f98838f6eb0ab9f27b | Eldorado (32-bit windows) |
| 7f21d5c966f4fd1a042dad5051dfd9d4e7dfed58ca7b78596012f3f122ae66dd | Eldorado (64-bit windows) |
| cb0b9e509a0f16eb864277cd76c4dcaa5016a356dd62c04dff8f8d96736174a7 | Eldorado (64-bit windows) |
| b2266ee3c678091874efc3877e1800a500d47582e9d35225c44ad379f12c70de | Eldorado (32-bit linux) |
| dc4092a476c29b855a9e5d7211f7272f04f7b4fca22c8ce4c5e4a01f22258c33 | Eldorado (64-bit linux) |
Network IOCs
- 173.44.141[.]152