Intended readership
CISOs, Incident Response teams, SOC managers, IT leaders, MSSPs
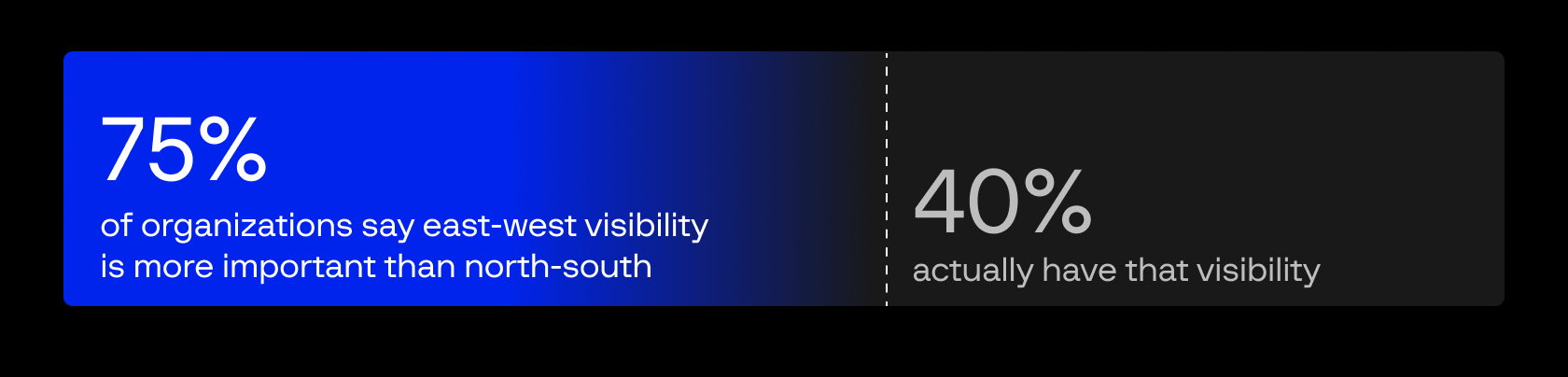
The visibility gap represents one of cybersecurity’s most dangerous contradictions. Security leaders understand where attacks cause damage, but deployment choices often prioritize convenience over comprehensive protection.
The market for network detection and response (NDR) is booming. Gartner reports 18% year-over-year growth and has just issued its first Magic Quadrant for NDR. But growth doesn’t equal coverage. While the market expands, the most critical attack vectors remain hidden in plain sight: inside your own network, where lateral movement, credential theft, and data exfiltration all often unfold undetected.
Why endpoint tools don’t tell the whole story
Endpoint detection and response (EDR) is a powerful tool, but many organizations still treat it like a magic pill. They install the agents, cover the hosts, and assume they’re safe. Some even believe that EDR extends to network and email traffic. Such a mindset creates dangerous blind spots.
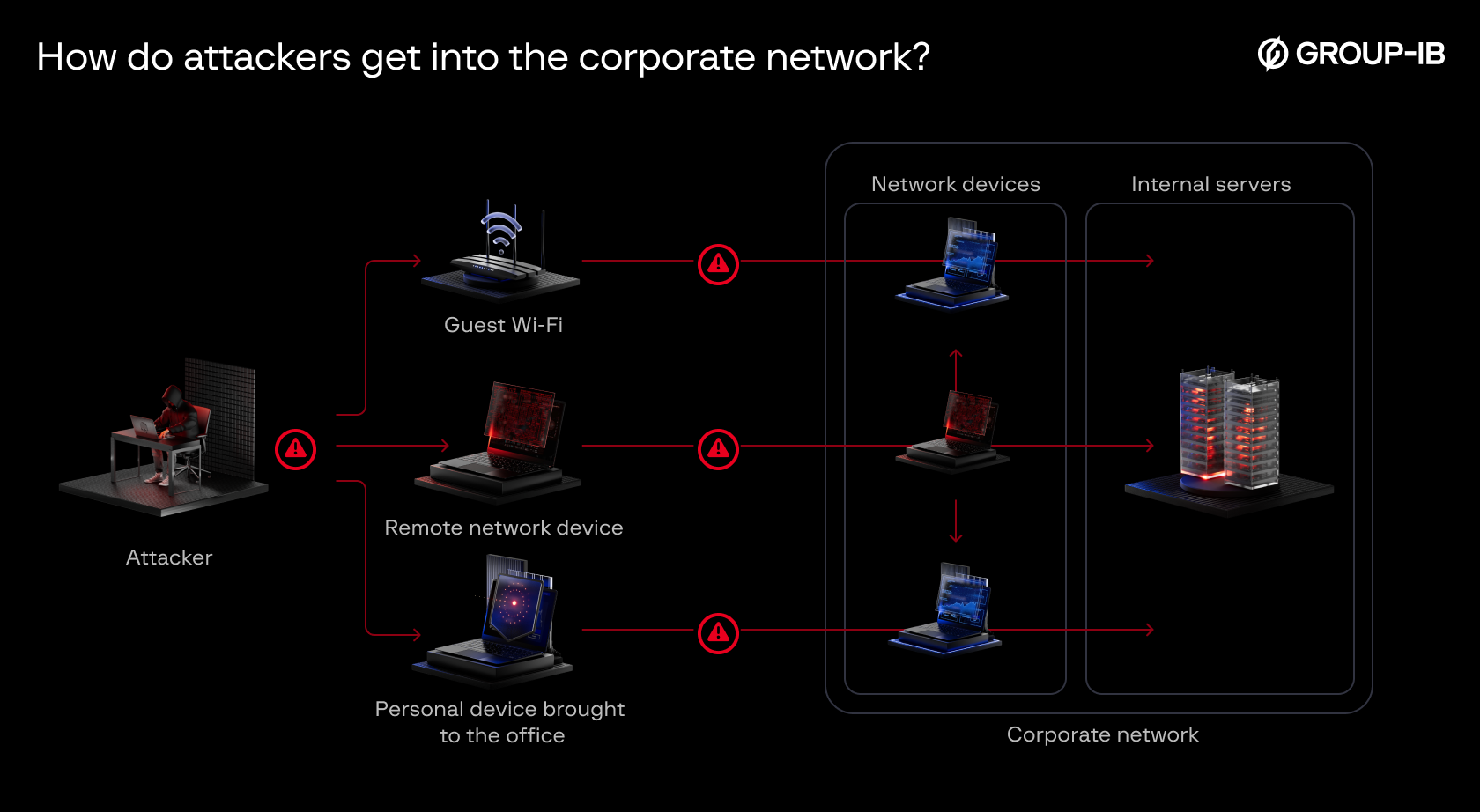
You can’t deploy agents everywhere. Network printers in executive offices store sensitive documents. File servers containing your most valuable data often can’t run EDR agents. IoT devices, routers, and personal devices connecting to corporate networks remain invisible to endpoint protection. Attackers know this and specifically target network printers in CEO offices or drop malware on file servers masqueraded as an Excel document called “salary-increase-sheet-November-2025.xls.”
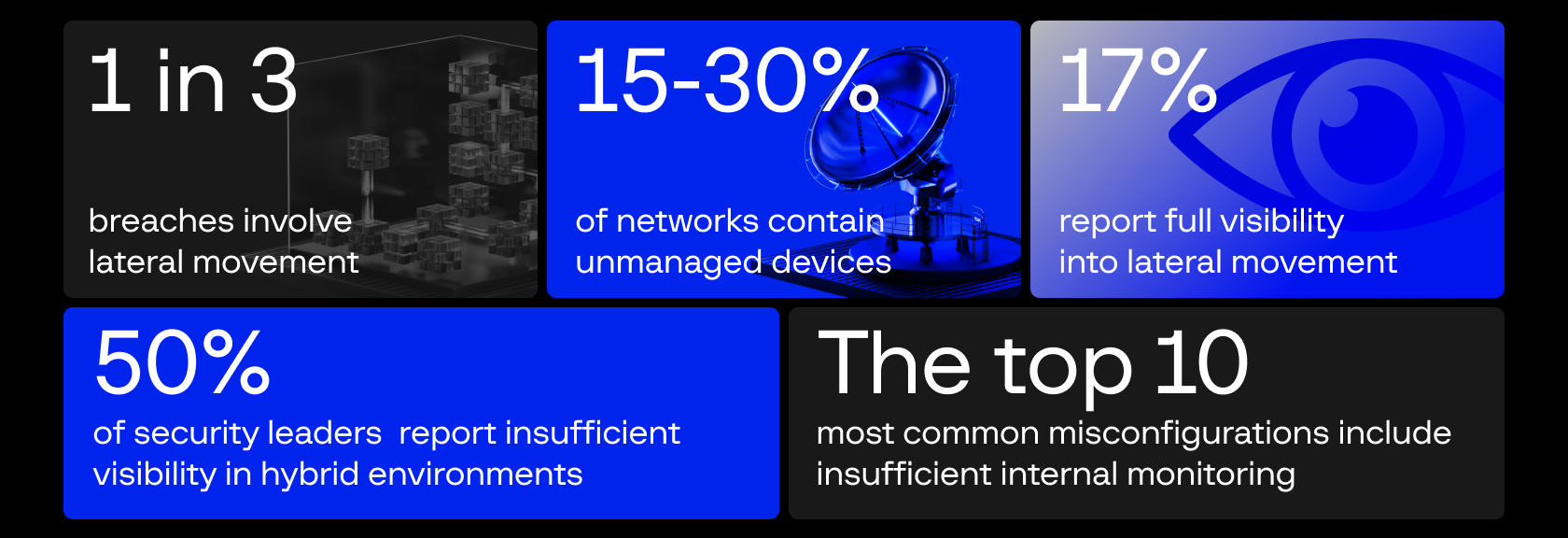
Remote work amplifies BYOD security risks. The COVID-driven shift to hybrid work has made Bring Your Own Device (BYOD) policies nearly inevitable, with employees routinely using personal laptops, smartphones, and tablets for work tasks. These devices connect to public WiFi networks, get shared with family members, and accumulate personal-use malware that corporate security teams never see. Recent data shows that 46% of compromised systems were unmanaged devices mixing personal and corporate accounts — often tied to BYOD policies.
Coverage is rarely complete. Shadow IT and forgotten branch offices leave entire segments unmonitored. One client discovered a branch office missing from EDR coverage only during a security audit.
Network communications are invisible to EDR. Agents can’t see traffic between systems and miss the lateral movement patterns, credential harvesting, and covert channels that define modern attacks.
Without network detection, threats can persist for days or even weeks. The longer the dwell time, the more likely that credential escalation, data staging, and exfiltration could occur, which increases both response time and cost.
What makes NDR different
Network detection and response tools analyze network traffic using behavioral analytics, continuously monitoring both internal (east-west) and external (north-south) communication. Unlike endpoint tools that only see individual hosts or firewalls that focus on blocking, NDR provides the network-wide visibility needed to understand attack patterns and lateral movement.
The fundamental difference from firewalls: Firewalls operate inline, sitting directly in the path of traffic and making real-time decisions. NDR systems analyze copies of network traffic, which inherently limits their response capabilities but provides comprehensive visibility without affecting network performance.
The economic factors driving vendors in the wrong direction
If NDR is designed to monitor both north-south and east-west traffic, why do so many organizations still lack internal visibility?
Hardware costs drive perimeter focus. Compared to comprehensive internal monitoring, deploying sensors at network egress points requires minimal hardware investment. Software licenses are cheap; hardware deployment is expensive, and customers naturally gravitate toward solutions that minimize capital expenditure.
Vendors do not want to create challenges for their customers: Reluctant to alienate price-sensitive SMEs, vendors have designed their NDR features around budget preferences rather than security requirements. They don’t want to lose clients to hardware costs so they don’t insist on comprehensive internal monitoring.
Detection capabilities misaligned with modern threats: Traditional beacon-type malware that connects to C2 servers at regular intervals can be detected using frequency analysis. Yet modern infostealers leverage legitimate communication platforms like email, Telegram and Slack for the purposes of command and control, which makes their traffic indistinguishable from normal business communication.
Incomplete deployment masquerading as comprehensive protection. While Gartner confirms that leading NDR vendors provide both north-south and east-west monitoring capabilities, many organizations still deploy NDR with limited internal coverage due to cost considerations. This creates a dangerous gap where customers believe they have comprehensive protection but are actually monitoring only perimeter traffic (where attacks begin) and miss internal lateral movement (where 70% of attack damage occurs).
Why internal traffic analysis matters more than you think
Attackers have long shifted from detectable, custom protocols to the camouflaged use of standard ones. Malicious traffic often hides in HTTPS, DNS and cloud services that resemble normal business use. When signature-only approaches do not work, behavioral analysis becomes essential.
Decisive damage occurs during lateral movement. After gaining initial access through phishing or vulnerabilities, attackers map the network, harvest credentials, and move toward sensitive data, within east-west traffic that perimeter-focused setups do not inspect.
Internal traffic also presents unique opportunities for visibility. Many environments still use HTTP for internal web applications, plain FTP for transfers, or unencrypted SMB on file shares. Monitoring such traffic can help reveal suspicious activity quickly, provided it is actually observed.
Use case: When perimeter monitoring fails
Let’s consider a real-world attack scenario that shows the limitations of north-south focused NDR:
An organization with “comprehensive” NDR coverage monitoring all perimeter traffic experiences a breach. The attack begins with a spear-phishing email that delivers an infostealer to an employee workstation. The malware uses Slack channels for C2 communication, which is completely invisible to perimeter monitoring.
The attacker conducts internal reconnaissance using native Windows tools, moving laterally through the network via pass-the-hash attacks and accessing file shares to identify valuable data. All this activity occurs in internal east-west traffic that the perimeter-focused NDR system cannot see.
When malicious communication occurs between two internal hosts, security teams face critical questions that consume valuable incident response time:
- What is the host? A server, laptop or printer?
- Which operating system is it running?
- Who owns the device?
- What business function does it serve?
Without immediate answers, security teams must coordinate with IT departments to identify basic assets while the malicious activity continues. The validation process for false positives becomes a bottleneck, especially when dealing with numerous alerts from systems that lack comprehensive asset context.
By the time the attack is detected through secondary indicators, the threat actor has already exfiltrated sensitive data and established persistent access across multiple systems, all via internal traffic that was completely unmonitored.
Group-IB’s approach: Comprehensive analysis of internal traffic
Our NDR solution within Managed XDR prioritizes monitoring of east-west traffic and makes comprehensive analysis of internal traffic accessible to organizations.
Beyond basic C&C detection
While many solutions focus on identifying malware that communicates with external command servers, we analyze the complete attack lifecycle within your network. Our behavioral analysis detects reconnaissance, credential access, privilege escalation, and data collection, all of which are critical MITRE ATT&CK tactics at a stage where attacks can still be stopped.
File storage integration
We can connect directly to file shares and analyze stored files. Being able to do so is a critical capability since shared resources often serve as malware distribution points for lateral movement. Such a proactive approach identifies threats before they can spread through the network.
Covert channel detection
Rather than relying on signature-based detection that fails against legitimate protocol abuse, we use behavioral analysis to identify hidden communications. Whether attackers use DNS tunneling, ICMP covert channels, or legitimate applications like Slack for C2, Group-IB NDR detects the behavioral anomalies that signature-based solutions often overlook.
Comprehensive asset inventory with local IP discovery
Through passive network monitoring, Group-IB automatically maintains an inventory of all network participants, including device types, operating systems, and communication patterns. Our new “Local IPs” feature passively collects detailed information about local IP addresses, including MAC addresses with vendor and operating system information, related domains, hostnames, and comprehensive lists of ports and network services.
When security alerts occur, analysts immediately have context about the communicating hosts, including their specific network footprint and service configuration. Rather than waiting for responses from the IT team to identify the host, security teams can instantly assess device type, operating system, running services, and network behavior patterns, which eliminates the coordination delays that allow attacks to progress.
Internal traffic file extraction
We leverage the fact that internal traffic often remains unencrypted to extract and analyze files in transit. Combined with ICAP integration, suspicious files can be automatically sent to our sandbox environment for analysis before they are allowed to be transferred between systems.
Advanced anti-evasion techniques
Files extracted by NDR from network traffic are analyzed in our Malware Detonation Platform. The platform supports over 500 file formats and uses sophisticated anti-evasion methods, including VM morphing, user activity emulation, and retrospective analysis to detect delayed attack scenarios that traditional systems tend to miss.
Multi-protocol and multi-environment support
Our NDR solution guarantees comprehensive coverage across L2-L7 network protocols and extends beyond traditional IT environments to support OT/ICS/IIoT protocols including MQTT, Modbus, and DNP3. This capability addresses industrial environments that many vendors ignore and provides unified visibility across both IT and operational technology networks.
Threat intelligence integration
Every instance of detection is automatically enriched with Group-IB’s world-leading threat intelligence, immediately attributing the incident to known threat actors, malware families, and attack campaigns. The integration goes beyond simple IoC matching to provide contextual understanding of attacker motivations, tactics, and infrastructure, allowing for faster and more informed decisions about response.
Integration with 24/7 managed services
Our NDR is backed by Group-IB’s 24/7 Managed XDR services, providing round-the-clock monitoring by expert analysts with over 21 years of experience in digital forensics and incident response. Such a managed approach offloads the burden from internal teams while ensuring that sophisticated threats are identified and responded to immediately, even outside business hours.
Monitor where attacks actually happen
IDC forecasts that the NDR market will grow at 14.1% CAGR through 2028, but this growth will favor solutions that address genuine security needs rather than deployment convenience. Organizations need NDR implementations that provide visibility into all attack phases, not just initial access attempts.
Attackers have shifted their tactics and now mainly operate within internal networks, using legitimate protocols and communication channels. Security strategies must evolve to match this reality.
Economic convenience should not dictate security effectiveness. While the market may prefer perimeter monitoring, attackers operate where comprehensive visibility matters most — within your network.
Group-IB Managed XDR
Would you like to assess your internal visibility gaps? Identify your east-west blind spots with a comprehensive network analysis