Introduction
The rapid and haphazard digital advances businesses make today come with significant challenges. Everyone’s using digital technologies more diversely and extensively. How businesses store information online is evolving, the operational perimeter has expanded, and the concept of personal identities on the Internet has also changed. With a lot of information now exposed to threat actors, the chances of them exploiting these opportunities to cause disruption are higher than anticipated. In fact, they affect more than 72% of global customers in one way or another.
So, the discussion here isn’t why you need digital risk protection but how it can help you minimize the damage and ensure brand integrity, trust, and operational continuity are maintained if a risk is identified or exploited.
Cyber attackers frequently utilize fraudulent websites, fake social media profiles, applications, and illicit use of brand content to perpetrate fraud, such as capturing and selling credentials on the dark web and underground forums. Once leaked, these credentials are often used in subsequent attacks against organizations. Despite such risks, security teams often face challenges in timely tracking and identifying such threats due to inadequate tools and monitoring capabilities.
How can a digital risk protection solution help businesses defend their critical assets?
Effective risk protection requires identifying and managing digital risk exposures to maintain a secure ecosystem and overcoming these challenges:
Lack of complete digital footprint visibility: Understanding and addressing visible and hidden digital risks is critical. Therefore, businesses need intelligence that sources insights from across-the-board assets rather than tunneling vision. This broad approach provides clear insights to identify and neutralize threats early.
Expanding digital attack surface: As the number of digital assets increases, the attack surface expands, complicating security and monitoring efforts.
Cross-channel digital footprint: As digital operations cross-channelize – including websites, apps, social media, and cloud services, businesses should ensure their current security assessments include cross-browser compatibility to cover a wide range of browsers and devices, identifying potential weaknesses across platforms.
Exposure management: Due to third-party interventions, unsupervised/shadow IT, and other factors, digital channels are increasingly exposed and harder to control. Therefore, swiftly and continuously identifying and managing exposures is essential for comprehensively protecting business-critical assets.
Detect and combat violations with Group-IB Digital Risk Protection
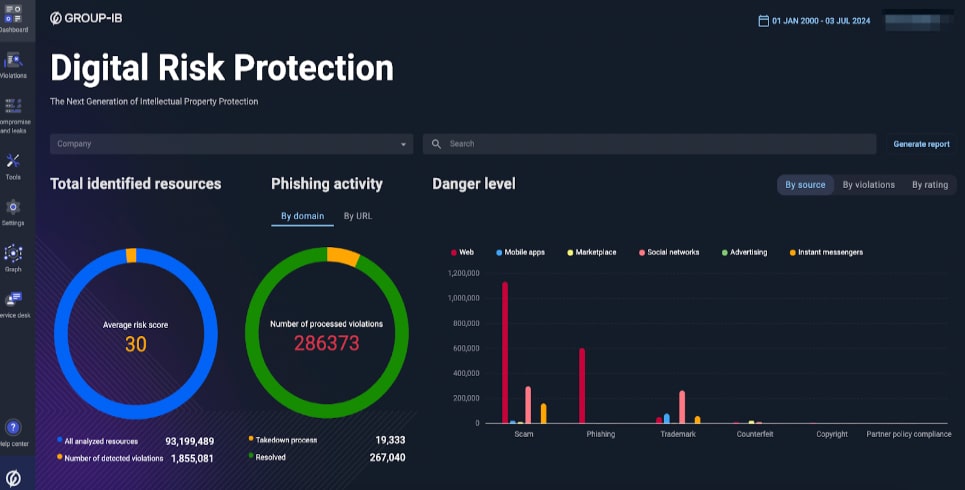
Image 1: Group-IB Digital Risk Protection multi-vision dashboard
Group-IB’s Digital Risk Protection is an automated solution that addresses current and emerging challenges in securing a business’s digital environment. It aims to rapidly eliminate external digital risks to a company’s intellectual property and brand, requiring minimal human intervention.
How does DRP monitor and detect violations?
Group-IB’s Digital Risk Protection (DRP) collects data from various digital assets, including social media, domains, cloud, dark web, public/private feeds, and marketplaces, through automated crawling, parsing, APIs, anti-evasion processes to generate intelligence and detect violations, and infringements. Digital Risk Protection (DRP) leverages our proprietary Threat Intelligence insights as a source of cross-platform data enrichment to understand the cybercriminal infrastructure and capture sophisticated violations comprehensively.
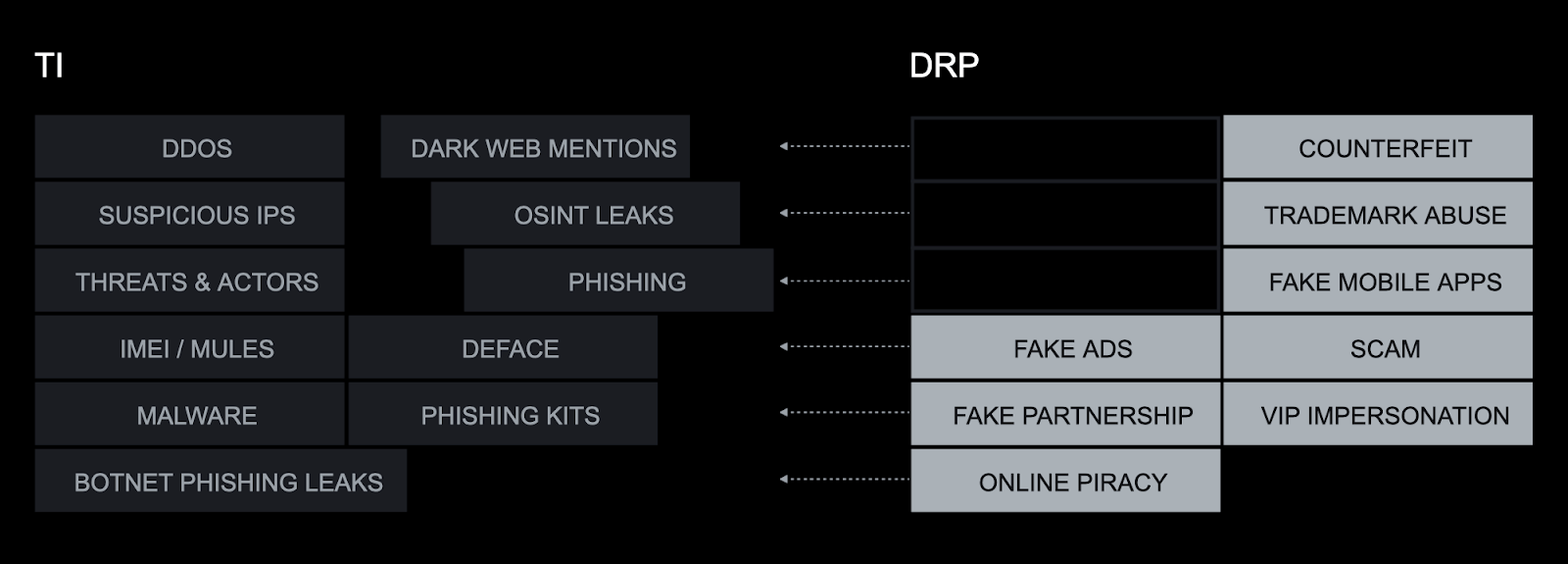
Image 2: Group-IB Digital Risk Protection and Threat Intelligence cross-platform data enrichment
This intelligence feeds into our Digital Risk Protection platform, which analyzes the data and uses advanced algorithms to scan the internet for instances of trademark infringement, counterfeiting, and unauthorized use of brand assets. These tools enable brand owners to proactively and automatically identify and address potential threats, minimizing the impact of online brand abuse on their reputation and revenue.
Digital risk protection solutions utilize various techniques to pinpoint and prioritize the most critical risks. Here’s how they typically operate:
Signature Analysis
- Signatures: These solutions scan for known patterns or “signatures” of malware, phishing attempts, and other malicious activities. These signatures are derived from historical incidents and help identify similar threats.
Domain Name Score:
- Domain Analysis Each domain receives a score based on its history, age, ownership, and past associations with malicious activities.
- Content Analysis: The solution examines the content hosted on domains to detect signs of phishing, counterfeit branding, or other deceptive practices.
Neural networks and general score:
- Pattern Analysis and Risk Scoring: Comprehensive risk scoring models integrate factors like domain reputation and presence of malicious signatures to calculate an overall risk score. The scoring is also self-adjustable, prioritizing enforcement depending on the severity of violations.
- Threat Intelligence Feeds: These solutions ingest threat intelligence from diverse sources, including public databases, private feeds, and dark web monitoring. This real-time information updates risk scores and enhances threat detection capabilities.
By leveraging these methodologies, digital risk protection solutions help organizations stay ahead of evolving threats, safeguard their digital assets, and maintain operational continuity.
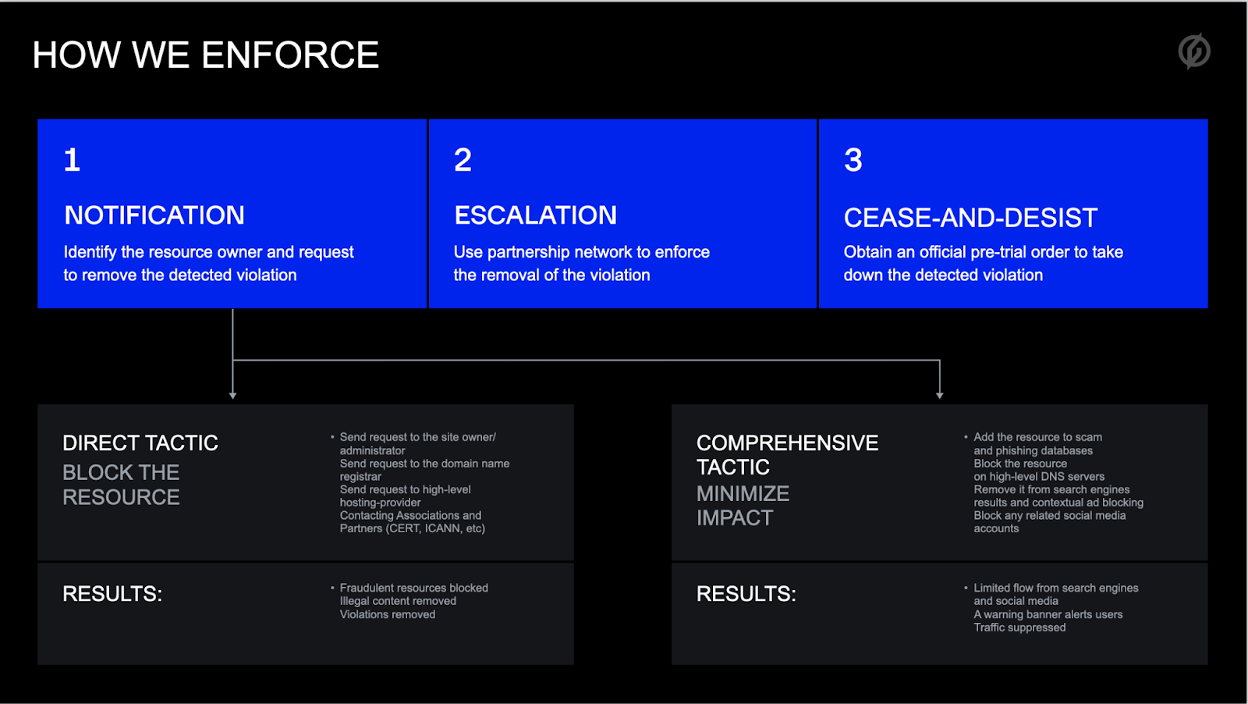
Here’s how Group-IB’s Digital Risk Protection ensures the fastest mitigation cycle from detection to elimination
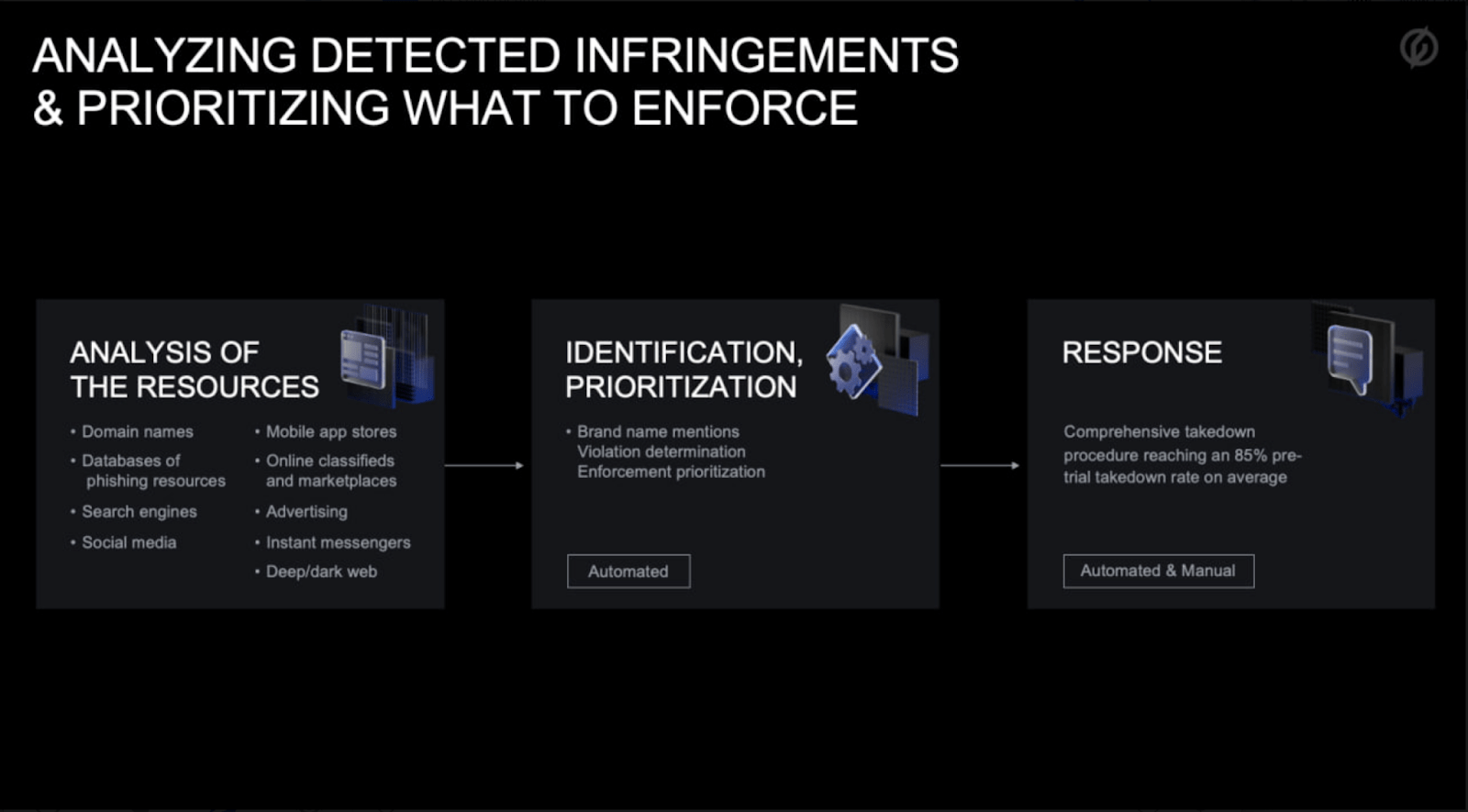
Comprehensive monitoring and detection
Analysis and prioritization of infringements
Takedown enforcement
How does Group-IB DRP enable comprehensive risk protection?
1. Connect dots effortlessly with Group-IB patented Graph technology.
Upon detecting a suspicious link to a phishing, fake, or pirated website, Group-IB Digital Risk Protection creates a graph of linked web resources and checks all the detected hosts for similar attributes. This helps detect more phishing resources (which remained active but undetected) and suspicious newly registered domains (created for future attacks but not yet active).
A common example: Experts find a phishing domain belonging to a server that hosts five other domains. A quick check shows that all five domains contained phishing content. As a result, DRP helps to block six phishing resources instead of one.
2. Identify scams and fraud before the traffic attraction stage
Before threat actors disseminate malicious resources, a few things need to be done. For example, suppose they want to spread phishing resources. In this case, they will first need to set the infrastructure, such as registering a domain name and ensuring that a connection to the C2 server (also known as C&C servers or C2 nodes, which serves as the linchpin of cyberattacks, allowing threat actors to remotely manage and coordinate their malicious operations) has been established.
While all these steps can be automated, there is a lull period before everything is up and running. This is where we can detect newly registered domains that are currently inactive. Once the phishing content is up, we can inform our clients and proceed with takedowns. The same is true for scams and frauds.
3. A huge database of domain names
Group-IB has a huge collection of domain names that we can analyze and cross-examine based on past and current phishing and scam attacks to better understand how these schemes work and how we can better detect them for current attacks on our customers.
4. Module-based risk protection
Group-IB Digital Risk Protection platform encompasses a broad spectrum of use cases organized into 5 modules that address key digital risks.
- Anti-scam: Protection against online brand abuse.
- Anti-counterfeiting: Protection against illegal online sales of counterfeit goods.
- Anti-Piracy: Protection against illegal distribution of digital content.
- Leaks Detection: Detection of sensitive data published on paste sites and the dark web.
- VIP Protection: Monitoring and mitigation of fake VIP accounts on social networks.
Users can also choose the number of brands and languages to monitor for each module. These modules can be customized and scaled to meet specific organizational needs, enabling businesses to prioritize areas most pertinent to their operations.
5. Automated digital risk detection
Enable security teams to easily automate the monitoring of digital assets on the web surface—criminal forums, dark web sources, and marketplaces—with 24/7/365 detection of violations and infringements.
Real-time alerts
DRP users receive alerts, view the list of violations, approve identified cases, and designate resources for takedown. They can assess real-time alerts and evidence of unauthorized brand mentions, impersonations, and compromised credentials to take proactive action against digital risks.
6. Reduced investigation time
Easily search for threats and investigate alerts with one comprehensive tool. Exposure reports with detailed context on areas of concern enable security teams to look into digital risks that require further investigation.
7. Improve response and mitigation efforts
Group-IB’s Digital Risk Protection’s standout features include scam intelligence, dark web monitoring and risk intelligence, automated violation detection, and response. These features directly and completely address digital threats with predefined workflows and response actions to protect brand assets.
8. Global takedown network
Due to Group-IB’s strong connections with digital platforms, moderator accounts, international response digital associations, and global CERTs, we can collaborate with industry networks, share information about suspicious activities, and mitigate damage in real-time. This enables us to take down violations within hours and improve security.
Additionally, we actively participate in information-sharing initiatives across regions, providing our business clients with collective intelligence that helps them avoid emerging threats and protect their brand and customers’ sensitive information.
How do you enable Digital Risk Protection for your business?
1. Identify launch requirements and baseline responses for your digital channels. Whitelist resources that require monitoring and violation detection.
2. Access the system and monitor your digital footprint through an intuitive dashboard that gives you constant insights on unauthorized brand name mentions and potential violations.
3. Get a dedicated Customer Success Manager (CSM) to continuously manage alerts with the risk of violations and other supportive reporting and follow-up activities.
Enable Digital Risk Protection for your business and stay protected from breaches, content knockoffs, infringements, and other disruptive digital risks.