Introduction
Most major supply chain attacks start with a single compromised account — often through one well-crafted phishing email. In the NPM ecosystem, where developers routinely exchange code and credentials, one successful compromise can cascade into thousands of vulnerable applications.
In this article, we analyze a simulated supply chain compromise targeting NPM developers and show how Group-IB’s Business Email Protection (BEP) could have detected the very first phishing message that triggered the incident. By flagging anomalies in sender behavior, domain spoofing, and malicious attachments, BEP would have stopped the attacker before they ever reached the developer’s inbox — cutting off the infection chain before it began.
This post is the first in a new Group-IB email protection series that will highlight real-world phishing, explain adversary tactics, and show how Business Email Protection uses advanced detection and global threat intelligence to stop threats before they can impact your business.
Case Study
On September 8, 2025, a threat actor compromised the NPM account of developer Josh Junon, known as “qix,” through a highly targeted phishing campaign impersonating NPM Support. The attacker sent an email titled “Two-Factor Authentication Update Required” from the spoofed address support@npmjs[.]help, urging the recipient to reset their MFA settings to maintain account access.
The phishing link — customized for each target — redirected victims to a cloned NPM login page. Once credentials were entered, the attacker gained full access to the victim’s NPM account.
With this access, the actor modified 20 popular NPM packages inserting a JavaScript clipper into their source code. The malware monitored browser and app activity for cryptocurrency wallet interactions, replacing copied or used wallet addresses with attacker-controlled ones. It could detect and replace Bitcoin (BTC), Ethereum (ETH), Solana (SOL), Tron (TRX), Litecoin (LTC), and Bitcoin Cash (BCH) addresses, effectively diverting funds without user awareness.
At least four other NPM developers reported receiving similar phishing emails during the same campaign, suggesting a coordinated attempt to compromise multiple high-impact maintainers. Overall, the affected packages represented nearly 2.8 billion weekly downloads, making this one of the most significant NPM supply chain incidents to date.
Following remediation, the compromised packages were reverted to clean versions, and the affected developers regained control of their accounts.
More information about the attack, related IOCs, phishing infrastructure indicators, and cryptocurrency wallets used by the adversary can be found in the Group-IB Threat Intelligence platform.
Email сharacteristics and tactics
The phishing emails were masqueraded as official NPM security notifications and claimed that the recipient’s two-factor authentication configuration was outdated and required immediate attention. The messages created a sense of urgency by threatening account suspension if the security issue was not resolved promptly.
Each email contained a malicious call-to-action link that directed victims to a credential harvesting site hosted on the npmjs.help domain. The fraudulent site was meticulously made to look like the authentic NPM interface.

Figure 1. Fraudulent message masqueraded as a security update
Signs of malicious activity
Despite successfully passing standard email authentication protocols (SPF, DKIM, and DMARC), several technical indicators revealed the campaign’s malicious nature:
- The npmjs.help domain had been registered recently and had no legitimate connection to NPM’s official infrastructure
- The emails contained language that fostered a sense of urgency and threatened account suspension to pressure recipients into immediate action
- The embedded link directed to the credential harvesting page
Collectively, the above indicators clearly point to a phishing attempt, despite the campaign successfully bypassing traditional email authentication mechanisms.
Indicators of compromise
Domains & hosts:
- npmjs[.]help
- static-mw-host[.]b-cdn[.]net
- img-data-backup[.]b-cdn[.]net
- websocket-api2[.]publicvm[.]com
- 185[.]7[.]81[.]108
URLs:
- https://websocket-api2[.]publicvm[.]com/images/jpg-to-png.php
- https://www[.]npmjs[.]help/login
Email address:
- support@npmjs[.]help
Detection with Business Email Protection
Group-IB’s Business Email Protection platform detects and blocks similar attacks through comprehensive signal correlation across multiple detection layers. The system analyzes subject lines, sender infrastructure, message content, embedded links, and metadata to identify sophisticated threats.
Our approach is based on multi-layer detection:
- Domain intelligence: RDAP checks would immediately flag the recently registered npmjs.help domain as suspicious
- Brand impersonation analysis: Advanced algorithms would detect the domain’s attempt to mimic legitimate NPM infrastructure
- Content analysis: Both static signatures and machine learning models would identify urgent language patterns and security-themed social engineering tactics such as the subject line that mentions two-factor authentication updates
- URL analysis: An in-depth inspection would reveal the credential-capturing functionality of linked pages
- Behavioral detection: Page rendering checks would expose the fraudulent replication of the NPM interface
Such a comprehensive approach ensures that advanced email protection can identify threats that successfully bypass basic authentication and reputation-based security controls.
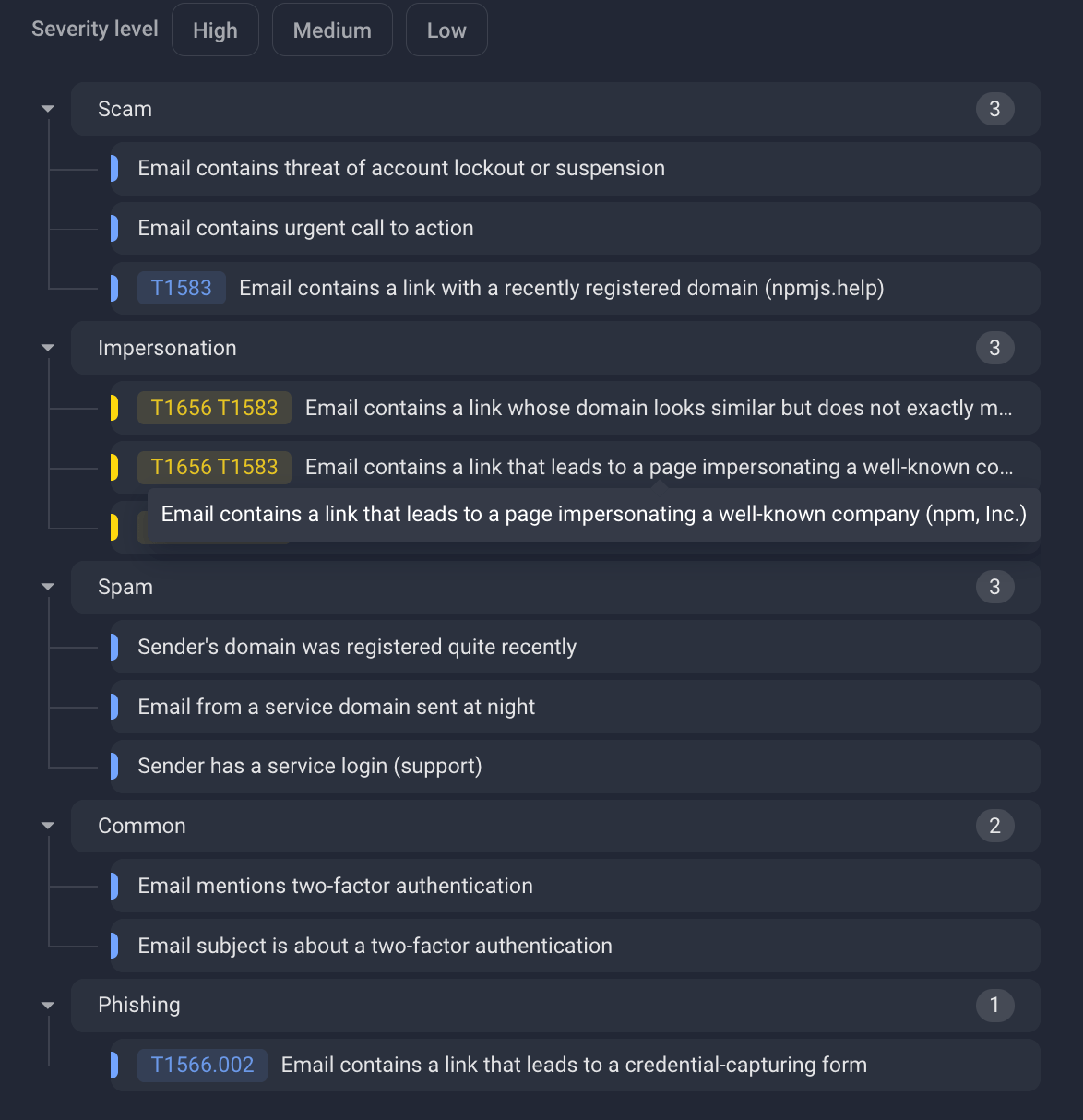
Figure 2. Business Email Protection interface showing threat indicators
Conclusion
The npmjs.help campaign shows how sophisticated adversaries can combine typosquatting domains with security-themed social engineering to target critical infrastructure maintainers. The attack’s success in bypassing email authentication while maintaining high credibility demonstrates the limitations of traditional approaches to email security.
Advanced email protection systems can reliably detect such malicious campaigns through domain intelligence, content analysis, and brand impersonation detection capabilities.
Group-IB’s Business Email Protection team continuously monitors emerging supply chain threats, analyzes adversary techniques targeting developer ecosystems, and updates detection models to protect our customers against evolving email-based attacks on critical infrastructure.
Take email security to the next level with Group-IB Business Email Protection
Detect, analyze, and block sophisticated email attacks before they impact your business


































