Introduction
A recent study by Group-IB’s Digital Risk Protection (DRP) analysts uncovered an increase in hacker attacks across Balkan countries, primarily targeting financial institutions and critical infrastructure. In 2022, hackers attacked the Republic Geodetic Institute (RGZ) of Serbia, causing a temporary shutdown and preventing public access for document requests. In 2023, Serbia’s power grid became the next major target of a cyberattack, highlighting the growing threat to essential services in the region.
In this blog, we highlight our recent research into phishing attempts by cybercriminals impersonating the postal service, targeting the general population in the Balkan region, more specifically in Croatia, Romania, Serbia, and Slovenia.
Key discoveries in the blog:
- Cybercriminals have been discovered to target postal service users in the Balkan region using a “failed delivery” scam.
- The scheme involves establishing first contact with their victims via email, which leads them to a phishing website impersonating a legitimate postal service, and coercing their victims to provide their personal and financial information in order to fulfill their “delivery”.
- Once the victims provide their personal and financial information, their information is harvested, with financial losses incurred.
Who may find this blog interesting:
- Cybersecurity analysts and corporate security teams
- Malware analysts
- Threat intelligence specialists
- Cyber investigators
- Computer Emergency Response Teams (CERT)
- Law enforcement investigators
- Cyber police forces
Phishy Package
Group-IB has recently discovered multiple phishing attempts by cybercriminals impersonating Pošta Srbije, the national postal service of Serbia, via email to their victims. Within the email, the cybercriminals attempt to deceive their victims by informing them that their “package has arrived at the warehouse, but it cannot be delivered due to incomplete address information”. As is common in most phishing attempts, the cybercriminals then introduce an element of urgency, asking their victims to “confirm their address” via a link “within 12 hours”.
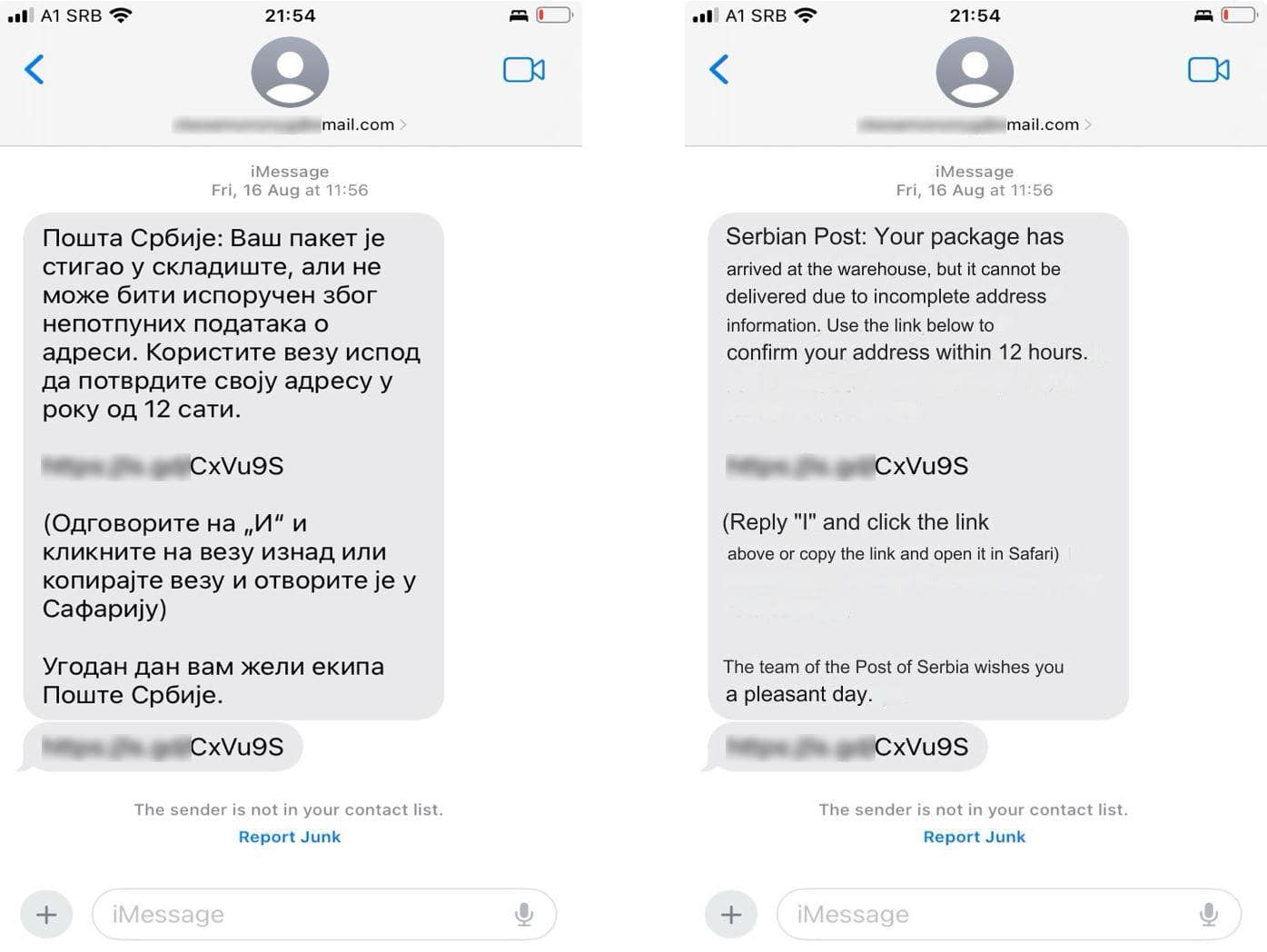
Figure 1. A screenshot (left) in Serbian and English translation (right) of a phishing email from the scammers informing their victims that their package cannot be delivered due to incomplete address information.
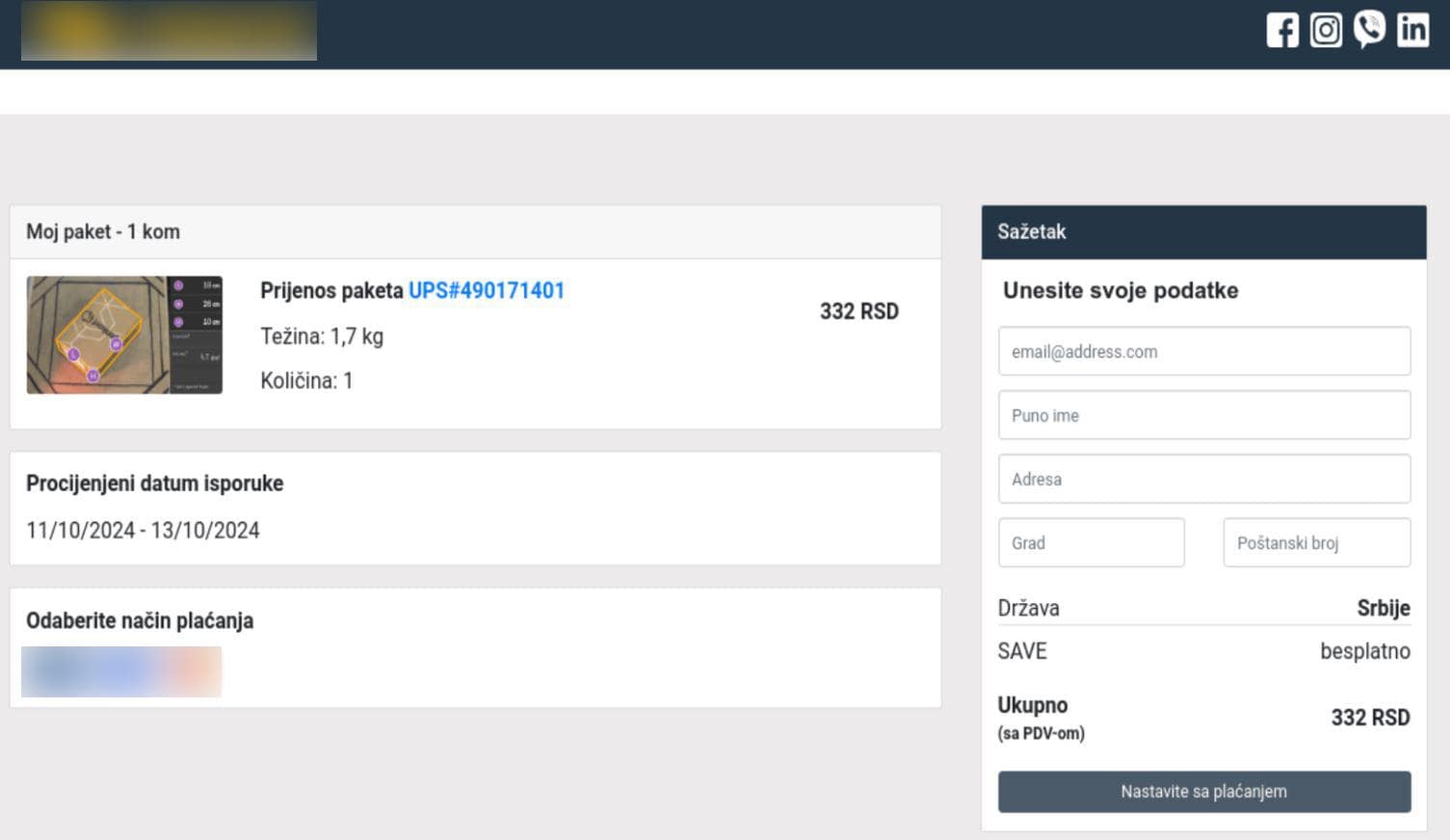
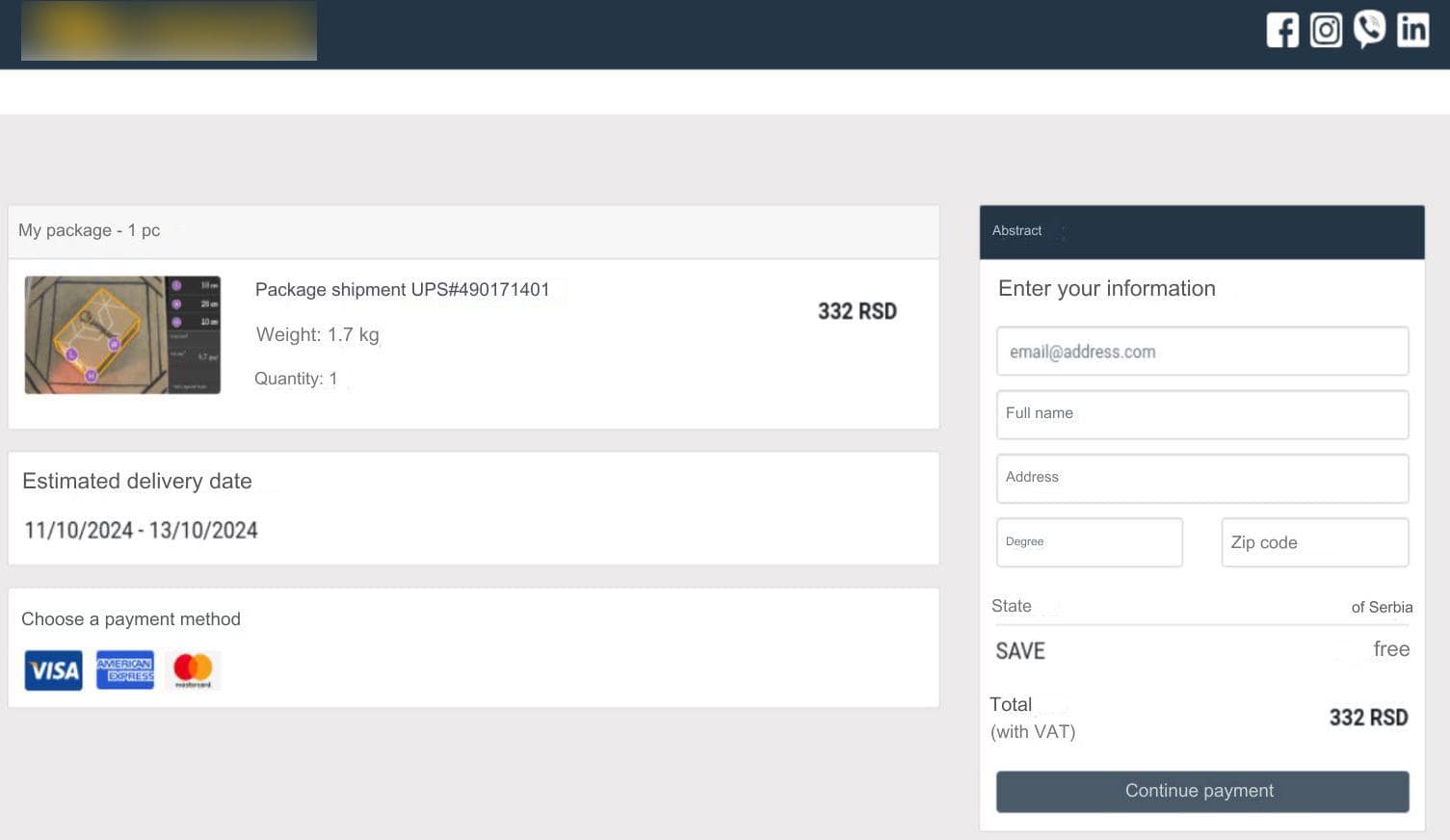
As soon as their victims click on the link, they are directed to a phishing website which is almost indistinguishable from the actual website of Pošta Srbije. The victims would then be required to provide their personal information including their name, residential or commercial address, and contact information, which the cybercriminals will harvest and use for future phishing attempts. Once the victims have provided their personal information, they would be informed that additional payment from them is required in order to fulfill the delivery of their package.
Undoubtedly, after the payment is made by the victims, the money is unrecoverable, and the cybercriminals become uncontactable, resulting in the loss of both personal information and money by their victims. Group-IB’s analysts have discovered that an email account associated with this phishing scam is still very much active as of the time of the publishing of this blog, and continues to pose a serious threat to both the reputation and customers of Pošta Srbije.
Attack on the Balkans
Further research by Group-IB’s Digital Risk Protection (DRP) analysts has revealed that the Pošta Srbije, and their customers, were not the only ones targeted by these cybercriminals. Nearly all postal services and post banks across the Balkan region have been affected, which indicates a widespread, coordinated effort by the cybercriminals aimed at exploiting the postal systems and critical infrastructure in the region, potentially compromising both institutional security and impacting customer trust on a regional scale.
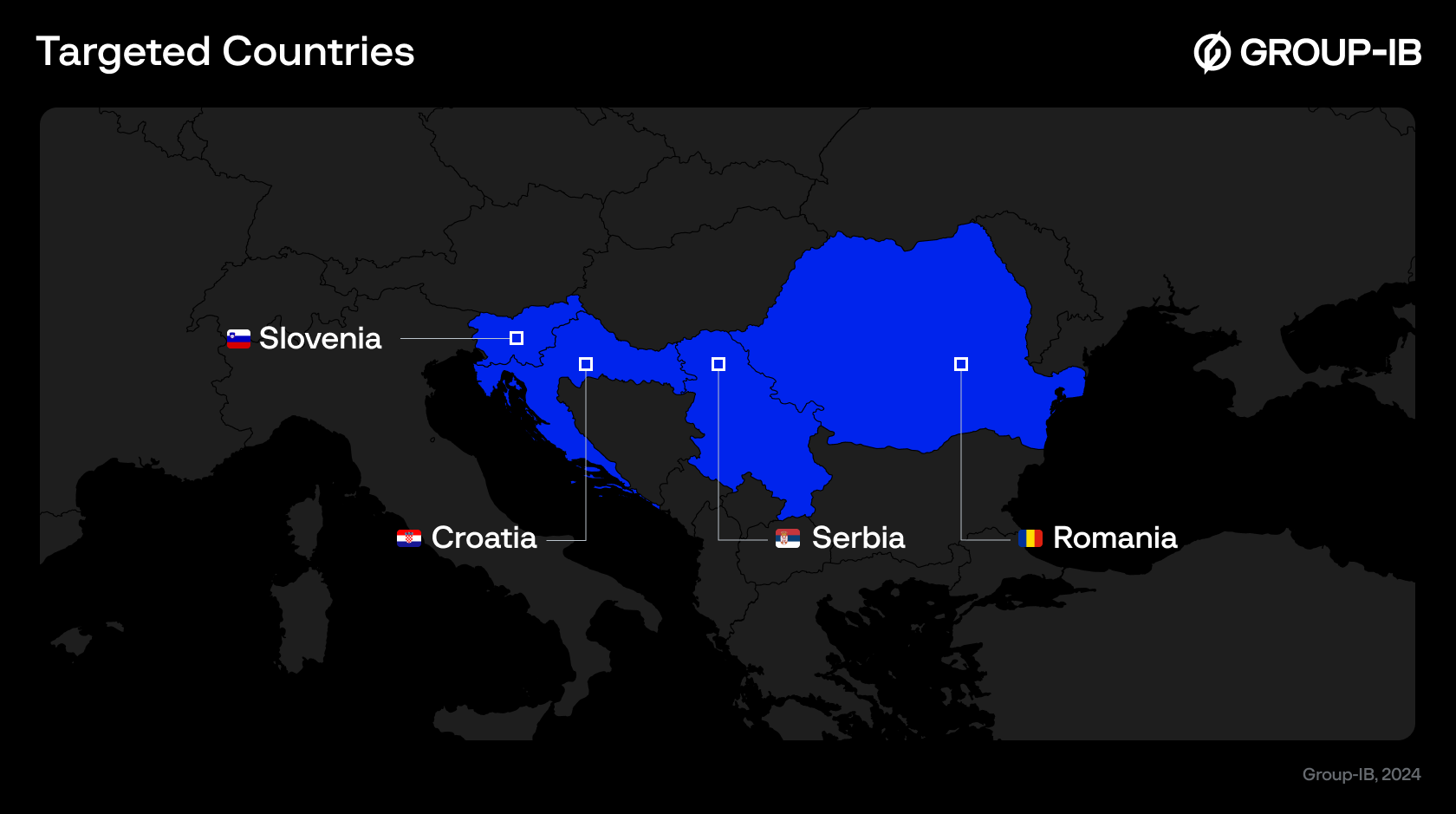
Figure 4. A map of the countries where the phishing attempts have been detected.
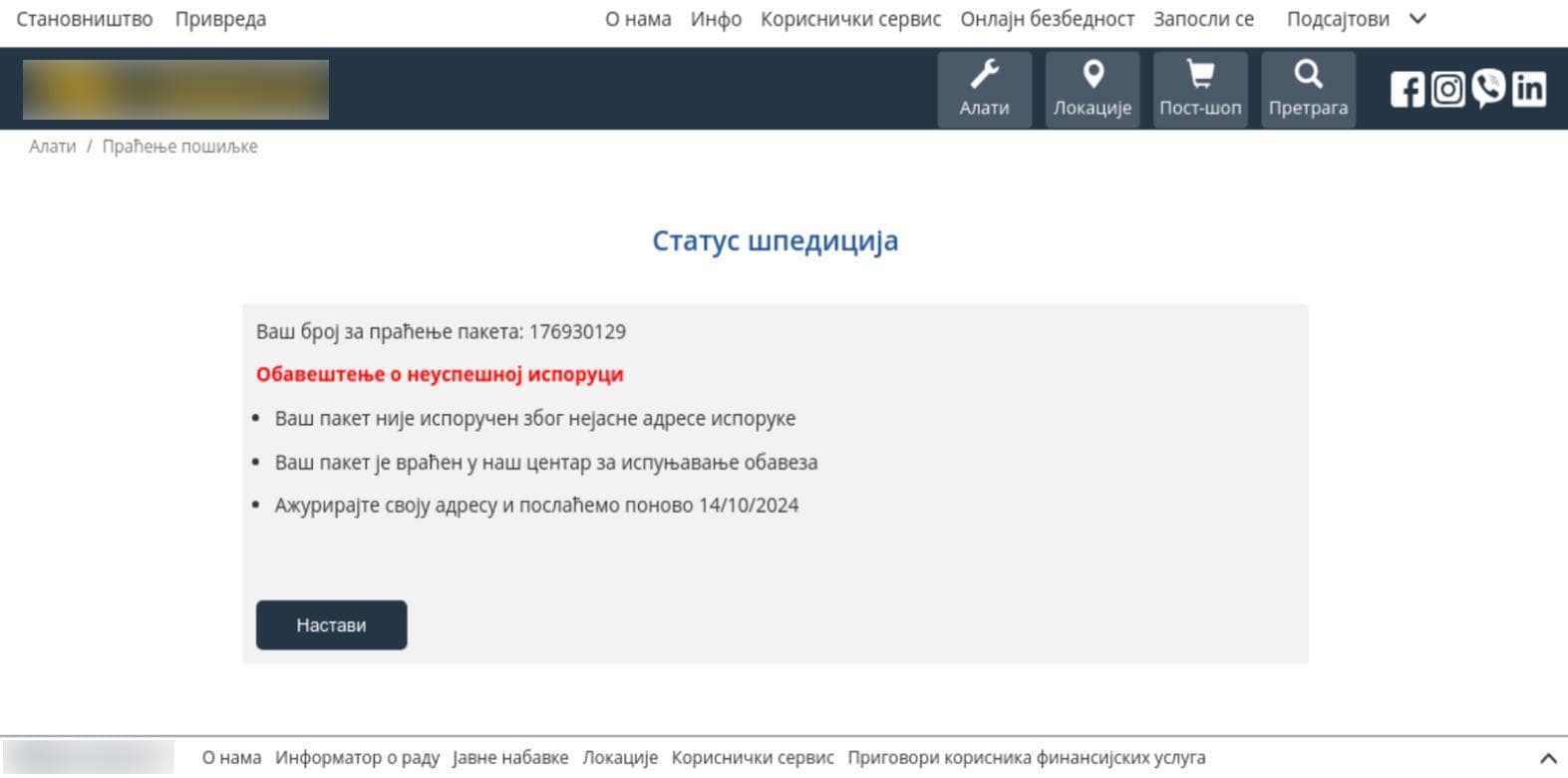
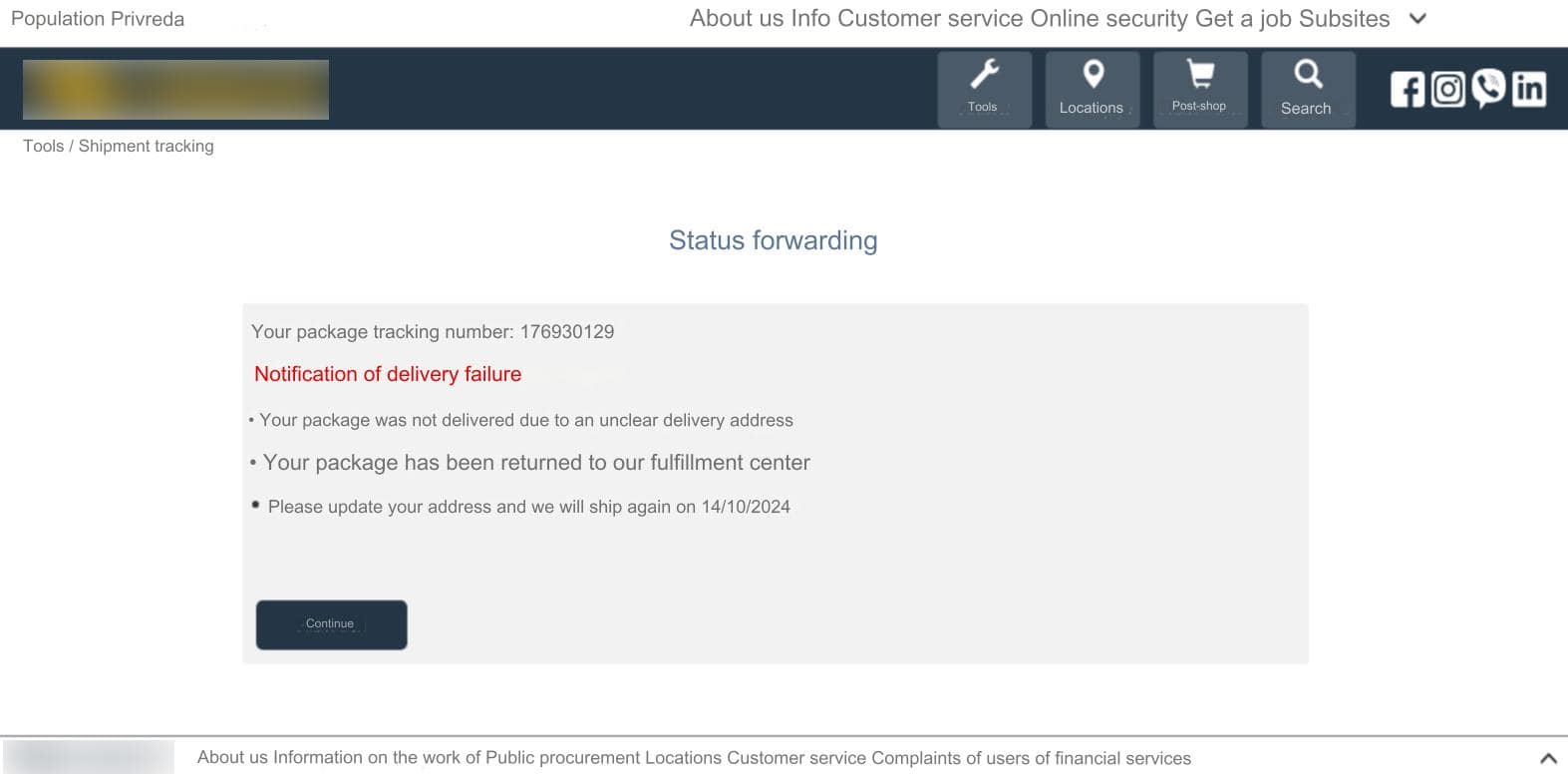
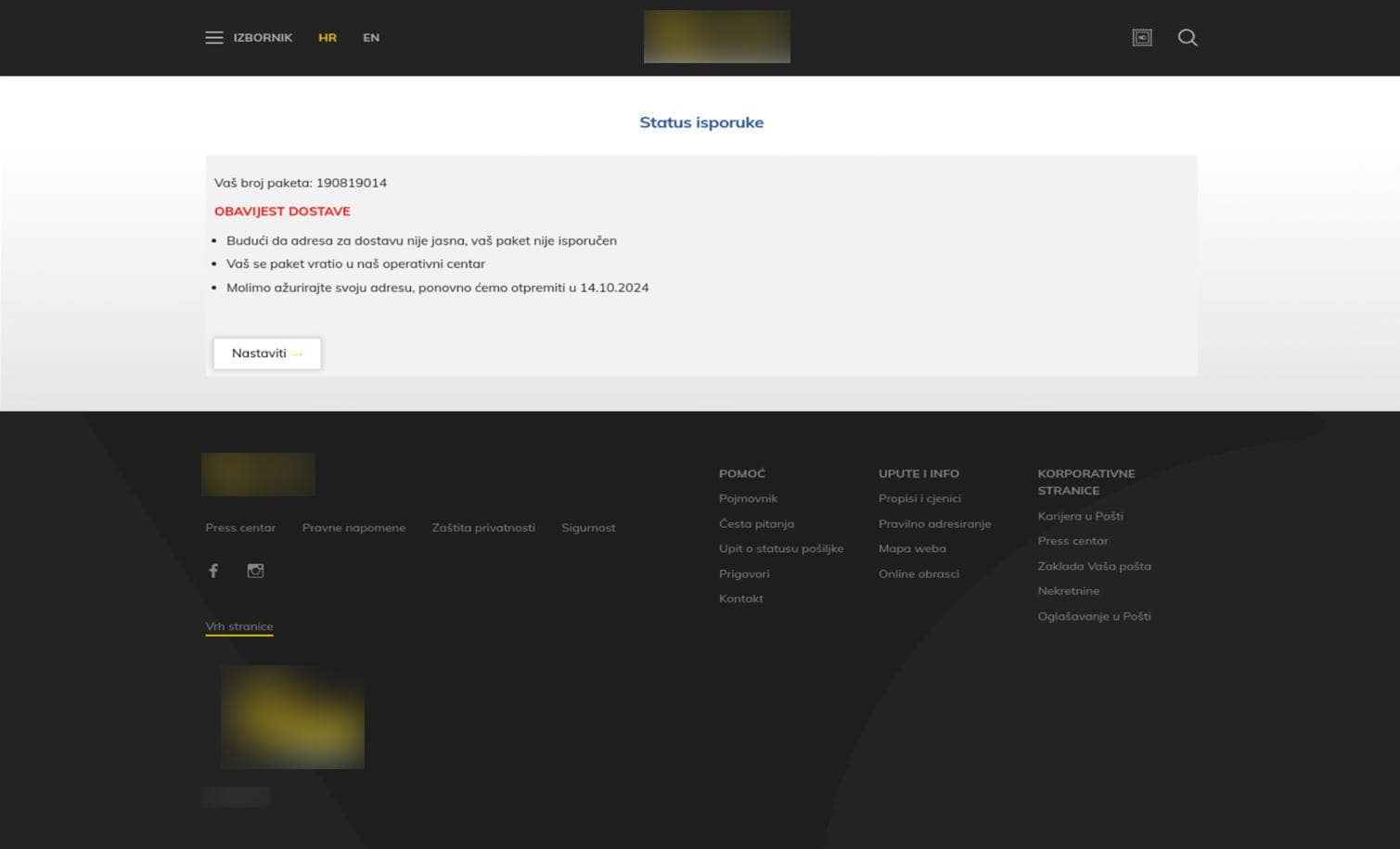
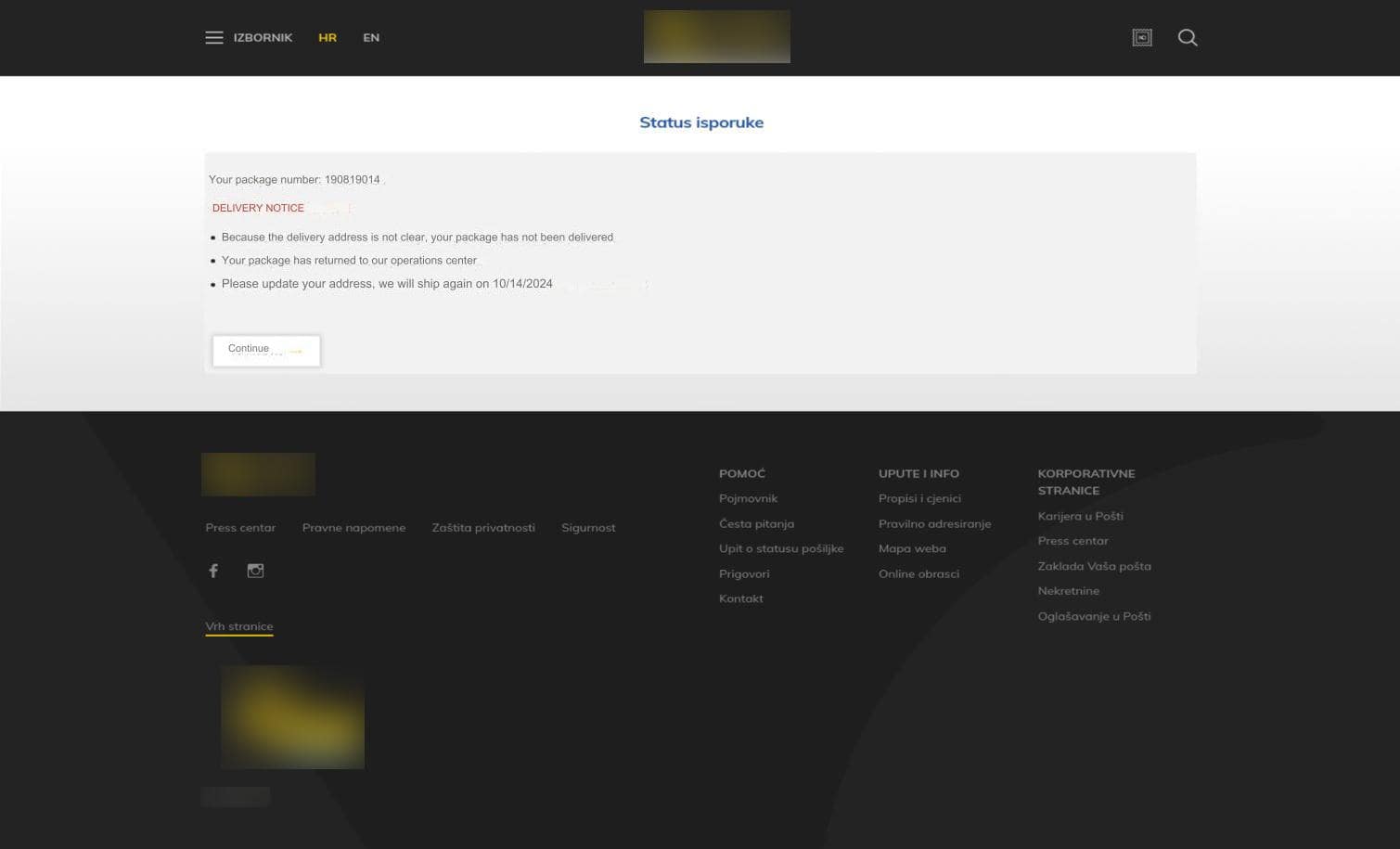
The recent surge in attacks on postal services–as well as banks associated with these services–have been increasing significantly over the past month since the publishing of this blog. These phishing websites typically include a “Delivery Notice” that includes a package number, as well as instructions that read:
- Because the delivery address is not clear, your package has not been delivered.
- Your package has returned to our operations center.
- Please update your address, we will ship again on [date].
The following are screenshots of some of the phishing websites that the cybercriminals used to scam their victims.
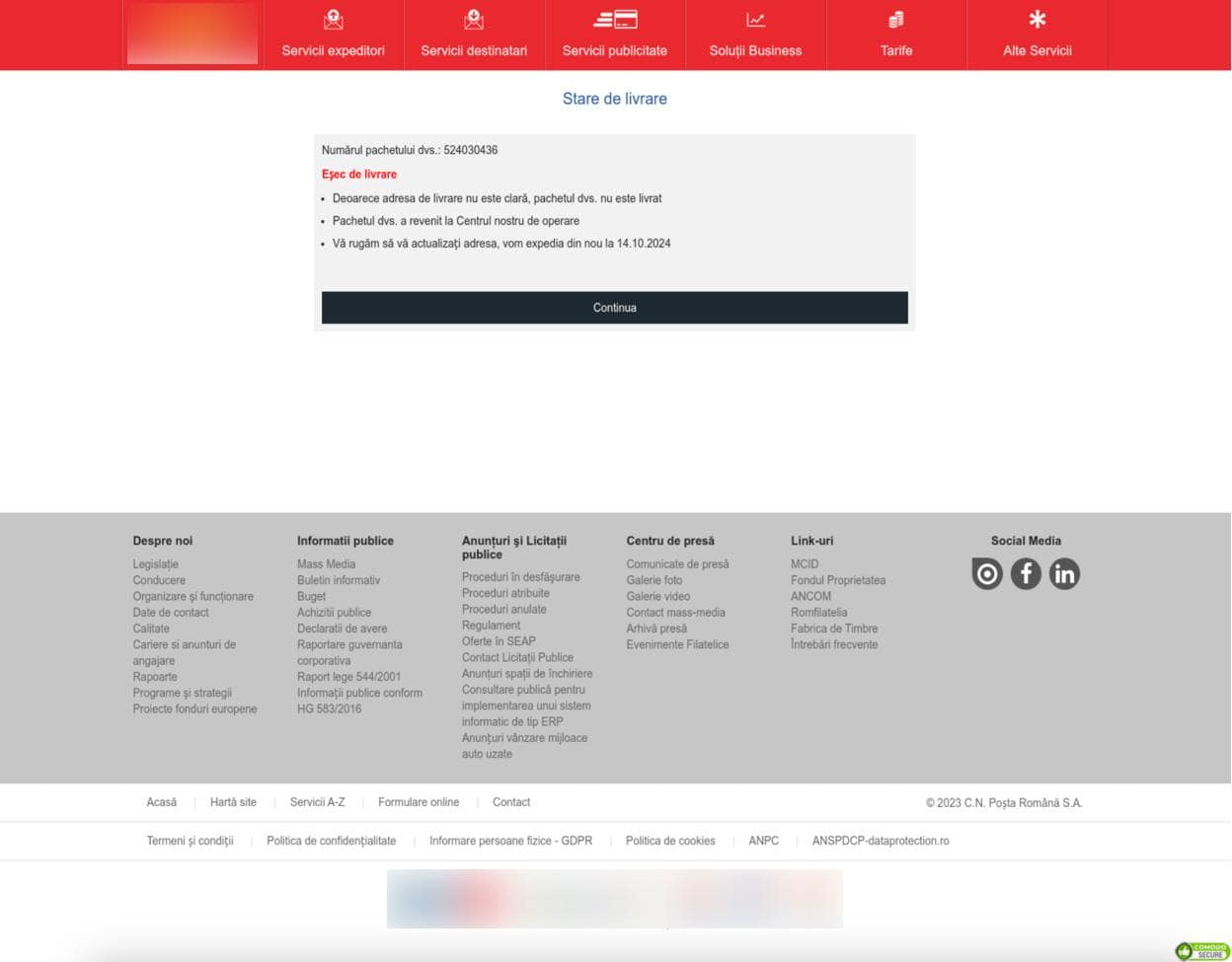
Figure 6. Screenshot of the phishing website impersonating the portal service in Romania, with instructions for their victims.
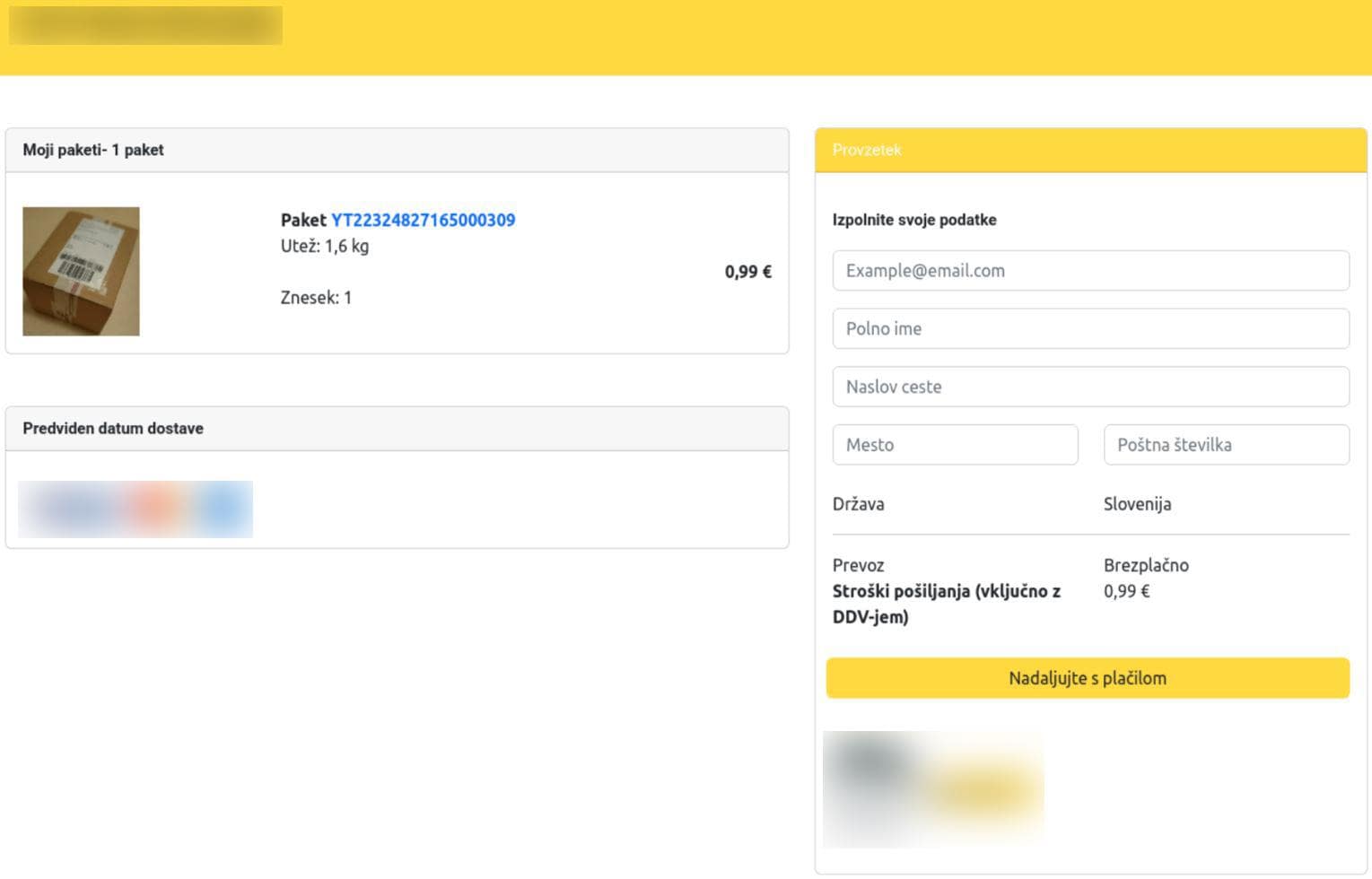
Figure 7. Screenshots of the phishing website targeting users in Slovenia, where victims are asked to provide their personal information, before proceeding to provide their financial information.
Conclusion
Postal services remain a vital component of the Balkan region’s infrastructure due to their role in facilitating communication, commerce, and connectivity, particularly in rural areas where digital access may be limited. This reliance underscores their importance in supporting both personal and business transactions, contributing to social cohesion and economic development.
However, users of these services are increasingly vulnerable to phishing attacks, as critical infrastructure is a prime target for threat actors, including individuals, state-sponsored groups, and hacktivists. These attacks can lure victims into disclosing sensitive information, leading to financial loss and greater risks. Malicious URLs may contain trackers or spyware capable of accessing sensitive features, such as activating a mobile device’s camera or tracking geolocation.
Recommendations
For postal service users:
- Always check any incoming emails from suspicious senders by checking if the email domain is legitimate.
- Check for spelling or grammar mistakes within the email.
- Do not click on suspicious links and, where possible, check with your local postal service if the email is legitimate.
- Any attachment should be open with caution and if the sender’s authenticity is in doubt, it is best to have the file reviewed by a cybersecurity professional.
For businesses:
Implementing a Digital Risk Protection solution will enhance your company’s security and the trust of your users, by detecting and addressing instances of brand impersonation, allowing you to identify and mitigate risks from unauthorized entities exploiting your brand’s identity.
Advanced Digital Risk Protection for Online Security
Defend your digital assets with best-in-breed, AI-powered brand protection online solution