Introduction
Security in silos is now proving to be counterproductive. Given today’s cyber threat reality, adversaries are far from conventional or conservative in their attack strategies. They repeatedly innovate and combine various methods of intrusion, fraud, extortion, leaks, and other threats, focusing on maximizing disruption rather than pursuing a single outcome through exploiting multiple vulnerabilities and initiating multi-vector attacks.
Therefore, it makes sense for security teams to leave behind the traditional siloed defense approach, which will soon be (if it isn’t already) inadequate against nefarious adversaries. While many organizations are already preparing to cope with the development and build a unified approach to cybersecurity and fraud prevention, most still lack awareness of the impending need for change.
The coming together of cybersecurity and fraud prevention: Impact on risk evaluation and response
Before we jump into how the amalgamation is likely to impact your existing defense strategy, let’s understand how the silos perform independently and how does can one function inform the other.
According to Gartner’s report, “With the explosion of online cyber fraud, organizations are struggling to implement controls that blur the line between online fraud and security. Many organizations are beginning to recognize the merits of treating online fraud incidents (such as account takeover and bot mitigation) as security issues. Cyber-fraud fusion centers are the future of fraud-fighting and will be part of the strategic direction of this industry over the next five to seven years.”
Cybersecurity and fraud prevention convergence reshapes organizations’ risk evaluation and response strategies. Traditionally, these two domains operated rather indifferently, with cybersecurity focusing on protecting information systems and fraud prevention mainly tracking and managing illicit activities exploiting business processes. However, with online fraud now increasingly stemming from methods and channels associated with cybersecurity activities, treating fraud incidents as security issues is a pragmatic approach.
Fraud protection teams traditionally conduct point-in-time inspections (anomaly detection) and study business logic (activities against baselines) and related abuse to identify and mitigate fraud attempts. They anticipate fraudsters’ tactics and leverage user behavioral analytics to identify anomalies, leveraging historical data for pattern recognition.
Modern fraud prevention tools are a step ahead, emphasizing real-time detection and combining behavioral monitoring with anomaly detection and historical analytics for a multi-layered defense. By integrating cybersecurity measures with fraud prevention strategies, organizations can address security incidents before they lead to fraud and enhance their defenses against evolving threats.
Fostering a defense-in-depth strategy
As cybersecurity and fraud resources combine, intelligence sources across the cyber threat landscape are integrated to create a comprehensive, end-to-end vision that resonates strongly in the market. Intelligence sources and technologies associated with online fraud prevention, like behavioral biometrics, device fingerprinting, and AML systems, are also being valued in broader enterprise security use cases such as compliance reporting, risk scoring, user identity authentication, enhanced internal and external threat detection, and more.
Sharing information, tools, and knowledge to develop fraud and cyber threat prevention strategies may remove organizations’ current challenges.
| Technology Interoperability Ensuring that cybersecurity and fraud prevention tools can communicate and operate seamlessly reduces the chances of gaps and overlaps in threat detection. This integration leads to a more cohesive defense strategy and reduces the complexity and cost of managing multiple, disjointed systems. |
Sharing of monitoring operations
By combining cyber and fraud monitoring, organizations can detect threats that may lurk across both domains. For instance, a phishing attack might be carried out with the intent of fraudulent financial transactions. |
Cutting down Mean Time To Response (MTTR)
When cybersecurity teams detect suspicious activities or anomalies within systems, networks, or applications, they can immediately alert fraud analysts. This real-time collaboration allows fraud analysts to swiftly investigate the incident and determine if it poses a potential fraud risk. |
| Multichannel surveillance
Teams can better understand normal versus suspicious behavior by fusing customer profiles and behavior data. This capability enhances fraud detection and enables more targeted responses. Monitoring across various channels (e.g., online transactions, social media, and email) helps identify and mitigate fraud attempts across multiple digital platforms. |
Shared Indicators Of Compromise (IOCs)
Shared IOCs allow organizations to quickly identify potential threats by leveraging information from multiple sources, including threat intelligence feeds, security tools, and internal research and monitoring. By integrating IOCs into response workflows, teams can automate the detection and response process, enabling faster action to mitigate risks and prevent further damage. |
Better awareness at the leadership/ organizational level A fused approach gives leadership a unified picture of the organization’s threat landscape. This improved visibility supports informed decision-making and strategic planning. Enhanced awareness at the leadership level fosters a proactive risk management culture, ensuring that cyber and fraud prevention measures are aligned with overall business objectives. |
Developing a comprehensive framework that helps with Critical Threat Intelligence (CTI) and fraudsters’ Tactics, Techniques, and Procedures (TTPs) analysis is essential to ensure that insights are directly applied to online fraud prevention rules and policies. Such a cyber-fraud framework is essential to help teams with:
Integration of Cyber Threat Intelligence and Fraudsters’ TTP
Cybersecurity TTPs can help understand and predict attacker behavior. This knowledge can be applied to configure and refine fraud detection rules, making them more proactive and resilient to sophisticated attacks. Group-IB’s forward-leaning cyber-fraud kill-chain framework (mentioned by Gartner) gives you exact and in-depth insights into adversaries’ TTs.
Currently, Group-IB is only one of the two vendors offering the capability.

Group-IB’s cyber-fraud kill chain mentioned in the Gartner report
Unified Dashboard for Analysis
Centralized View: Create a unified dashboard where security teams can view and analyze insights from fraud prevention and cybersecurity tools. This dashboard should provide real-time updates and allow tailored insights and views based on specific security roles and needs.
Data Correlation: Use advanced correlation techniques to link data from different sources. This helps identify patterns that indicate fraudulent activities and cyber threats, allowing for a more comprehensive security posture.
Alert Management: Implement an integrated alert management system that prioritizes alerts based on severity and potential impact. This system should enable quick triage and response, enhancing the efficiency of security operations.
Adaptative Defenses
Regular Updates: Continuously update the cyber-fraud framework to incorporate new threat patterns and evolving security needs. This includes enhancing anomaly detection algorithms and integrating additional data sources from the Threat Intelligence platform as they become relevant.
Machine Learning and AI: Leverage machine learning and AI to improve threat detection accuracy. These technologies help identify subtle patterns and anomalies that traditional methods might miss.
Feedback Loops: Establish feedback loops where insights from incident investigations are fed back into the system to refine detection and response strategies. This iterative process ensures that the system evolves with the threat landscape.
Embracing the inevitable fusion with Group-IB’s Fraud Matrix
Considering the ever-increasing complexity and multi-vector nature of modern fraud, the Fraud Matrix is designed to equip your organization with:
- Clear, actionable insights: Deconstructing complex fraud schemes using a standardized methodology, gaining a comprehensive view of your fraud landscape.
- Proactive threat identification: Pinpointing and prioritizing potential threats before they impact your bottom line.
- Data-driven prevention: Optimizing fraud prevention efforts with actionable Fraud Intelligence.
Group-IB’s Fraud Matrix connects fraud prevention with cybersecurity by combining Cyber Threat Intelligence (CTI) with cybersecurity tactics, techniques, and procedures (TTPs). The Fraud Matrix provides a standardized multi-layered analysis of evolving threats, ensuring that insights from the cyber threat landscape are directly incorporated into online fraud prevention rules and policies, improving their effectiveness. This tool allows users to link the fraud scheme with the cyber threat techniques used to execute different schemes.
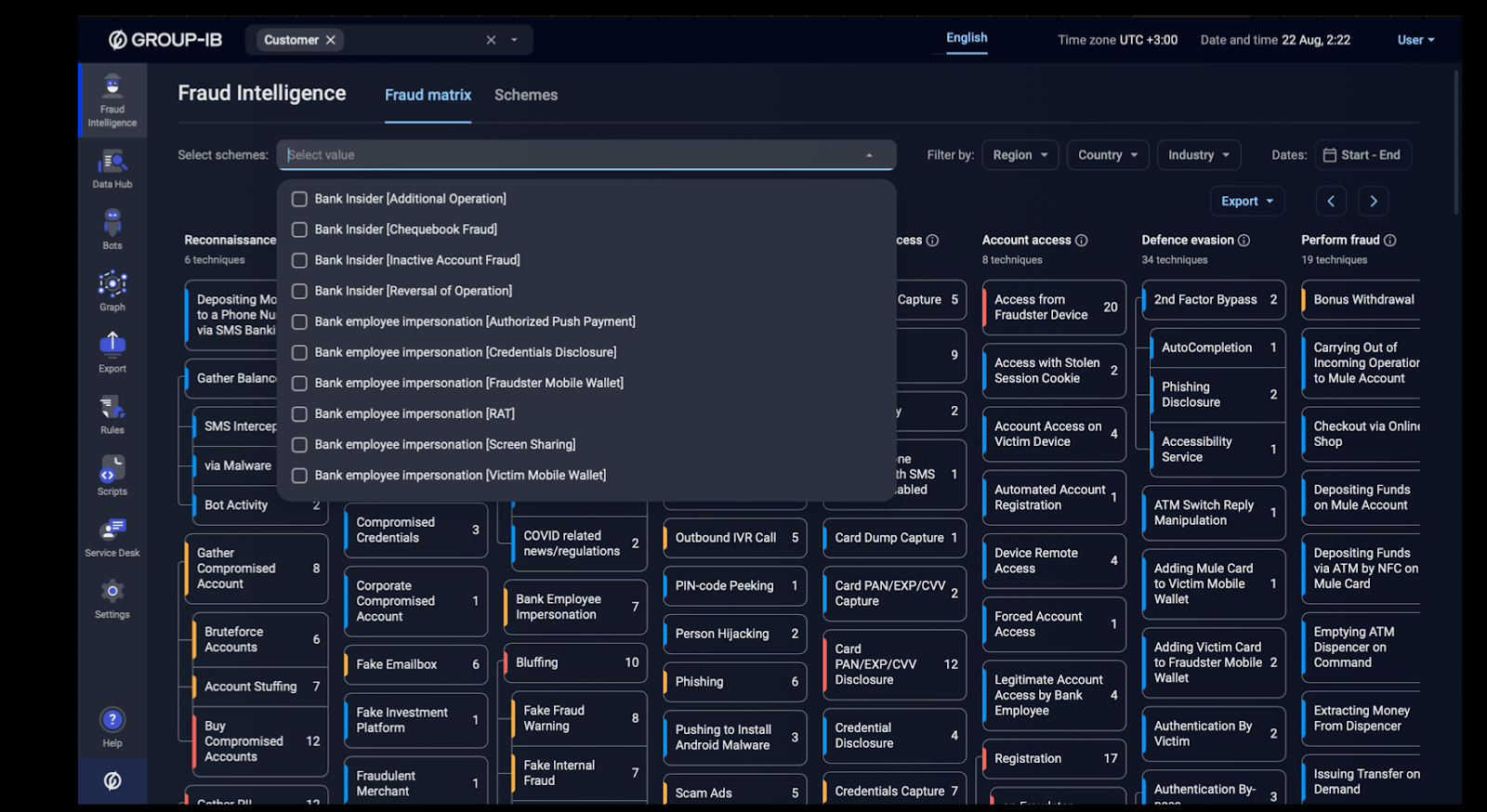
Group-IB Fraud Matrix fraud scheme breakdown in MITRE framework
With Group-IB’s Fraud Matrix, Group-IB’s ability to provide integrated solutions that streamline operations, offer real-time and highly actionable insights to stop fraud and risks in tracks, and enhance collaboration between security teams for better performance positions us as a trusted business partner in the fight against digital fraud and cybercrime. To explore our team’s case studies and reports that showcase how The Fraud Matrix dissects real-world fraud schemes, access the following resources:


































