Introduction
Mobile Device Management, or MDM, is a software deployed by many companies to centralize the management of mobile devices – most commonly laptops, tablets, and smartphones – that are issued to its employees. Administrators leveraging an MDM service can perform various tasks depending on the specific vendor’s offerings. Common functionalities include installing applications — both from official markets and custom sources — tracking geolocation, accessing SMS logs, configuring profiles, device locking, and more. Each of these features contributes to efficient device management within organizational contexts.
Over the course of the past year, Group-IB’s researchers have been combing the dark web and analyzing vast amounts of compromised data to discover at least 1,500 pairs of logins and passwords from local and public MDM services, which were stolen as a result of targeted malware attacks by threat actors.
Extent of External Accessibility and Associated Risks
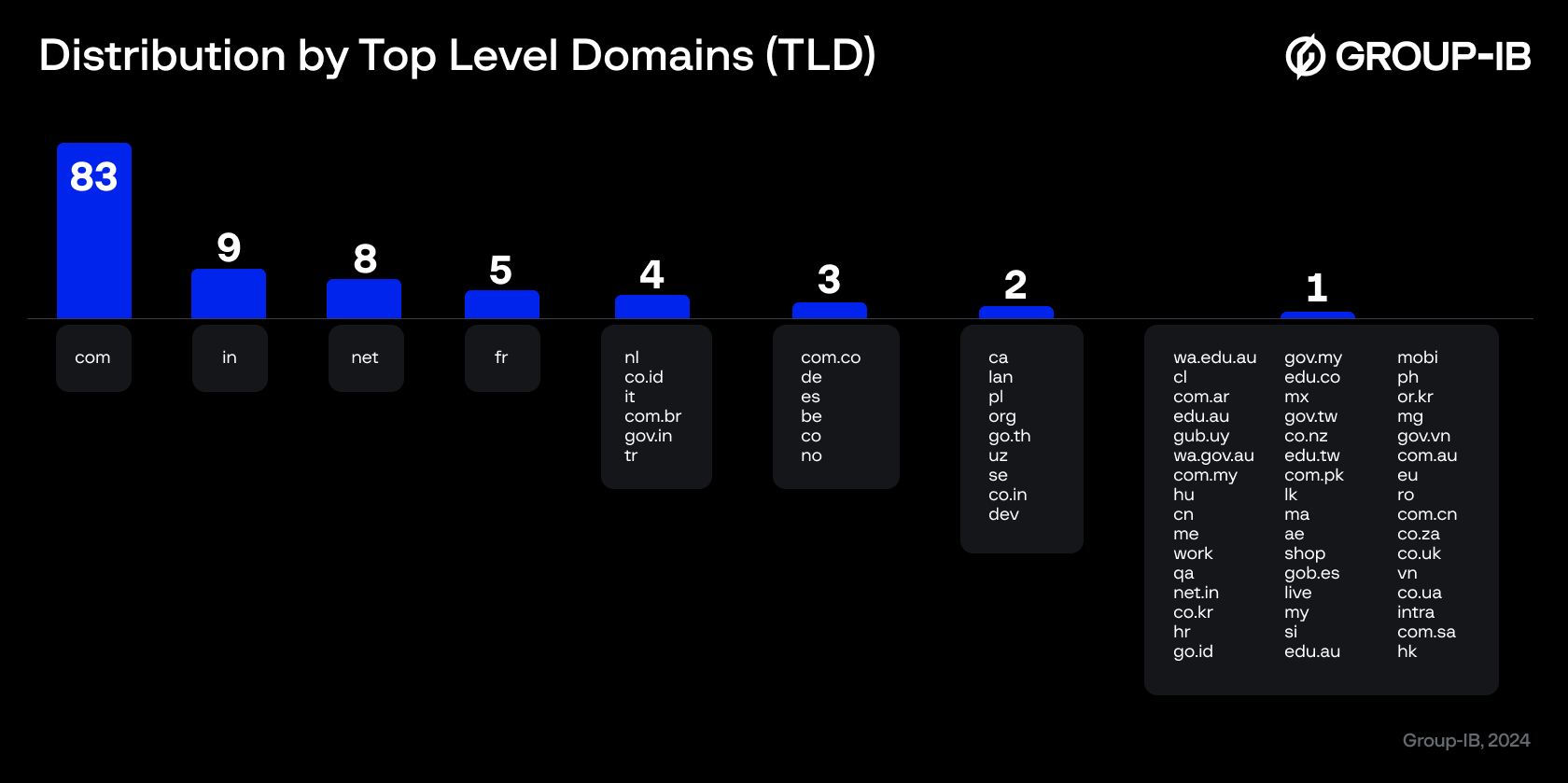
In our analysis of the stolen logins and passwords from the dark web, we found that 27.5% of web-based Mobile Device Management (MDM) service interfaces were accessible from the external Internet. These services were owned by companies ranging in size from 10 to 5,000 employees from India, France, the Netherlands, Indonesia, Italy, Brazil, Turkey, Germany, Spain, and Belgium, some of which have reported revenues exceeding US$1 billion. This indicates a significant exposure of MDM services to potential risks associated with external accessibility.
Risks to Business Continuity
In the event of leaked credentials, threat actors could exploit unauthorized access to managed devices within an organization’s network. As we previously highlighted in our exposé of the GoldFactory iOS malware, this could enable them to peruse sensitive corporate data, implant malicious software, or assume remote control over the devices.
Access to MDM consoles using compromised credentials grants threat actors potential access to extensive organizational information, such as device configurations, user profiles, and potentially sensitive corporate data stored on managed devices. Such breaches could result in severe repercussions for the organization’s reputation, financial stability, and legal compliance.
Compromised MDM credentials could also empower threat actors to disrupt organizational operations by remotely locking or wiping devices, causing disorder and potentially substantial downtime, which in turn significantly impacts productivity and revenue, while at the same time causing harm to the organization’s standing in the industry and among its customers.
Distribution by Top Level Domains (TLD)
Conclusion
In conclusion, Mobile Device Management (MDM) systems play a crucial role in efficiently managing and securing mobile devices within organizational environments. However, recent findings underscore significant vulnerabilities that organizations must address to safeguard their data and operations. The exposure of MDM services on the dark web, coupled with the accessibility of web-based interfaces from external networks, highlights the urgent need for robust security measures.
The risks associated with compromised MDM credentials extend beyond data breaches to potential operational disruptions and regulatory non-compliance. Digital nomads, who often work remotely using personal devices enrolled in MDM systems, face heightened security challenges due to varied network environments and potential exposure to malware. These factors underscore the critical importance of implementing comprehensive security protocols, including encryption, multi-factor authentication, and regular audits of access controls.
Recommendations
- If a hack has already occurred or if you have discovered access to your MDM network on the Dark Web, it may be necessary to re-enroll all devices into the MDM system with new credentials. This step ensures that all devices are securely managed under updated security policies. Additionally, promptly revoke your credentials to prevent unauthorized access, which is crucial in halting any further exploitation.
- Monitoring the sale of access to your networks and the leakage of credentials from your systems on the Dark Web is essential. Implementing continuous monitoring and threat intelligence tools, such as Group-IB’s Unified Risk Platform, can help detect unauthorized access attempts and the presence of compromised credentials being sold.
- The third important tip is to strengthen your defense. Implement MFA for accessing MDM systems. This adds an extra layer of security, making it significantly harder for attackers to gain access with just a password. Educate employees and administrators about best practices for credential management and phishing awareness. Regular training helps to maintain a high level of security awareness across the organization.
Discover Group-IB’s Unified Risk Platform
Prevent breaches, fraud and brand abuse with a single platform!