Introduction
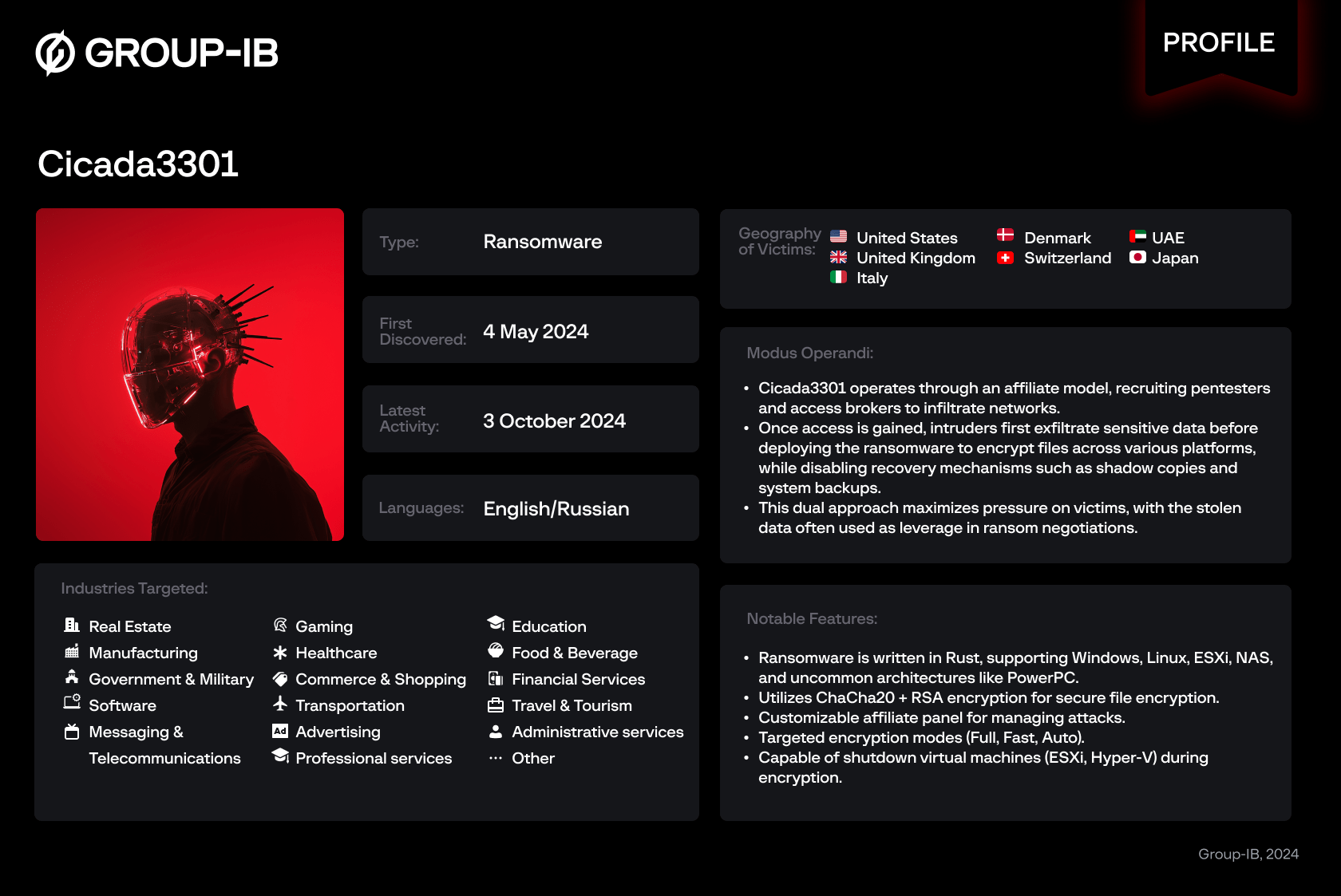
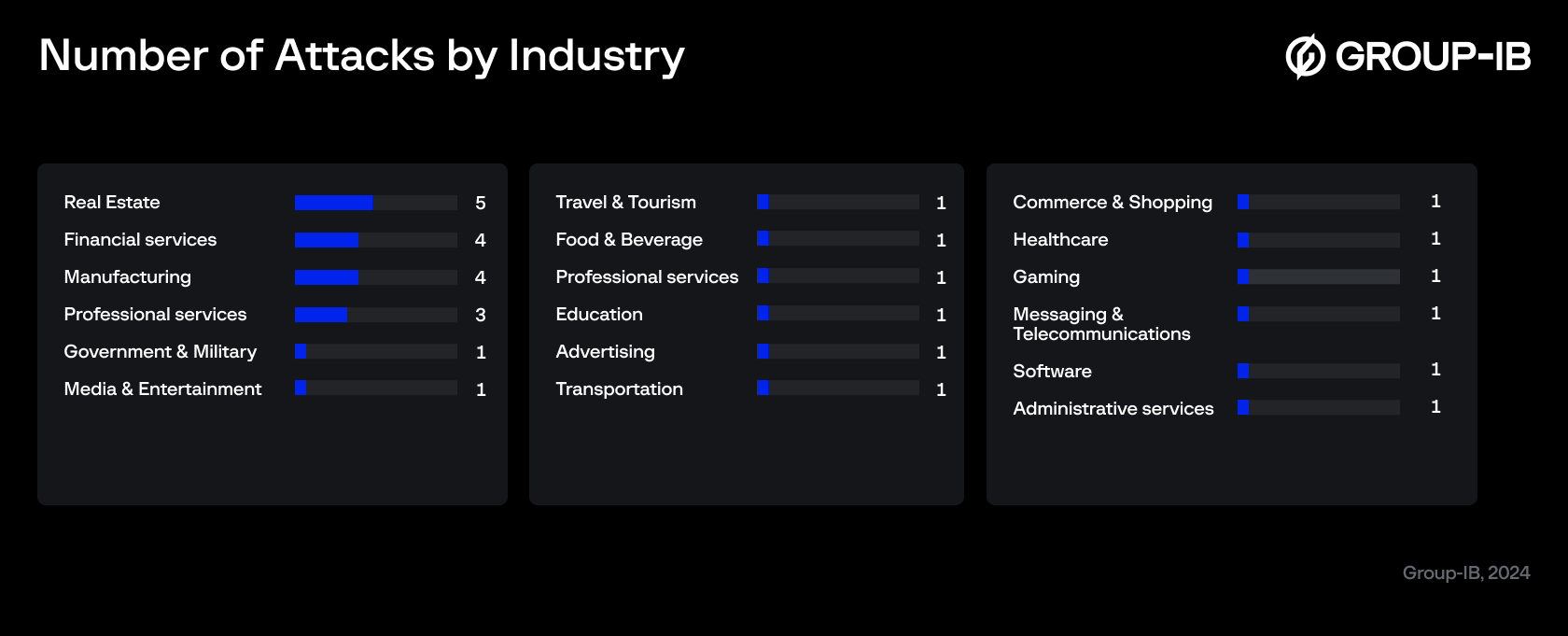
Since its discovery in June 2024, the Cicada3301 ransomware-as-a-service (RaaS) group has been observed targeting businesses across a wide range of critical sectors. Between June and October 2024, the group published stolen data from 30 companies on their dedicated leak sites (DLS), with 24 instances of attacks that claimed victims based in the United States and the United Kingdom.
Group-IB has recently and successfully gained access to the Cicada3301 ransomware affiliate panel. In this blog, we share its inner workings based on our thorough analysis of the available ransomware versions offered within the affiliate panel, and all accessible sections to provide a definitive assessment of this threat.
Researcher’s Note: The ‘original’ Cicada 3301 emerged in 2012 as an enigmatic cryptographic puzzle group, challenging individuals worldwide with complex ciphers, hidden clues in both digital and physical spaces, and references to esoteric literature, philosophy, and art, creating an aura of intellectual intrigue and deep mystery. The group’s motives and true identity remain shrouded in speculation, with theories ranging from a secret society to a covert recruitment tool for intelligence agencies.
Key Discoveries in this Blog
- Emergence of Cicada3301 Ransomware Group: Since its discovery in June 2024, Cicada3301 has rapidly targeted 30 organizations across critical sectors within three months, with a significant focus on the USA and the UK.
- Advanced Multi-Platform Ransomware: The ransomware is written in Rust, supporting Windows, Linux, ESXi, and NAS platforms, even extending to uncommon architectures like PowerPC.
- Sophisticated Affiliate Program: Cicada3301 runs an affiliate program recruiting penetration testers (pentesters) and access brokers, offering a 20% commission, and providing a web-based panel with extensive features for affiliates.
- Complex Encryption Techniques: Utilizes ChaCha20 and RSA encryption with configurable modes (Full, Fast, Auto), capable of both full and partial file encryption to optimize the speed and impact of the attacks.
- Aggressive Tactics for Maximum Impact: Features include shutting down virtual machines on ESXi and Hyper-V, terminating processes and services, deleting shadow copies, and encrypting network shares to maximize disruption.
Who may find this blog interesting:
- Cybersecurity analysts and corporate security teams
- Malware analysts
- Threat intelligence specialists
- Cyber investigators
- Computer Emergency Response Teams (CERT)
- Law enforcement investigators
- Cyber police forces
Threat Actor Profile
Onion domain of dedicated leak site (DLS) of Cicada3301 ransomware:
hxxp[:]//cicadabv7vicyvgz5khl7v2x5yygcgow7ryy6yppwmxii4eoobdaztqd[.]onion/
Figure 1. Screenshot of a dedicated leak site (DLS) of Cicada3301 ransomware.
Infiltrating the Cicada3301 Ransomware Group
On 29-June 2024, a user named “Cicada3301” started an affiliate program of the Cicada3301 ransomware as a topic on the popular underground dark web forum “RAMP”.
Figure 2. Screenshot of the user profile ‘Cicada3301’ on the RAMP forum.
Affiliate Program Recruitment:
The topic starts by stating that Cicada3301 is seeking pentesters and access advertisers, and a “mini-interview” is required as a prerequisite for participation in the affiliate program. Interestingly, it also strictly prohibits its affiliates from conducting any operations in the countries of the Commonwealth of Independent States (CIS), and that panel access must not be shared with third parties without support approval. The topic also states that the affiliates will receive a 20% cut of the total payout from its victims, which would be paid-out via wallets in the chat. In instances where the payouts exceed US$1.5-million, two wallets would be used—one for the affiliate, and another for the program.
LOCKER Details:
The locker is developed in Rust, and utilizes ChaCha20 and RSA encryption, offering multiple modes including Full, Fast (15 blocks of 1 MB), and Auto. It operates offline and is compatible with Windows (from version 7), Linux, ESXi, and NAS systems. The locker supports multithreading and network mode, featuring targeted encryption, process termination, and system cleanup prior to encryption. It leaves instructions in each encrypted folder and excludes system-critical files and directories, while also supporting ESXi/Hyper-V VM stoppage. A decryption key is required to initiate the decryption process.
WEB Interface:
The web interface is only accessible via Tor, and provides services including chat, support, and sub-affiliate accounts. The interface also features a locker builder and landing page generator, as well as customizable ransom notes and file storage for data leaks. Notably, private keys are not stored on servers. Cybercriminals remain wary after a significant incident involving the LockBit ransomware group, in which their private keys were leaked following Europol’s
“Operation Cronos”, disrupting their affiliates’ ransom deals, and allowing their victims to obtain decryptors for free. As a result, RaaS owners now claim that they do not handle private decryption keys on their server, although this claim by the owners could not be verified.
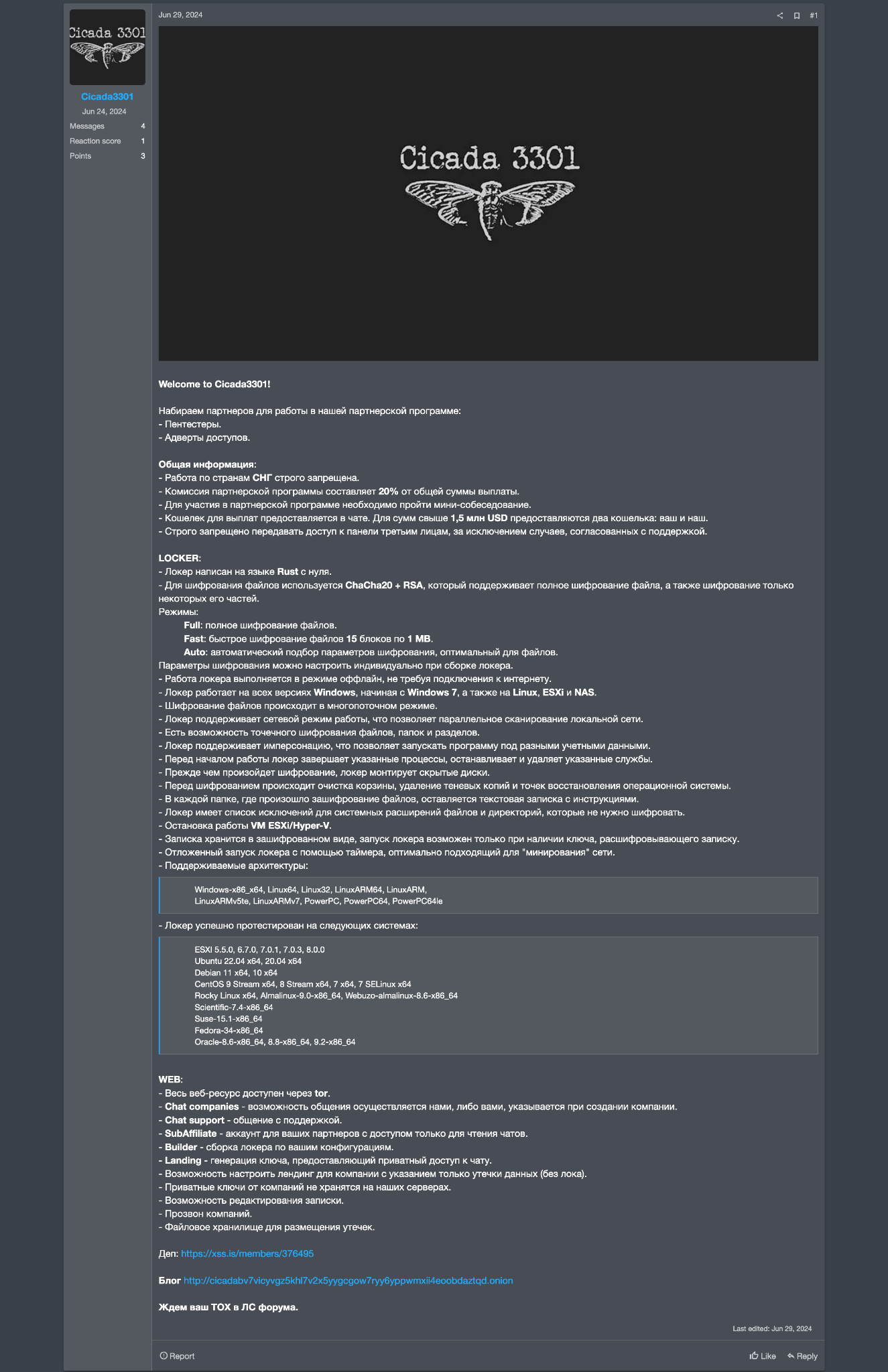
Figure 3. Screenshots of a post by Cicada3301 promoting its ransomware-as-a-service on the RAMP forum.
The following is a translation of the topic posted by Cicada3301, from Russian to English:
Welcome to Cicada3301!
We are recruiting partners for our affiliate program:
– Pentesters.
– Access advertisers.
General Information:
– Operations in CIS countries are strictly prohibited.
– Affiliate program commission is 20% of the total payout.
– Participation requires a mini-interview.
– Payout wallet is provided in the chat; for amounts over $1.5 million USD, two wallets are provided: one for you and one for us.
– It is strictly forbidden to share panel access with third parties unless approved by support.
LOCKER:
– Developed from scratch in Rust.
– Uses ChaCha20 + RSA for file encryption, supporting both full and partial file encryption.
Encryption Modes:
Full: Full file encryption.
Fast: Fast encryption of 15 blocks of 1 MB.
Auto: Automatic selection of optimal encryption parameters.
– Configurable encryption parameters at locker build.
– Works offline, no internet connection required.
– Compatible with all versions of Windows from Windows 7, as well as Linux, ESXi, and NAS.
– Supports multithreading and network mode for parallel local network scanning.
– Features targeted encryption for files, folders, and partitions.
– Supports impersonation to run under different credentials.
– Terminates specified processes and stops/deletes specified services before encryption.
– Mounts hidden drives before encryption.
– Cleans recycle bin, deletes shadow copies, and removes system restore points before encryption.
– Leaves a text note with instructions in each encrypted folder.
– Has an exclusion list for system file extensions and directories that should not be encrypted.
– Stops VM ESXi/Hyper-V operations.
– Note is stored encrypted; locker can only be started with a decryption key.
– Supports delayed locker start via timer, suitable for “mining” the network.
– Supported architectures:
Windows-x86_x64, Linux64, Linux32, LinuxARM64, LinuxARM,
LinuxARMv5te, LinuxARMv7, PowerPC, PowerPC64, PowerPC64le
– Successfully tested on the following systems:
ESXI 5.5.0, 6.7.0, 7.0.1, 7.0.3, 8.0.0
Ubuntu 22.04 x64, 20.04 x64
Debian 11 x64, 10 x64
CentOS 9 Stream x64, 8 Stream x64, 7 x64, 7 SELinux x64
Rocky Linux x64, Almalinux-9.0-x86_64, Webuzo-almalinux-8.6-x86_64
Scientific-7.4-x86_64
Suse-15.1-x86_64
Fedora-34-x86_64
Oracle-8.6-x86_64, 8.8-x86_64, 9.2-x86_64
WEB:
– Entire web resource accessible via Tor.
– Chat companies: Communication can be handled by us or by you, as specified when creating the company.
– Chat support: Communication with support.
– SubAffiliate: Account for your partners with read-only chat access.
– Builder: Locker build according to your configurations.
– Landing: Key generation providing private chat access.
– Option to set up a landing page indicating only data leaks (without encryption).
– Private keys from companies are not stored on our servers.
– Option to edit the note.
– Company call handling.
– File storage for data leaks.
Deposit: https://xss.is/members/376495
Blog: http://cicadabv7vicyvgz5khl7v2x5yygcgow7ryy6yppwmxii4eoobdaztqd.onion
Awaiting your TOX in forum PM.
Group-IB Threat Intelligence analysts infiltrated the Cicada3301 Ransomware group and contacted the user “Cicada3301” via Tox, an instant messaging protocol, and through our private conversations received access to the affiliate program of the Cicada3301 ransomware.
Figure 4. Screenshot of the authentication page of Cicada3301 ransomware group.
Within the dashboard of the Affiliates’ panel of Cicada3301 ransomware group contained sections such as Dashboard, News, Companies, Chat Companies, Chat Support, Account, an FAQ section, and Log Out.
Dashboard
The “Dashboard” section provides an overview of the successful or failed logins by the affiliate, fingerprint details, and a chart depicting the number of companies attacked by the affiliate.
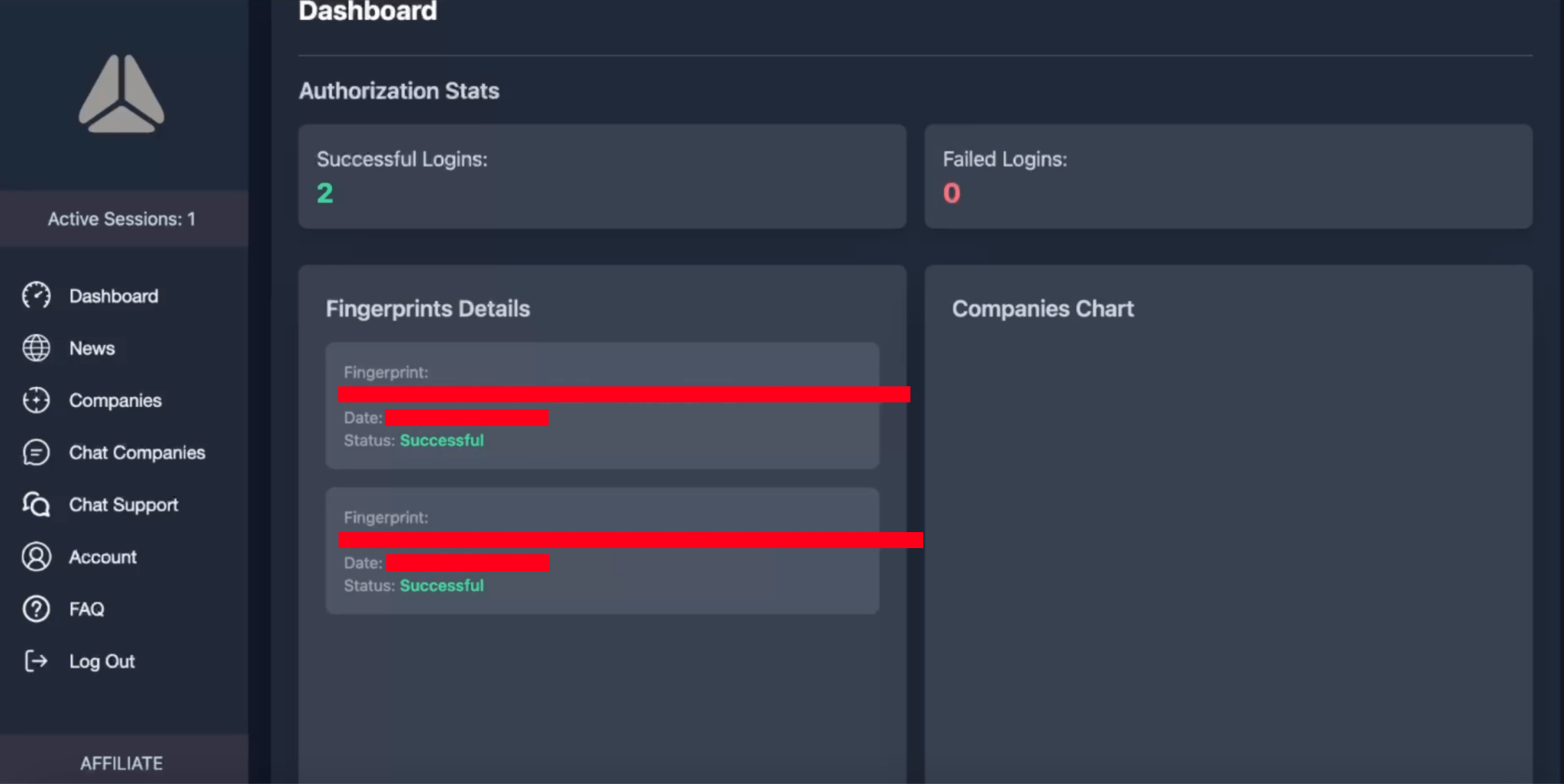
Figure 5. Screenshot of the section “Dashboard” of Cicada3301 ransomware panel.
News
The section “News” contains information about updates and news of the Cicada3301 ransomware program. During the review of the “News” section within the affiliate panel, we identified the following updates in the operations of the Cicada3301 Ransomware RaaS group:
|
Date |
Update |
| 4 May 2024 | Announced plans to implement new features:
|
| 13 June 2024 | Released a series of updates and optimizations:
|
| 15 June 2024 | Introduced their own file server and invited affiliates to start uploading exfiltrated data |
| 18 June 2024 | Completed the setup of the call center and invited affiliates to provide contact numbers, victim names, and ransom texts for calls |
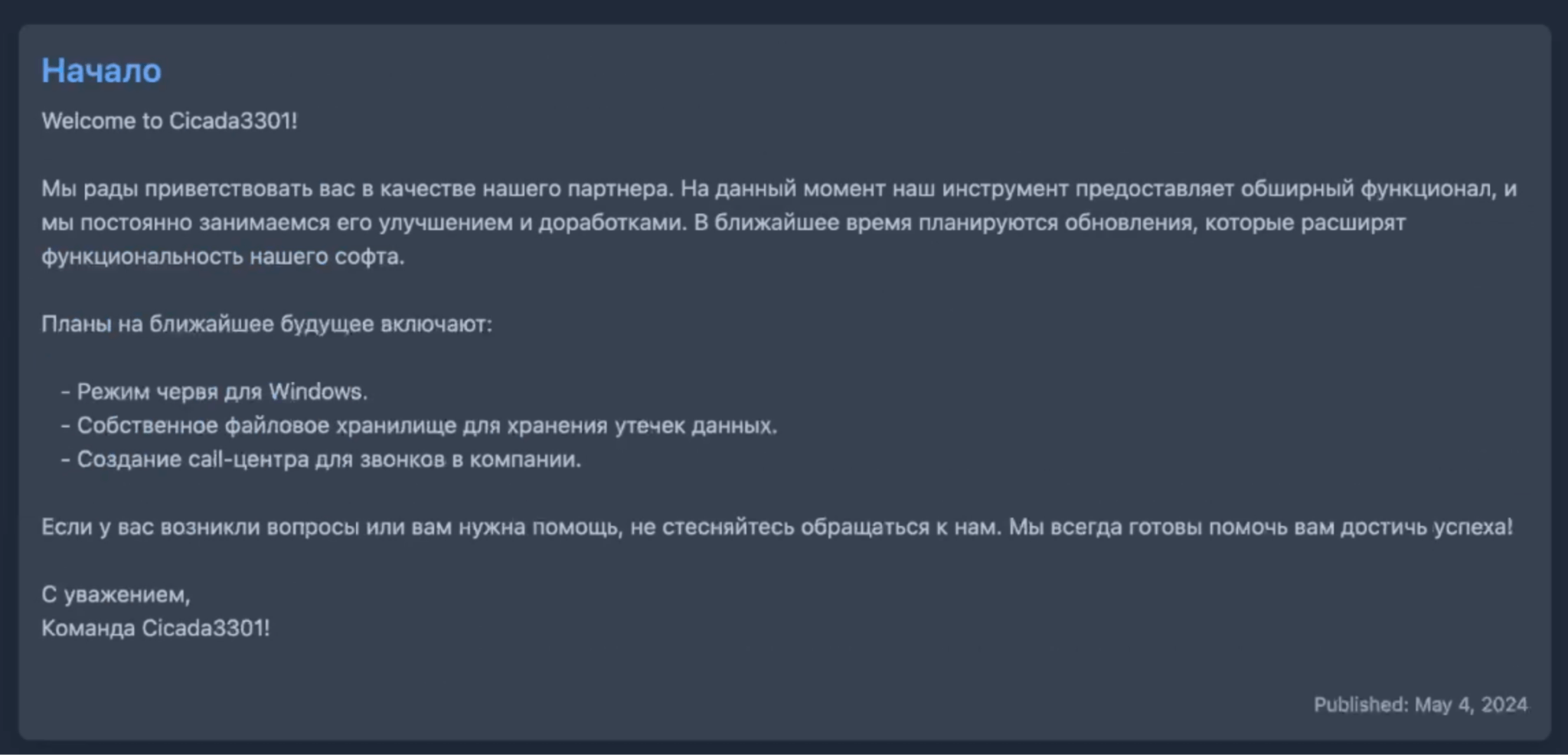
Figure 6. Screenshot of a post in the “News” section of Cicada3301 ransomware panel, dated 4 May 2024.
The following is a translation of the post above (Figure 6), from Russian to English:
Start
Welcome to Cicada3301!
We are pleased to welcome you as our partner. At the moment, our tool provides extensive functionality, and we are constantly improving and improving it. Updates are planned in the near future that will expand the functionality of our software.
Plans for the near future include:
– Worm mode for Windows.
– Own file storage for storing leaked data.
– Creation of a call center for calls in the company.
If you have any questions or need help, don’t hesitate to contact us. We are always ready to help you achieve success!
Sincerely,
Team Cicada3301!
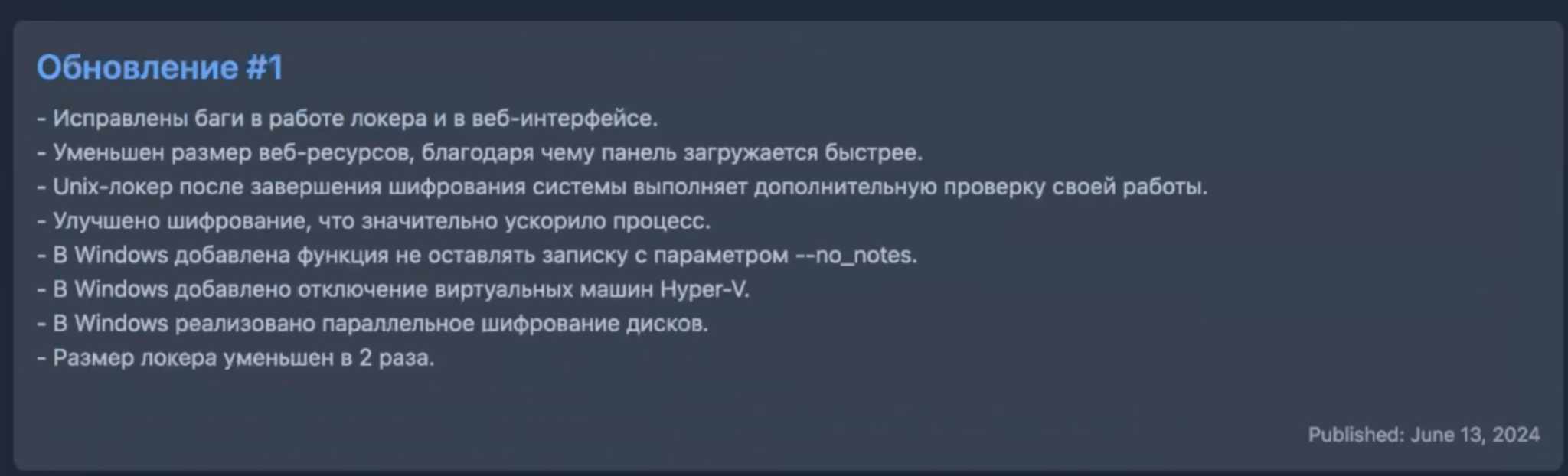
Figure 7. Screenshot of “Update #1” in “the News” section of the Cicada3301 ransomware panel, dated 13 June 2024.
The following is a translation of the post above (Figure 7), from Russian to English:
Update #1
– Fixed bugs in the locker and the web interface.
– The size of web resources has been reduced, making the panel load faster.
– After completing system encryption, the Unix locker performs an additional check of its operation.
– Improved encryption, which significantly speeded up the process.
– In Windows, a function has been added not to leave a note with the –no_notes parameter.
– Added disabling Hyper-V virtual machines to Windows.
– Windows implements parallel disk encryption.
– The size of the locker is reduced by 2 times.
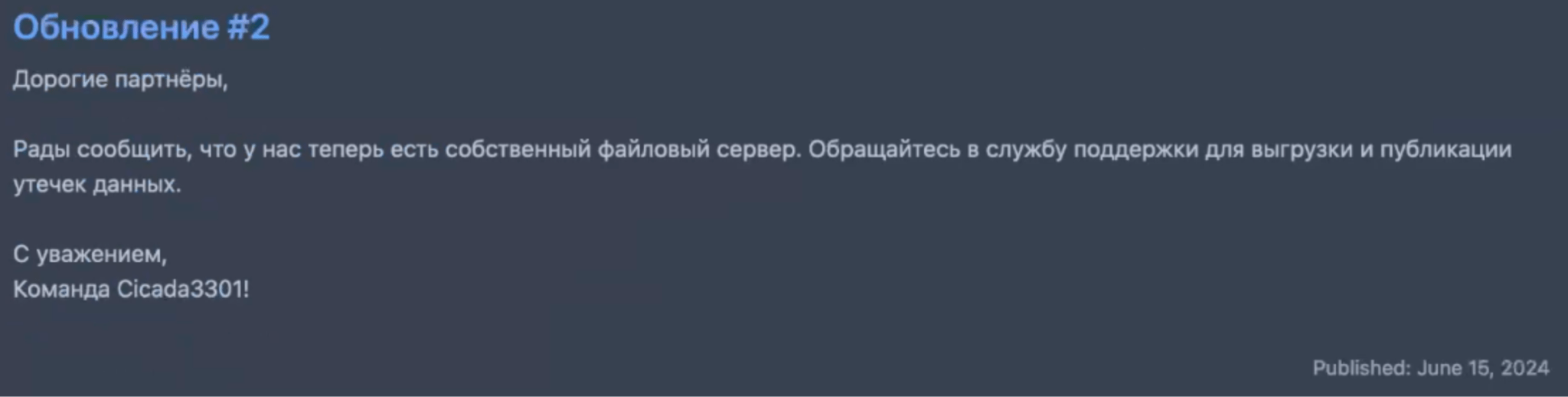
Figure 8. Screenshot of “Update #2” in the “News” section of Cicada3301 ransomware panel, dated 15 June 2024.
The following is a translation of the post above (Figure 8), from Russian to English:
Update #2
Dear partners,
We are pleased to announce that we now have our own file server. Contact support to upload and publish data leaks.
Sincerely,
Team Cicada3301!
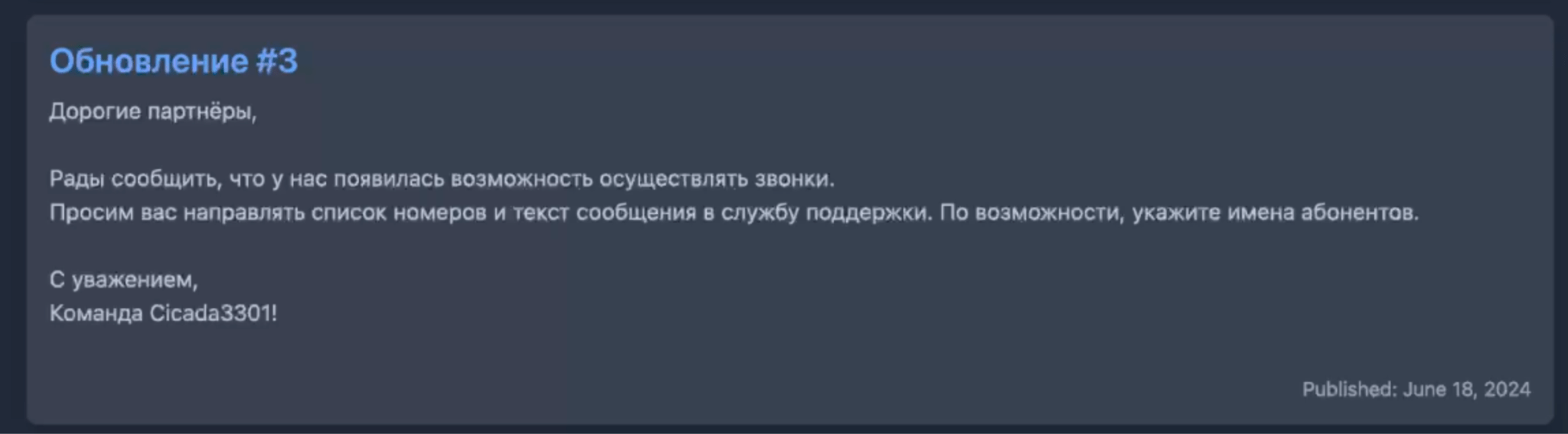
Figure 9. Screenshot of “Update #3” in the “News” section of the Cicada3301 ransomware panel, dated 18 June 2024.
The following is a translation of the post above (Figure 9), from Russian to English:
Update #3
Dear partners,
We are pleased to announce that we have the opportunity to make calls.
We ask you to send a list of numbers and the text of the message to the support service. If possible, include the names of the callers.
Sincerely,
Team Cicada3301!
Companies
Within the “Companies” section, affiliates can add their victims, build samples of Cicada3301 ransomware, and configure these samples.
Figure 10. Screenshot of the “Companies” section of Cicada3301 ransomware panel.
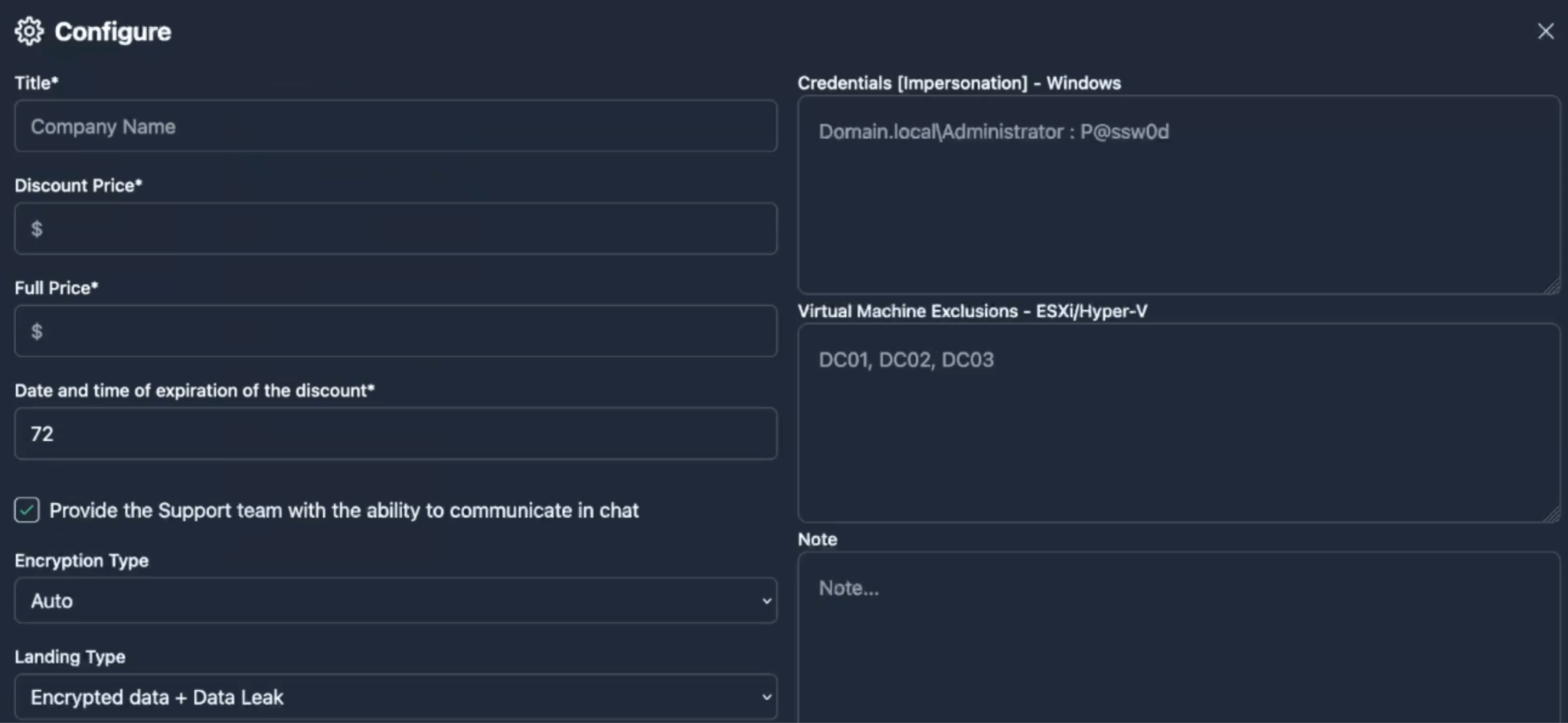
Using the “Create company” function, affiliates can configure the name of the company (victim), the full price (amount) of the ransom demanded, as well as a discounted price of the ransom and the discount expiration date (in hours).
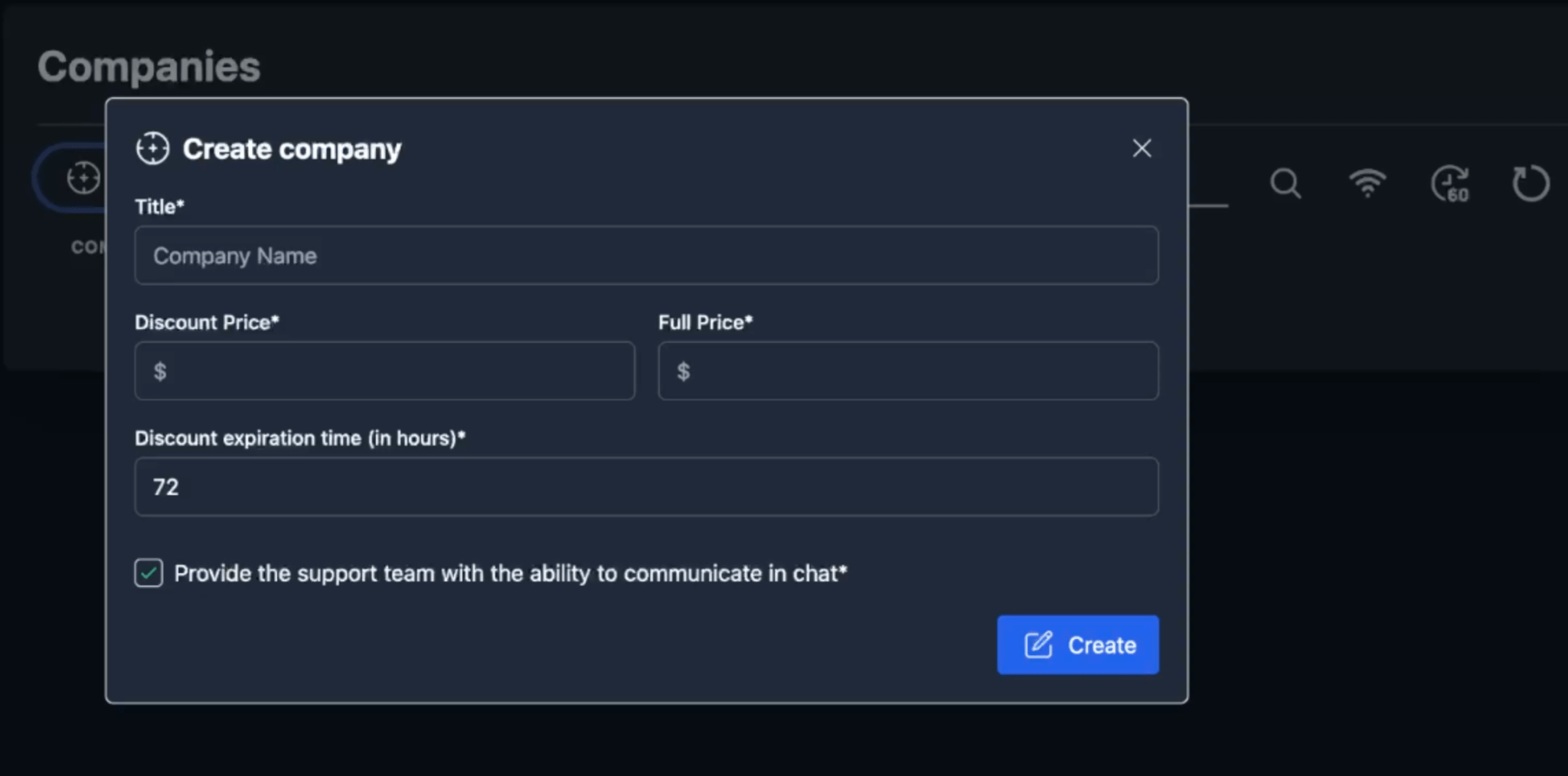
Figure 11. Screenshot of the “Create company” panel within the “Companies” section of the Cicada3301 ransomware panel.
Once the affiliates create entries of the companies they attacked, they will be able to see their victims on the “Companies” section, and configure ransomware samples for specific victims.
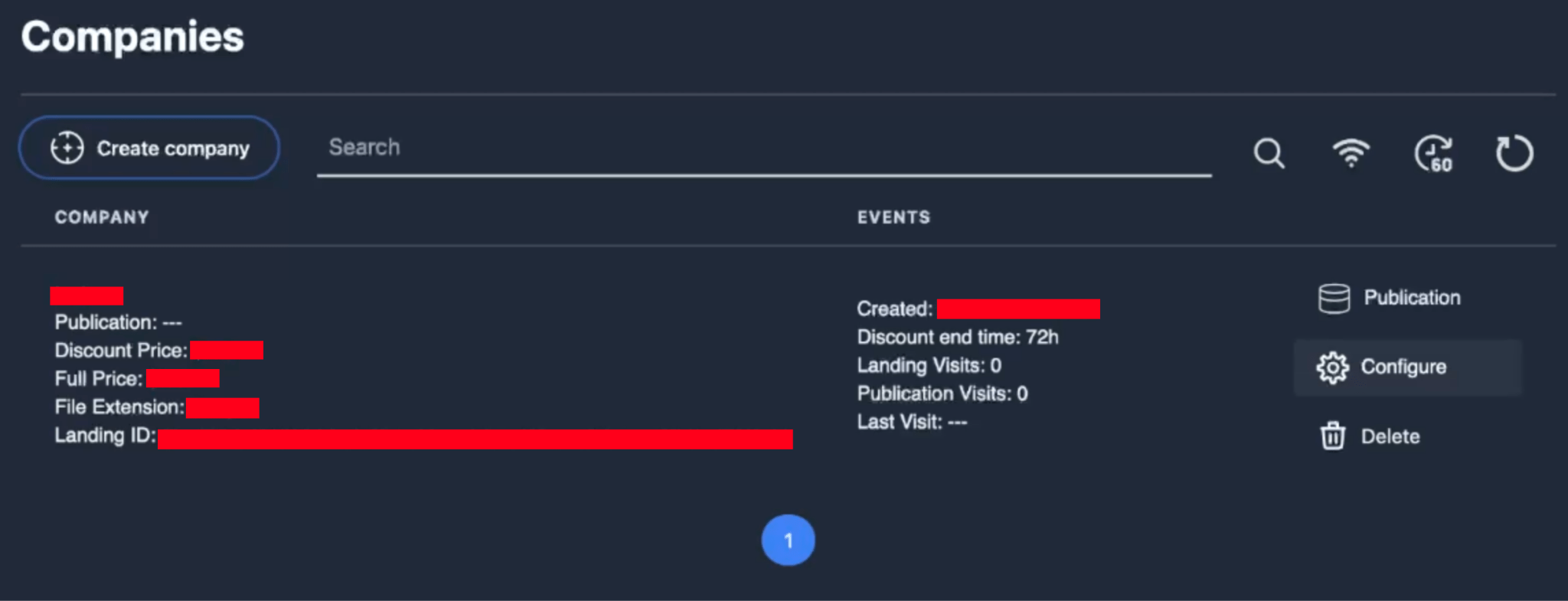
Figure 12. Screenshot of the “Companies” section after an entry of a victim is created.
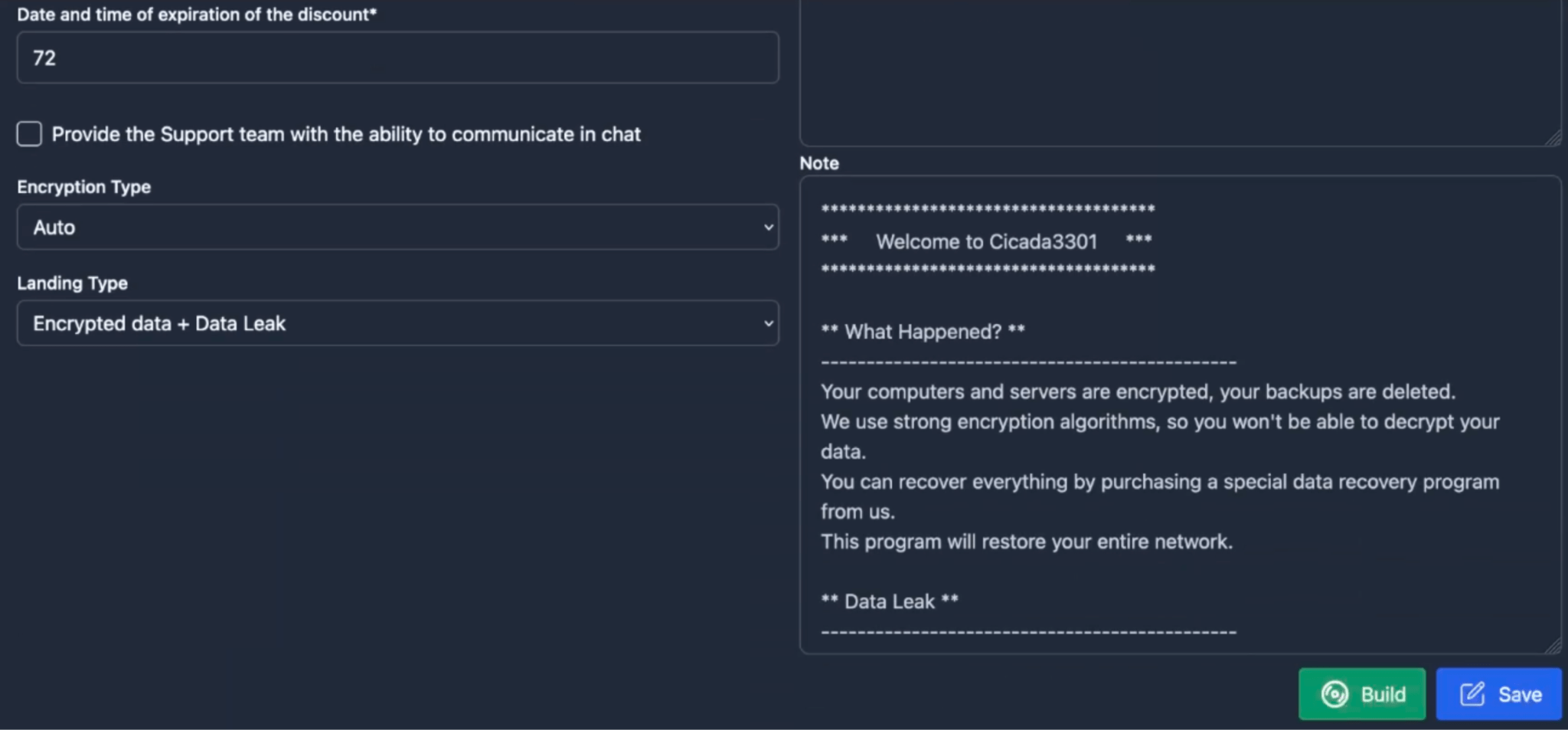
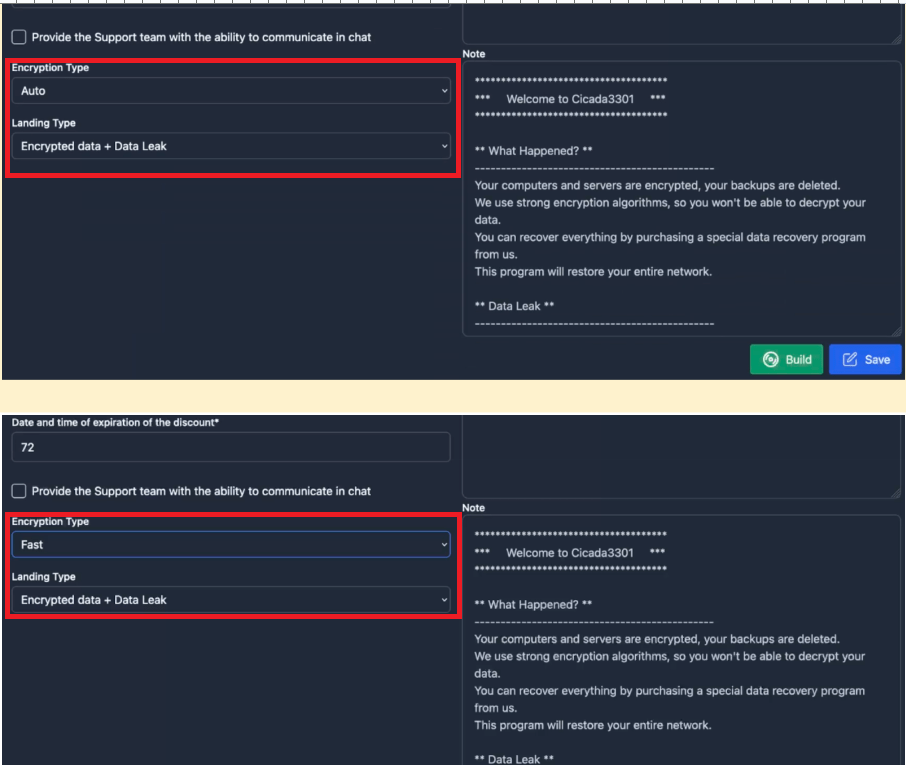
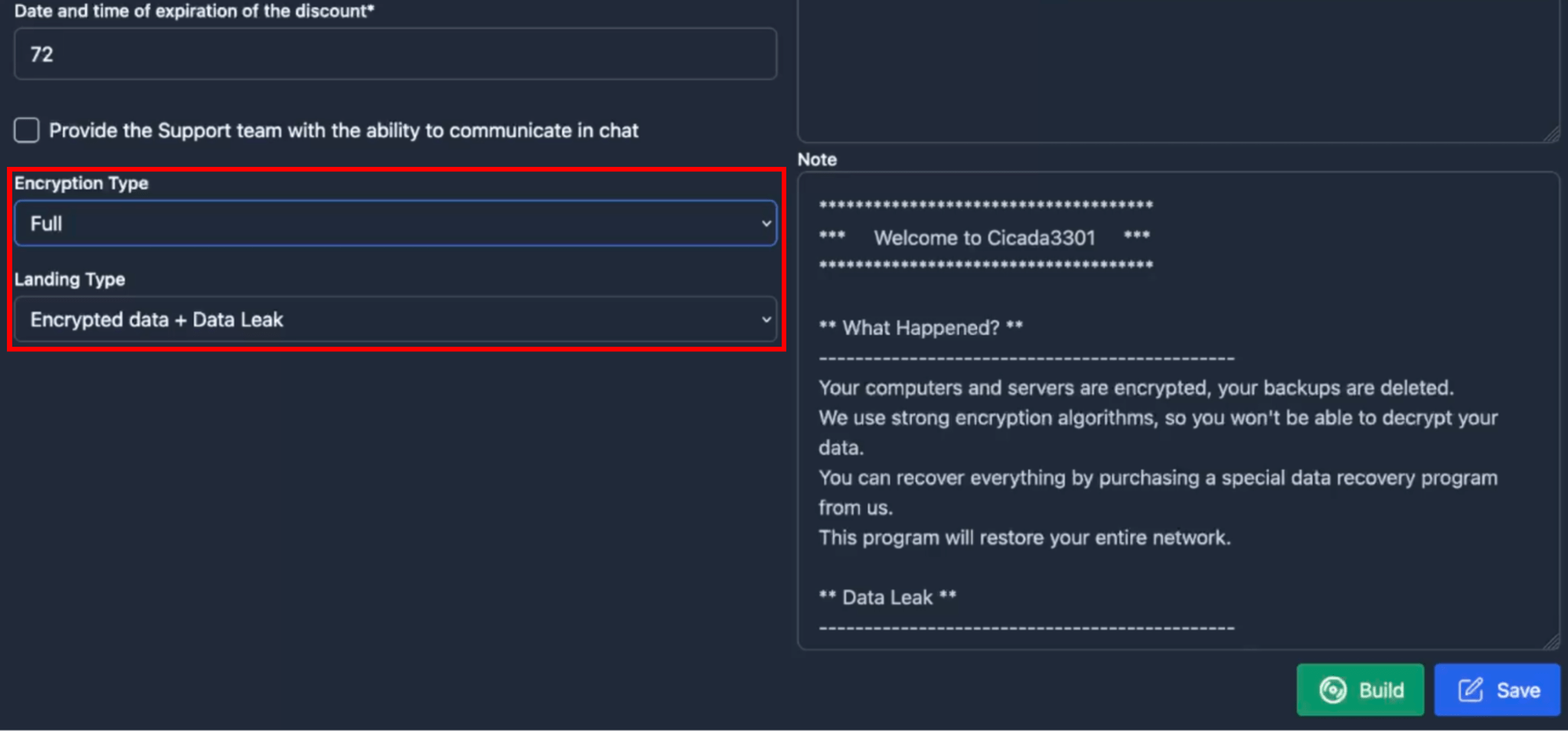
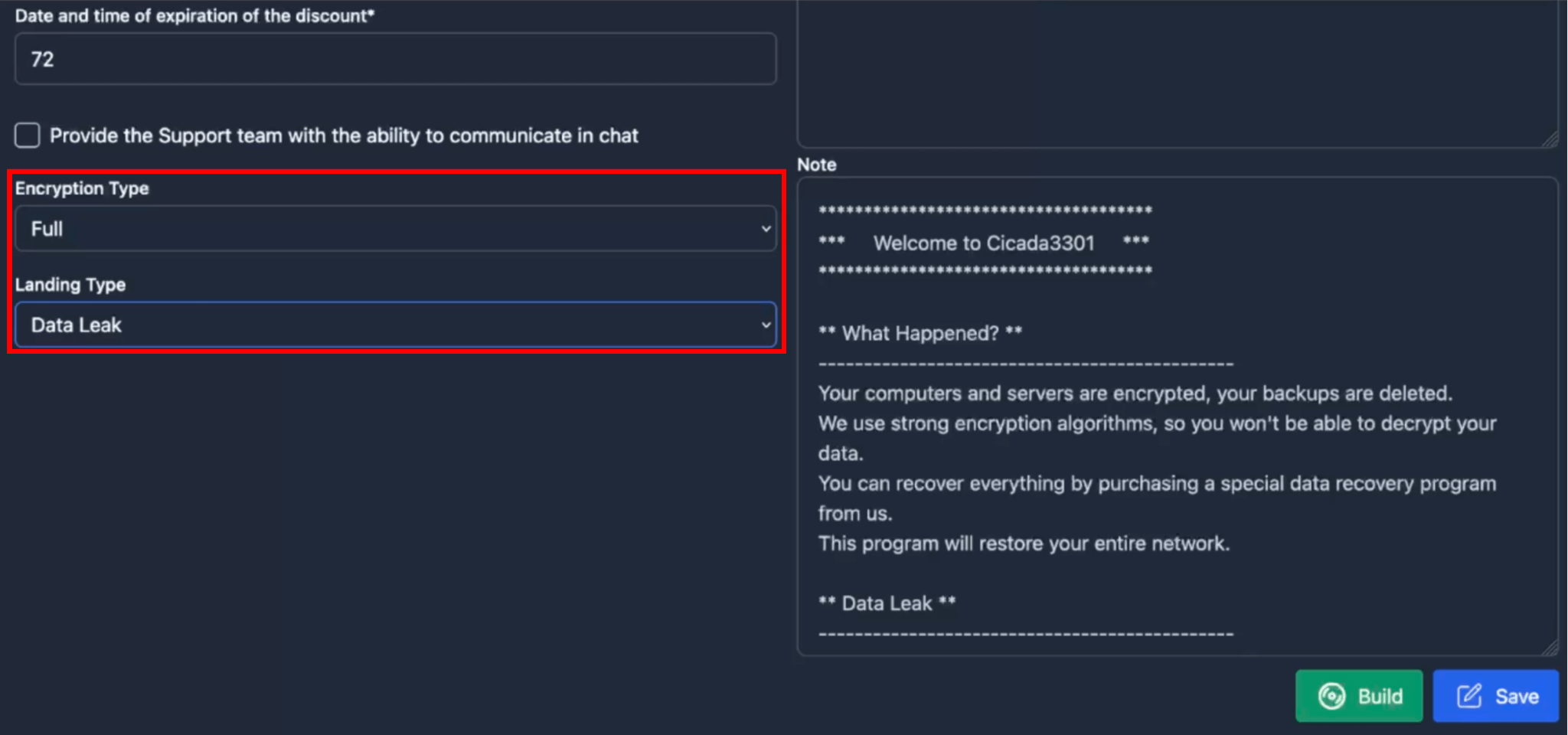
In addition to the fields that were previously highlighted in Figure 12, affiliates can make further changes via the “Configure” panel such as the type of encryption (Fast/Full/Auto), the type of landing page (Encrypted Data + Data Leak or Data leak only), credentials (Impersonation) for Windows-based platforms, virtual machine exclusions for ESXi/Hyper-V, as well as the text of the ransom note.
Chat Companies
Within the “Chat Companies” section, affiliates are greeted with an interface where they can select and search for the necessary chats with victims via the negotiation page, and communicate with them regarding the ransom during negotiations.
Figure 14. Screenshot of the “Chat Companies” section of the Cicada3301 ransomware panel.
Chat Support
The “Chat Support” section contains an interface where you can communicate with representatives of the Cicada3301 ransomware group to resolve various issues. As mentioned in the “News” section, affiliates can use this interface to request for a phone call service to contact their victims.
Figure 15. Screenshot of the “Chat Support” section of the Cicada3301 ransomware panel.
Account
The “Account” section allows affiliates to reset and change their password for the affiliate panel.
Figure 16. Screenshot of the “Account” section of the Cicada3301 ransomware panel.
FAQ
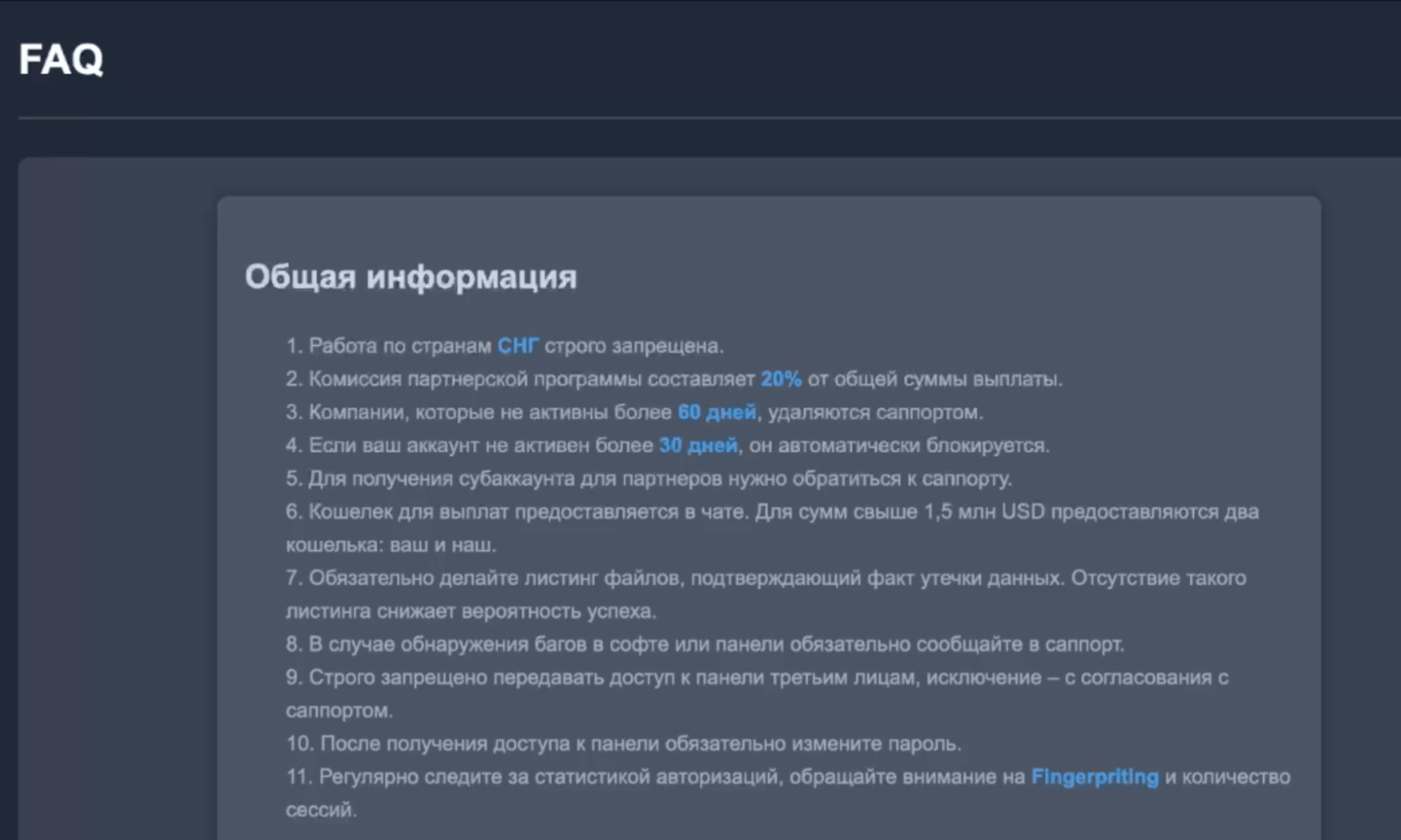
As for the “FAQ” section, the administrators of the Cicada3301 ransomware group provide rules and guides on creating victims in the “Companies” section, working with the builder, and executing samples of Cicada3301 ransomware on various operating systems.
The following is a translation of the “General Information” content within the “FAQ” section, from Russian to English:
General Information
1. Work in the CIS countries is strictly prohibited.
2. The affiliate program commission is 20% of the total payment amount.
3. Companies that are inactive for more than 60 days are removed by support.
4. If your account is inactive for more than 30 days, it is automatically blocked.
5. To get a subaccount for partners, you need to contact support.
6. The wallet for payments is provided in the chat. For amounts over 1.5 million USD, two wallets are provided: yours and ours.
7. Be sure to make a file listing that confirms the fact
data leaks. The absence of such a listing reduces the likelihood of success.
8. If you find bugs in the software or panel, be sure to report it to support.
9. It is strictly prohibited to transfer access to the panel to third parties, with the exception of agreement with support.
10. After gaining access to the panel, be sure to change the password.
11. Regularly monitor authorization statistics, pay attention to Fingerpriting and the number of sessions.
The following is a translation of the “Locker” content within the “FAQ” section, from Russian to English:
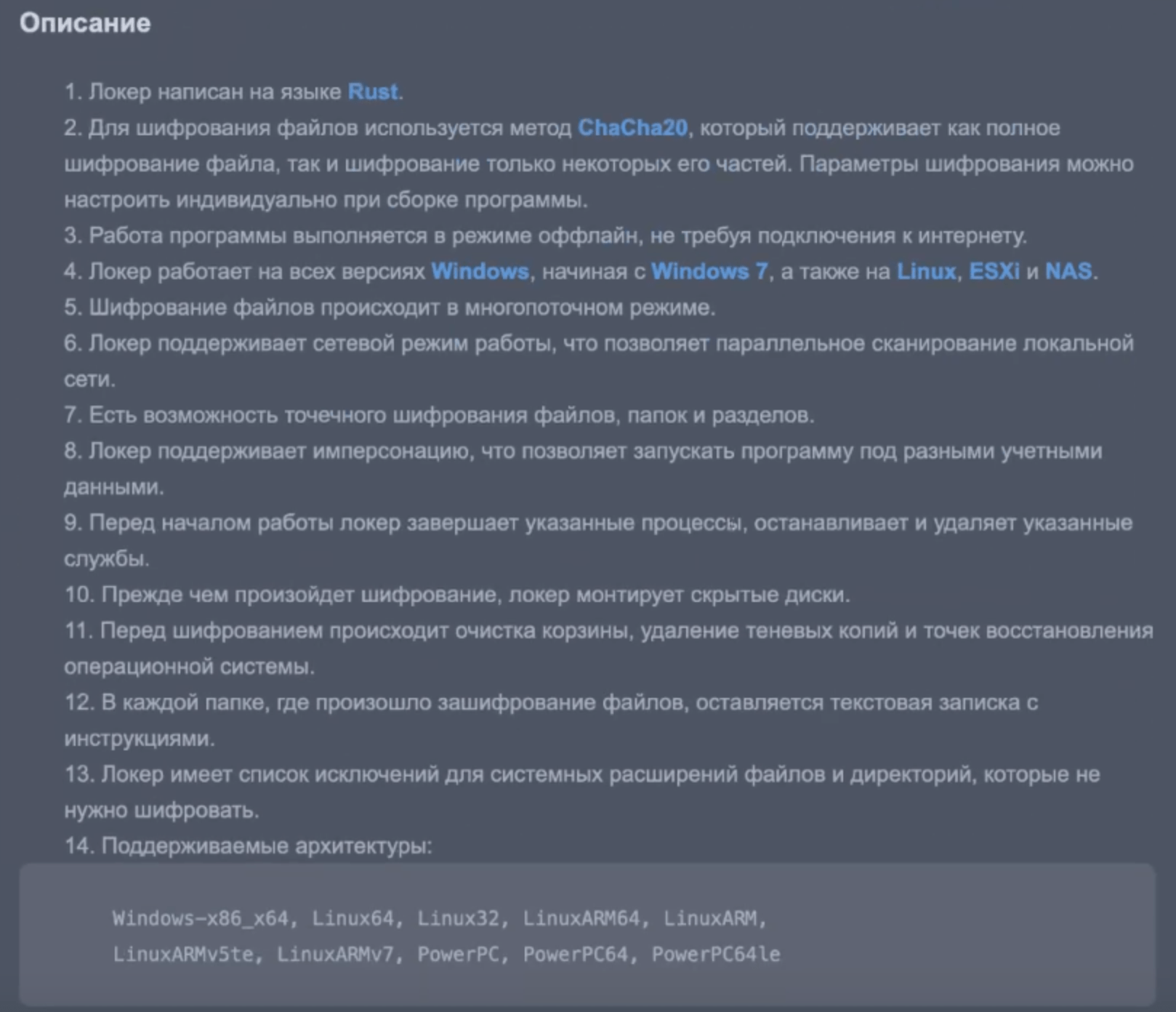
Description
1. The locker is written in Rust.
2. To encrypt files, the ChaCha20 method is used, which supports both full file encryption and encryption of only some of its parts. Encryption parameters can be configured individually when building the program.
3. The program works offline, without requiring an Internet connection.
4. The locker works on all versions of Windows, starting with Windows 7, as well as on Linux, ESXi and NAS.
5. File encryption occurs in multi-threaded mode.
6. The locker supports network operating mode, which allows parallel scanning of the local network.
7. It is possible to provide point-to-point encryption of files, folders and partitions.
8. The locker supports impersonation, which allows you to run the program under different credentials.
9. Before starting work, the locker terminates the specified processes, stops and deletes the specified services.
10. Before encryption occurs, the locker mounts the hidden drives.
11. Before encryption, the recycle bin is emptied, shadow copies and operating system restore points are deleted.
12. A text note with instructions is left in each folder where files have been encrypted.
13. The locker has a list of exceptions for system extensions of files and directories that do not need to be encrypted.
14. Supported architectures:
Windows-x86_x64, Linux64, Linux32, LinuxARM64, LinuxARM,
LinuxARMv5te, LinuxARMv7, PowerPC, PowerPC64, PowerPC64le
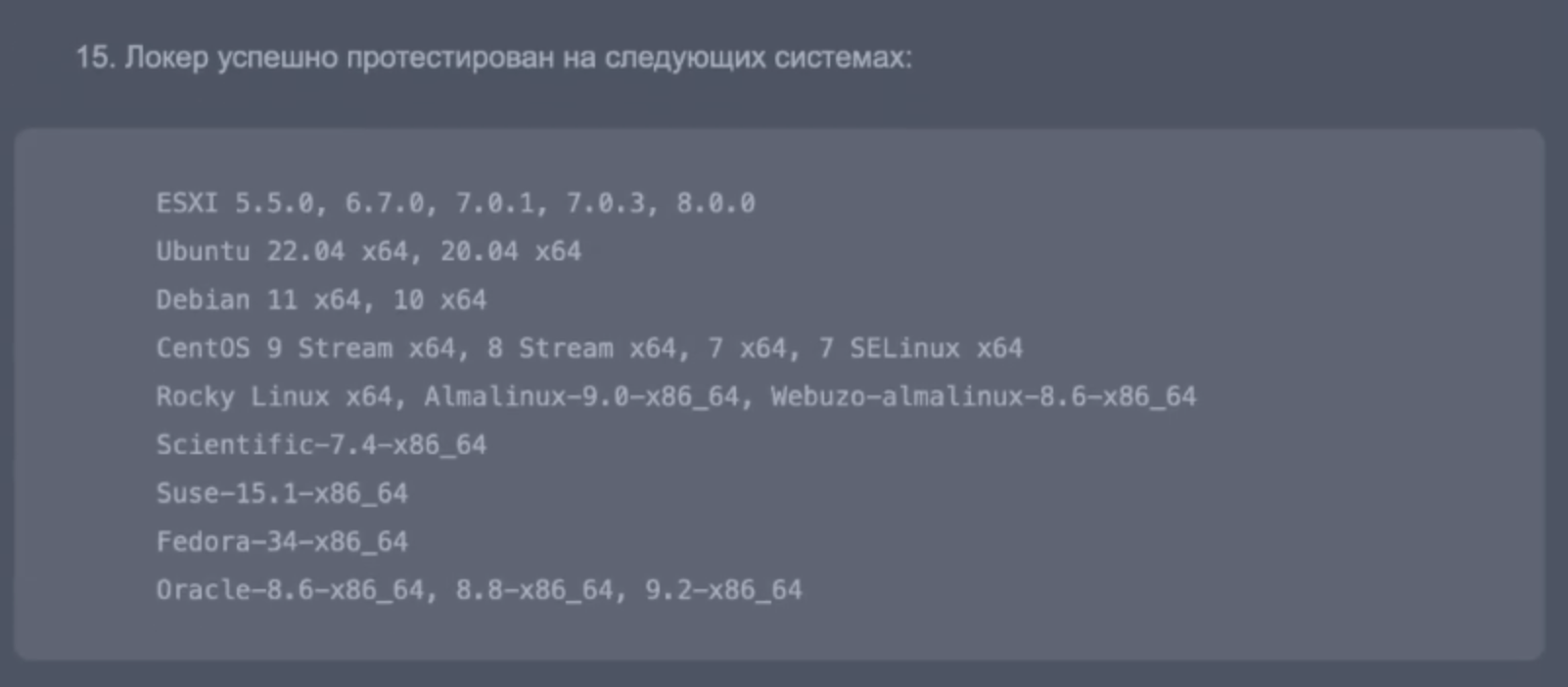
15. The locker has been successfully tested on the following systems:
ESXI 5.5.0, 6.7.0, 7.0.1, 7.0.3, 8.0.0
Ubuntu 22.04 x64, 20.04 x64
Debian 11 x64, 10 x64
CentOS 9 Stream x64, 8 Stream x64, 7 x64, 7 SELinux x64
Rocky Linux x64, Almalinux-9.0-x86_64, Webuzo-almalinux-8.6-x86_64
Scientific-7.4-x86_64
Suse-15.1-x86_64
Fedora-34-x86_64
Oracle-8.6-x86_64, 8.8-x86_64, 9.2-x86_64
The following is a translation of the content on how to create and configure victims in the “Companies” within the “FAQ” section, from Russian to English:
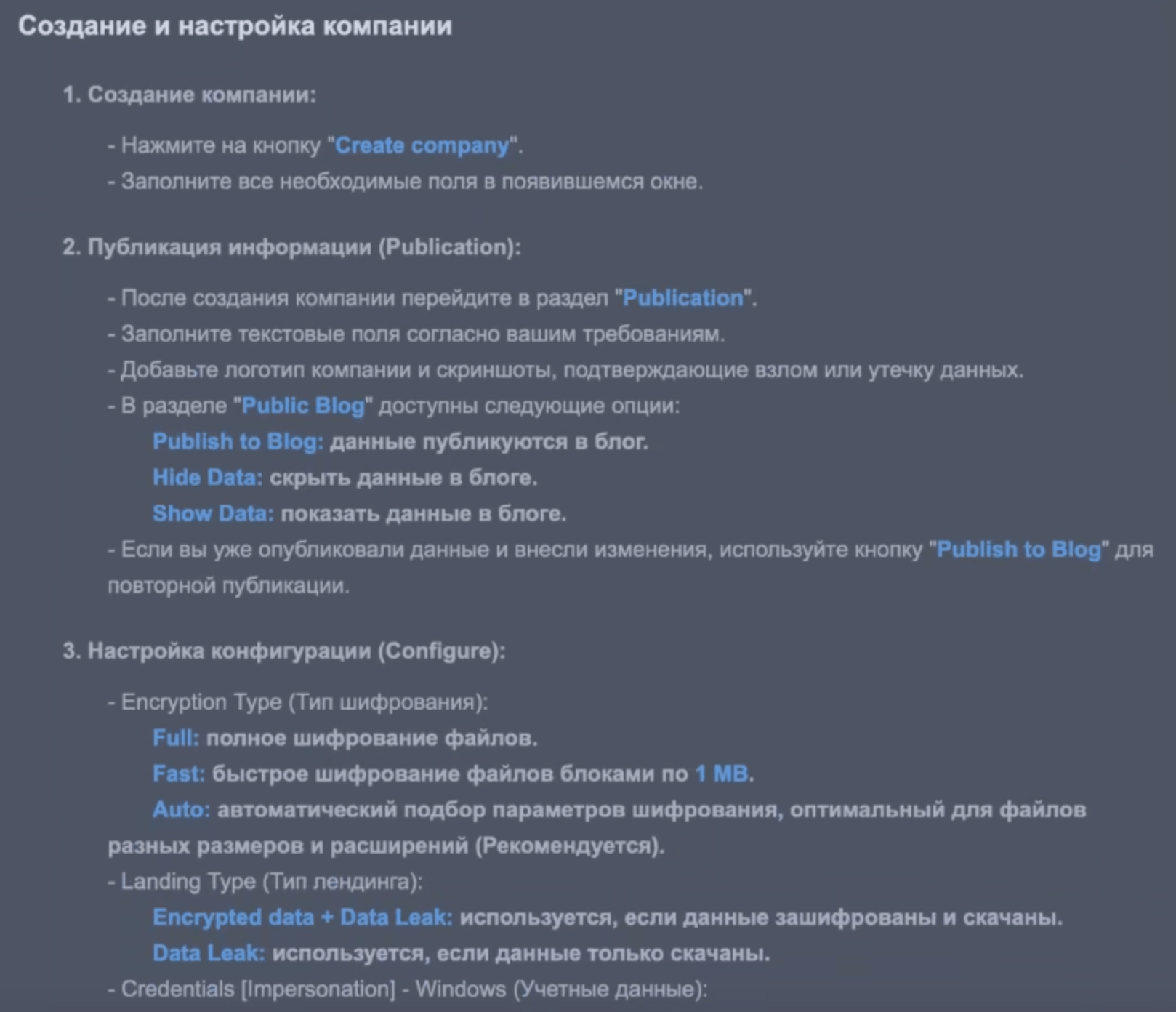
Creating and setting up a company
1. Company creation:
– Click on the “Create company” button.
– Fill in all the required fields in the window that appears.
2. Publication of information:
– After creating a company, go to the “Publication” section.
– Fill in the text fields according to your requirements.
– Add a company logo and screenshots confirming a hack or data leak.
– The following options are available in the “Public Blog” section:
Publish to Blog: The data is published to the blog.
Hide Data: Hide data on the blog.
Show Data: Show data in the blog.
– If you have already published data and made changes, use the “Publish to Blog” button to republish.
3. Configure:
– Encryption Type:
Full: Full file encryption.
Fast: fast file encryption in 1 MB blocks.
Auto: automatic selection of encryption parameters, optimal for files of different sizes and extensions (Recommended).
– Landing Type:
Encrypted data + Data Leak: used if the data is encrypted and downloaded.
Data Leak: used if the data has just been downloaded.
– Credentials [Impersonation] – Windows:
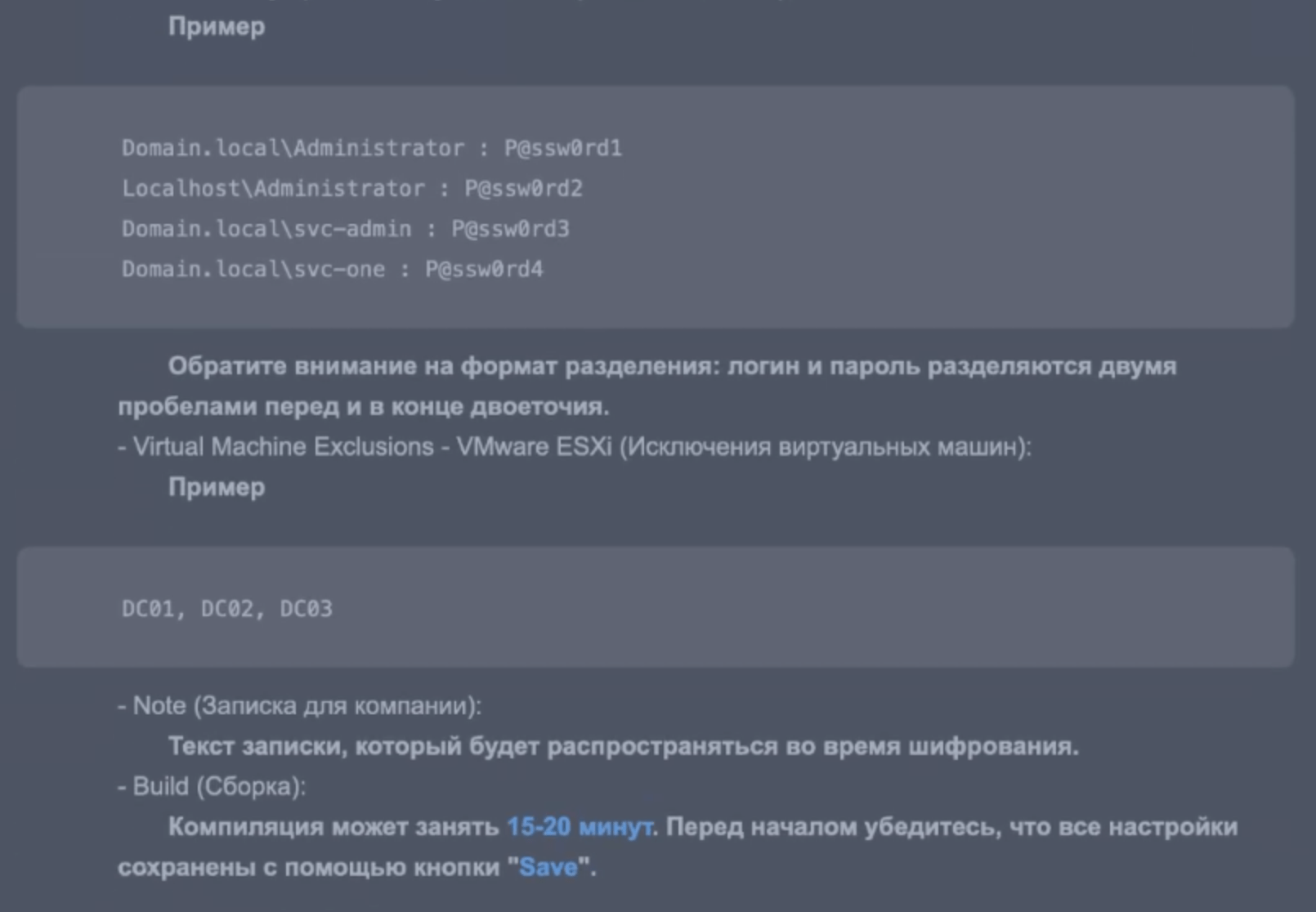
Example
Domain.local\Administrator : P@ssw0rd1
Localhost\Administrator : P@ssw0rd2
Domain.local\svc-admin : P@ssw0rd3
Domain.local\svc-one : P@ssw0rd4
Please note the separation format: the login and password are separated by two spaces before and at the end of the colon.
– Virtual Machine Exclusions – VMware ESXi (Virtual Machine Exclusions):
Example
DC01, DC02, DC03
– Note (Note for the company):
The text of the note that will be distributed during encryption.
– Build:
Compilation may take 15-20 minutes. Before you begin, make sure that all settings are saved using the “Save” button.
The following is a translation of the content on how to execute the Cicada3301 ransomware samples within the “FAQ” section, from Russian to English:
Working with a locker
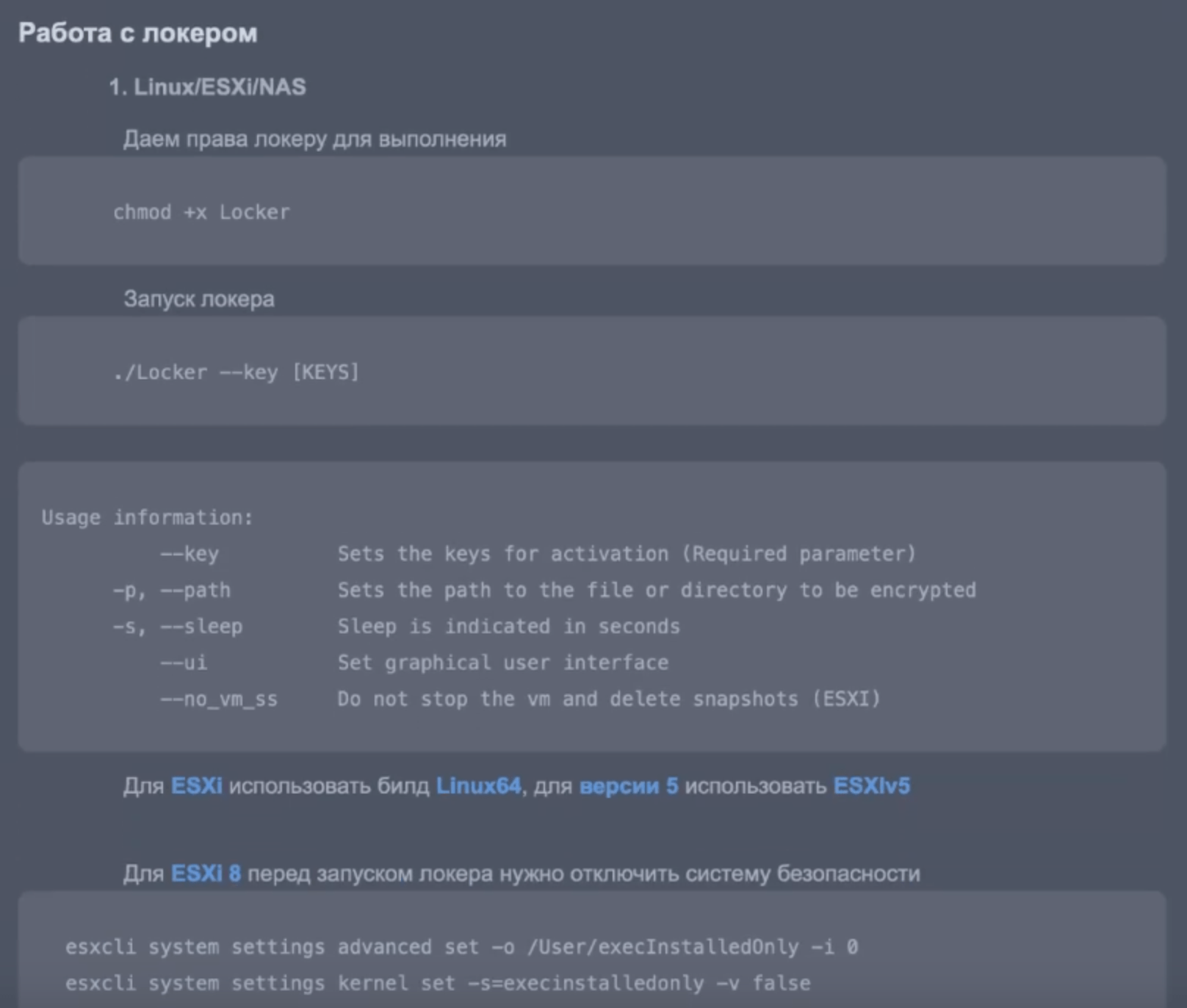
1. Linux/ESXi/NAS
We give permissions to the locker to execute
chmod +x Locker
Launching the locker
./Locker –key [KEYS]
Usage information:
–key Sets the keys for activation (Required parameter)
-p, –path Sets the path to the file or directory to be encrypted
-s, –sleep Sleep is indicated in seconds
–ui Set graphical user interface
–no_vm_ss Do not stop the vm and delete snapshots (ESXI)
For ESXi use the Linux64 build, for version 5 use ESXIv5
For ESXi 8, you need to disable the security system before starting the locker
esxcli system settings advanced set -o /User/execInstalledOnly -i 0
esxcli system settings kernel set -s=execinstalledonly -v false
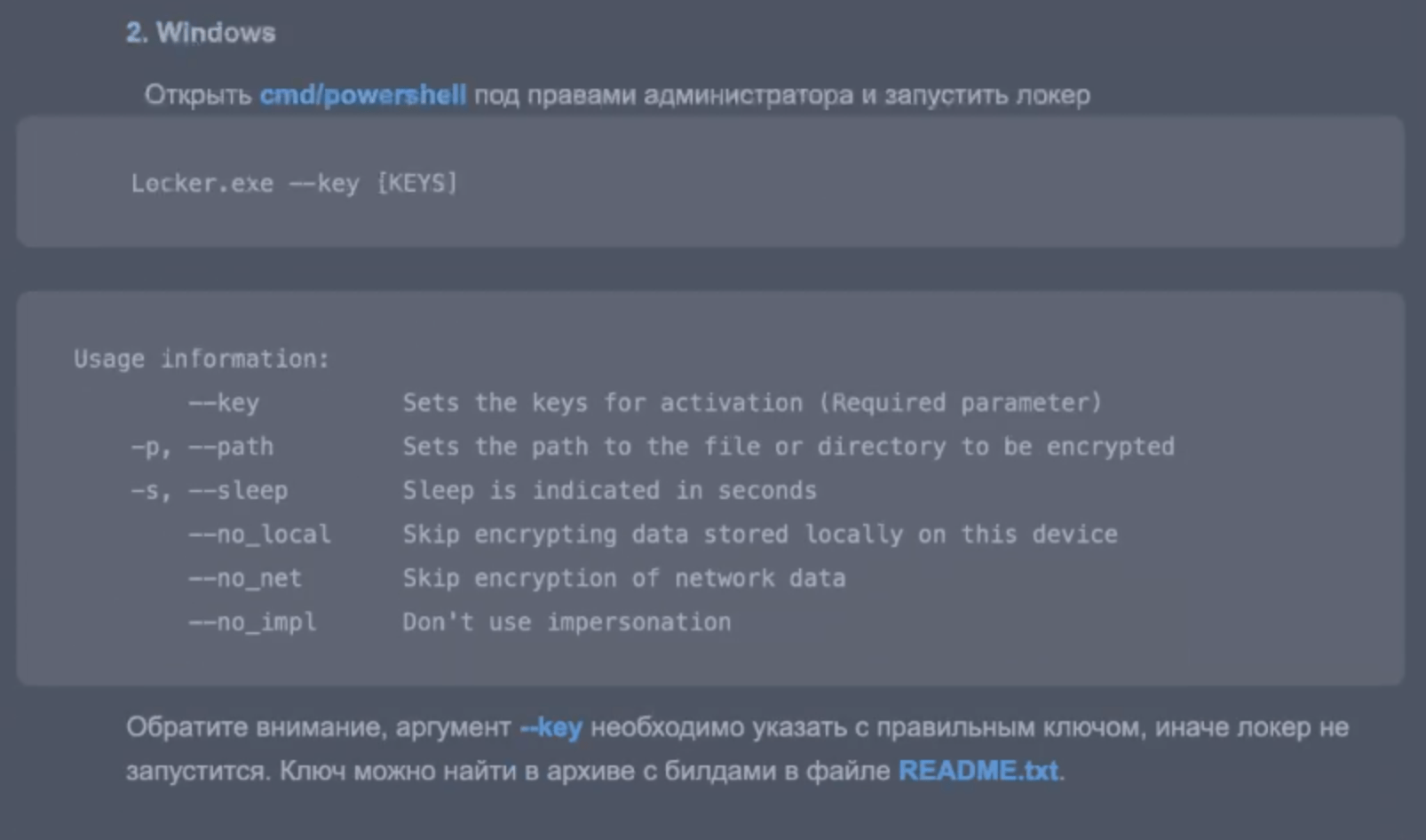
2.Windows
Open cmd/powershell as administrator and run locker
Locker.exe –key [KEYS]
Usage information:
–key Sets the keys for activation (Required parameter)
-p, –path Sets the path to the file or directory to be encrypted
-s, –sleep Sleep is indicated in seconds
–no_local Skip encrypting data stored locally on this device
–no_net Skip encryption of network data
–no_impl Don’t use impersonation
Please note that the –key argument must be specified with the correct key, otherwise the locker will not start. The key can be found in the build archive in the README.txt file.
Technical Information
The Cicada3301 ransomware is written in Rust which supports architectures such as x86, ARM and PowerPC, and can be easily compiled for Windows, macOS, and Linux.
Ransomware developers favor Rust for its ability to compile across platforms, making it easier to target various operating systems. Its high performance and efficiency enable quick execution of malicious operations. Additionally, robust support for concurrent programming allows multiple tasks to run simultaneously, enhancing overall effectiveness. Cicada3301 are not the only ones who prefer Rust – Hive, RansomExx, ALPHV, Qilin (Agenda), and Luna have also been observed adopting this programming language.
Interestingly, the Cicada3301 ransomware shares very strong similarities with the retired and infamous ransomware, BlackCat. The only key differences between Cicada3301 and BlackCat are:
- Only 6 command line options, considerably lesser when compared to BlackCat.
- Initial activation key must be correct else the encryptor won’t start. This key is used to decrypt the ransom message.
- No embedded configuration.
- The Ransom note has the naming convention of RECOVER-[encrypted_extension]-DATA.txt, whereas Blackcat’s note uses the convention RECOVER-[encrypted_extension]-FILES.txt.
Ransom Note
In contrast, where the access key is used to decrypt BlackCat’s configuration, the key entered on the command line in Cicada3301 is used to decrypt the ransom note. After decryption, it will check if the decrypted content starts with `***ok***`. The ransom note is dropped in each directory with filename “RECOVER-[encrypted_extension]-DATA.txt”.
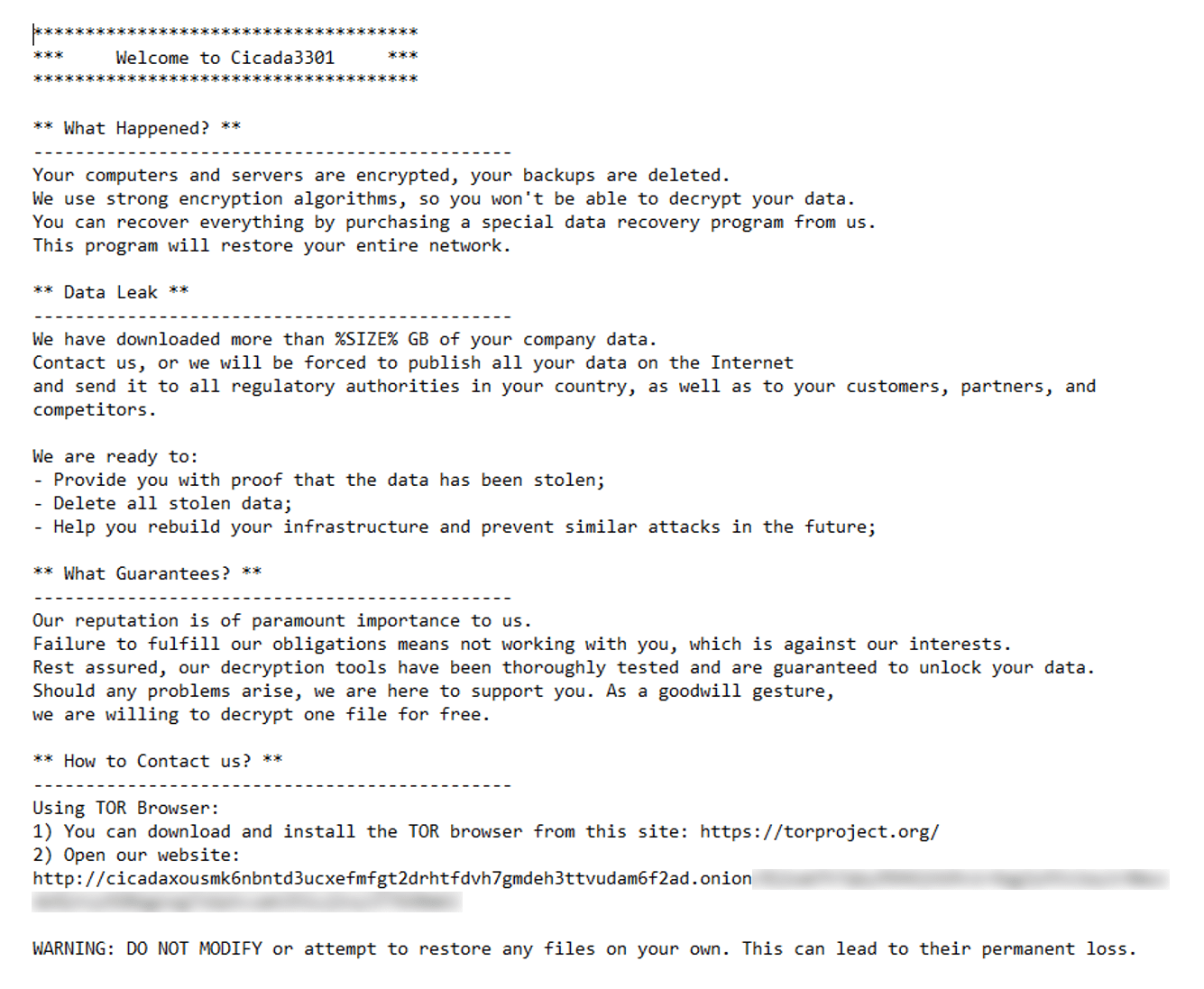
Figure 18: A screenshot of a Cicada3301 Ransom note
Encryption Scheme
The Cicada3301 ransomware utilizes a thread pool consisting of 50 threads to efficiently encrypt files. By employing multiple threads, it can simultaneously process numerous files, significantly speeding up the encryption process. It enumerates drives from A:\ to Z:\ and proceeds to encrypt files found in valid drives, excluding the whitelisted paths and extensions found in Annex A.
The encryption process is straightforward. It randomly generates a 32-byte Chacha key and 12-byte nonce to encrypt the file. These values are then encrypted using a hard-coded RSA public key, and the result is appended to the file.
From the guide, the encryption can be configured using Full, Fast or Auto during the build. The sample that we obtained during our investigation is configured for Auto, which automatically selects the encryption parameters, and is optimized for files of different sizes and extensions. Files can be categorized into three categories:
- Files that are less than 100MB will be fully encrypted.
- For files greater than 100MB, the ransomware encrypts files in chunks, processing every 1 MB for a total of 30 blocks. This means it will first encrypt 1MB and skip N bytes (filesize / 30) and so on.
- For files that are greater than 100MB and have the following extensions, only the first 200MB is encrypted. At this point in our investigation, we are not sure if it was meant to be this way or this could be a bug, and can only confirm this for the sample that we have.
sql, doc, rtf, xls, jpg, jpeg, png, gif, webp, tiff, psd, raw, bmp, pdf ,docx, docm, dotx, dotm, odt, xlsx, xlsm, xltx, xltm, xlsb, xlam, ods, pptx, pptm, ptox, potm, ppsx, ppsm, odt, odp, mdf, txt
Environment Preparation
Inhibit System Recovery
The Cicada3301 ransomware runs the following commands to disable the automatic launch of Windows Recovery Environment after a failed boot, delete shadow copies, and clear Windows Event Logs.
bcdedit /set {default}
bcdedit /set {default} recoveryenabled No
vssadmin.exe Delete Shadows /all /quiet
wmic.exe Shadowcopy Delete
for /F 'tokens=*' %1 in ('wevtutil.exe el') DO wevtutil.exe cl %1
Kill processes and terminate services
It uses the below 3 commands to terminate processes and services. The list of terminated items can be found in Annex B.
C:\Windows\System32\taskkill.exe /IM [processname]* /F
for /F "tokens=2 delims=:" %i in ('sc query state^= all ^| findstr /I [servicename]') do sc stop %i
net stop [servicename] /y
Others
// Discover and stop local Virtual Machines
powershell -Command "Get-VM | Where-Object { $_.Name -notin @() } | ForEach-Object { Stop-VM -Name $_.Name -Force -Confirm:$false }"
// Follows symbolic links
fsutil behavior set SymlinkEvaluation R2L:1
fsutil behavior set SymlinkEvaluation R2R:1
// Increase the number of outstanding network requests allowed
reg add HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services \LanmanServer\Parameters /v MaxMpxCt /d 65535 /t REG_DWORD /f
// Stop the Internet Information service (IIS)
iisreset.exe /stop
PSExec
PsExec binary is embedded inside the Cicada3301 ransomware itself. When the locker runs without the “no_impl” option, it copies itself to C:\Users\Public, drops a PsExec binary at C:\Users\Public\psexec0.exe and a batch file at C:\Users\Public\[rand_10chars].bat. It then launches the batch file which will then re-execute the locker.
Contents of C:\Users\Public\[rand_10chars].bat:
C:\Users\Public\psexec0.exe -accepteula -s -d [locker filepath] --no_impl --key [key] del /Q "C:\Users\Public\[rand_10chars].bat"
PsExec is a command-line tool that allows users to run programs on remote systems. While the sample that we obtained does not contain embedded credentials, we presume that if credentials were used during the building process, the PsExec will be executed with credentials.
Linux and ESXi variant
There are two notable and additional differences between the Linux and Windows variants:
--ui Set graphical user interface --no_vm_ss Do not stop the vm and delete snapshots (ESXI)
When executed with the –ui option, logs akin to the below will be printed.
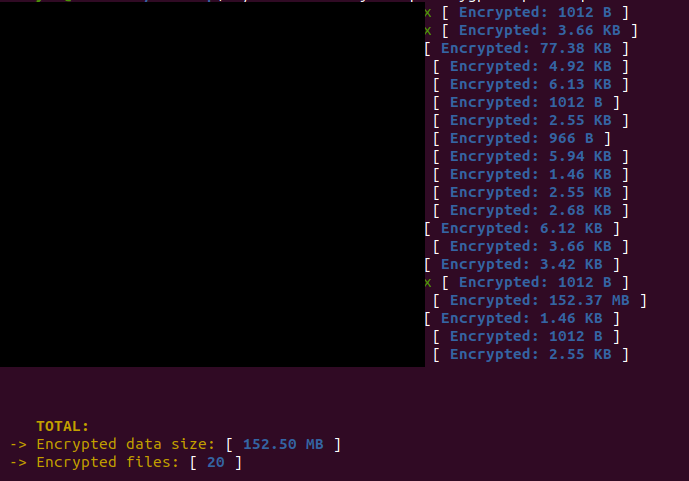
Figure 19: Console logs with –ui option.
For Linux variants, it avoids encrypting files that reside within these directories, or have the following extensions:
// whitelisted directories /etc, /run, /usr, /sys, /dev, /bin, /lib, /boot, /snap, /proc, /sbin, /lib64, /cdrom // whitelisted extensions lock, tmp
For ESXi variants, the Cicada3301 ransomware will first shutdown the running virtual machines, before encryption starts with the following 2 commands used simultaneously. It terminates all the virtual machines and then deletes all snapshots. Cicada3301 does this via this single line command detailed below. However, one can choose not to shutdown the virtual machines via the “no_vm_ss” option.
esxcli --formatter=csv --format-param=fields=="WorldID,DisplayName" vm process list | grep -viE ",()," | awk -F "\"*,\"*" '{system("esxcli vm process kill --type=force --world-id="$1)}' > /dev/null 2>&1;
for i in `vim-cmd vmsvc/getallvms| awk \'{print$1}\’`;do vim-cmd vmsvc/snapshot.removeall $i & done > /dev/null 2>&1
PowerPC
The Cicada3301 ransomware also supports the PowerPC architecture. PowerPC is a type of microprocessor architecture that was developed by the AIM—an alliance between Apple, IBM, and Motorola in the early 1990s. It was designed to be a high-performance, Reduced Instruction Set Computing (RISC) architecture. PowerPC processors are not commonly found in recent mainstream personal computers, but they are still used in older Macs or specific legacy systems.
Conclusion
The Cicada3301 ransomware group has rapidly established itself as a significant threat in the ransomware landscape, due to its sophisticated operations and advanced tooling. The group’s ransomware, written in Rust, supports a wide range of platforms, including Windows, Linux, ESXi, NAS, and even uncommon architectures like PowerPC. By leveraging ChaCha20 + RSA encryption and offering a customizable affiliate panel, Cicada3301 enables its affiliates to execute highly targeted attacks. Their approach of exfiltrating data before encryption adds an additional layer of pressure on victims, while the ability to halt virtual machines increases the impact of their attacks.
Their operations are marked by aggressive tactics designed to maximize impact, such as terminating essential services, shutting down virtual machines, and encrypting data across various platforms and network shares. The use of a sophisticated affiliate program amplifies their reach, enabling skilled cybercriminals to customize attacks and manage victims efficiently through a feature-rich web interface.
The emergence of Cicada3301 underscores the evolving threats organizations face from ransomware groups that are increasingly professional, resourceful, and bold. It highlights the urgent need for organizations to bolster their cybersecurity measures, engage in proactive threat intelligence, and adopt a multi-layered defense strategy to protect against such advanced adversaries.
Recommendations
Although ransomware groups have gained notoriety for targeting companies in critical sectors, they are a threat to organizations across all industries and companies large and small. In addition to having new members in its cybercriminal network, ransomware affiliate programs equip members with upgraded tools and techniques. That being said, it is essential that businesses take specific steps immediately to keep their mission-critical operations and data secure. We recommend the following:
- Add more layers of security: Multi-factor authentication (MFA) and credential-based access solutions help businesses secure their critical assets and high-risk users, making it harder for attackers to be successful.
- Stop ransomware with early detection: Leverage the behavioral detection capabilities of the Endpoint Detection and Response (EDR) solution to help identify ransomware indicators across your managed endpoints, promptly alerting your teams to any suspicious activity for further scrutiny. This proactive approach enables agile detection, investigation and remediation of both known and unknown threats on your endpoints.
- Have a backup strategy: Data backup processes should be conducted regularly as they reduce damage and help organizations avoid data loss following ransomware attacks.
- Leverage an advanced malware detonation solution: Organizations should leverage AI-infused, advanced analytics-based solutions to detect intrusions in real time. Learn how Group-IB’s Managed XDR coupled with Threat Intelligence helps businesses to:
- gain insights into the unique Tactics, Techniques, and Procedures (TTPs) used by Advanced Persistent Threats (APTs) and other cybercriminal groups and pivot their security strategies accordingly; and
- enable multi-layered cybersecurity (endpoint, email, web, and network) through automated threat detection and response.
- Patch it up: The longer a vulnerability remains unpatched, the greater the risk that it will be exploited by cybercriminals. Security patches should therefore be prioritized, and organizations should also set up a process to regularly review and apply patches as they become available.
- Train your employees: The human factor remains one of the greatest vulnerabilities in cybersecurity. Educate employees about the risks relating to the organization’s network, assets, devices, and infrastructure. Organizations should conduct training programs and security drills to help employees identify and report the tell-tale signs of cybercrime (e.g. phishing emails).
- Control vulnerabilities: Do not turn a blind eye to emerging vulnerabilities. Checking your infrastructure annually with a technical audit or security assessment is not only a good habit, it also adds a much-needed layer of protection. Infrastructural integrity and digital hygiene processes should be monitored continually.
- For businesses seeking to enhance their cybersecurity stance and boost resilience against ransomware attacks, we strongly recommend reviewing our Ransomware Readiness whitepaper.
MITRE ATT&CK
| T1059.001 Command and Scripting Interpreter: PowerShell | Use of PowerShell for executing malicious commands and scripts to control infected systems. |
| T1070.004 Indicator Removal on Host: File Deletion | Deleting logs or files to erase evidence of compromise and hinder forensic analysis. |
| T1046 Network Service Scanning | Scanning internal and external networks to identify services, systems, and shares for exploitation. |
| T1016 System Network Configuration Discovery | Gathering details about network configurations, such as IP addresses, routing tables, and ARP tables. |
| T1570 Lateral Tool Transfer | Using tools such as PsExec to move files or execute code on remote machines for lateral movement. |
| T1486 Data Encrypted for Impact | Encrypting files on a victim’s system to disrupt availability and demand ransom for decryption. |
| T1490 Inhibit System Recovery | Deleting system restore points, shadow copies, or backups to prevent recovery after the attack. |
| T1489 Service Stop | Stopping critical services, including security, backup, and virtualization services, to disrupt normal system functions. |
Public Available Indicators of Compromise (IOCs)
|
Filename |
SHA256 |
| C:\Users\Public\psexec0.exe | 078163d5c16f64caa5a14784323fd51451b8c831c73396b967b4e35e6879937b |
| csrss.exe | 7b3022437b637c44f42741a92c7f7ed251845fd02dda642c0a47fde179bd984e |
| veeam.exe | 3969e1a88a063155a6f61b0ca1ac33114c1a39151f3c7dd019084abd30553eab |
| system32.exe | 56e1d092c07322d9dad7d85d773953573cc3294b9e428b3bbbaf935ca4d2f7e7 |
Network Indicators
hxxp[:]//cicadabv7vicyvgz5khl7v2x5yygcgow7ryy6yppwmxii4eoobdaztqd[.]onion/
Annex A
Terminated Processes
agntsvc, dbeng50, dbsnmp, encsvc, excel, firefox, infopath, isqlplussvc, msaccess, mspub, mydesktopq, mydesktopservic, notepad, ocautoupds, ocomm, ocssd, onenote, oracle, outlook, powerpnt, sqbcoreservic, sql, steam, synctime, tbirdconfig, thebat, thunderbird, visio, winword, wordpad, xfssvccon, *sql*, bedbh, vxmon, benetns, bengien, pvlsvr, beserver, raw_agent_svc, vsnapvss, CagService, QBIDPService, QBDBMgrN, QBCFMonitorSe, SAP, TeamViewer_Service, TeamViewer, tv_w32, tv_x64, CVMountd, cvd, cvfwd, CVODS, saphostexe, saposcol, sapstartsrv, avagent, avscc, DellSystem, EnterpriseClient, VeeamNFSSvc, VeeamTransportSvc, VeeamDeploymentSvc
Terminated Services via sc stop
mepocs, memtas, veeam, svc$, backup, sql, vssmsexchange, sql$, mysql, mysql$, sophos, MSExchange, MSExchange$WSBExchange, PDVFSService, BackupExecVSSProvider, BackupExecAgentAccelerator, BackupExecAgentBrowser, BackupExecDiveciMediaService, BackupExecJobEngine, BackupExecManagerService, BackupExecRPCService, GxBlr, GxVss, GxCIMgr, GxCIMgrS, GxCVD, GXMMM, GxVssHWProv, GxFWD, SAPService, SAP, SAP$, SAPD$, SAPHostControl, SAPHostExec, QBCFMonitorService, QBDBMgrN, QBIDPService, AcronisAgent, VeeamNFSSvc, VeeamDeploymentService, VeeamTransportSvc, MVArmorMVarmor64, VSNAPVSS, AcrSch2Svc, DefWatchccEvtMgr, ccSetMgr, SavRoam, RTVscan, QBFCService, Intuit.QuickBooks.FCS, zhudongfangyu, stc_raw_agent, BackupExecManagementService, CASAD2DWebSvc, CAARCUpdateSv
Terminated Services via net stop
WSearchnet, MSExchangeIS, MSExchangeSA, MSExchangeADTopology, wuauserv, eventlog, MSSQLSERVER, SQLSERVERAGENT, SQLBrowser, MSSQLServerOLAPService, ReportServer, MsDtsServer, SQLWriter
Annex B
Whitelisted extensions, paths
*.exe
*.EXE
*.DLL
*.ini
*.inf
*.pol
*.cmd
*.ps1
*.vbs
*.bat
*.pagefile.sys
*.hiberfil.sys
*.drv
*.msc
*.dll
*.lock
*.sys
*.msu
*.lnk
*.search-ms
*\$Windows.~WS*
*\$windows.~ws*
*\$WINDOWS.~WS*
*\$windows.~bt*
*\$Windows.~BT*
*\$WINDOWS.~BT*
*\Windows.old*
*\NTUSER.DAT*
*\ntuser.dat*
*\autorun.inf
*\boot.ini
*\desktop.ini
*\system volume information*
*\Boot*
*\DumpStack.log.tmp
*\PerfLogs*
*\Users\*\Microsoft_Corporation\*.config
*\AppData\Local\Microsoft\GameDVR*
*\AppData\Local\Packages\Microsoft.*
*\AppData\Local\Packages\MicrosoftWindows.*
*\AppData\Local\Packages\Internet Explorer*
*\AppData\Local\Temp*
*\Program Files\Common Files\microsoft shared*
*\Program Files\Common Files\Services*
*\Program Files\Common Files\System*
*\Program Files\Internet Explorer*
*\Program Files\ModifiableWindowsApps*
*\Program Files\Uninstall Information*
*\Program Files\Windows Defender*
*\Program Files\Windows Mail*
*\Program Files\Windows Media Player*
*\Program Files\Windows NT*
*\Program Files\Windows Photo Viewer*
*\Program Files\Windows Portable Devices*
*\Program Files\Windows Security*
*\Program Files\Windows Sidebar*
*\Program Files\WindowsApps*
*\Program Files\WindowsPowerShell*
*\Program Files (x86)\Common Files*
*\Program Files (x86)\Common Files\Microsoft Shared*
*\Program Files (x86)\Common Files\Services*
*\Program Files (x86)\Common Files\System*
*\Program Files (x86)\Internet Explorer*
*\Program Files (x86)\Microsoft\*Edge*
*\Program Files (x86)\Microsoft\Temp*
*\Program Files (x86)\Microsoft.NET*
*\Program Files (x86)\Windows Defender*
*\Program Files (x86)\Windows Mail*
*\Program Files (x86)\Windows Media Player*
*\Program Files (x86)\Windows Multimedia Platform*
*\Program Files (x86)\Windows NT*
*\Program Files (x86)\Windows Photo Viewer*
*\Program Files (x86)\Windows Portable Devices*
*\Program Files (x86)\Windows Security*
*\Program Files (x86)\Windows Sidebar*
*\Program Files (x86)\WindowsPowerShell*
*\ProgramData\ssh
*\ProgramData\ntuser.pol
*\ProgramData\regid.*.com.microsoft
*\ProgramData\USOPrivate*
*\ProgramData\USOShared*
*\ProgramData\Microsoft\UEV*
*\ProgramData\Microsoft\Device Stage*
*\ProgramData\Microsoft\DeviceSync*
*\ProgramData\Microsoft\Diagnosis*
*\ProgramData\Microsoft\DiagnosticLogCSP*
*\ProgramData\Microsoft\DRM*
*\ProgramData\Microsoft\EdgeUpdate*
*\ProgramData\Microsoft\Event Viewer*
*\ProgramData\Microsoft\IdentityCRL
*\ProgramData\Microsoft\MapData*
*\ProgramData\Microsoft\MF*
*\ProgramData\Microsoft\NetFramework*
*\ProgramData\Microsoft\Network*
*\ProgramData\Microsoft\Provisioning*
*\ProgramData\Microsoft\Search*
*\ProgramData\Microsoft\SmsRouter*
*\ProgramData\Microsoft\Spectrum*
*\ProgramData\Microsoft\Speech_OneCore*
*\ProgramData\Microsoft\Storage Health*
*\ProgramData\Microsoft\User Account Pictures*
*\ProgramData\Microsoft\Vault*
*\ProgramData\Microsoft\WDF*
*\ProgramData\Microsoft\Windows*
*\ProgramData\Microsoft\Windows Defender*
*\ProgramData\Microsoft\Windows NT*
*\ProgramData\Microsoft\Windows Security Health*
*\ProgramData\Microsoft\WinMSIPC*
*\ProgramData\Microsoft\WPD*
*\ProgramData\Microsoft\Crypto\RSA\MachineKeys\*
*\ProgramData\Microsoft\ServerManager\Events\FileServer.Events.xml
*\ProgramData\Packages\USOPrivate*
*\ProgramData\Packages\WindowsHolographicDevices*
*\ProgramData\Packages\USOShared*
*\ProgramData\Packages\MicrosoftWindows.*
*\ProgramData\Packages\Microsoft.*
*\Windows\*
*\All Users\Microsoft\*
*\AppData\Local\*
Supercharge cybersecurity
Defeat threats efficiently and identify attackers proactively with a revolutionary cyber threat intelligence platform by Group-IB