Introduction
Zero trust had taken over discussions long before buzzwords like AI and ML dominated cybersecurity. While it is often seen as a specific approach to security architectures, software frameworks, and communication models, zero trust security has never been more relevant—especially after COVID (and ever since globalization) changed how businesses operate.
How? Some wise cybersecurity men raised important questions:
“Data is everywhere, but do you know everywhere your data is?”
Even if you do, who is accessing your data? As businesses, we’ve gone perimeter-less, serverless, and—consequently—security-less. Companies are now remote, relying on extended zero trust network access connectivity, password policies, firewalls, VPNs, and cloud-native architectures to manage operations. They are often based on intangible (an unmeasurable) trust, which attackers have become skilled at exploiting. Assigning an identity, device, and behavior to every request (context), interaction, packet, and activity within the perimeter is necessary.
So what is the alternative? “Zero trust Security “
As the name suggests, zero trust is a system where every person, device, application, or file is considered a threat unless properly verified. In other words, zero trust equates to “always assuming breach,” where
- Authorization may be granted only after verification
- Least-privileged model and limited access on a need-to-know basis are followed
- All traffic must be continuously inspected and logged to verify user behavior.
By 2025, 60% of companies will use Zero Trust solutions instead of virtual private networks. That’s the prediction from last year’s “Zero Trust Architecture and Solutions” report by Gartner. This year, we’ll see even more significant growth in adopting Zero Trust solutions.
Zero trust security is the need of the hour, but it isn’t for you if…
Organizations operating on legacy systems and server-based infrastructure that is not updated (unpatched) are mostly on-prem; they may not be ready for zero trust, as it’s a more complex, modern approach. Zero trust requires a more agile, cloud-first mindset and high system flexibility.
Also, zero-trust (ZT) isn’t for you if you solely focus on technology to upgrade your cybersecurity, not the people, business, and process aspects. Zero trust security is not a ready-made framework but a constant process you need to build, manage, and upkeep. The benefit for any organization is that the implementation depends on factors like stakeholder adoption, business size, industry, infrastructure, and risk tolerance.
Before adopting zero-trust architecture, organizations must define their attack surface and key components of the attack surface where Zero Trust (ZT) security principles should be applied, such as:
- Publicly Available Assets –Public websites, customer-facing portals, and externally exposed APIs.
- Assets Available to Partners / B2B – Partner portals, supply-chain portals, externally facing APIs restricted to specific partners.
- VPN Users – Employees or contractors accessing on-premise resources remotely via a VPN connection or terminal/VDI access.
- Internal Enterprise Assets – On-premise applications, databases, file servers, IoT devices, workstations, VMs, containerized and serverless environments, and hypervisors.
- Cloud Assets – Workloads running on AWS, Azure, GCP, SaaS applications, container platforms, and serverless functions.
- BYOD (Bring Your Own Device) – Workstations, mobile phones, and other personal devices used for work.
Organizations should assess changes and future scale-up requirements for ZT and determine how to leverage existing infrastructure. Rather than blindly picking vendor solutions, they should first clarify desired outcomes.
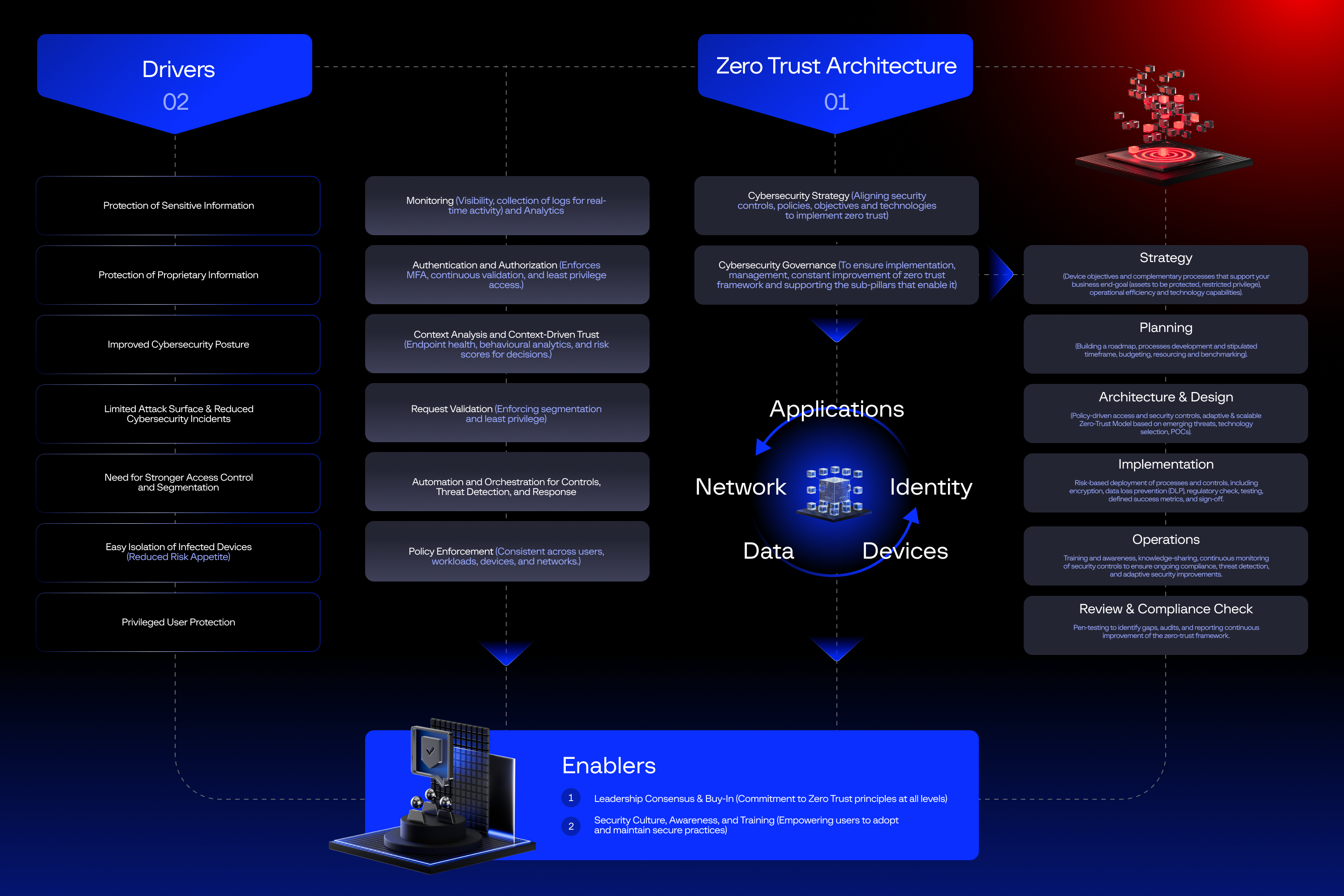
Zero trust architecture is the strategic placement of multiple security controls, protocols, and processes that are followed systemically to strengthen security. An organization needs to build an entire ecosystem, keeping in mind the pillars and their equally important enablers, such as visibility and monitoring, enforcement, and adopting zero trust (ZT) security practices in your culture with regular awareness and training, to provide a risk-based approach to cybersecurity.
Image 1: Key considerations for building a zero-trust ( ZT) framework
Zero-trust security and least privilege – are they the same thing?
Being online, as a user/identity/account, the experience is continuously designed to be as easy to navigate and frictionless as possible. A key part of that design is authenticity verification. To cut through the clutter, a form of “trust” is typically assigned to a user based on their profile status, historical activity, and authorization regarding access to company data. Zero Trust security challenges this trust-based approach by requiring constant verification, limiting access, enforcing strict permission requirements, and monitoring all connections, assuming compromise is always possible.
On the other hand, the least privilege can be incorporated under the security ideology of zero trust security, but it mainly deals with giving the least access to a particular user to perform a specific assigned task. It primarily concerns access control and does not incorporate zero trust tenets such as micro-segmentation, monitoring, and continuous verification.
This translates into giving a customer support representative access to the performance dashboard, not the company’s core strategies or financial reports.
A Practical use-case where zero trust averts threats
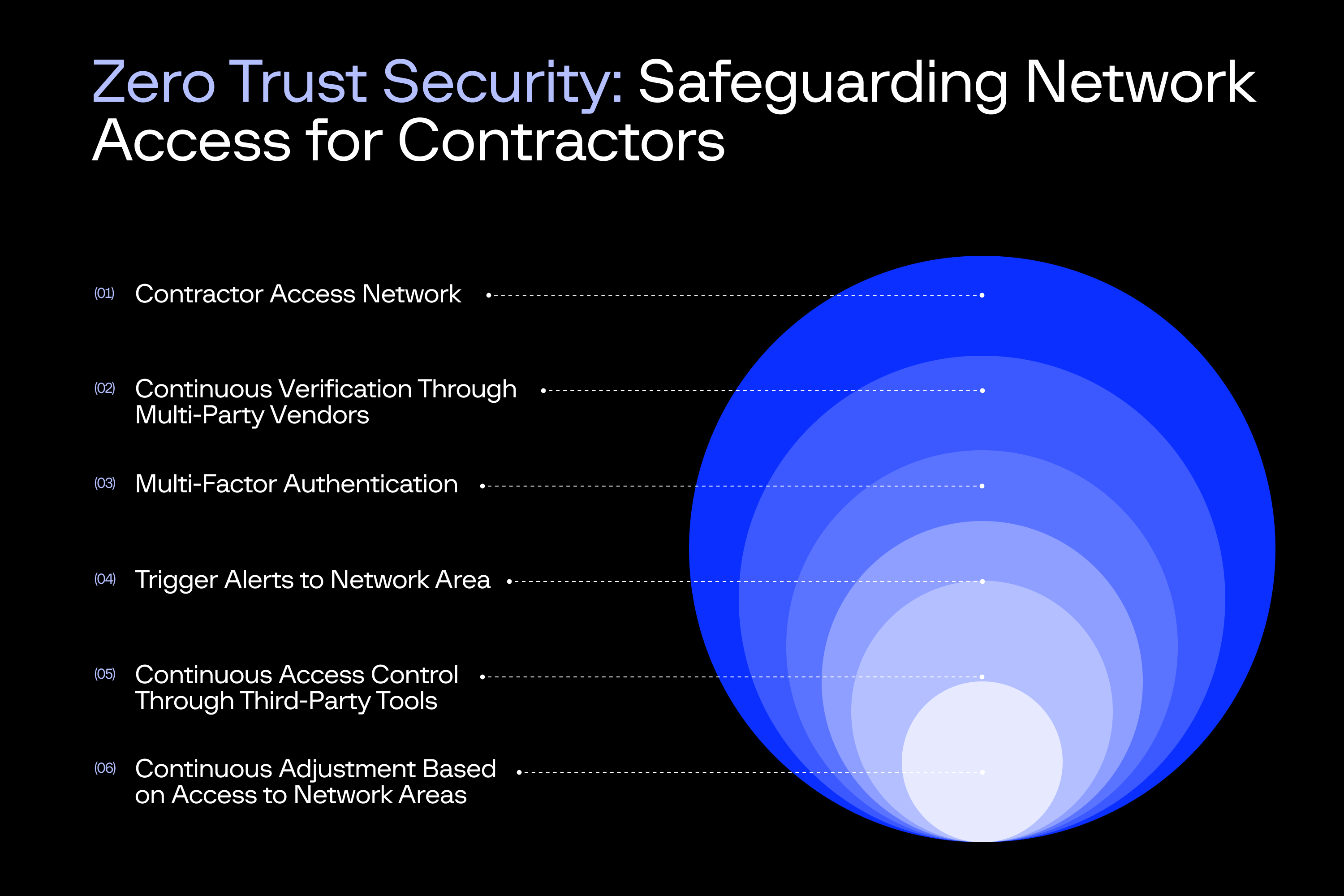
Contractors, third-party, or guests using the network infrastructure
Scenario: A company allows third-party contractors to access its internal network to collaborate on a project. Traditionally, once authenticated, contractors might have access to a wide range of resources based on their credentials, such as shared drives, financial data, or even confidential business strategies. This can lead to a significant risk if the contractor’s credentials are compromised, intentionally or unintentionally, allowing malicious actors to infiltrate the network and gain unauthorized access.
How Zero Trust Averts Threats: Zero trust security ensures that contractors accessing a network are continuously verified, closely monitored, and given only the minimum necessary access. Rather than assuming trust after the initial authentication, zero trust mandates ongoing verification through multi-factor authentication (MFA) and real-time identity validation.
Granular access control follows the least privilege principle, limiting contractors to only the resources essential for their specific tasks. Micro-segmentation further isolates critical systems, preventing unauthorized lateral movement within the network.
Real-time monitoring and anomaly detection are crucial for identifying suspicious activities—such as unauthorized access attempts—prompting immediate alerts and revoking access when needed. This containment strategy guarantees that even if credentials are compromised, attackers cannot easily navigate the zero trust network or access sensitive data. Third-party access can introduce vulnerabilities, as outside vendors may have less robust security practices. Zero trust mitigates this risk by assuming a breach and treating all vendors as “guilty until proven innocent.” Organizations must perform continuous security assessments and real-time verifications instead of access based on previous access settings or one-time audits.
To effectively implement Zero trust at scale, security teams require a well-organized framework with immediate access to vendor risk assessments, security profiles, and compliance reports.
Image 2: Zero trust security checks for third-party access
To understand how implementing a zero trust architecture can work for you—based on specific use cases, your company’s growth ambitions, attack surface, or function management—reach out to our Group-IB experts to identify and define your most critical assets, build your data sources, and contextualize information better for risk and alert management as you progress along the maturity curve. Start building an initial blueprint today.
Taking the Zero Trust Security Journey
“Modern organization’s cybersecurity has no perimeter.”
Building and deploying a zero-trust (ZT) architecture is a gradual process that requires clear requirements, success metrics, and continuous adjustments based on outcomes. While full implementation takes time, organizations can achieve quick wins—such as enhancing monitoring in cloud-native environments—to address immediate security gaps.
However, it is important to note that attaining 100% Zero Trust shouldn’t be a definitive goal for organizations because putting the idea into reality makes it less viable due to the baseline trust required for operations (you can trust less, but can you trust no one?), the constantly changing threat landscape, and the ongoing need to pivot controls and integrations to adapt to evolving work dynamics. However, the goal is to get as close to it as efficiently as possible through strengthening security processes and controls and improving risk-based alerting. However, the idea is to get as close to it as efficiently as possible through strengthening security processes and controls, better risk-based alerting and frameworks, and not trusting anyone accessing your data and systems.
Zero Trust Maturity Levels
Basic: Establish foundational security controls, starting with identity and access management (IAM), multi-factor authentication (MFA), and network segmentation.
Intermediate: Expand zero trust principles by integrating continuous monitoring, micro-segmentation across the network, behavioral analytics to set baseline behavior, and least privilege access across users and devices.
Advanced: Achieve full zero trust maturity by implementing automated threat response, full micro-segmentation, and zero trust across all five pillars—identity, devices, networks, applications, and data.
Zero trust does not require complete infrastructural changes; organizations can leverage and upgrade their existing tools and frameworks to implement zero trust concepts. The key is consistent focus and refinement to evolve security at every stage. The entire zero trust architecture is based on the right data at the right time and context.
🔴 Preparation: Initial discovery and assessment activities.
With Zero Trust
🟡 Basic: Establish foundational security controls (telemetry, least privilege, security and logging, manual response, and deployment) and integrate core capabilities.
🔵 Intermediate: Strengthen access controls, automate security policies, and refine integrations, adjusting to least privilege based on testing.
🟢 Advanced: Deploy adaptive protections, advanced analytics, and orchestration for continuous security, adjusting least privilege based on risk and posture assessments. Build toward enterprise-wide awareness, including externally hosted resources, with self-reporting and dynamic policies based on automated/observed triggers. Ensure interoperability with continuous monitoring and centralized visibility with comprehensive situational awareness.
Essential checks before moving towards Zero Trust
Define and Inventory Your Data and Assets
First, identify your organization’s most critical assets—specifically, what you need to protect and monitor in order of priority. This will be an important data source for IT and security monitoring and the foundation of a comprehensive end-to-end zero trust program.
- Identify Desktop as a Service (DaaS)
- Build data flows
- Inventory identities (users + devices)
- Log network traffic
- Identify privileged accounts
Identify access based on fine-grained user and device attributes (applications, user behavior, historical access, time of access).
Trust no one isn’t cynical; it’s defensive: Log and inspect everything
Trust varies and cannot be a definitive parameter. You don’t grant or deny access based solely on an account’s status, historical behavior, or previous authorizations. Zero trust security is about continuous verification and strict access controls at every level, assuming potential breaches are everywhere and responding accordingly.
While telemetry ingestion and keeping logs of all data have been past practices, monitoring, and logging take center stage in zero trust. Aggregated logs into a central location—such as SOAR—allow deviations in logs, like activity from an unusual device, different geolocation, privilege escalation, or policy changes, to be inspected and altered. Automation smooths the entire process, reducing the time gap between action (deviation) and reaction (applying feedback).
Policy Implementation/ Enforcement
While this is a solid zero trust principle, monitoring should be network-based, user/device-based, and data repository-driven rather than endpoint-based. Endpoint-based monitoring has critical weaknesses, especially regarding advanced threats like rootkits that can compromise the endpoint.
The ideal strategy is to adopt a hybrid approach: network-based detection that focuses on monitoring network traffic (for broader security enforcement) coupled with user/device-based detection to enforce policies at the network, identity, and device levels (for granular enforcement). Network-based monitoring also supports microsegmentation for additional isolation and control within the network.
Real-time UEBA monitoring for risk-based action
Real-time User and Entity Behavior Analytics (UEBA) enables risk-based action by analyzing deviations from expected behavior. Instead of relying solely on static policies, variable trust levels adjust dynamically based on contextual signals like user behavior, device specs, and location.
Avoiding Noise: Smart Prioritization & Automated Responses
Zero Trust security operates on predefined rules, similar to conventional cybersecurity practices, but the key difference is that those rules must continuously evolve. They adapt based on threat intelligence data, automated defenses, and feedback loops. This constant evolution ensures that the system stays up-to-date with emerging threats rather than relying on static rules that may become outdated or ineffective over time.
- Define Behavioral Baselines – Establish clear “normal” behavior patterns for users, devices, and applications.
- Risk Scoring & Thresholds – Assign risk scores based on deviations, preventing excessive alerts from minor anomalies.
- Context-Aware Automation – Trigger actions (like MFA re-authentication or session termination) only when multiple risk factors align.
- Integrate Across Layers – Combine UEBA insights with network telemetry, endpoint activity, and identity signals to refine trust calculations.
- Adaptive Learning – Continuously refine detection models to prevent over-alerting while improving accuracy.
This way, zero trust isn’t just about enforcing rigid rules—it becomes adaptive and intelligent, ensuring security teams focus on genuine threats and not acting on the noise.
Conclusion
Zero Trust security alone can’t always stop fraud, insider threats, or advanced attacks that exploit authorized access (e.g., compromised user credentials). However, it can contain incidents and restrict damage—provided the right anomalies are detected quickly. If we monitor the wrong signals, these threats might slip through.
The first step is to assess a company’s current state and identify weak points and threats that exploit trust relationships. This is where cybersecurity consulting comes in. Cybersecurity auditing and consulting services can help companies evaluate their infrastructures and processes, understand their current security risks, and identify how to mitigate them.
Experts audit your infrastructure and processes through various assessments to uncover shortcomings, evaluate maturity levels, and determine how ready your company is to withstand attacks. This may also include designing the future security system in relation to people, processes, and technology and developing a roadmap to achieving that target state. The latter is particularly useful for implementing zero trust architecture, frameworks and principles – start now with Group-IB’s team of security experts.