Introduction
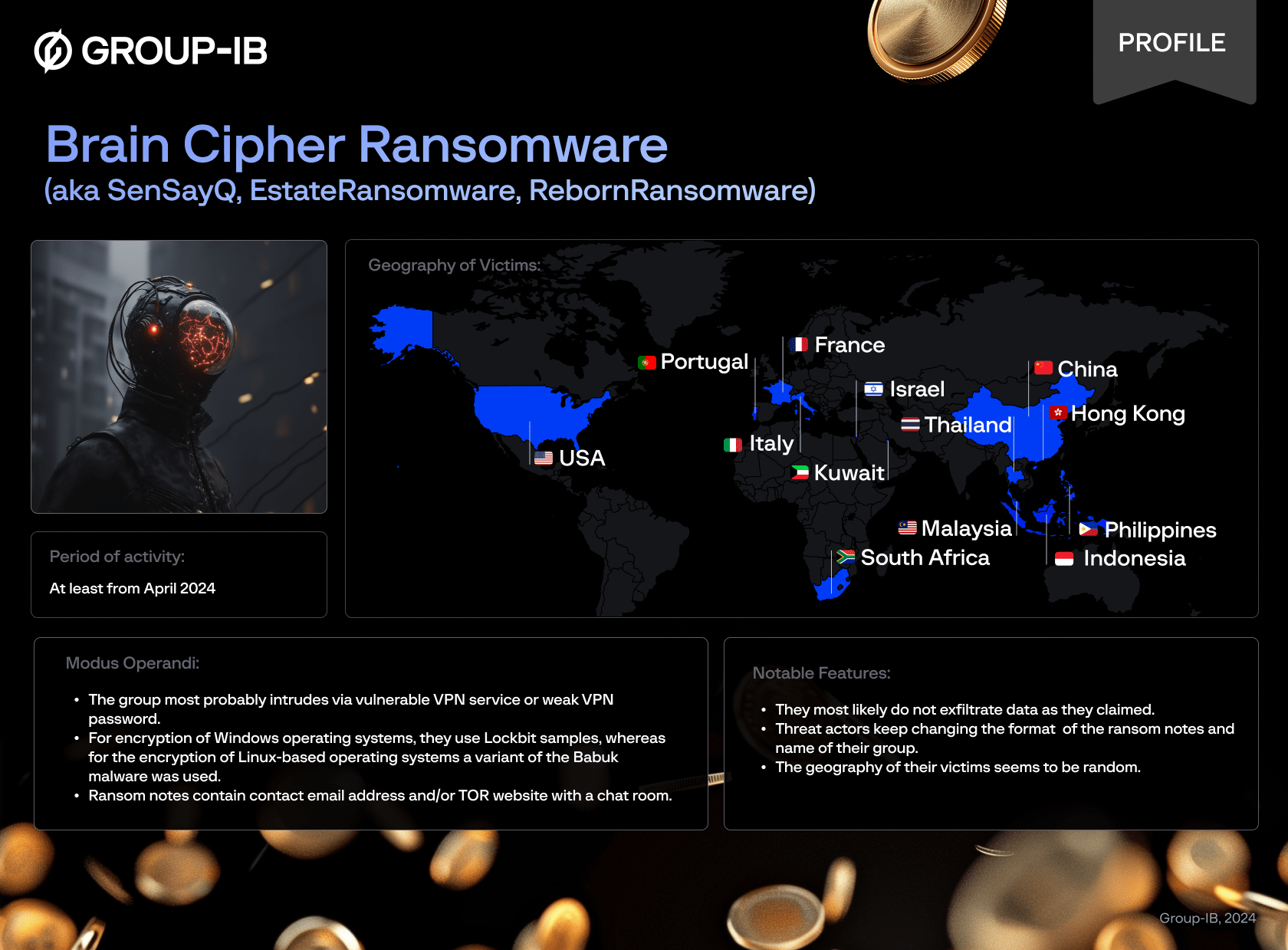
On 20 June 2024, Indonesian data center suffered a major ransomware attack that crippled approximately 210 critical national and local government services, including customs and immigrations, which resulted in substantial delays for travellers at the airports. The threat actor Brain Cipher that perpetrated the attack had initially demanded a ransom of US$8-million, but subsequently published the decryptor for free. In this blog, the Group-IB High-Tech Crime Investigation team sheds light on the threat actor’s previous attacks and techniques.
When a ransomware infection happens, a ransom note typically appears on the infected system. This note provides instructions on how to contact the ransomware group to decrypt the ransomware-encrypted data. The contact information can vary, ranging from email address to TOR onion links leading to a support page. As a method of double extortion victims could be blackmailed by a possibility of leaked data to be published on the ransomware group’s data leak site (DLS) or other resources.
Based on our research, individuals behind the Brain Cipher ransomware group have been active at least since April 2024. Group-IB has noticed variations of ransom notes left by the group which brought us to the connection with other ransomware groups such as EstateRansomware and SenSayQ. More details can be found within this article.
Key Discoveries in the blog
- The Group-IB High-Tech Crime Investigation team discovered the first traces of the Brain Cipher ransomware group on 16 June 2024.
- Brain Cipher ransom notes are found related to Lockbit malware samples.
- There are similarities in terms of style and content of the Brain Cipher’s ransom note to those by SenSayQ ransomware. The TOR websites of Brain Cipher ransomware group and SenSayQ ransomware group use similar technologies and scripts.
- The contact email addresses of SenSayQ ransomware group, EstateRansomware group and another ransomware group without a name specified overlap. First traces of the EstateRansomware group were found in April 2024.
- We suppose that individuals behind Brain Cipher and EstateRansomware could be the same. Tactics, techniques and procedures of the EstateRansomware were described by Group-IB before.
- The attacks in July 2024 with similar ransom notes were performed under the name of the RebornRansomware group.
Who may find this article interesting:
- Cybersecurity analysts and corporate security teams
- Malware analysts
- Threat Intelligence specialists
- Cyber investigators
- Computer Emergency Response Teams
- Law enforcement investigators
- Cyber Police Forces
What happened after Brain Cipher Ransomware Infections?
In the case of Brain Cipher ransomware, the ransom note is created on the victim’s infected systems in a format presented below.
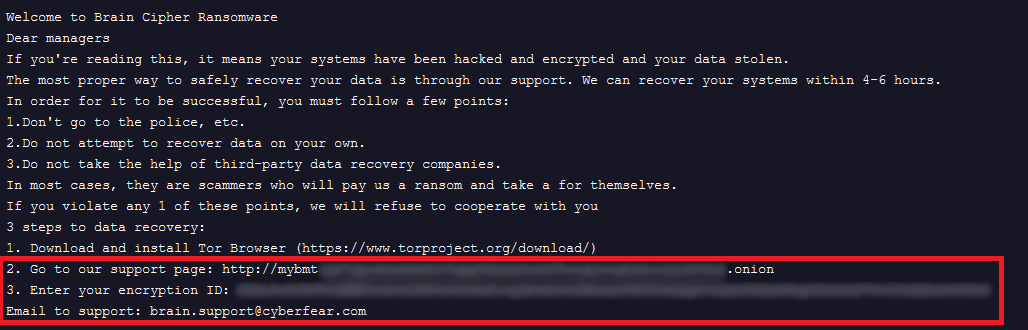
Figure 1. Example of Brain Cipher Ransom Note
In every ransom note, the TOR onion link to the ransomware group support page and an email address for technical support were provided.
- brain.support[@]cyberfear.com
- hxxp://mybm<redacted>[.]onion
Victims are supposed to access the TOR onion link provided in the ransom note that leads to the ransomware group’s support page. To join a chat room with threat actors, victims are required to enter a unique encryption ID which can be found in the same ransom note. If the victim has encountered any technical difficulty, they can contact the email address provided.
We have found several ransom notes mentioning Brain Cipher ransomware group. The first ransom note related to Brain Cipher was discovered on 16 June 2024. Victims of the group are located at least in Indonesia, the Philippines, Portugal, Israel, South Africa, and Thailand.
An additional onion link to Brain Cipher’s DLS was found in the ransom note which supposedly belonged to the victim in the Philippines.
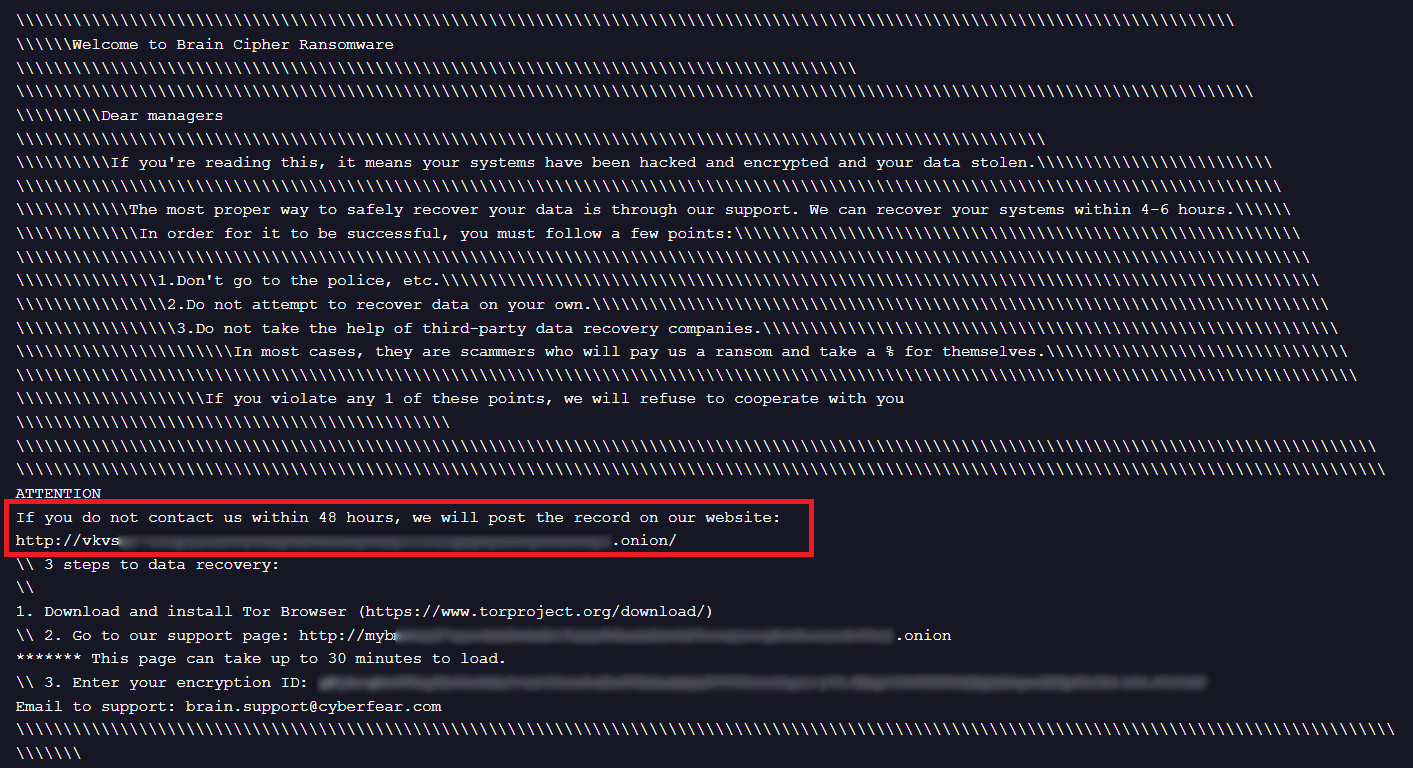
Figure 2. Brain Cipher Ransom Note contains link to DLS
Both websites will be described in the sections below.
Entering Brain Cipher’s Support Page
Victims of the Brain Cipher ransomware group would access the support page with the encryption ID written in the ransom note.
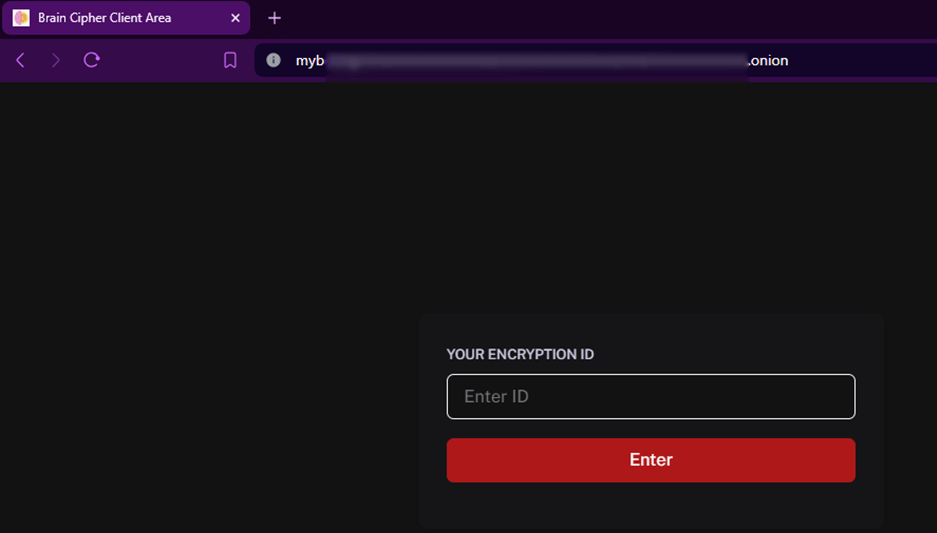
Figure 3. Screenshot of website for victims to enter their encryption ID to initiate data recovery with threat actors
The chat with the threat actors states the amount to be paid for decryption and the type of cryptocurrency. The example of chat with a victim is presented below:
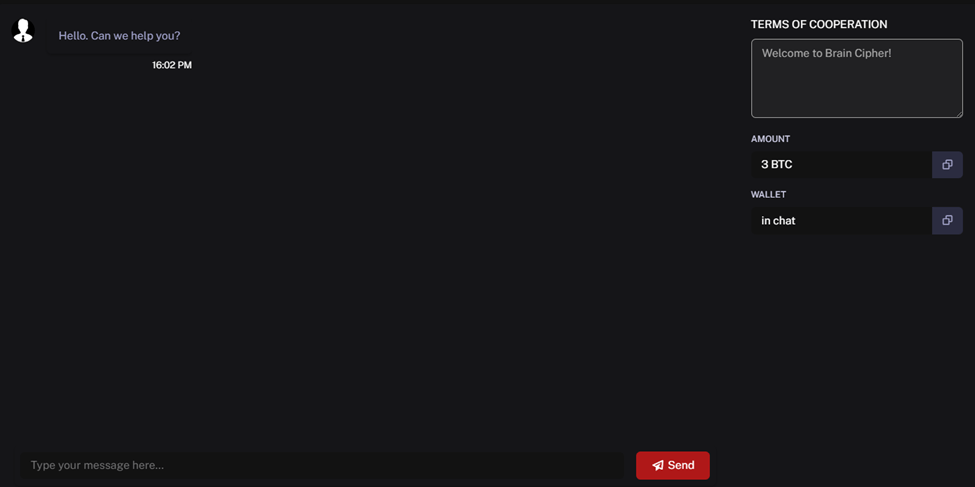
Figure 4. Chat room with threat actors after entering encryption ID
A part of the source code of the client chat area is presented below:
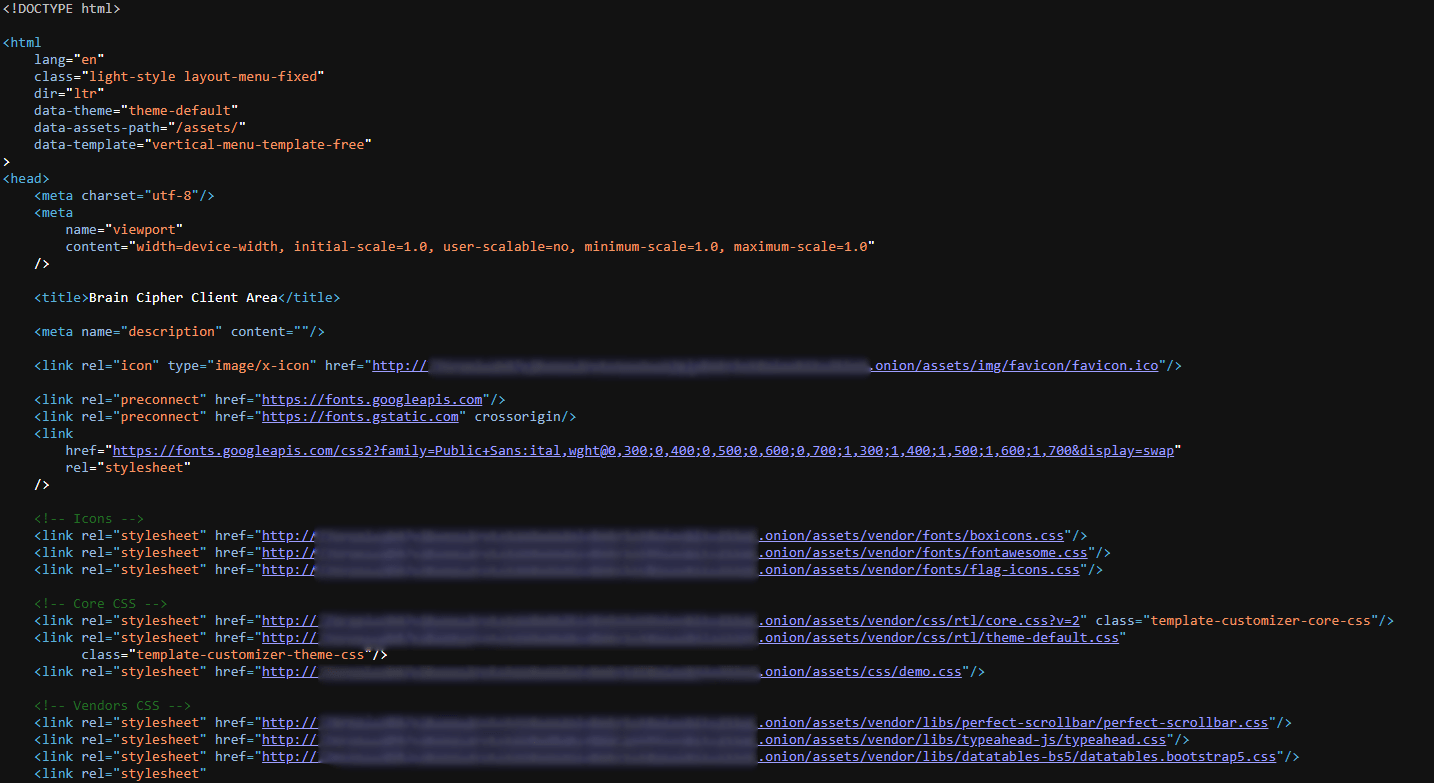
Figure 5. Source code of client chat webpage
We will compare it with the web resources of other groups further.
Data Leak Site of Brain Cipher Ransomware group
At the time of writing the DLS is still online with the main page showing data leaks belonging to 7 companies. Each of the leaked data can have a timer.
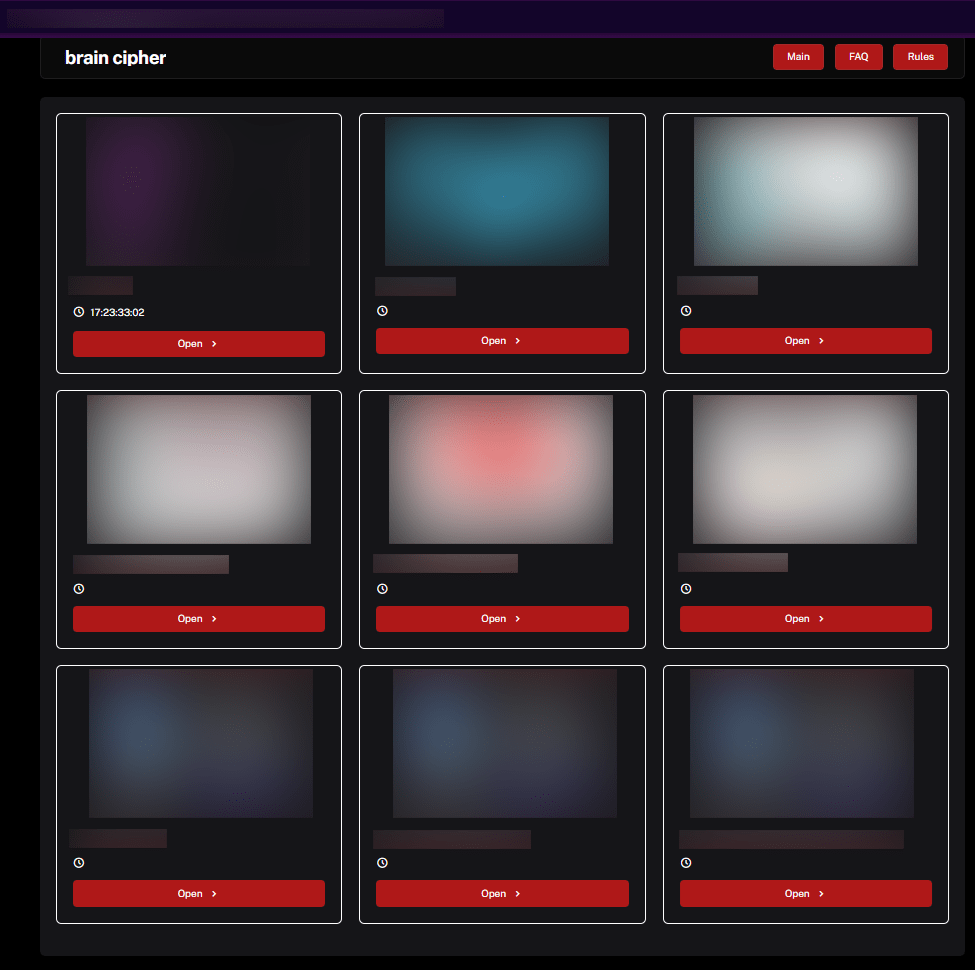
Figure 6. Announcement of attacks on DLS of Brain Cipher (as of 13 August 2024)
The screenshot below shows an example of the announced data leak which will be available for download after 6 days at the time of writing.
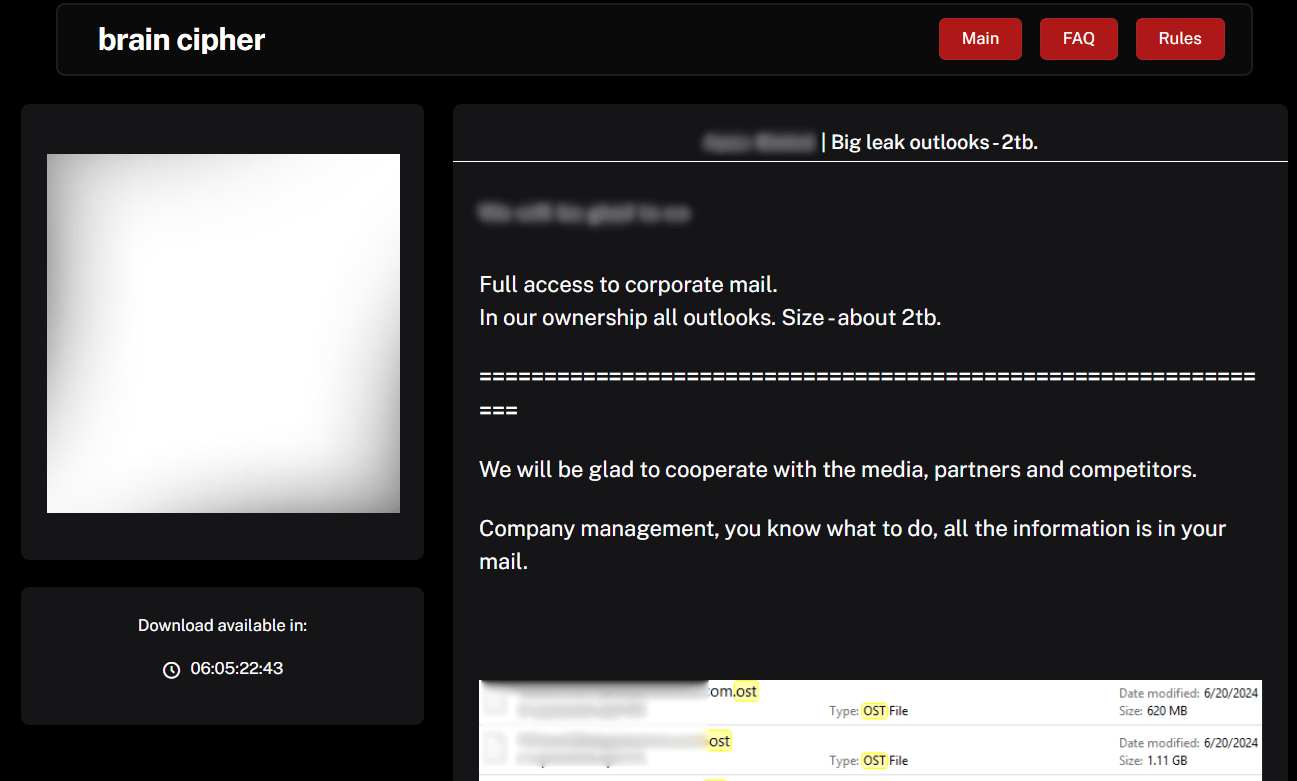
Figure 7. Screenshot of a data leak data for one of the victims
The data was not published for most of the victims we monitored, so we can assume that Brain Cipher doesn’t exfiltrate content from the victims as they claim.
Scripts used by the DLS main page are presented below:
Figure 8. Scripts used by the DLS of Brain Cipher
The DLS also contains information about their terms of service and also a FAQ section. The FAQ section contains the same contact information contained in the ransom notes.
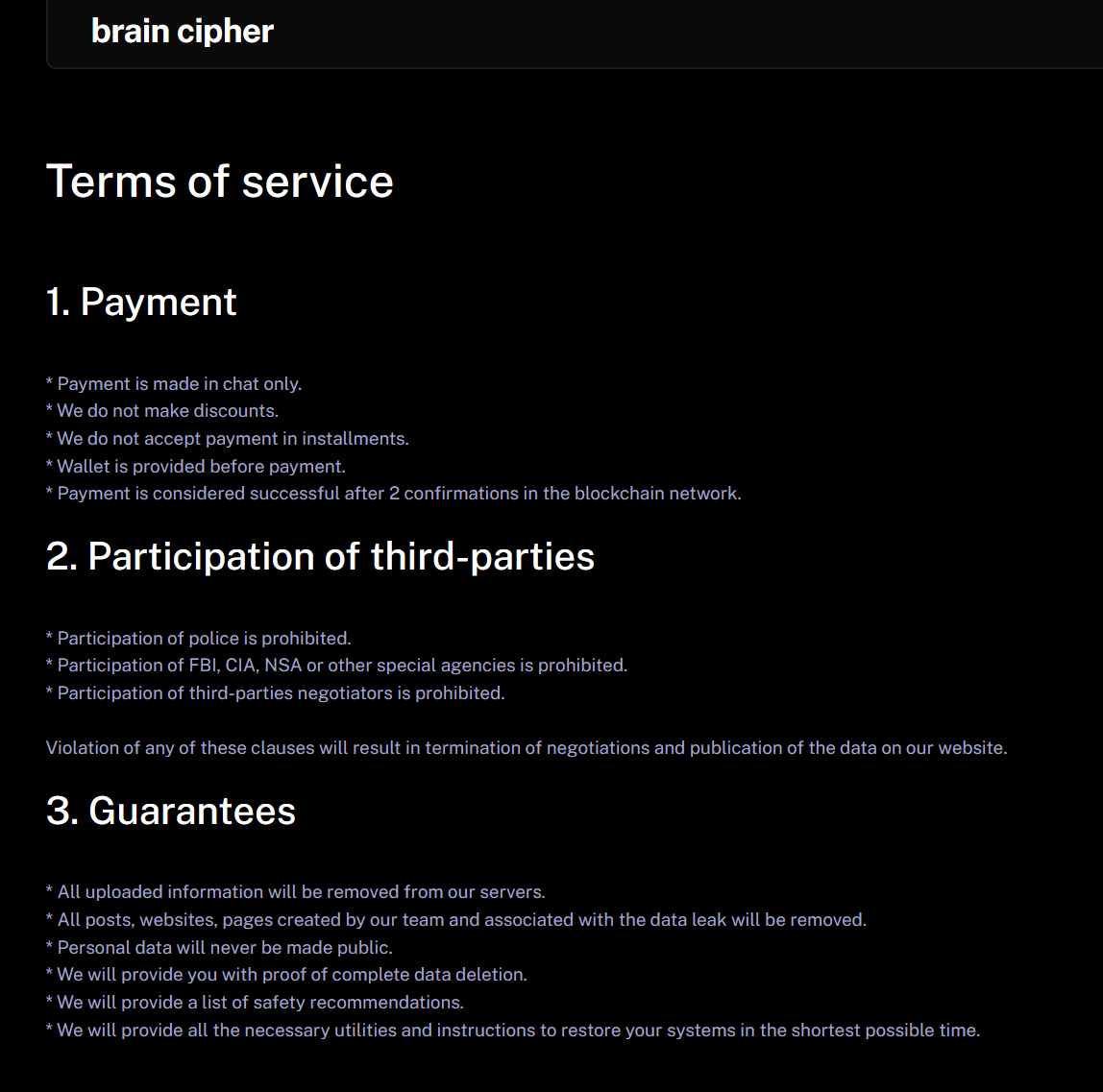
Figure 9. Terms of Service on the DLS
Figure 10. FAQ section of the DLS
All these sections will be compared with similar sections of other ransomware groups below.
Connections to other ransomware actors
Most of the ransom notes left by Brain Cipher ransomware group were related to the malware samples detected as Lockbit. Below shows one of the ransom notes examples.
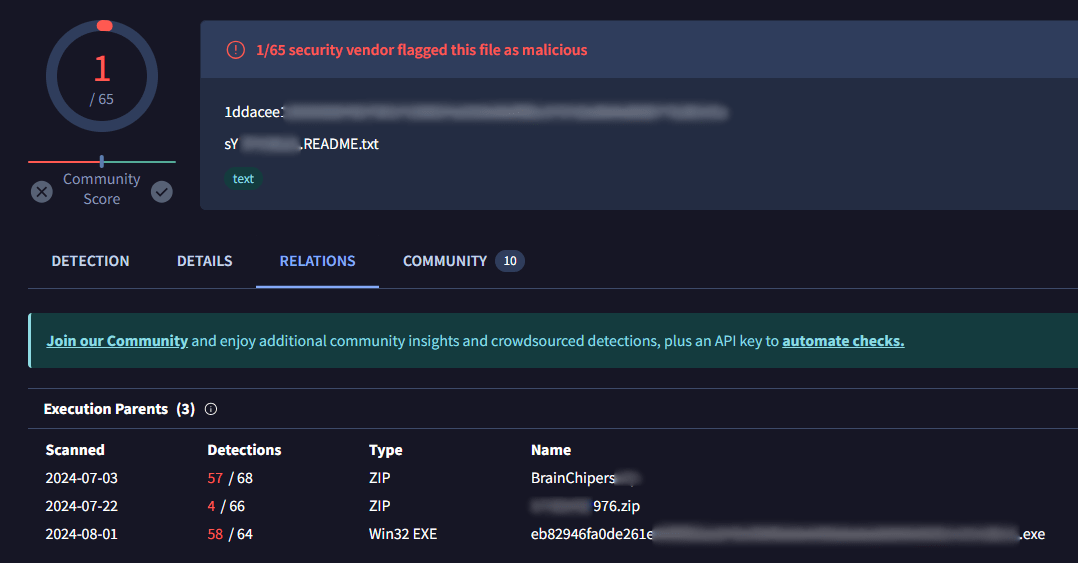
Figure 11. Correlation of ransom note with executable files
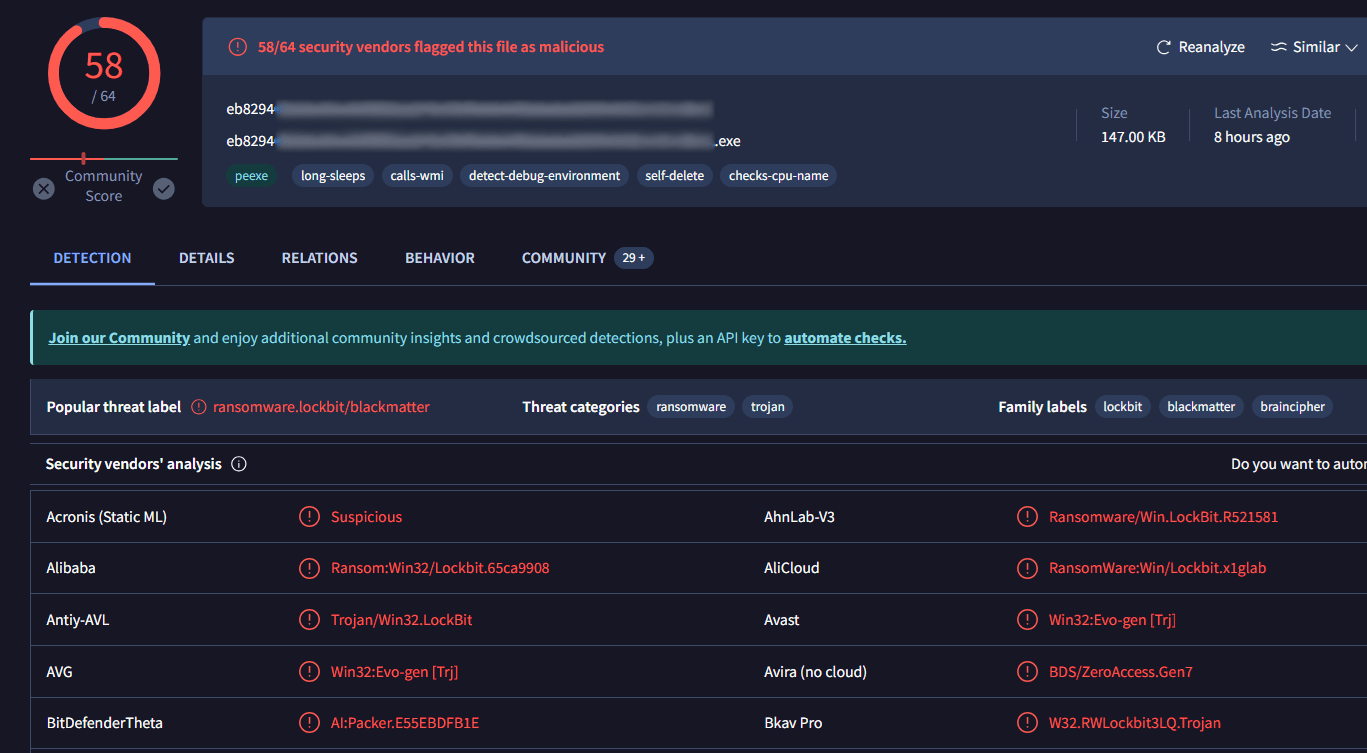
Figure 12. Detection of executable as Lockbit encryptor samples
The ransom note of Brain Cipher group contains the opening sentence of “Dear managers”, and phrases in the body content of “If you’re reading this, it means your systems have been hacked” and “within 4-6 hours”. It then ends with an email address belonging to cyberfear[.]com mail service. The format of the TOR website and the ID is presented below.
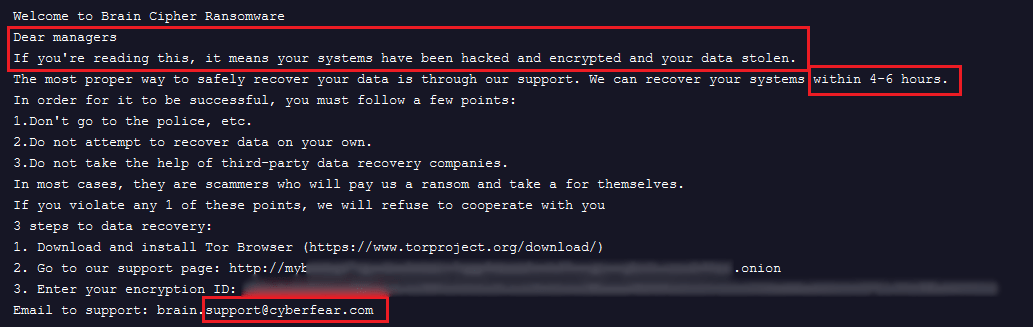
Figure 13. Example of Brain Cipher ransom note
Also, the group published a Linux decryptor for an Indonesian victim, which turned out to be a variant of Babuk ransomware sample.
With these patterns, the Group-IB Investigation team discovered several similar ransom notes of other ransomware groups.
SenSayQ Ransomware
While searching for ransom notes that are similar to Brain Cipher one and are related to Lockbit malware samples, a ransom note was discovered which contains a new email address, qn.support[@]cyberfear.com. It has the similar opening sentences “Dear managers” and “If you are reading this, it means your network has been attacked”.
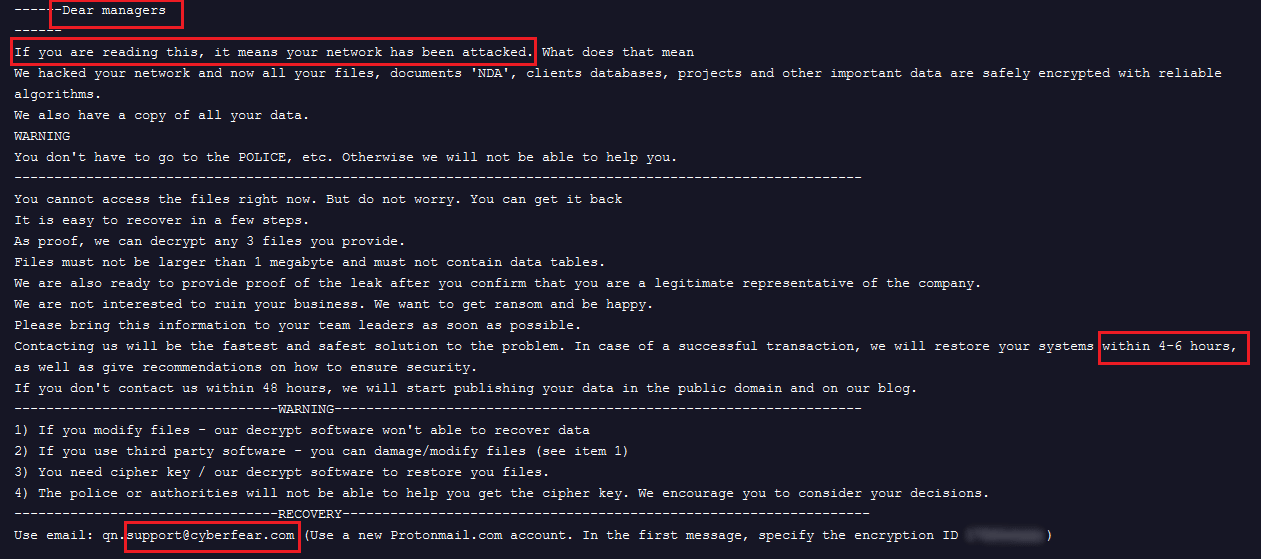
Figure 14. Ransom note of another ransomware group with some phrases similar to Brain Cipher ransom notes
The format of the note is not as Brain Cipher uses. There is no mention of the involved group, so we will refer to it as the “Noname” group.
However, the same email address qn.support[@]cyberfear.com was found in the ransom note of SenSayQ ransomware group. It also contains the TOR link of the support page for SenSayQ ransomware.
![Screenshot of SenSayQ ransom note containing the same email address qn.support[@]cyberfear.com](https://www.group-ib.com/wp-content/uploads/brain-cipher-ransomware-15-min.png)
Figure 15. Screenshot of SenSayQ ransom note containing the same email address qn.support[@]cyberfear.com
The format of the encryption ID of Brain Cipher and SenSayQ groups are similar. They also had a victim support page. Both specified contact email with the word “support” and use mail service “cyberfear.com”.
The SenSayQ support page was offline at the time of writing, we found the saved copy of the website and its interface looks similar to the support page of Brain Cipher.
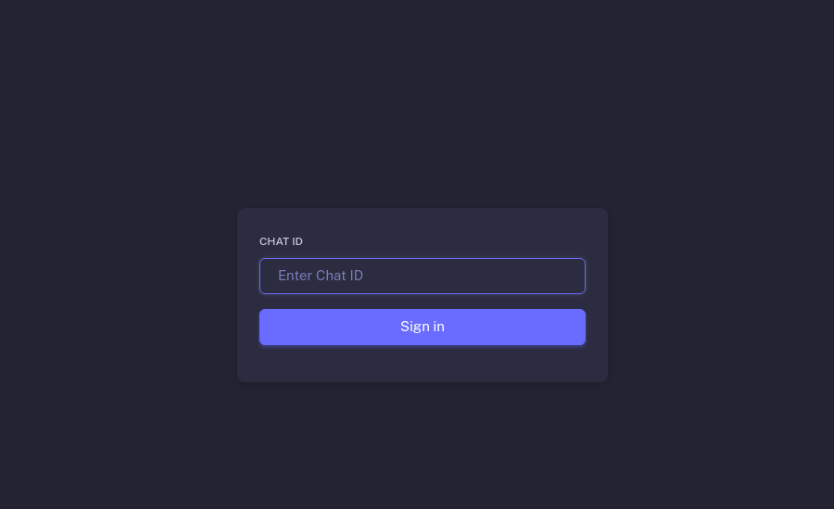
Figure 16. Support page of SenSayQ ransomware groups
The part of the source code for this page is presented below:
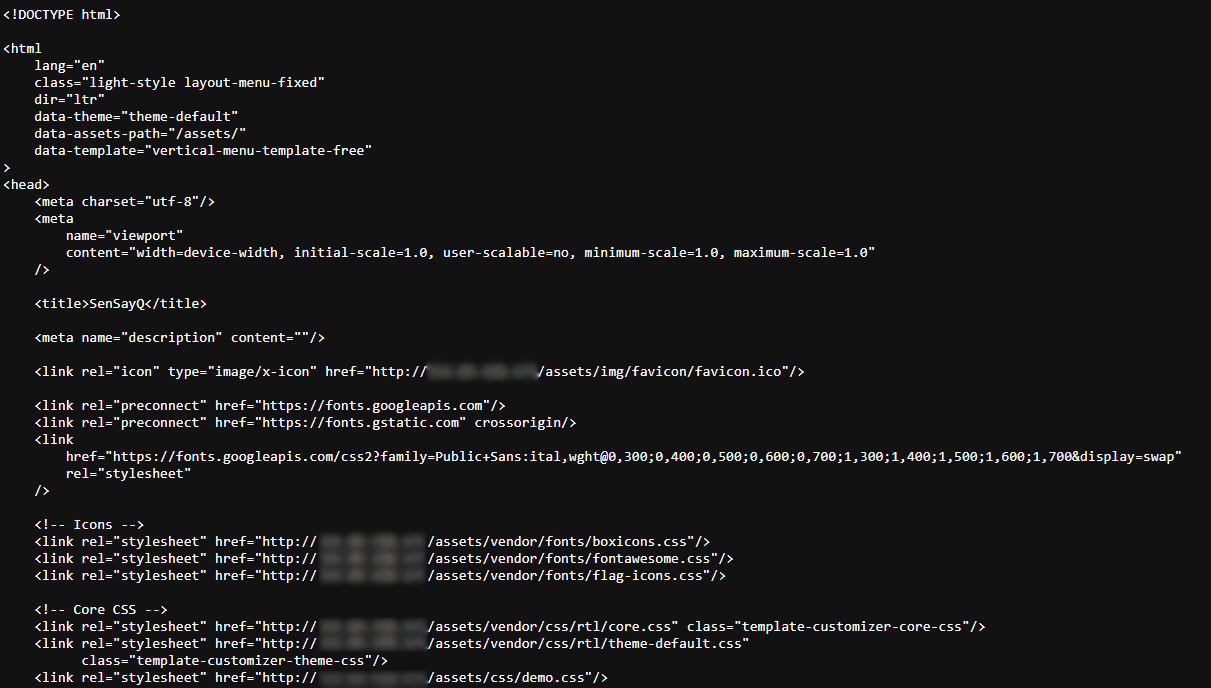
Figure 17. Source code of SenSayQ support page
It is similar to the one of Figure 5 for the Brain Cipher support page. The same stack of technologies and scripts were used by the Brain Cipher group.
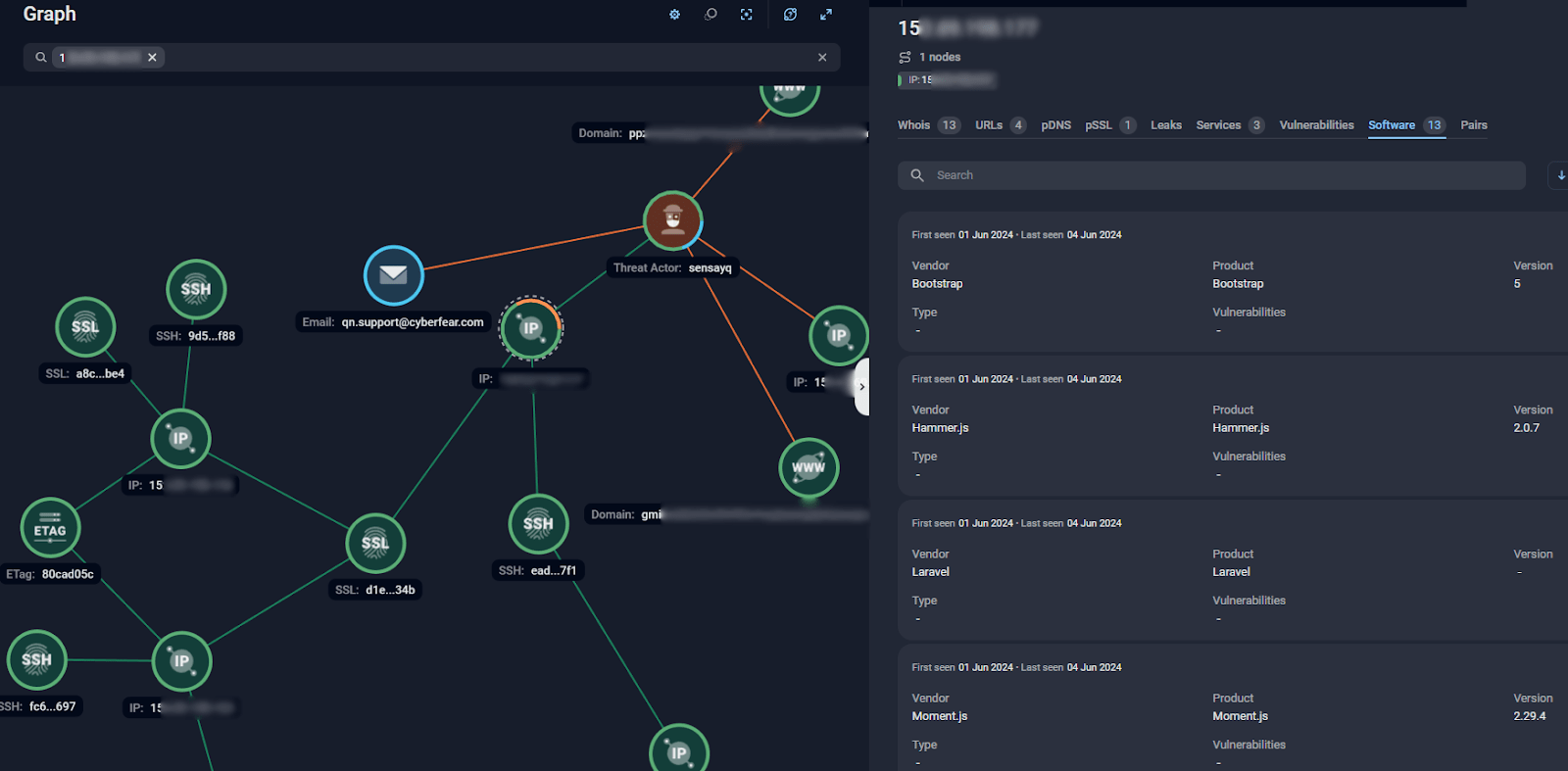
The information about correlation of SenSayQ servers and identified stack of technologies is shown using Group-IB Graph:
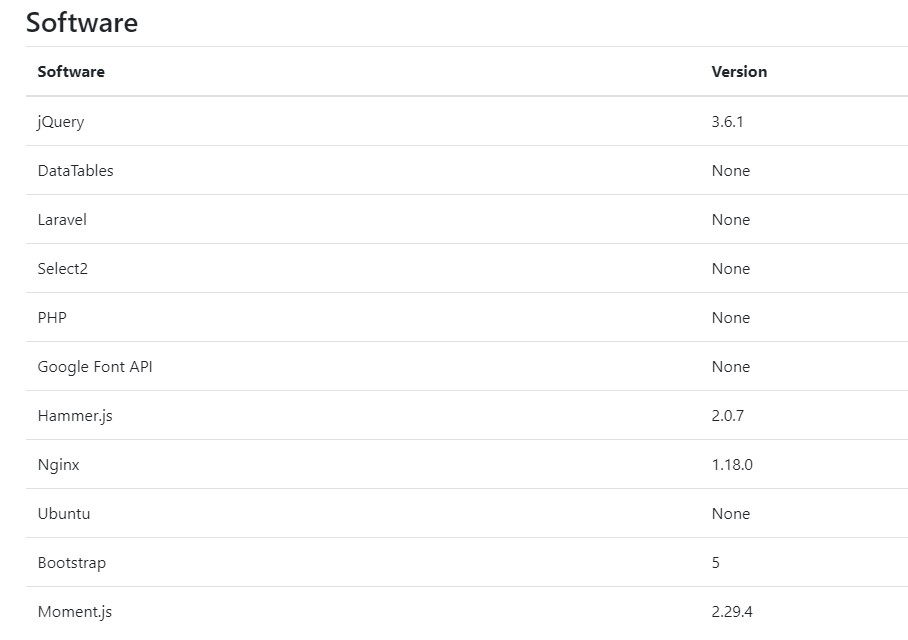
Figure 19. Stack of technologies used by SenSayQ support page website
SenSayQ ransomware group had a separate DLS as well. The interface of the website is presented below:
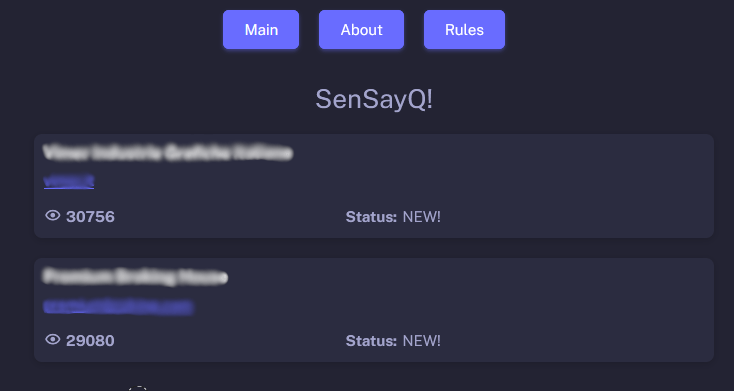
Figure 20. Data leak about two companies presented at the main page of SenSayQ DLS
The same list of scripts was used by both SenSayQ and Brain Cipher (Figure 8) DLS websites:
Figure 21. Scripts used by SenSayQ DLS main page
The DLS of SenSayQ has a FAQ (about) and Rules section. The rules are similar to those used on Brain Cipher DLS.
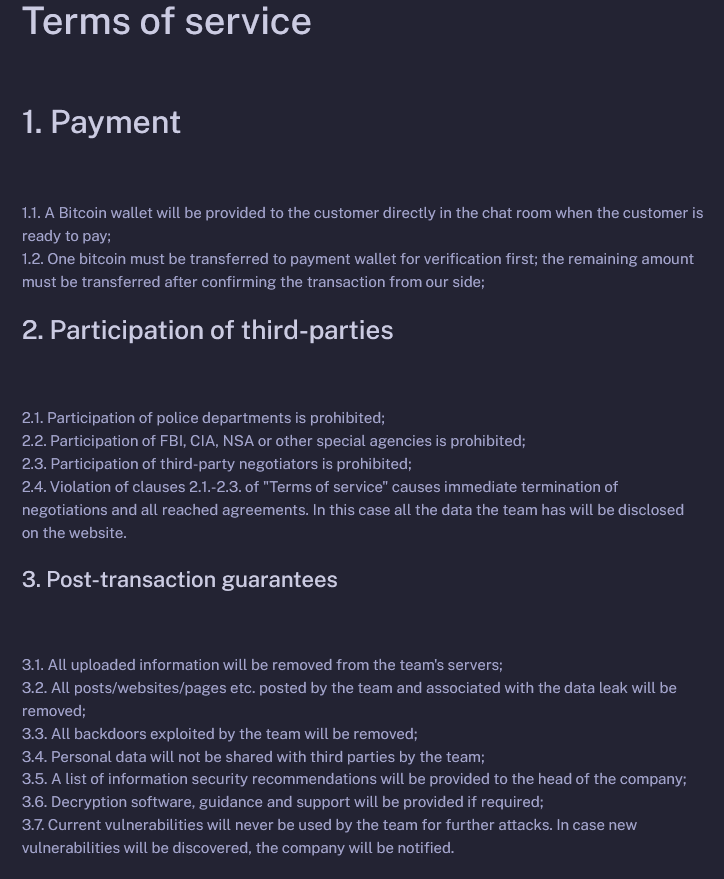
Figure 22. Rules section on SenSayQ DLS site which is similar to the terms of service on Brain Cipher DLS
So, we concluded that Brain Cipher and SenSayQ could be related to each other due to similarities in their ransom notes, contact details and TOR websites.
Since SenSayQ shares the same contact email address with a “Noname” ransomware group we can suppose that all three are related to each other.
EstateRansomare
Another email of the “Noname” group is shared with the EstateRansomware.
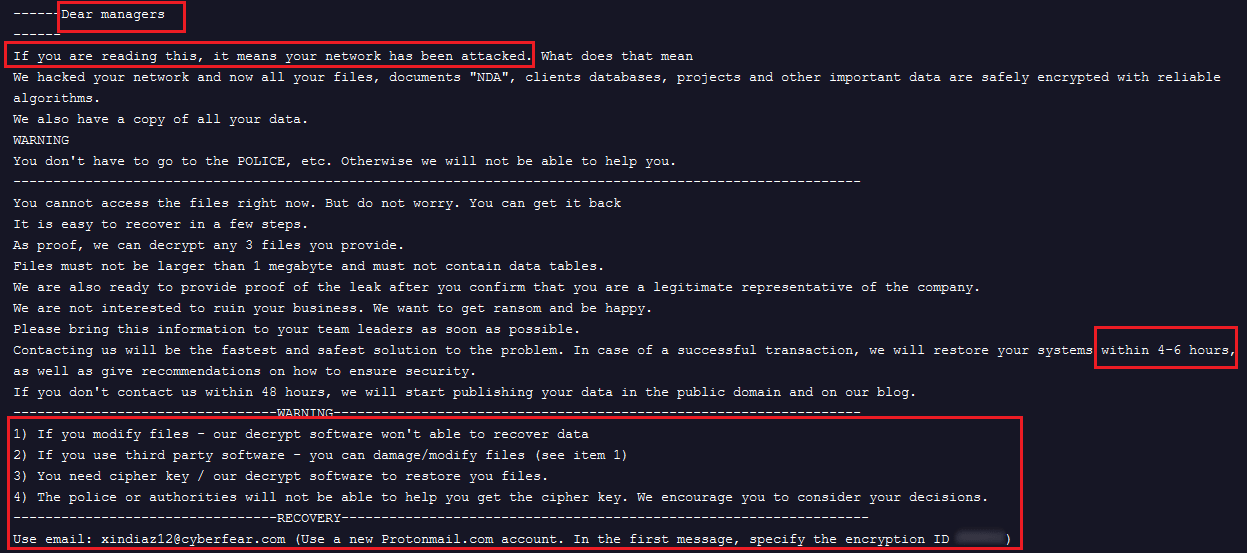
Figure 23. Screenshot of a ransom note used by “Noname” group
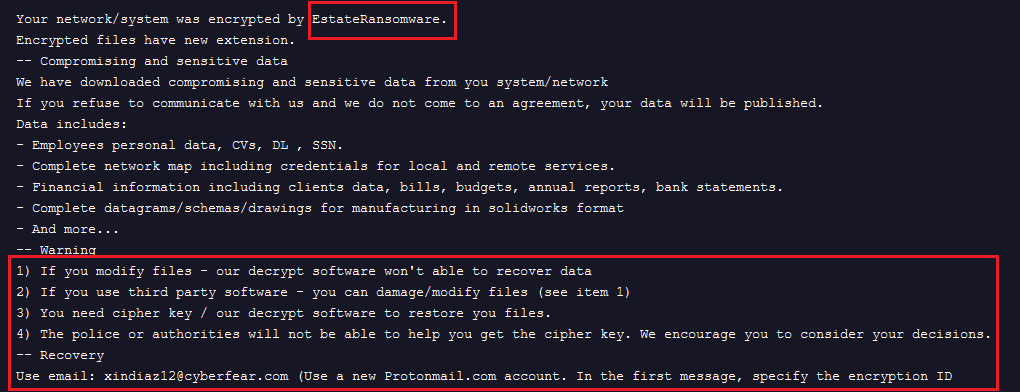
Figure 24. Screenshot of EstateRansomware ransom note with similar warning message and instruction to use protonmail
Group-IB has previously published the Incident Response details for the EstateRansomware group.
Based on the comparison we believe that EstateRansomware, SenSayQ and “Noname” ransomware are controlled by the same individuals as the Brain Cipher group.
We have discovered victims of the EstateRansomware/SenSayQ/Noname groups in France, Malaysia, Hong Kong, the USA, Italy, and Lebanon.
RebornRansomware
Some of the recent attacks in July 2024 with a similar format of a ransom note was linked to RebornRansomware:
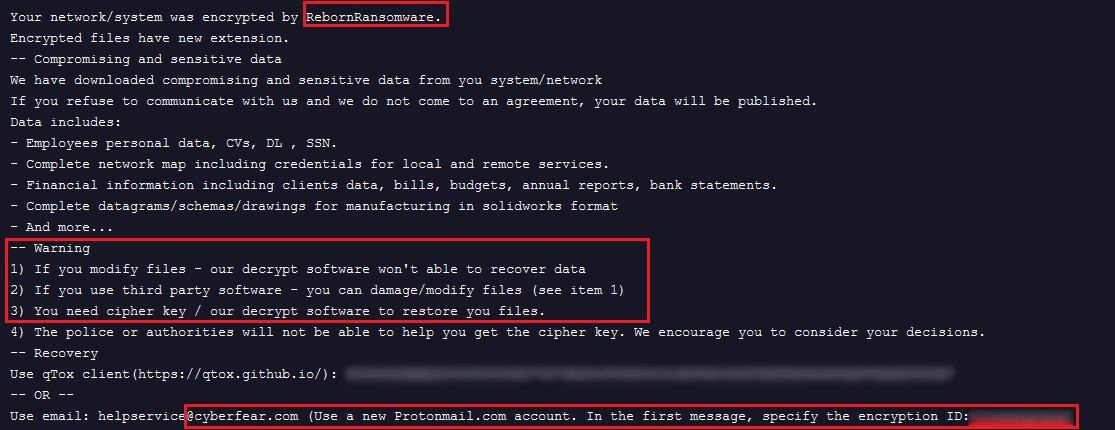
Figure 25. Screenshot of RebornRansomware ransom note
The new contact email is helpservice@cyberfear.com. The TOR website is changed to qTox account. Victims of the RebornRansomware group are located at least in France, China, Kuwait and Indonesia, at the time of writing.
Timeline of Events
The revealed correlations among ransom notes are presented below. Some of the victims of Brain Cipher were discovered in August 2024 as well. Some of the victims for SenSayQ were added to their DLS later in June 2024.
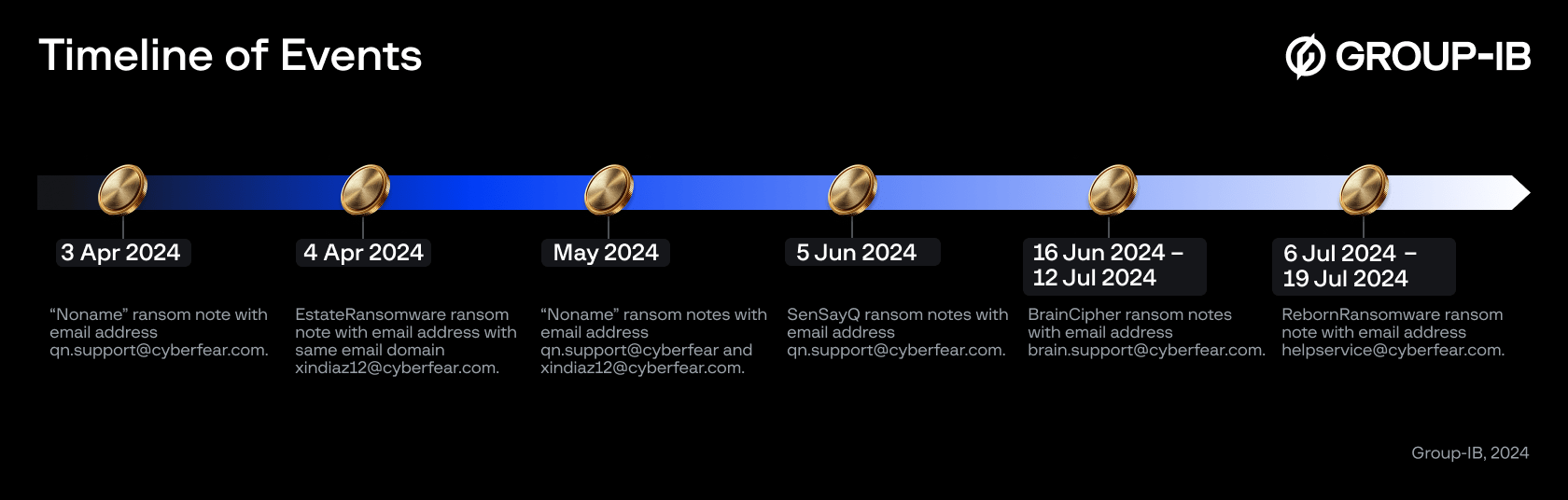
Figure 26. Timeline of changing in ransom notes of possibly related ransomware groups
Similarity in ransom notes, correlation of email addresses and chronological following of changing names can make us think that the same individuals are behind EstateRansomware, SenSayQ, Brain Cipher and RebornRansomware. We won’t make any suggestions on the reason for constantly changing the brand of the group in an era of a big game hunting by ransomware players. Group-IB will be watching Brain Cipher with any new name they decide to take.
Recommendations
- Monitor and audit accounts regularly. Delete or disable any dormant account to prevent unauthorized access. Implement multi-factor authentication (MFA) for VPN and other remote access services.
- Implement patch management policy to ensure firmwares and softwares used are updated with the latest security patches to protect against known vulnerabilities.
- Segment critical systems and enforce strict firewall rules to limit lateral movement within the network. Disable unnecessary RDP access and restrict it to specific, trusted IP addresses.
- Implement application control on hosts to prevent execution of unauthorized programs. Ensure that only approved security applications are used and running on enterprise systems.
- Implement Endpoint Detection and Response (EDR) solution to detect and respond to suspicious activities such as deployment of backdoors and the use of tools like PsExec.
- Engage in MTH (Managed Threat Hunting) service, to proactively detect unknown threats and sophisticated attacks.
- Subscribe to an incident response retainer service to ensure access to a team of cybersecurity professionals who can effectively respond to any incidents that may occur within the infrastructure.