A new high-impact and easy-to-exploit vulnerability with a CVSS Base Score of 9.8 has been reported by CERT-UA. According to the Microsoft Threat Intelligence team, the vulnerability was exploited by a Russia-based nation-state threat actor in targeted attacks against a limited number of European organizations in the government, transportation, energy, and military sectors. The exploit was used to bypass NTLM authentication and gain unauthorized access to an internal network using an intercepted account.
The exploit doesn’t require any user interaction to trigger the vulnerability.
How does the exploit work?
The attacker sends a specially crafted email containing an extended MAPI property PidLidReminderFileParameter, which includes a UNC path to an SMB (TCP 445) share on a server controlled by the threat actor. The connection to the remote SMB server sends the user’s NTLM negotiate message, which the attacker can then relay for authentication against other systems that support NTLM authentication.
Due to the logic implemented in MS Outlook, once the malicious email is received by the Outlook client, the vulnerability can be triggered immediately.
Which systems are affected? Am I in danger?
CVE-2023-23397 impacts all supported versions of Microsoft Outlook for Windows but doesn’t affect Outlook for Android, iOS, or macOS versions.
Online services such as Outlook on the web and Microsoft 365 (online but not Microsoft 365 Apps) do not support NTLM authentication, thus they are not vulnerable to attacks exploiting this NTLM relay vulnerability.
To check whether you have been targeted using this vulnerability, you need to identify emails containing a PidLidReminderFileParameter property. Luckily, Microsoft has already published a PowerShell script to perform such audit.
Threat Intelligence: underground buzz and attribution
Given the ease of implementation, It is a matter of when, not if, the cybercriminals will add this exploit into their arsenals.
Even though the usable exploit is already available on GitHub, there are some discussions on how to use/buy an exploit code for CVE-2023-23397:

Figure 1. Underground discussions about CVE-2023-23397. Source: Group-IB Threat Intelligence
Here is a sample available on VirusTotal 582442ee950d546744f2fa078adb005853a453e9c7f48c6c770e6322a888c2cf:

Figure 2. Sample email exploiting CVE-2023-23397
If we check properties of that email, we can find a PidLidReminderFileParameter property, the value of which can be found via the Outlook interface:

Figure 3. The value of PidLidReminderFileParameter property. Source: Group-IB Threat Intelligence
If we use the above IP address to build a network graph with Group-IB’s proprietary Graph Network Analysis tool, it reveals the link with APT28 – the only group that has been exploiting the vulnerability since last year. Given that CVE-2023-23397 became known in March 2023, it confirms the link to this nation-state threat actor.
![Network graph based on 113[.]160[.]234[.]229](https://website.cdn.group-ib.com/wp-content/uploads/4-min-20.png)
Figure 4. Network graph based on 113[.]160[.]234[.]229. Source: Group-IB Threat Intelligence
Mitigation steps
The most simple way is to keep track of the released patches and install them on time The necessary security updates can be found here.
If it is not possible, then as temporarily measures Microsoft suggests:
- Add users to the Protected Users Security Group, which prevents the use of NTLM as an authentication mechanism. Performing this mitigation makes troubleshooting easier than other methods of disabling NTLM. Consider using it for high value accounts such as Domain Admins when possible. Please note: This may cause impact to applications that require NTLM, however the settings will revert once the user is removed from the Protected Users Group.
- Block TCP 445/SMB outbound from your network by using a perimeter firewall, a local firewall, and via your VPN settings. This will prevent the sending of NTLM authentication messages to remote file shares
Group-IB’s solutions are capable of monitoring and detecting the attacks exploiting CVE-2023-23397. The malicious emails will be deleted before being delivered to your employees.
How Group-IB can help
Group-IB Business Email Protection automatically blocks CVE-2023-23397 in email messages as of March 15, 2022.
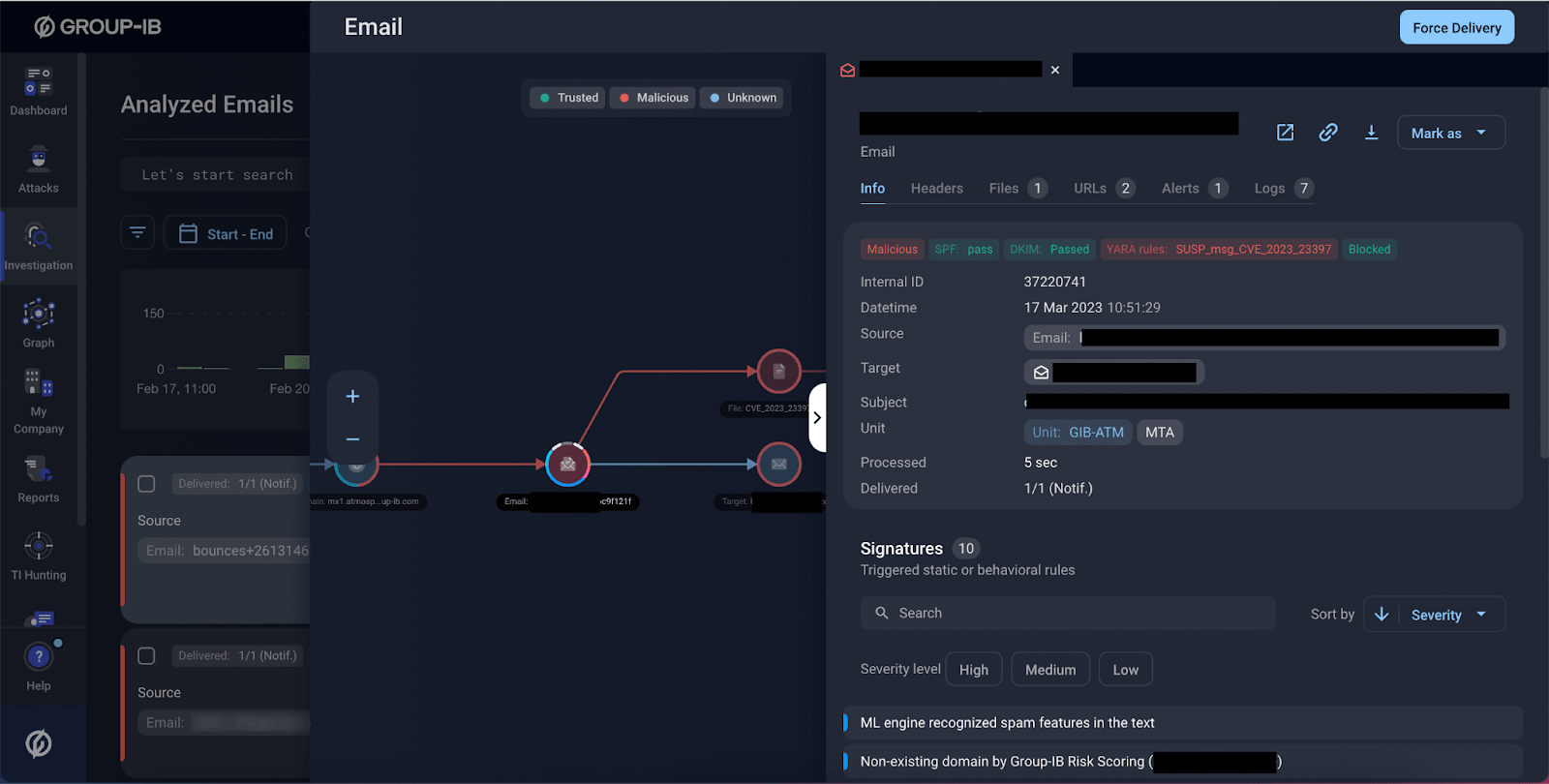
Figure 5. An email with malicious payload blocked by Group-IB Business Email Protection
Try Group-IB Business Email protection Now
Block advanced email-borne threats
































