Introduction
The airline industry is continuously exposed to new vulnerabilities, which can function as major attack vectors. From fake support, scam giveaways, booking payment fraud, in-flight scams, and employee account phishing to loyalty program fraud – the airline industry, according to Europol, is estimated to lose over $1 billion in yearly damage. The increasing cyber threats directly affect the brand and its associated service providers and customers.
Frequent travelers are rewarded with miles or redeemable points to revere their brand loyalty. But as much as your customers are eager to cash in on the accrued benefits of a miles bonus program, fraudsters show a similar resolve.
Just like credit cards or fiat currencies, air miles and loyalty points are also considered a currency, making the misuse of the programs more lucrative to the fraudsters.
According to Group-IB research, the number of cases of loyalty fraud increased exponentially by 30% in 2022 compared to a year earlier.
In 2022, over 75 airlines were impacted by fraudsters, and over 2,000 malicious resources were involved in fraudulent schemes.
The problem of airline scams is increasing. More businesses from various industries are taking an extra step to educate their customers to prevent fraud. One of the most recent examples is the N26 anti-airline-scam campaign.
Customer Service Scam
Scammers impersonate airlines’ customer service through fake websites, fake phone numbers, and call centers accepting calls to these phone numbers. The scammers share US-format phone numbers via different platforms. They also created flight reservation websites that lure customers into calling a phone number to book a flight or claim a refund.
The customers are first lured into calling the provided phone numbers as the flights proposed cannot be booked online. Then, the customers are led into giving their banking information to fulfill their needed reservations. After giving their flight information (dates, destination, preferred seats, etc.), the customers can provide their credit card numbers to complete the transaction. Once given, the scammers have all the information needed to steal money from the given credit cards.
Along with stealing banking data, fraudsters try to take control of a victim’s PC by persuading them to install remote access Trojans (RAT). Once they capture control, fraudsters can steal data stored on the PC.
Most websites are linked to the same or similar phone numbers, implying that the scammers use a common call center or a virtual carrier to perform their scam. Most websites also seem to be structured in the same way giving more hints that the same group of scammers would operate this scam. As a result of our investigation, we identified a group of scammers from India who are behind this attack. We are currently collecting information to pass it on to law enforcement agencies.
Air Miles Loyalty Program Fraud
What is a miles bonus program? It is a loyalty program offered by airlines, credit card companies, and other businesses. The program rewards customers with miles, which can be redeemed for flights, upgrades, product purchases, or other perks.
Miles are typically earned by making purchases with an affiliated credit card or by miles earned per dollar spent, varying per the program. Miles are usually redeemed for flights on the airline or its partners or upgrades to business class/first class. Some programs also offer bonuses for reaching certain milestones, such as the number of flights or a particular spending range achieved.
So far, Group-IB’s Fraud Intelligence team has identified companies affected by the scheme in the EU, the UK, and the US. Our analysts also tracked fraudulent activities against six major North American airlines, three major European airlines, and many others.
Loyalty scheme execution stage
Loyalty fraud can be committed through mile hacking, mile/point buying, account takeovers, and other illegitimate means to steal rewards and benefits. Airline fraud impacts many stakeholders, which is why cybercrime has been an increasing security concern for national and international security authorities such as INTERPOL, Europol, etc.
How is loyalty fraud initiated? A phishing website disguised as an authentic airline is created, and the victim is redirected to the page to take a short survey and then fill out a form to receive winnings. Furthermore, the victims can be redirected to the company’s legitimate website depending on the attacker’s goals. This is how the attackers obtain the victim’s data.
Also, the phishing page may contain a request to provide card details, and after confirmation, the victim gets a message from a bank to “confirm” the card details. At this point, the fraudster gains access to the funds and makes a transfer.
Here’s how loyalty program members’ personal information is collected and their accounts are accessed.

Figure 1: Scheme overview
Group-IB Fraud Matrix representation
Group-IB Fraud Matrix analyzes fraudulent schemes and outlines techniques used by fraudsters at each stage. Based on the MITRE model, the Matrix is a critical source of intelligence against fraud with deep insights into schemes, modus operandi, as well as recommendations that can ensure your organization is equipped with the most robust defense measures. To demonstrate the value of the Group-IB Fraud Matrix, we will walk through this particular scam campaign according to the stages outlined in Figure 4 (below).

Figure 4: Fraud Matrix Bonus Fraud Scheme
Reconnaissance & resource development stages
- Promotion of fake numbers
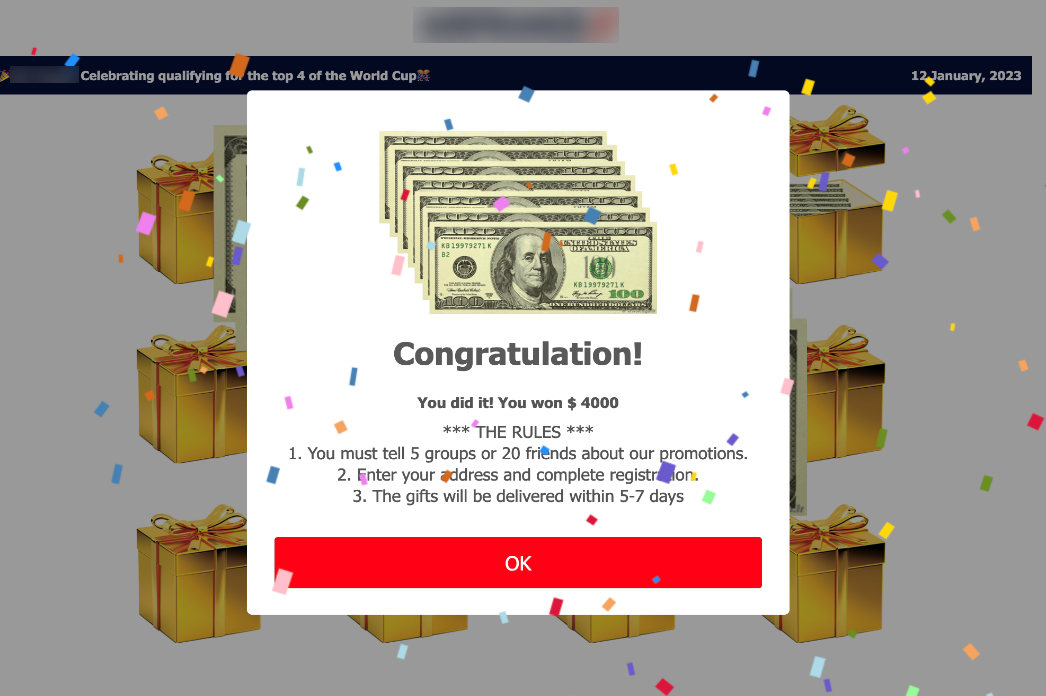
Fraudsters run a mass promotion campaign to deliver fake support numbers to victims. They create malicious infrastructure on social networks, blogs, fake websites, etc. The number of fake advertisements is so high that it is barely possible for the passenger to find legitimate contact details.

Figure 5: Fake advertisement example
- Establishing specialized call centers
A customer service scam is a common way to steal credentials and utilize them for transactional fraud. Fraudsters have an organized business and well-equipped call centers with multiple employees and hierarchy.
- Buying compromised accounts
Buying stolen data on the dark web or underground forums is relatively simple. You only need an internet connection, a special browser, and Bitcoin.
- Developing a phishing/scam campaign targeting an airline or a loyalty program provider
This approach is used more often. A message is sent to the victim via instant messengers or email containing a message about winning a big prize and a link to a phishing page.
Trust abuse, end-user interaction, credential access, and account access stages
- Mimicking airlines’ customer services
Once a victim calls the scammers, they pretend to be an airline customer support operator by using prepared scripts and mimicking an airline corporate code. Victims are lured into providing their flight details and credentials on the call.
- Phishing pages
As stated earlier, in this stage, the victim has to take a short survey and then fill out a form to receive a reward on a phishing site to obtain the victim’s data.
Also, a phishing page may contain a request to provide card details, and upon confirmation, the fraudster can execute a transfer. The presented matrix considers collecting personal data about the victims to access a user’s account on the company’s legitimate website.
Initiation of fraud, monetization, and laundering stages
Depending on the goals of the attackers and the airline or service provider of the program, the fraudsters can:
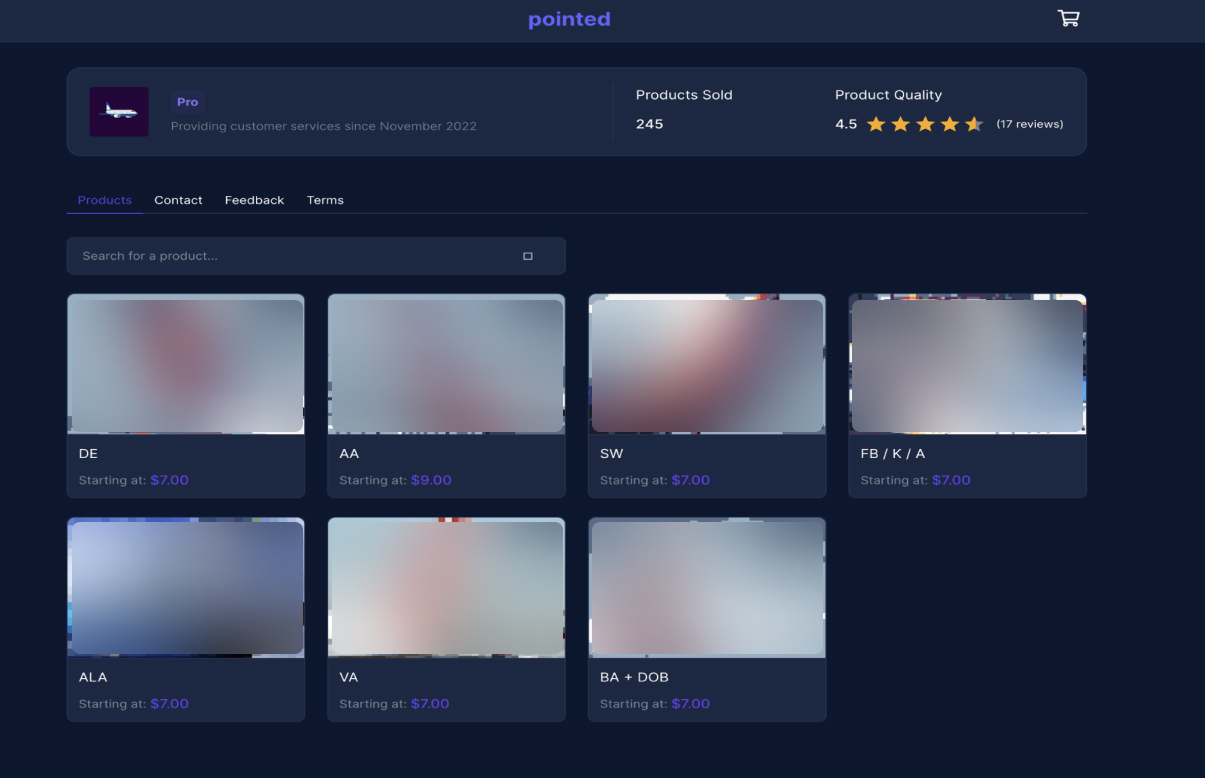
- Sell accounts to third-party scammers on specialized sites
- Offer to buy tickets with significant discounts for 3rd party persons.

Figure 9: Selling flights at 60% discount
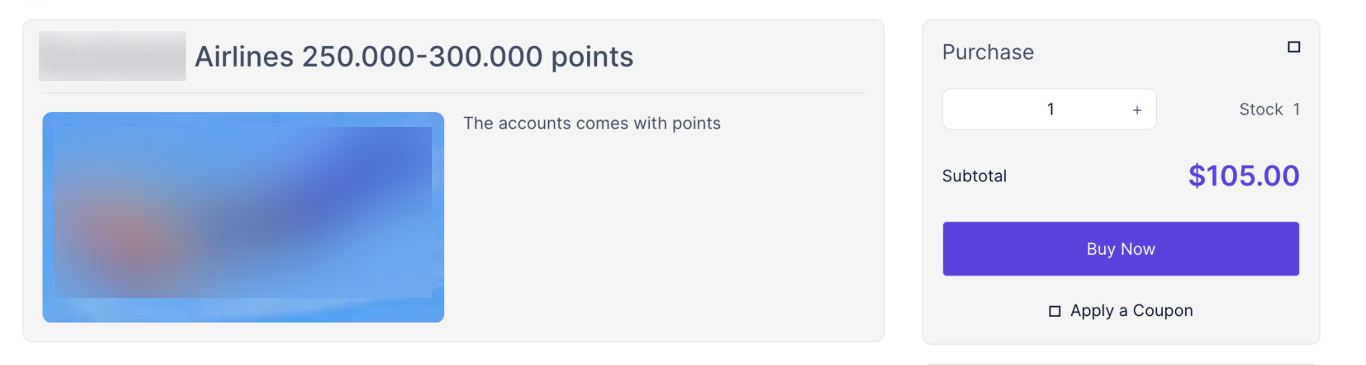
- Withdraw funds through the loyalty program partners.
Third parties linked to the loyalty program that need to take necessary steps to protect their platforms provide an easy extraction point for fraudsters.

Figure 10: An example of buying goods for points
Detection and Prevention
There are several steps that companies can take to mitigate and detect bonus fraud in their loyalty programs at different stages of the attack.
Reconnaissance stage
Tools and capabilities required:
Fraud and Threat Intelligence
Monitoring demand on data from fraudsters/hackers, possible data leaks of user data including 3rd party providers, and information about malicious call-centers recruitment ads on
- Darknet & deepnet
- Underground forums & specialized platforms
- Forums & instant messengers
Sessional anti-fraud systems:
Prevent account takeover and monitor multi-accounting to detect fake account creation.
- Passive biometrics with behavioral analysis
- Advanced device fingerprinting
Resource development, trust abuse, and end-user interaction stage
Tools and capabilities required:
Digital risk monitoring and mitigation tools:
- Monitoring phishing pages targeting the company and/or supply chain service providers
- Detection and analysis of the fraudsters’ infrastructure
- Risk prevention and attack mitigation: removal of fake contact information from publicly available sources like websites, social networks, and blogs
- IoC collection and hunting rules creation

Figure 11: Example graph infrastructural analysis. Source: Group-IB Graph Network Analysis tool
Detecting artifacts related to the preparation of scam distribution campaigns in an existing data flow, like copying legitimate websites or specific tools fraudsters use to create landing pages.
Credential access and account access stage
Tools and capabilities required:
Sessional anti-fraud systems:
- Access to user accounts from unusual or high-risk locations, new devices, or well-known fraudulent devices.

Figure 12: Group-IB Fraud Protection Interface
Defense evasion stage
Tools and capabilities required:
Sessional anti-fraud systems:
- Detection of location spoofing using proxies, public and private VPN services, or hosting systems.
- IP intelligence scoring systems are identifying highly risky IP/subnet or ISP providers.
- Detection of web or mobile device spoofing (anti-detect browsers or mobile emulators)
Performing Fraud stage
Tools and capabilities required:
Sessional anti-fraud systems:
- Detecting suspicious bonus withdrawals or bonus transfers from an unusual or well-known fraudulent device.
- Detecting bonus withdrawals performed by a user that does not match the passive biometric profile of the legitimate account owner.

Figure 13: Dark web shop selling spoofing services

Figure 14: Dark web shop offering air miles with client feedback
Stay unabated against rising airline fraud with Group-IB
Cybercriminals launch attacks at leaders in all key verticals, leveraging ever-evolving fraud techniques. It’s no different for the aviation industry.
Global airlines must be wary, proactively detect anomalies, and comprehensively secure their infrastructure by integrating an advanced fraud detection and prevention solution. What’s more, except for the financial losses, the trusted brands suffer reputational damage that can be prevented with the right risk assessment tools and in-depth expertise.
Designed to nab suspicious activity (such as account creations or instant accrual of points) and events indicative of fraud at their very onset, Group-IB’s Unified Risk Platform, including Fraud Protection and Digital Risk Protection, constantly assesses several risk indicators through signature, behavioral, and cross-channel analytics. These capabilities will stop scammers from performing account takeovers or using your brand to perform phishing attacks.
Combined with our proprietary Threat Intelligence, Fraud Protection, and Digital Risk Protection, we help organizations gain 360-degree visibility of the most persistent risks to their business.
Establish your anti-fraud and anti-scam strategy to secure the entire loyalty platform ecosystem and prevent sophisticated fraud attempts in real-time.