We’ve all been there: a flagged file or URL pops up, suspicious enough to warrant attention but vague enough to send you spiraling into hours of investigation. Is it harmless, or is it the first breadcrumb of a large attack?
Conventional malware analysis tools provide isolated data but rarely the full story. Analysts are left behind piecing together fragments of information while the attackers surge ahead.
Given our understanding of such challenges gained through first-hand experience, we created the Malware Reports library — a free tool designed to uncover malware behavior, speed up analysis, and sharpen your skills.
What’s under the hood
Malware Reports is not just another database providing ‘yes’ or ‘no’ verdicts. Without needing to sign up, you can access thousands of public malware samples, every single one of which has been analyzed by Group-IB’s Malware Detonation Platform, an analytical sandbox capable of revealing how threats behave and operate on a deeper level. The platform helps analysts gain access to step-by-step malware behavior, process execution trees, and examine network activity details. You can input a hash, domain, URL, IP address, or MITRE ATT&CK® technique to uncover indicators of compromise, connections, and patterns that link one suspicious activity to a broader threat.
Whether you’re a SOC analyst, threat hunter, or reverse engineer, such an analysis gives you the clarity required to make faster and better informed decisions. It allows you to triage alerts quickly, identify recurring behavioral patterns, and create custom detection rules like Sigma and YARA.
In this post, we describe five typical use cases, showing you how you can leverage our tool.
Unlock full access to Malware Detonation Platform
1. From hash to horizon: seeing the bigger picture
Imagine: you’re a researcher and you’ve just been sent an alert flagged in your environment. There’s no immediate context and no known malware family — just a lot of questions. You paste a hash or URL into Malware Reports. In seconds, you uncover its ties to a well-documented phishing campaign targeting financial institutions. You find out that it’s connected to domains spoofing major retailers, and that it spawns secondary files to exfiltrate sensitive data.
Even if you don’t find a report for a specific file, you can still use reports relating to other analyzed files with similar characteristics to inform your analysis. For instance, if the file communicates with a particular domain or IP address, you can search for other files that interact with the same online resource. Additionally, if the file creates another file during its activity, you can find reports about cases where the same files were generated. This approach allows you to leverage existing analyses, which means that you can understand and manage the flagged file more effectively.
The first screenshot shows a search for a similar file based on predefined properties, for example a phishing email whose attachment creates a process with the word “DHL” in the name. The results indicate that the threat can likely be attributed to the Formbook malware. The second screenshot shows a detailed report on Formbook activity and contains all the necessary information to make informed response decisions.
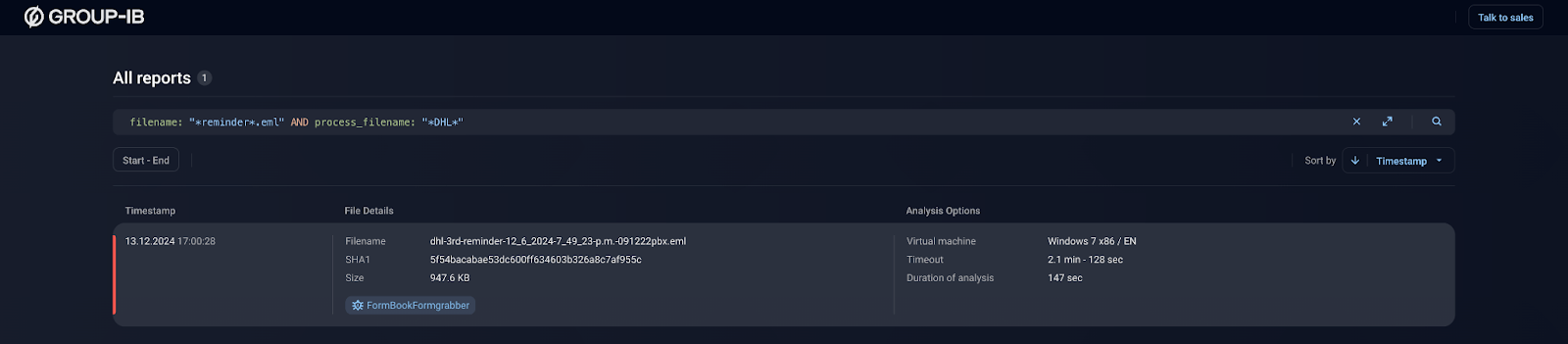
Figure 1. Search for a similar file based on predefined properties
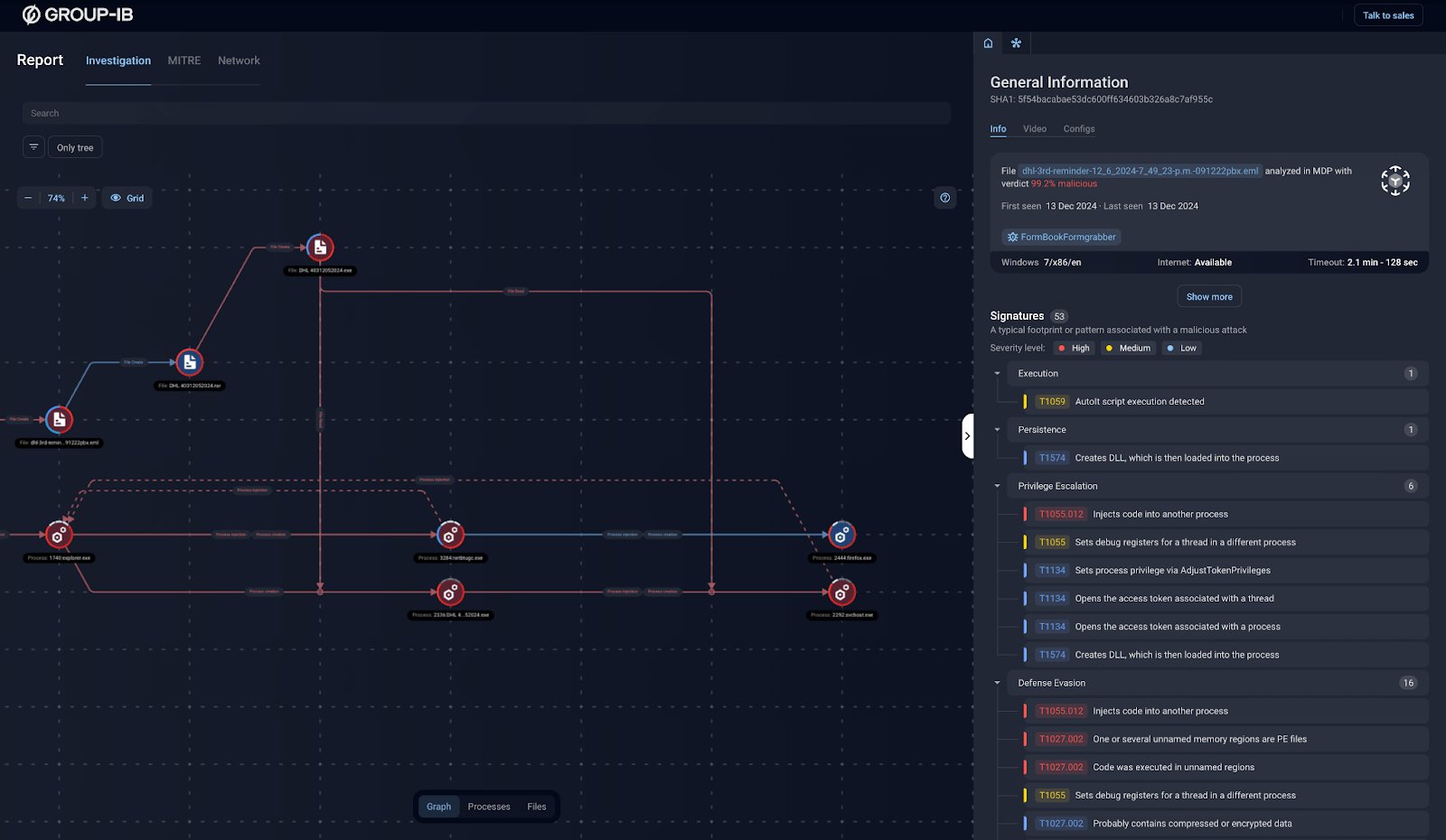
Figure 2. Example of a detailed report on Formbook stealer
This is attribution in action. It’s the foundation of in-depth investigations — the kind that frameworks like MITRE ATT&CK® build on. Instead of wading through noise, you dive into clear, actionable intelligence that places the suspicious hash into a broader context and speeds up the malware analysis.
2. Behavior is everything
Say you’re a security analyst and your anti-virus system detects a file on the host. After you find a report on the file and attribute it, you will probably want to dive deeper and understand its behavior.
- Did the file drop hidden executables or modify system files?
- Did it modify registry entries to achieve persistence?
- Did it communicate with known command-and-control servers or use encrypted channels to exfiltrate data?
When analyzing a suspicious file, it’s important to examine any secondary files it creates or launches as these can provide insights into the malware’s behavior and persistence mechanisms. For instance, if you discover that the file has generated another executable, you must locate and analyze the secondary file on your system to assess its impact and remove it if necessary.
Similarly, if the malware has established a new system service, identifying and disabling the service is vital to preventing the malicious process from running on startup. Malware might also modify firewall rules to facilitate unauthorized communications or data exfiltration. Detecting such changes means that you can revert the firewall settings to their secure state and block any malicious network activity.
To find such details, you can explore the report or the tab with artifacts that contain a list of all the modifications that have been carried out.
In the case of LockBit, for instance, Malware Reports demonstrates how deeply this ransomware infiltrates systems and establishes many persistence points. Simply deleting the original file won’t suffice — you’ll need to make a considerable effort to remove it from your computer for good.
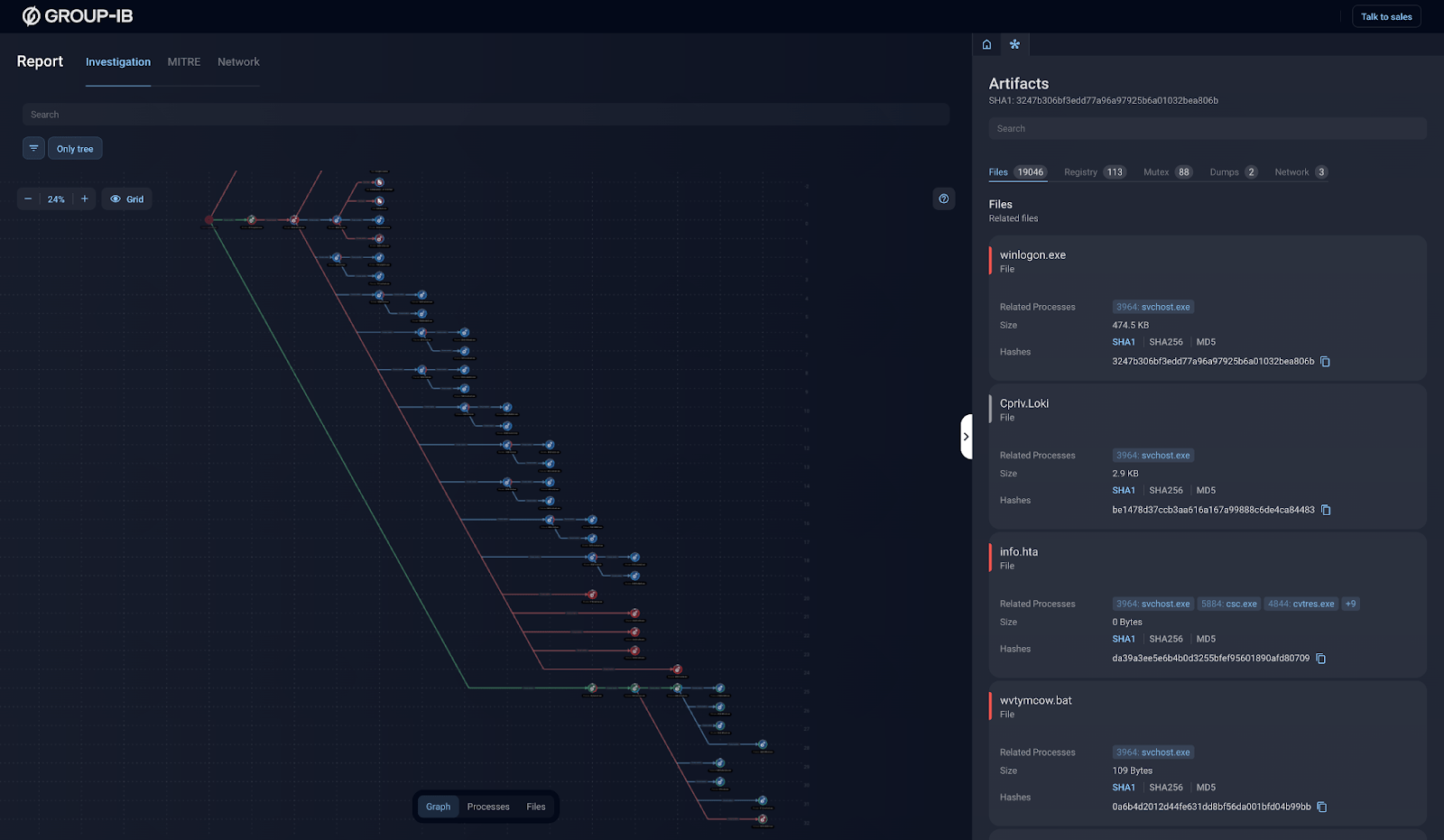
Figure 3. Example of a report on LockBit malware that shows its complex infiltration methods and persistence techniques
Such insights give guidance on how to isolate and clean compromised hosts effectively while also providing the intelligence required to prevent similar threats from taking hold in the future.
3. From curiosity to action
Insights are valuable, but only if they lead to action. Malware Reports bridges the gap by helping you turn findings into proactive measures.
For example, let’s say you’re reading a blog post about a new malware strain that’s making waves in your industry. The post provides some background, but it lacks the technical details on malware behavior that you need to protect your organization. In such cases, you could search Malware Reports for the file in question. Looking at its signatures, you can understand how the malware behaves and which artifacts it creates in the system. This knowledge will help you craft Sigma rules for your SIEM or Suricata signatures for your IDS.
In the screenshot below, you can once again see LockBit in action. The report provides clear and valuable insights into its behavior, which can be used to create behavior-based Sigma rules.
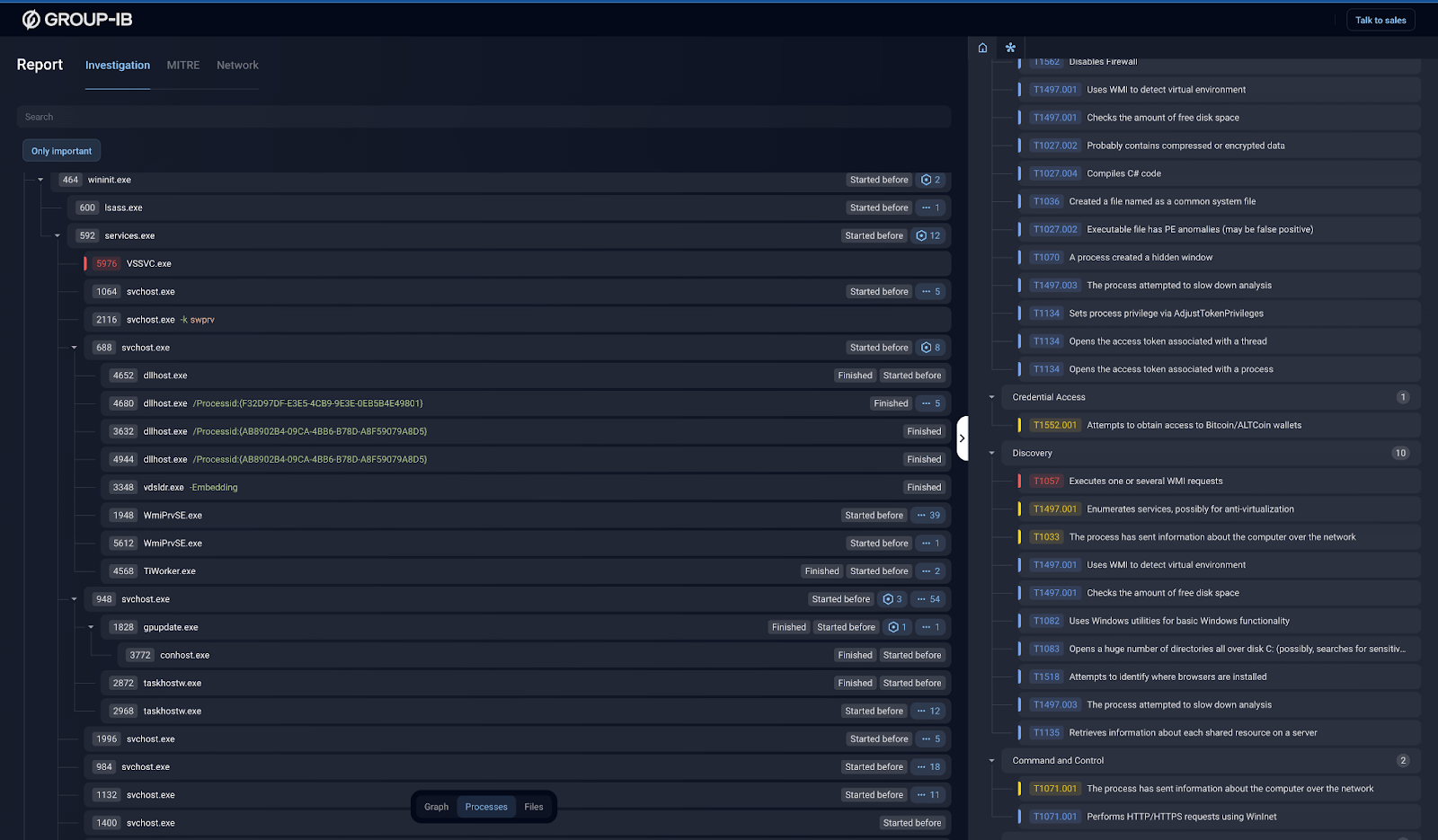
Figure 4. Example of LockBit behavior analysis that can be used to create Sigma detection rules
Proactively deploying such custom rules enhances your security and ensures that you’re anticipating threats and blocking attackers before they have a chance to strike.
4. Adapting to an evolving enemy
Malware doesn’t stay the same for long. Variants emerge, techniques evolve, and attackers adapt to bypass defenses. Malware Reports helps you stay one step ahead by comparing behavior across samples from the same family.
- Can this threat be found by the file created?
To answer the above question, you should search for similar samples over various periods. Doing so will help to identify family-recurring patterns, like process injection, unique file paths, or creating the same file every time. Or, you might discover that while an older variant relied on HTTP for command-and-control communication, a newer version has shifted to DNS tunneling. Based on such patterns, you can create detection rules for your security systems. Such insights aren’t just interesting — they will help to refine and strengthen your detection and prevention strategies.
As an example of historical data analysis, the screenshot below illustrates the AgentTesla malware family, analyzed over a one-year period.

Figure 5. AgentTesla malware family reports in a one-year perspective
5. A resource for growth
Last but not least, Malware Reports is also a resource for building expertise.
Say you’re a junior malware analyst learning how to reverse engineer malware. After hours of digging through its code, you can use Malware Reports to validate your findings against its detailed behavioral report. Did you catch every clue? What did you miss? The process sharpens your skills all the while ensuring that your analysis is accurate.
For newer team members, using Malware Reports is a safe and practical way to explore real-world malware and gain hands-on experience, which helps them grow as analysts. You can also share the reports with your team and community, thereby raising everyone’s awareness and expertise.
Find millions of free malware reports in one place
Why analytical sandboxes are essential for your business
While standard sandboxes excel at automating basic detection and providing verdicts, they often stop short of offering the depth that analysts need. That’s why using analytical sandboxes like Group-IB’s Malware Detonation Platform is essential.
Analytical sandboxes operate in a different league, focusing on enriching knowledge about file behavior. They uncover the intricate workings of malware, offering detailed and visual insights into how it behaves and evolves over time. The more in-depth understanding allows for better decisions and proactive defense strategies. Such tools are usually offered as an isolated solution that only tells you how the threat functions. Often they are difficult to integrate with other solutions.
Here’s where Group-IB takes things a step further: we’re one of the few major vendors that integrates an analytical sandbox directly into protection solutions as part of Group-IB’s Managed XDR. This means that the insights from Malware Detonation Platform aren’t theoretical — they’re actionable and directly tied to your workflows.
Key benefits of an analytical sandbox in your security stack:
- Integrated predictions with EDR: By connecting an analytical sandbox to an EDR, you gain a sophisticated protection system enriched with detailed behavior analysis reports. This means that your system predicts how the detected file will behave in your system and protects you against even the most evasive malware, with no integration or manual efforts required.
- Proactive email protection: Imagine receiving a malicious email attachment. Instead of waiting for it to execute, you’ll obtain a clear prediction of its behavior in the system. For example, the malware might disable Windows Security options or create alternate data streams. If the same malware is detected on your host, the sandbox will give you detailed instructions on how to neutralize the threat long before the file starts to run on the host.
- Prepared responses: With instructions generated well before the file can exhibit any harmful activity, you save critical time. Everything you need — process isolation, termination, and host cleanup — is prepared for you in advance.
- Smooth investigations: An analytical sandbox doesn’t just detect threats — it maps the entire attack chain. You’ll gain a complete timeline of events — from the initial infection source to lateral movement, which will help your team to investigate incidents quickly and effectively.
When an anti-virus or EDR solution on your host alerts you to a threat, you usually don’t have hours to examine it manually. Analytical sandboxes save you time, spare your nerves and, eventually, protect your infrastructure. Instead of hiring additional in-house staff or outsourcing malware analysts to explain a file’s behavior and advise on remediation, the sandbox does the job and acts as an automated virus analyst. It helps you identify malicious processes, terminate them, and prevent further compromise all the while helping your team to understand the threat better.
Watch Group-IB expert Gary Ruddell show how to harness the power of Malware Reports for your malware analysis.



































